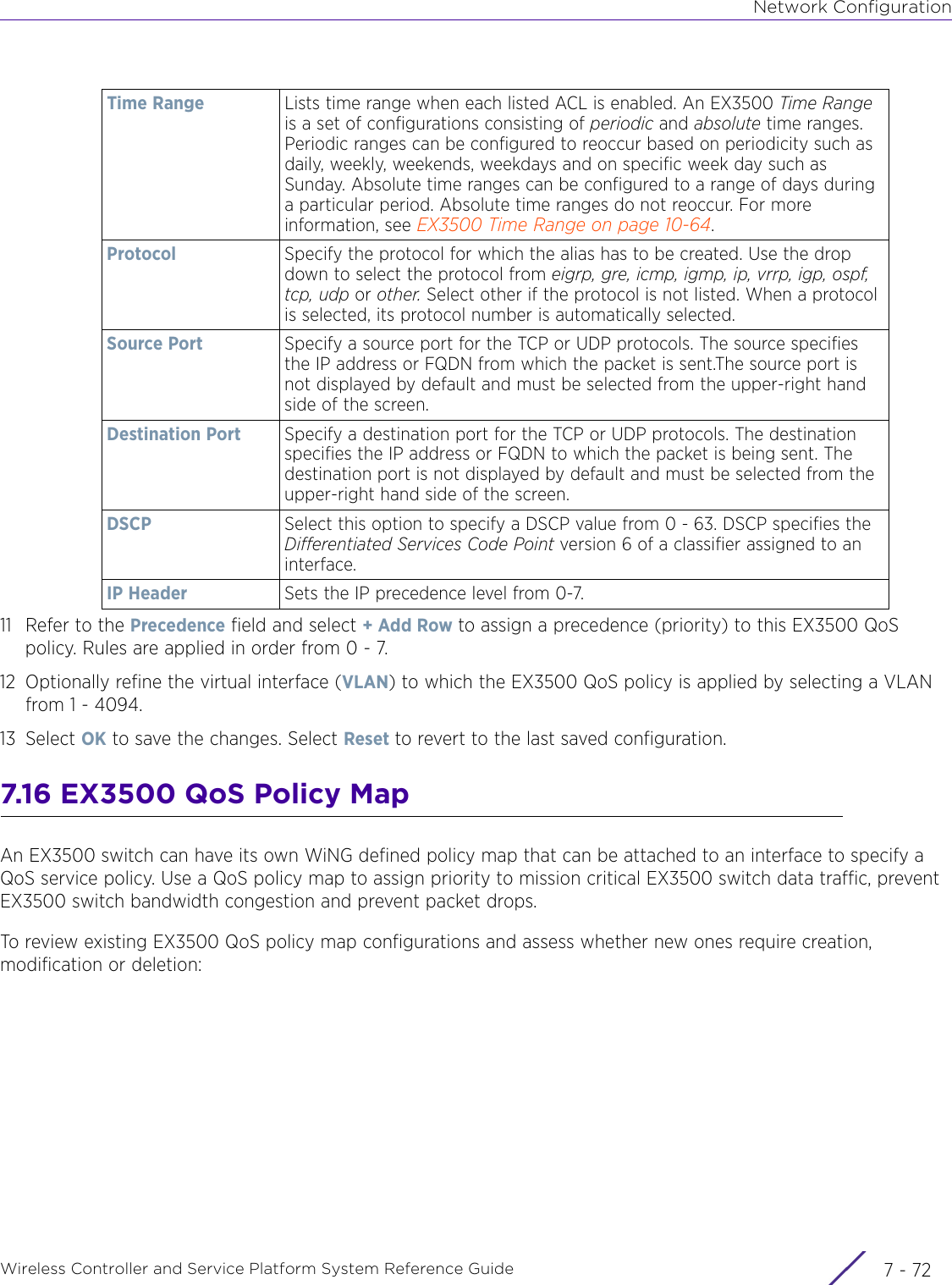
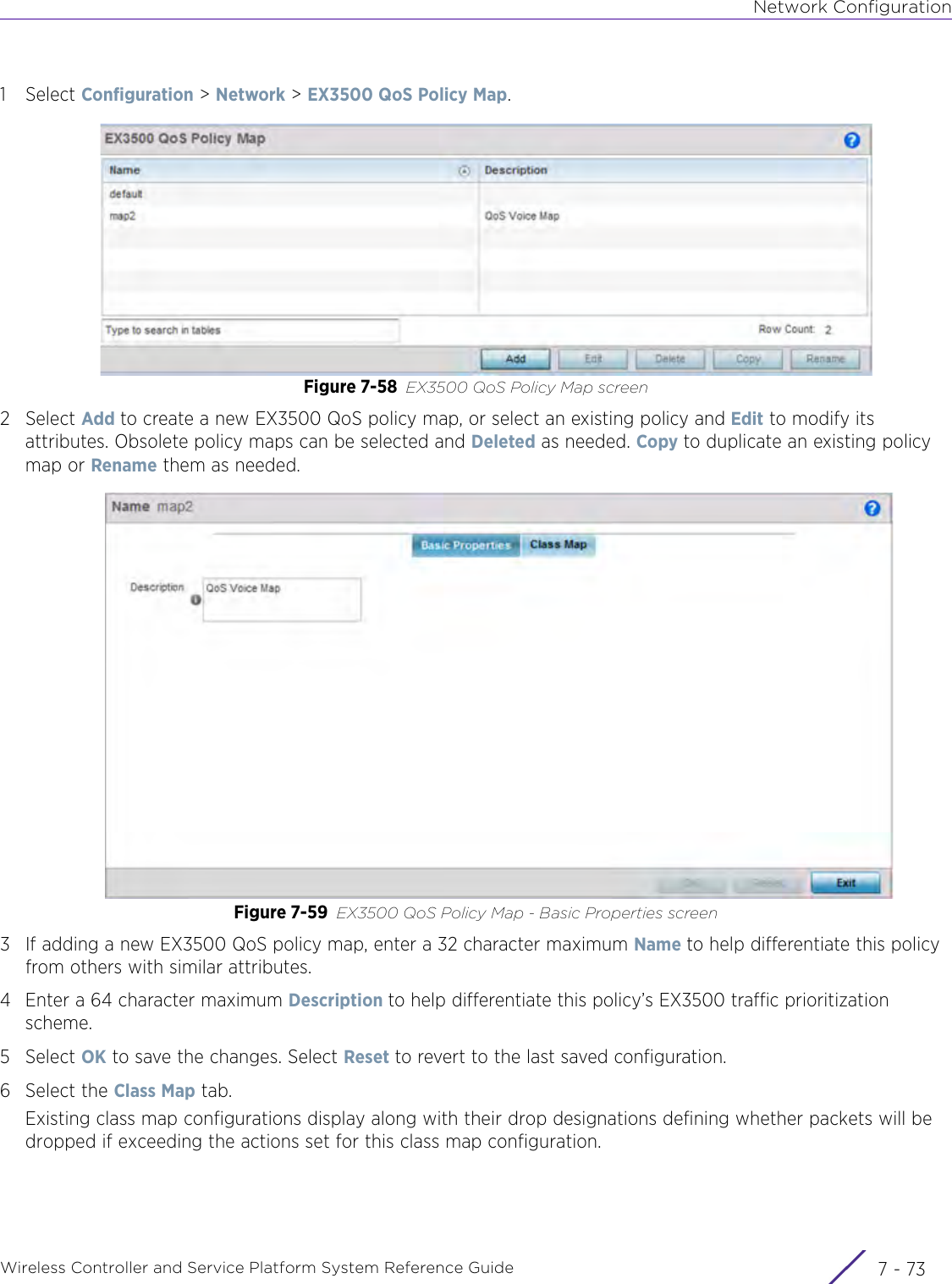
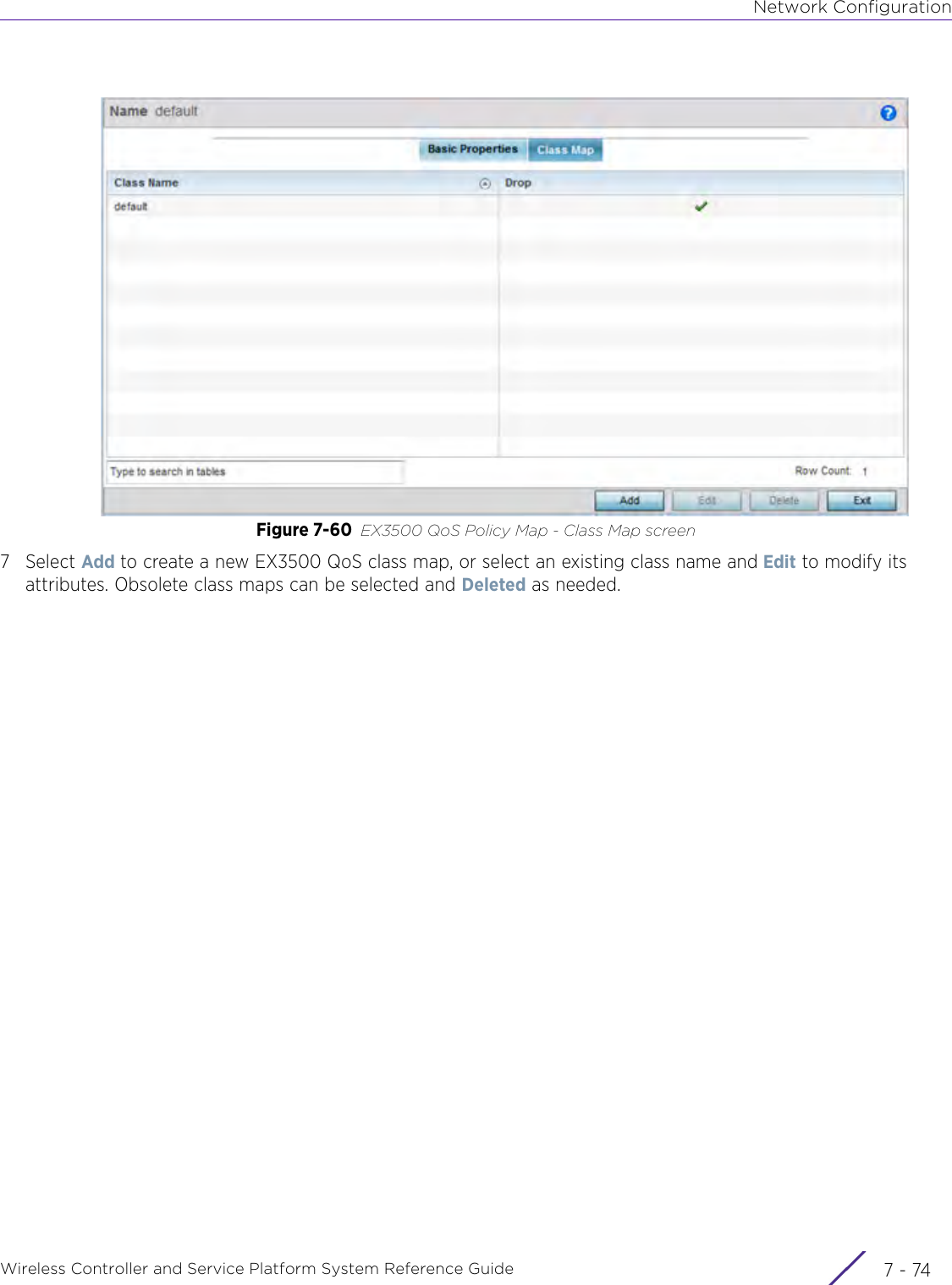
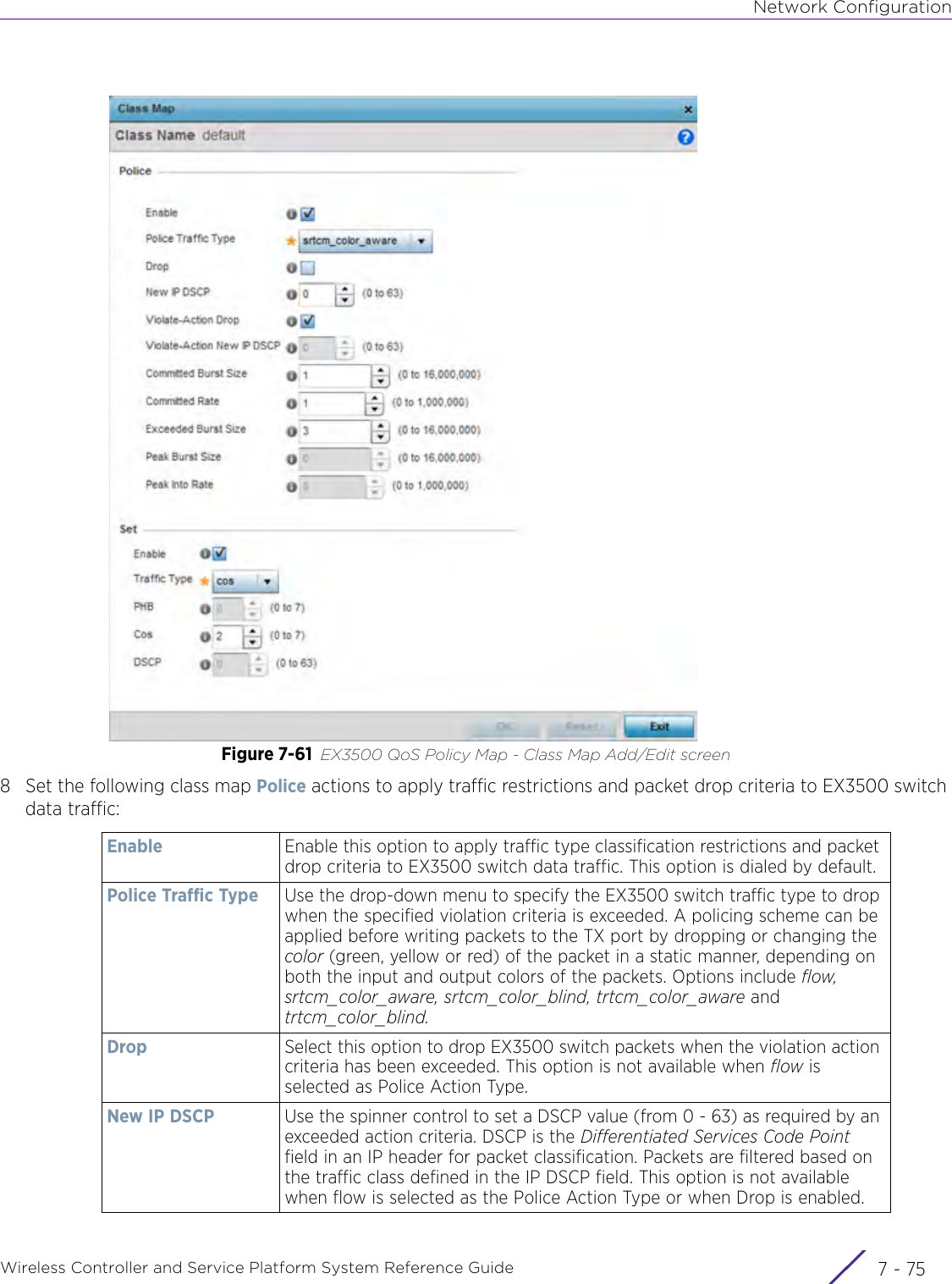
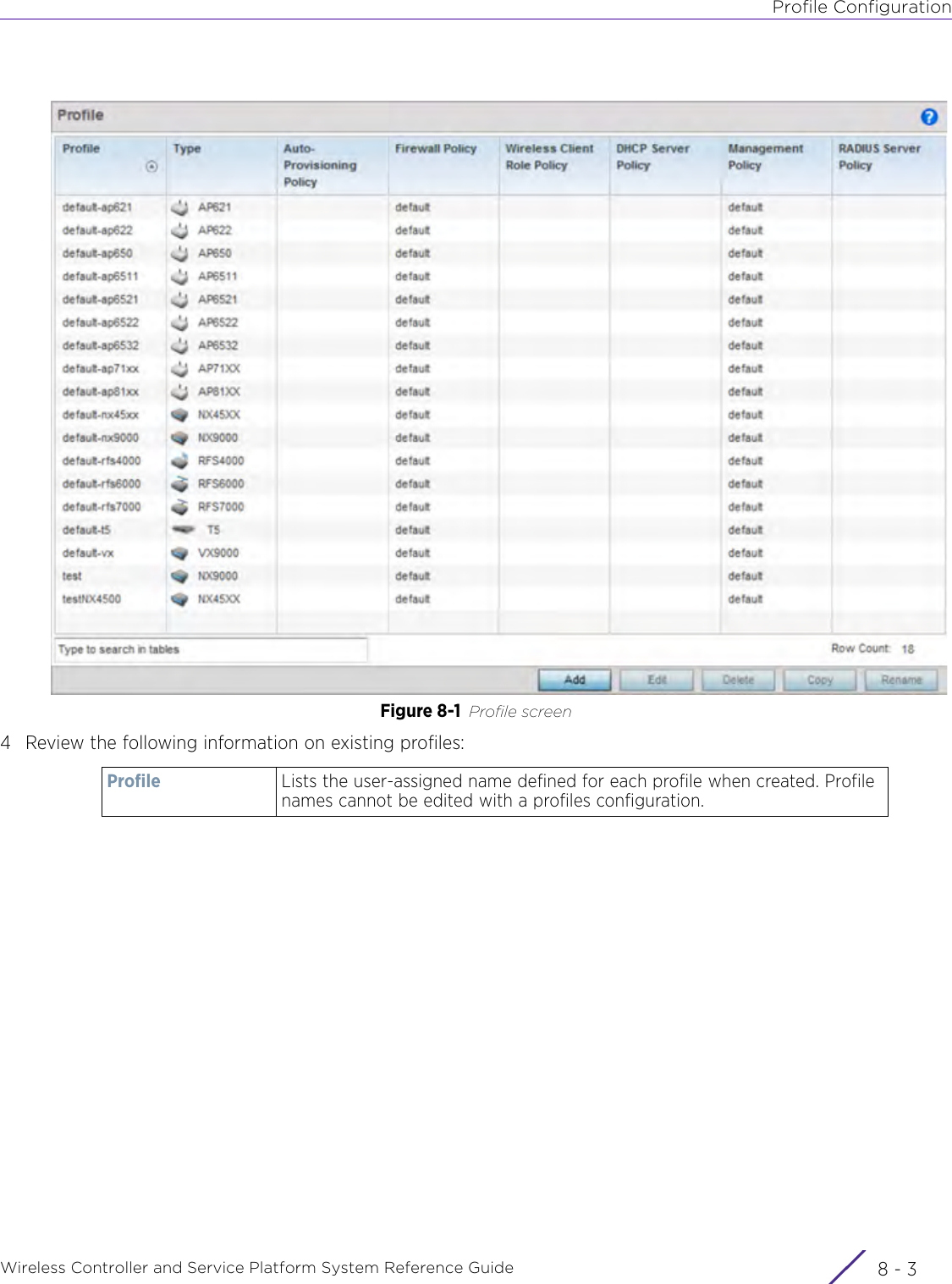
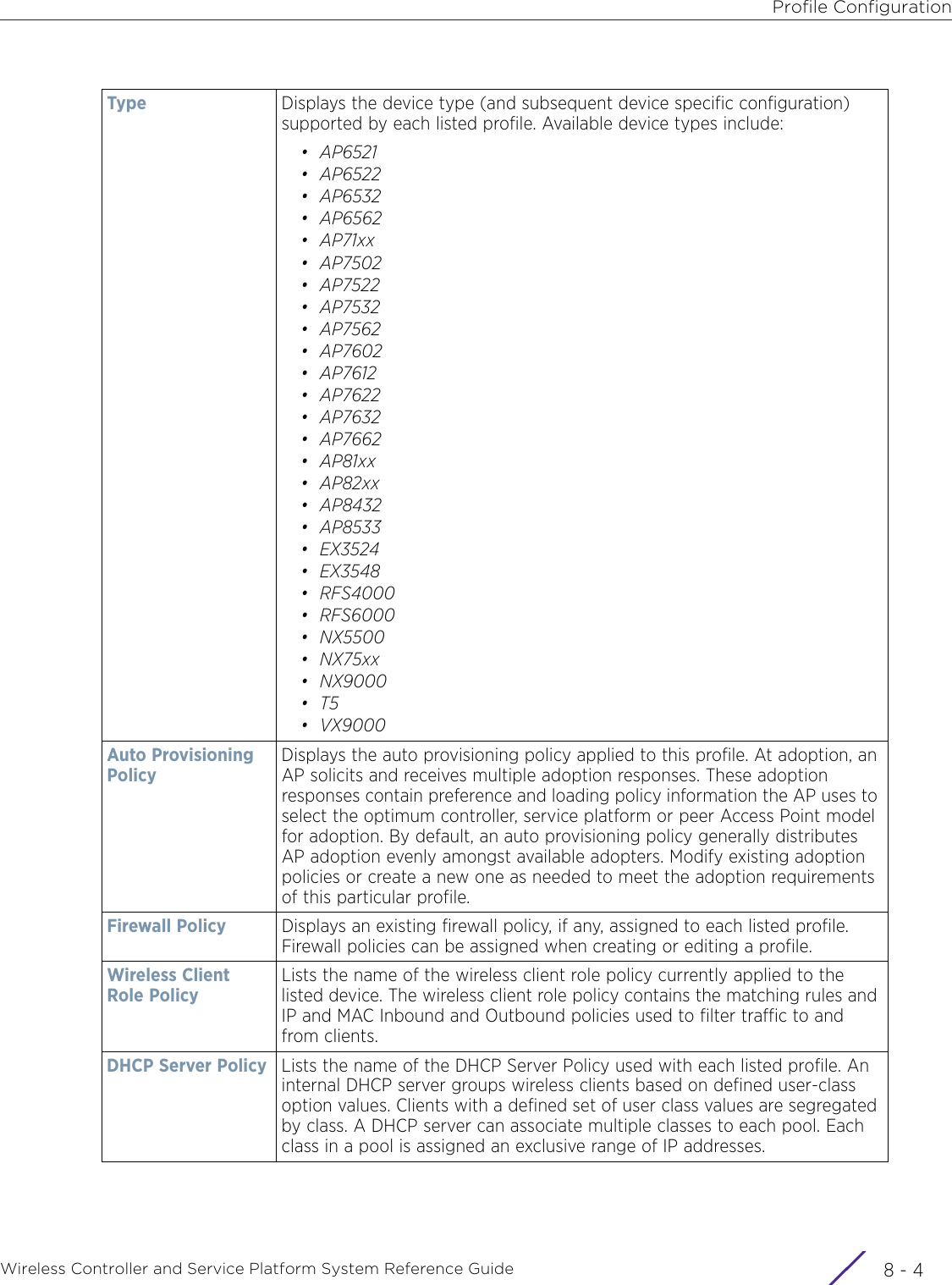
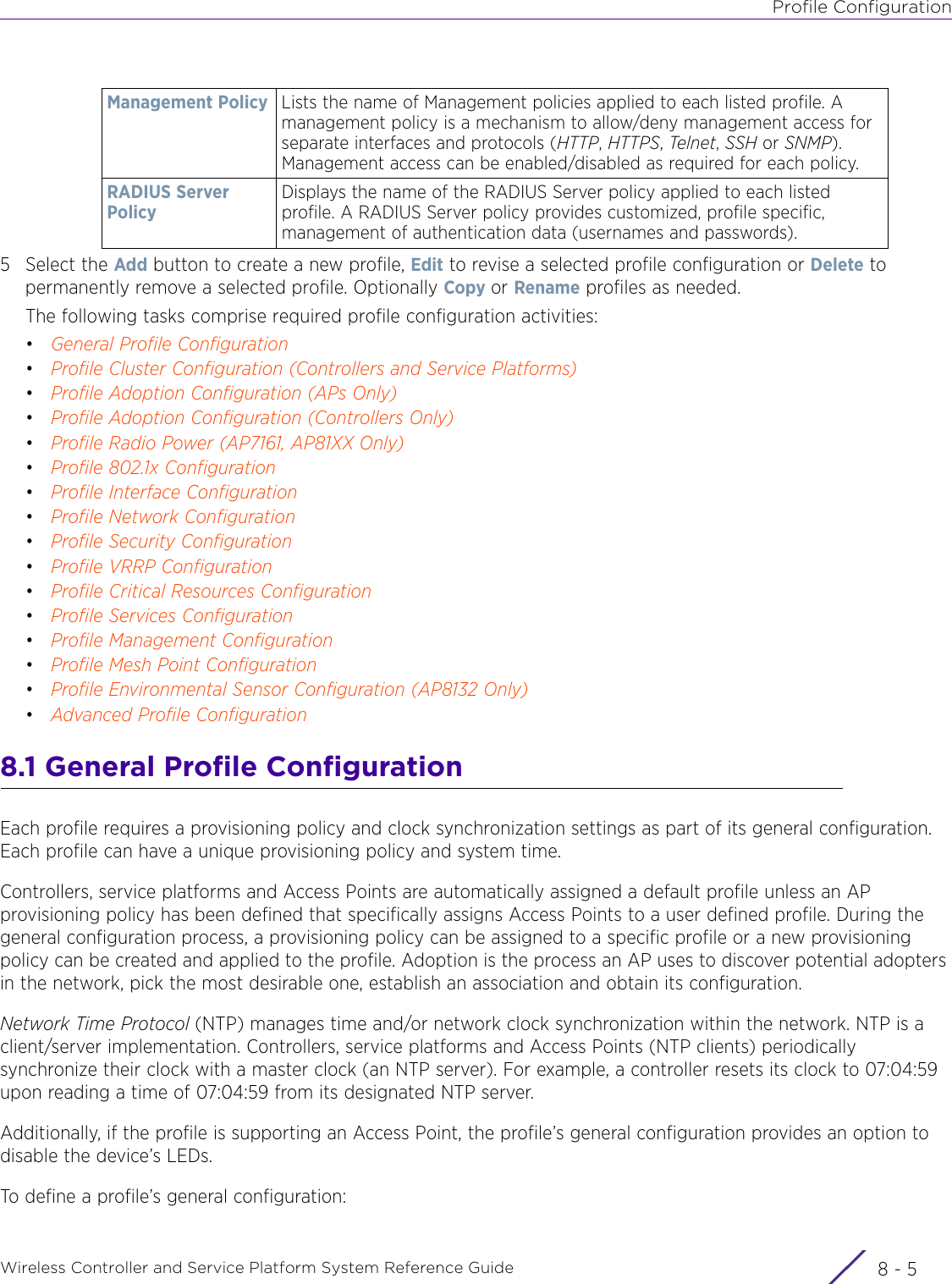
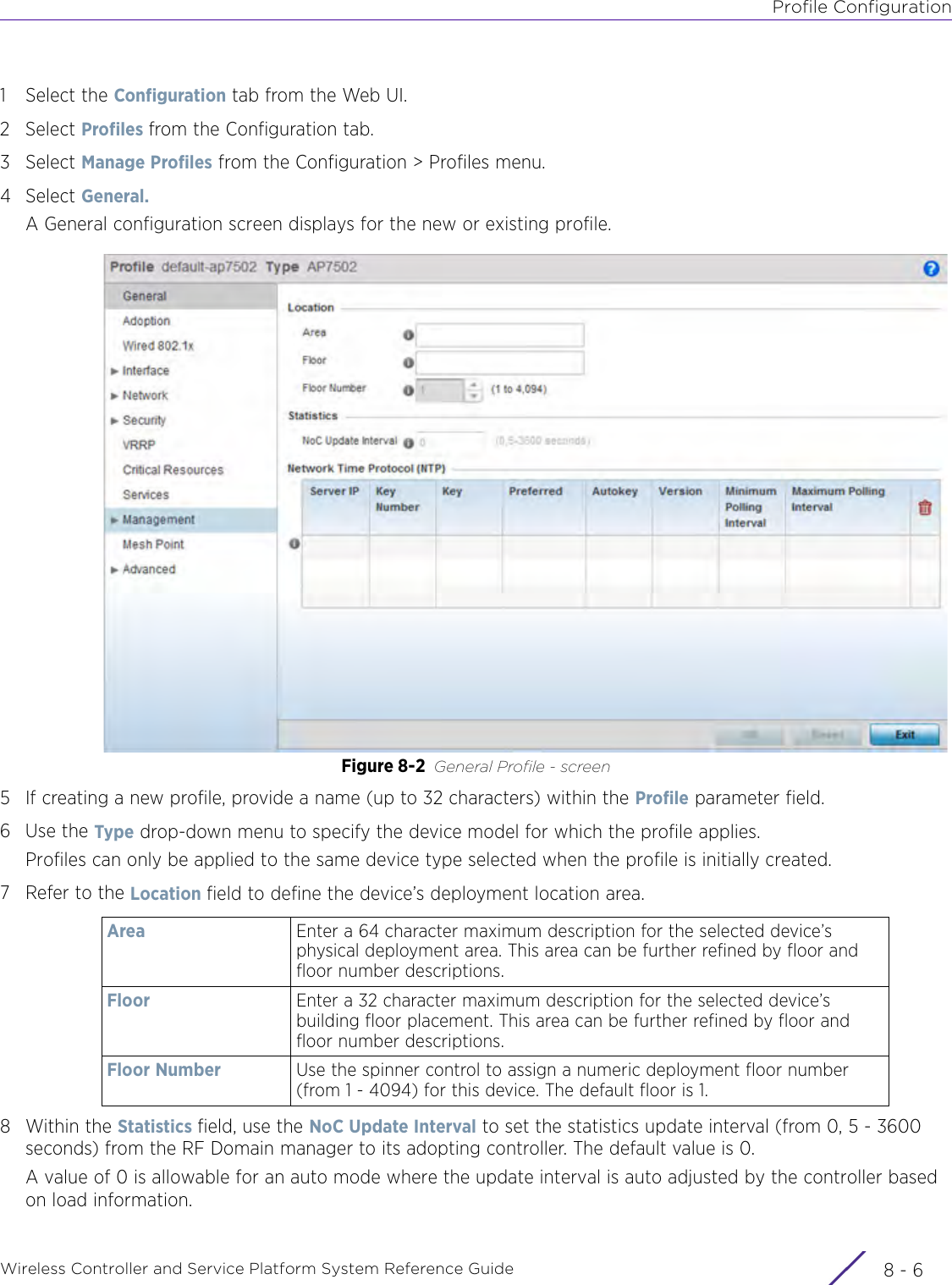
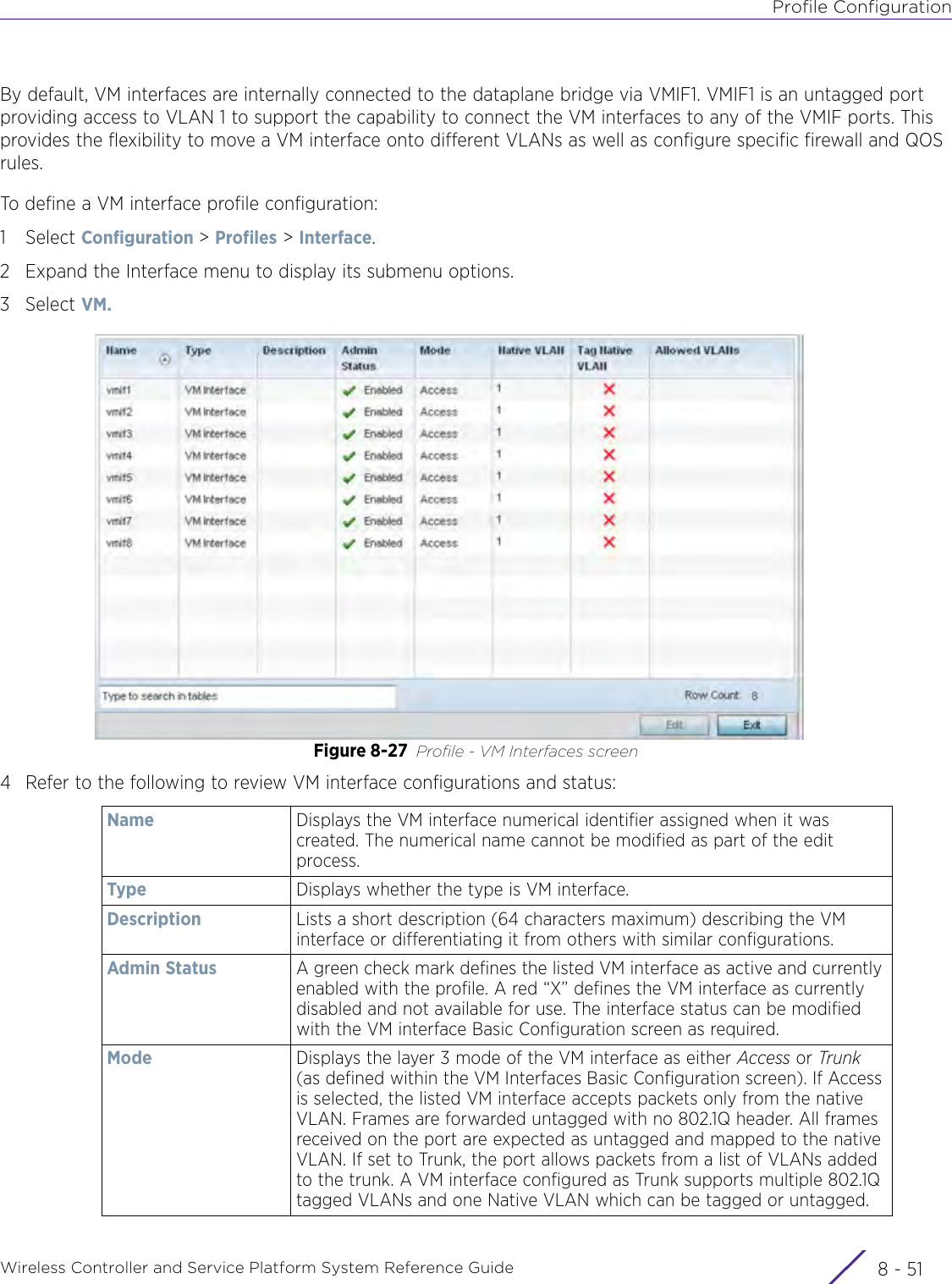
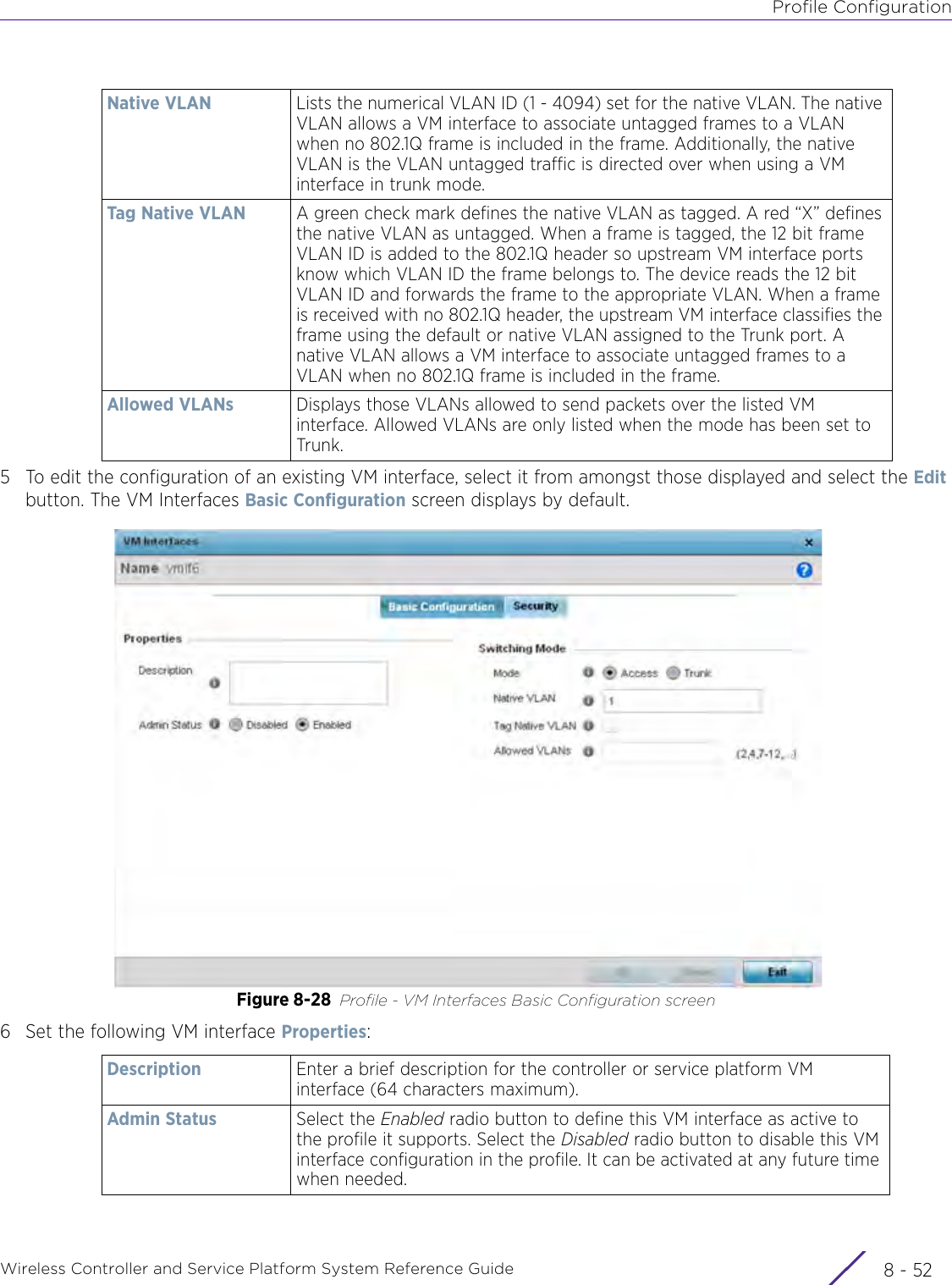
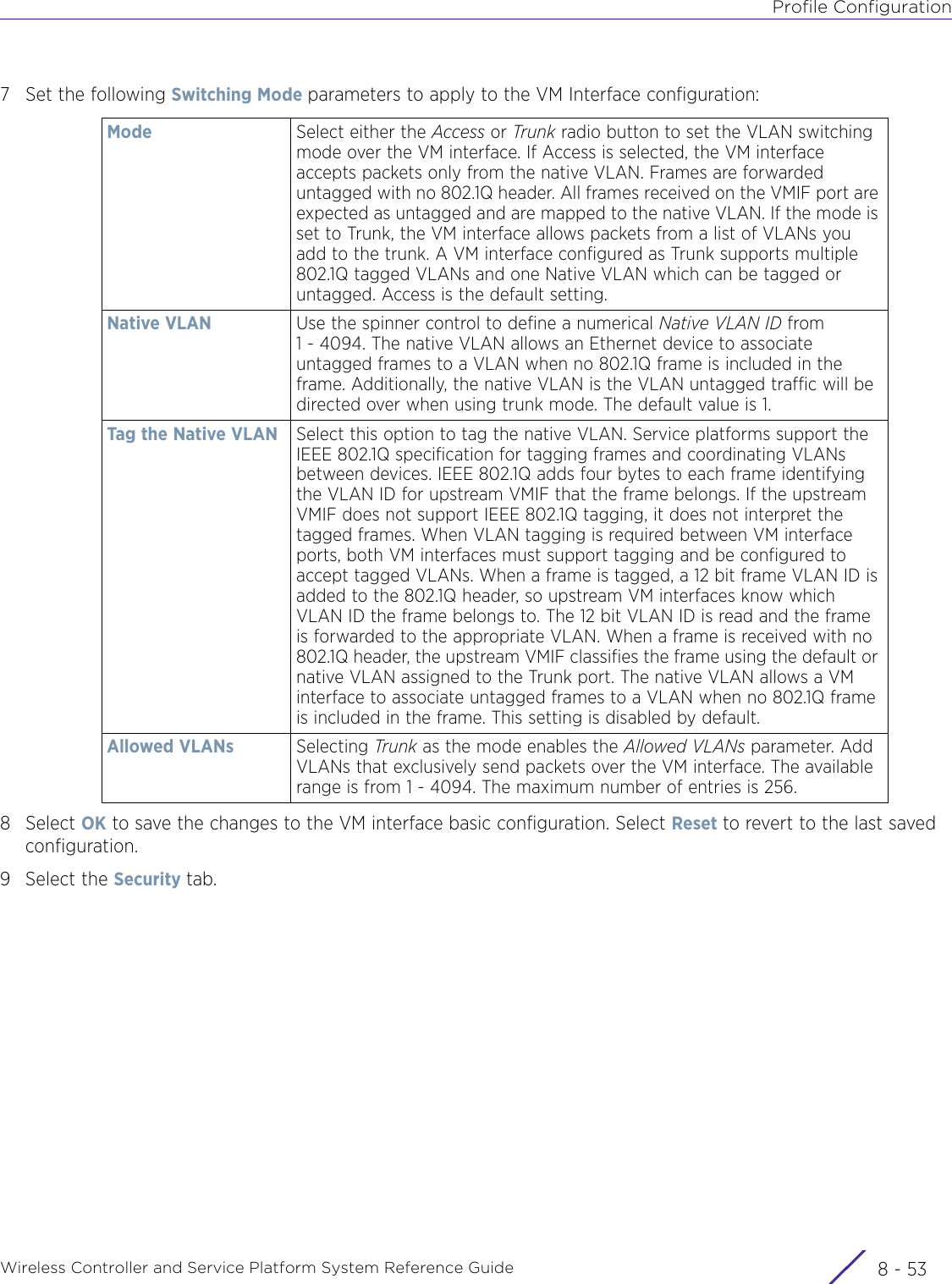
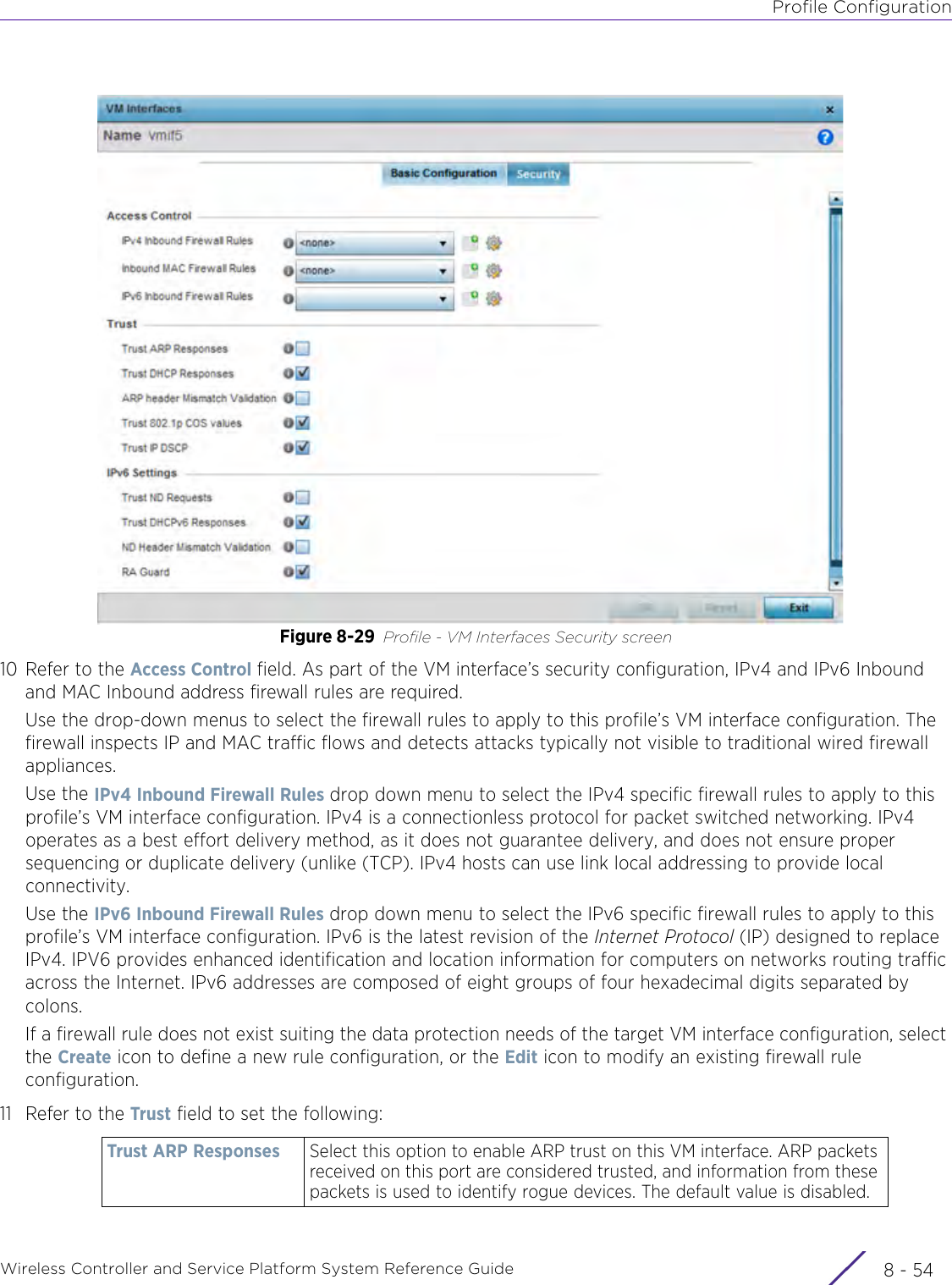
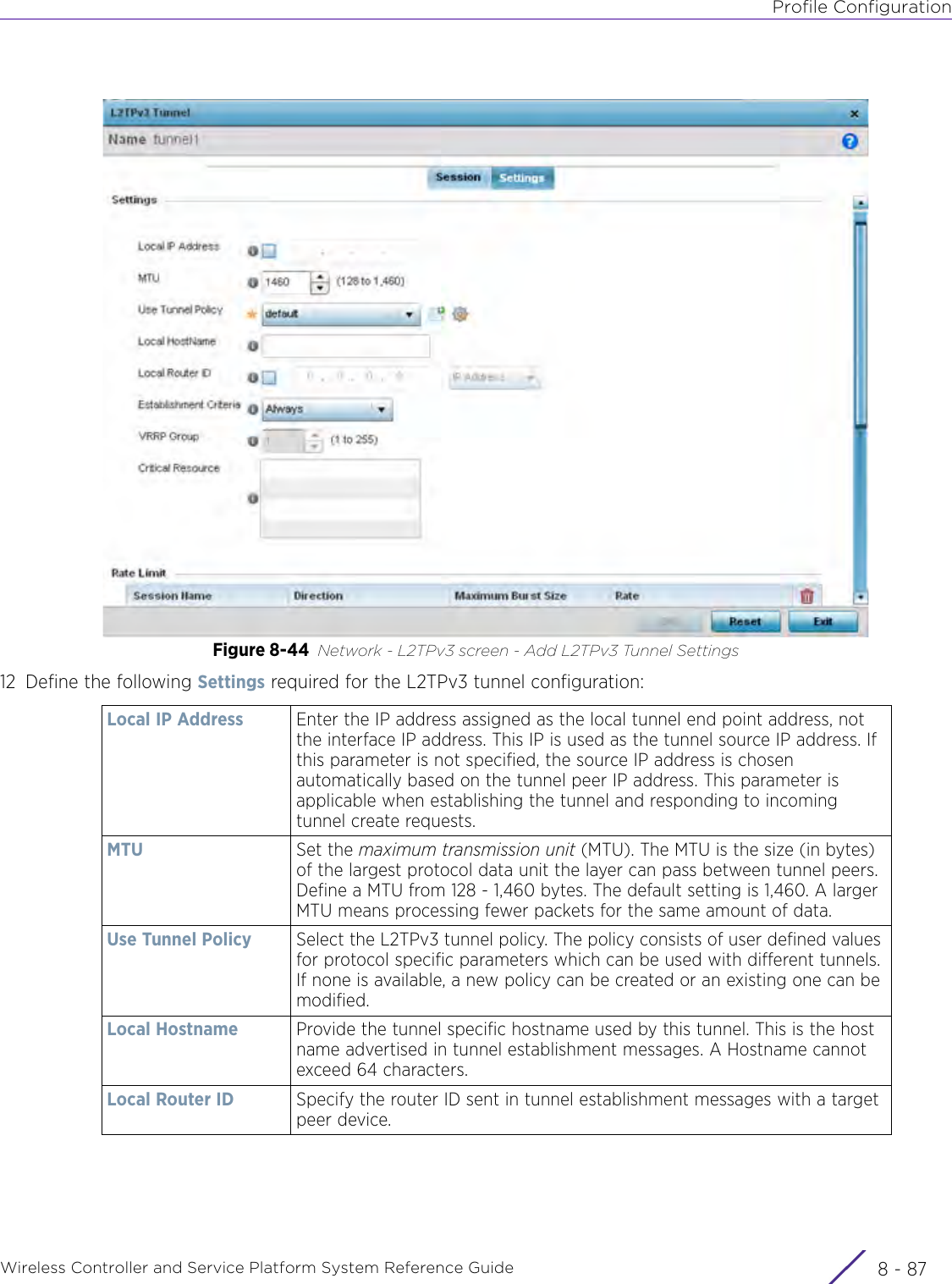
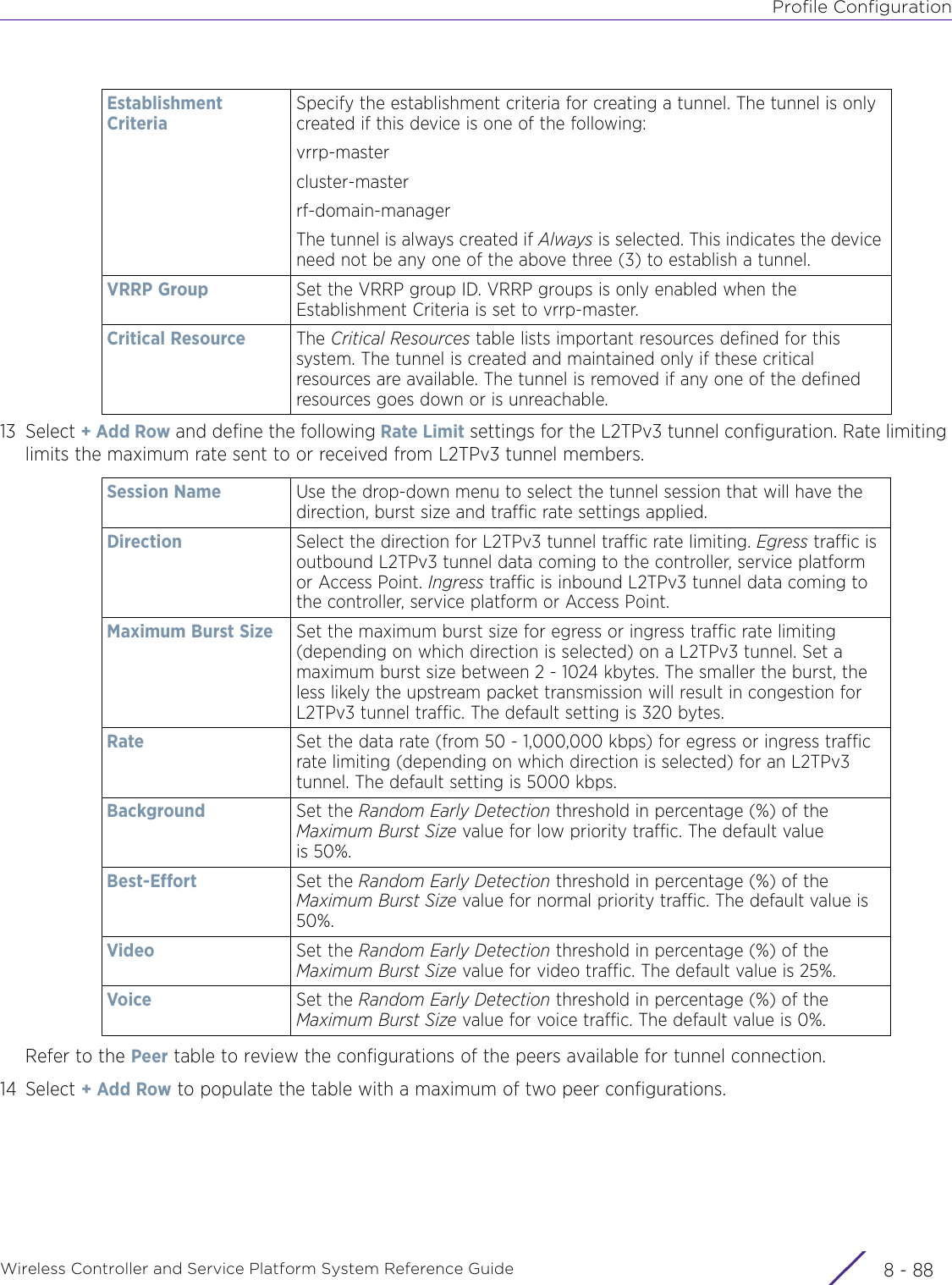
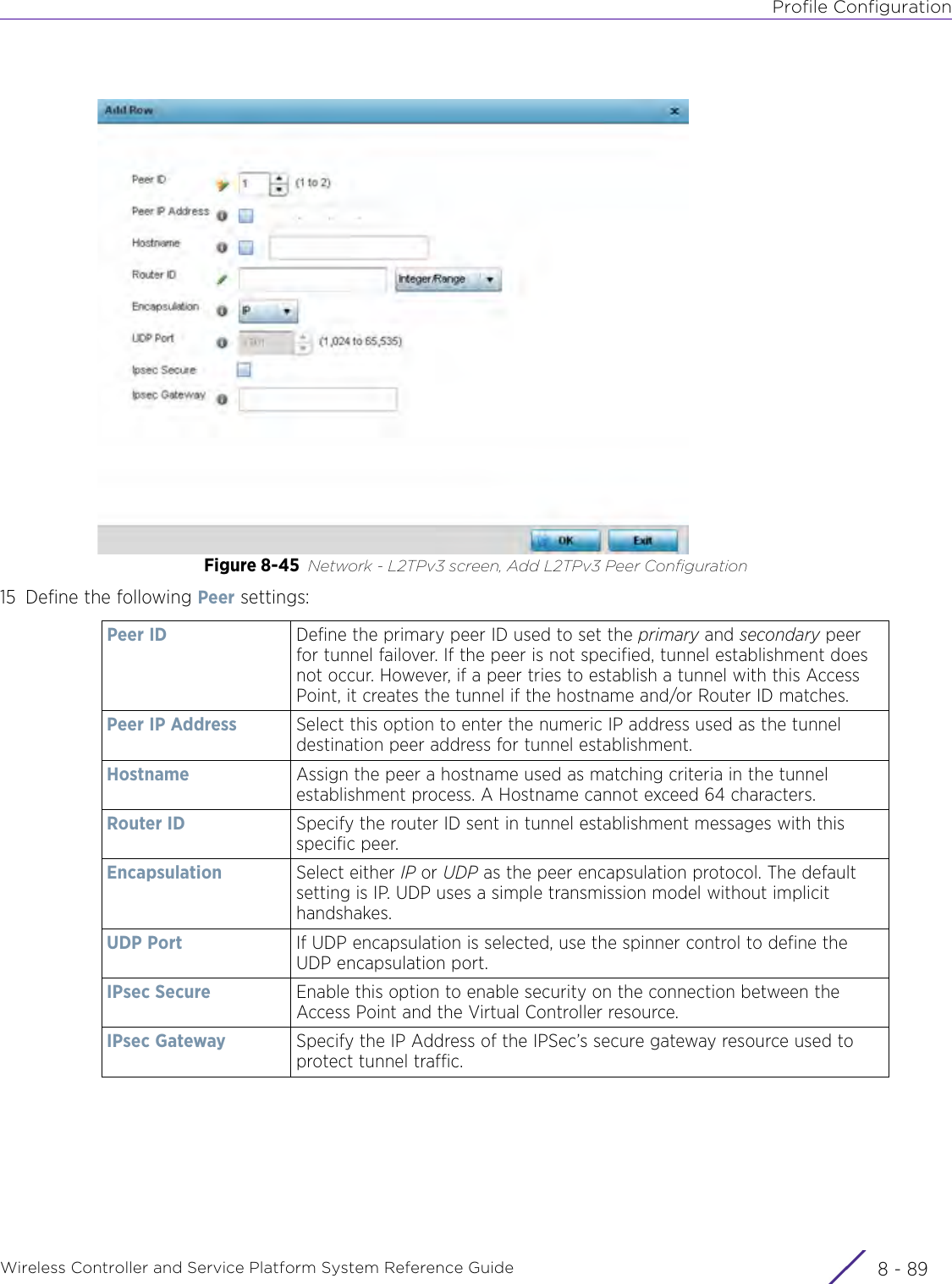
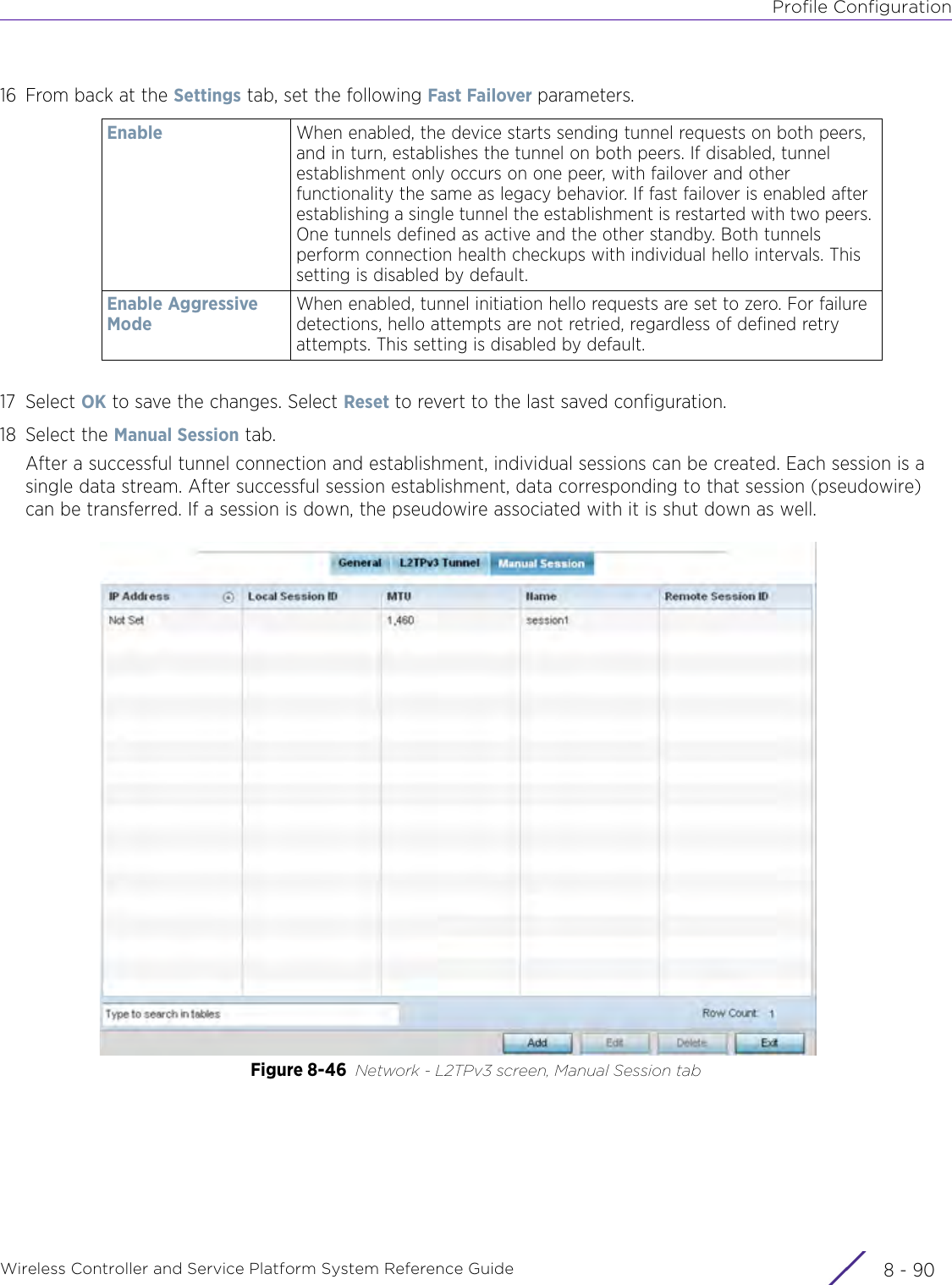
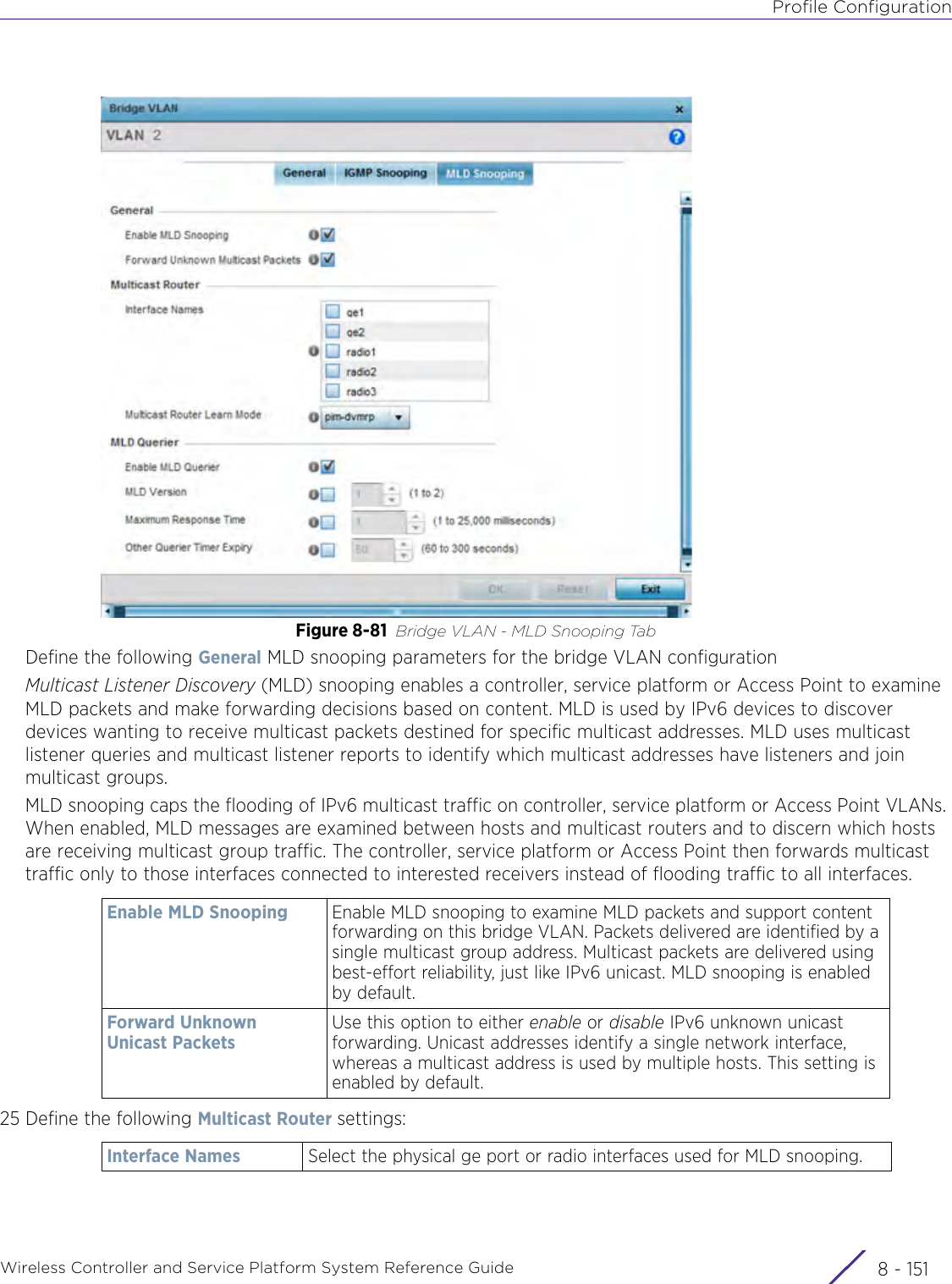
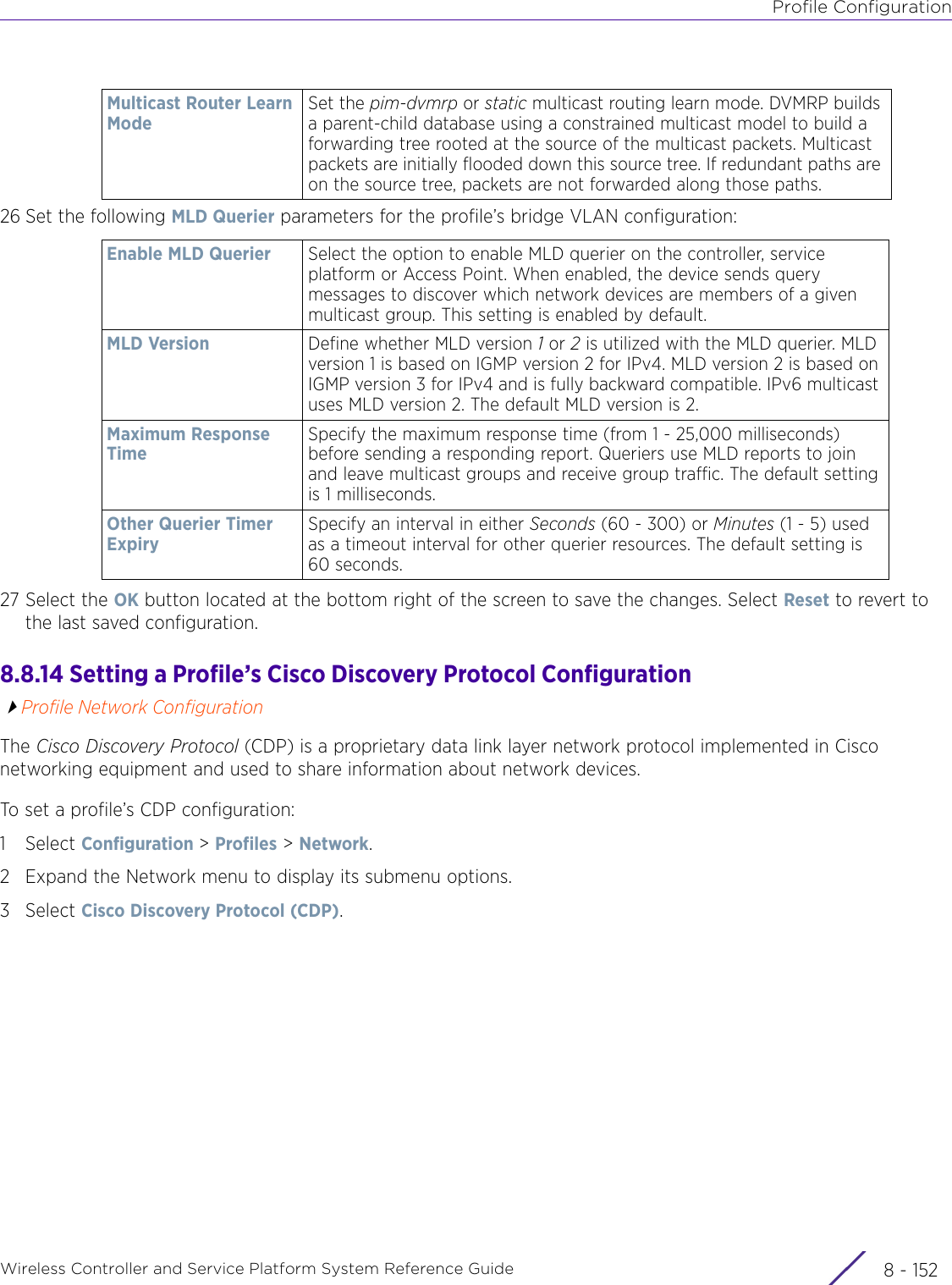
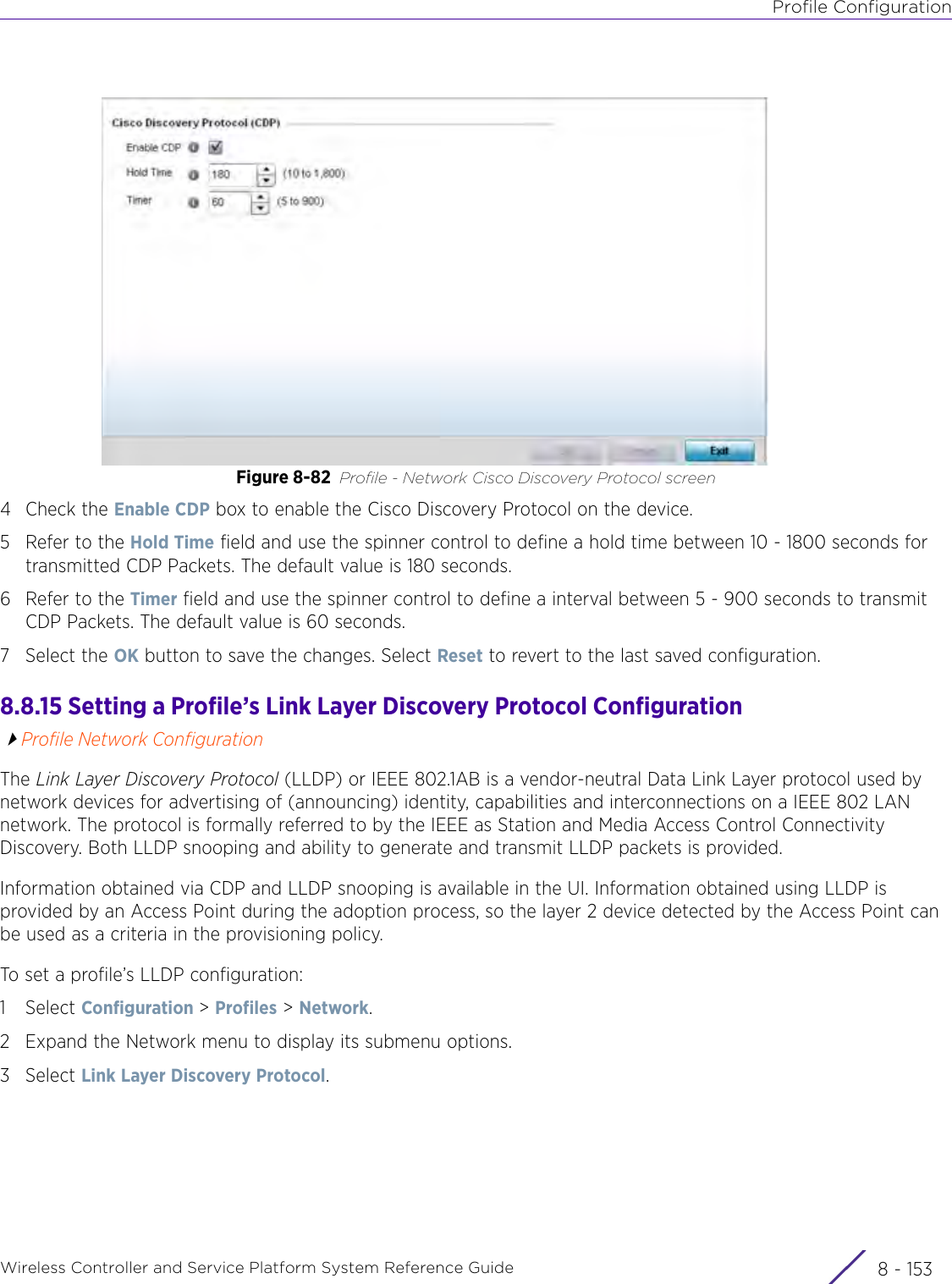
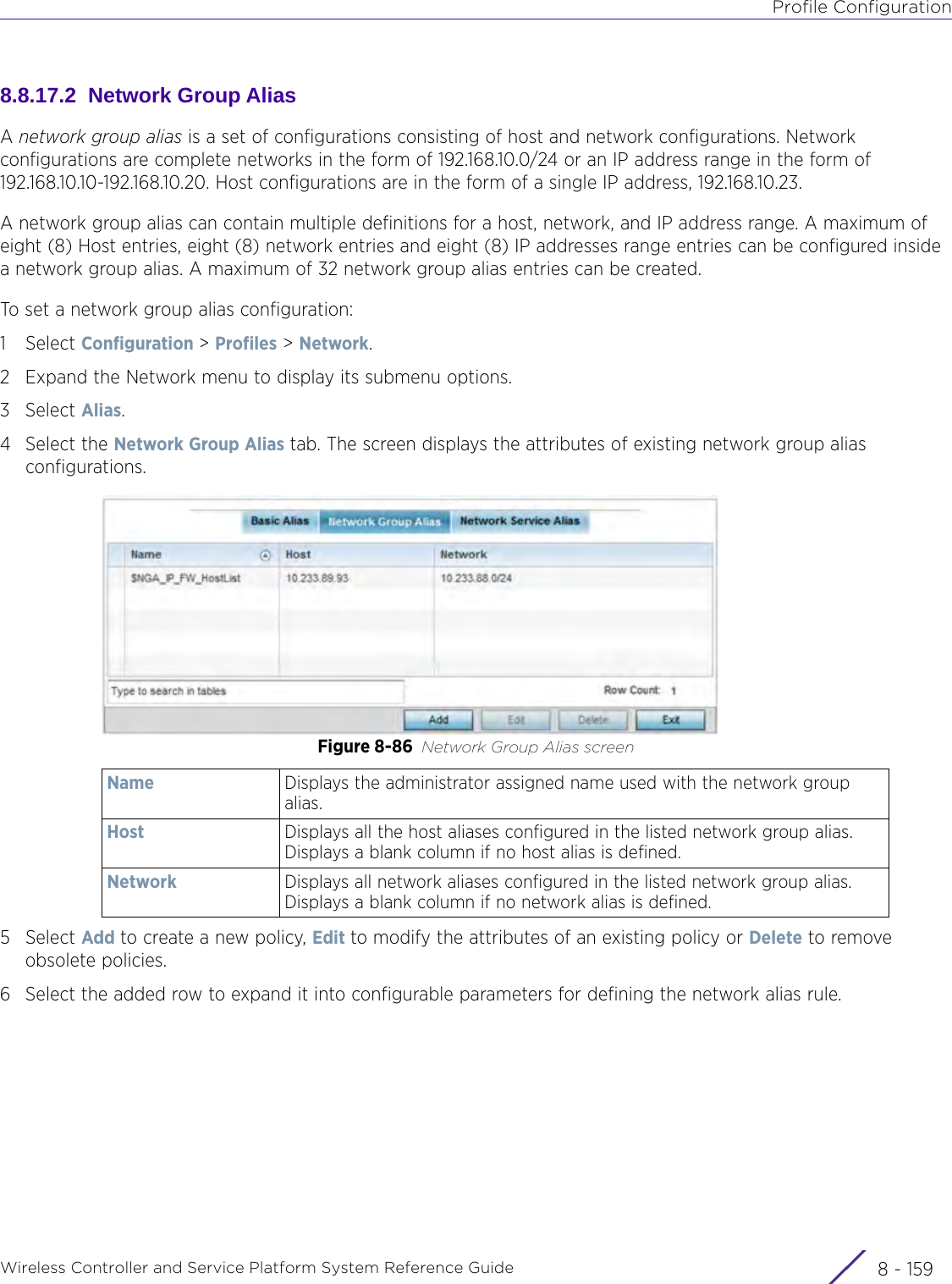
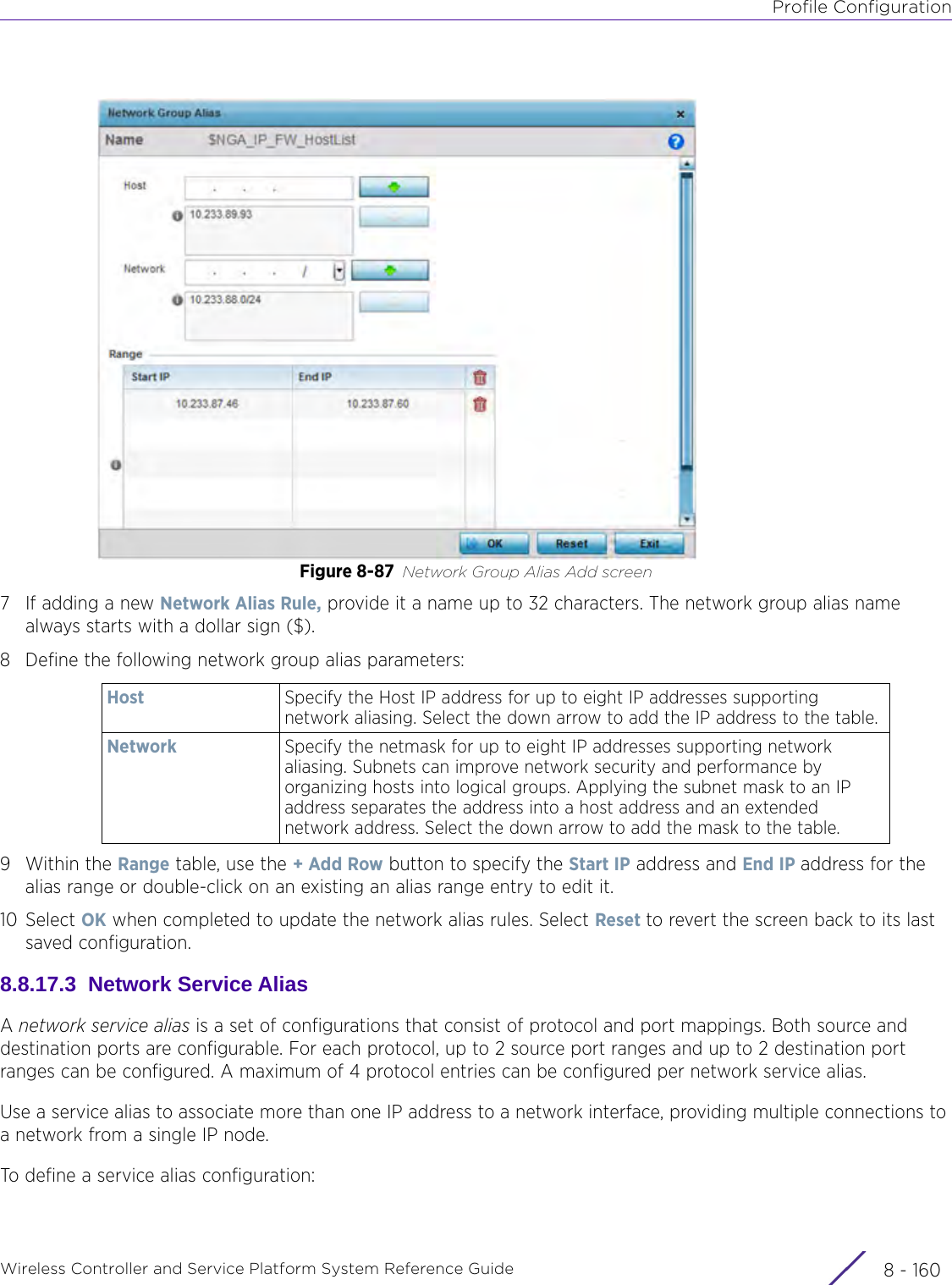
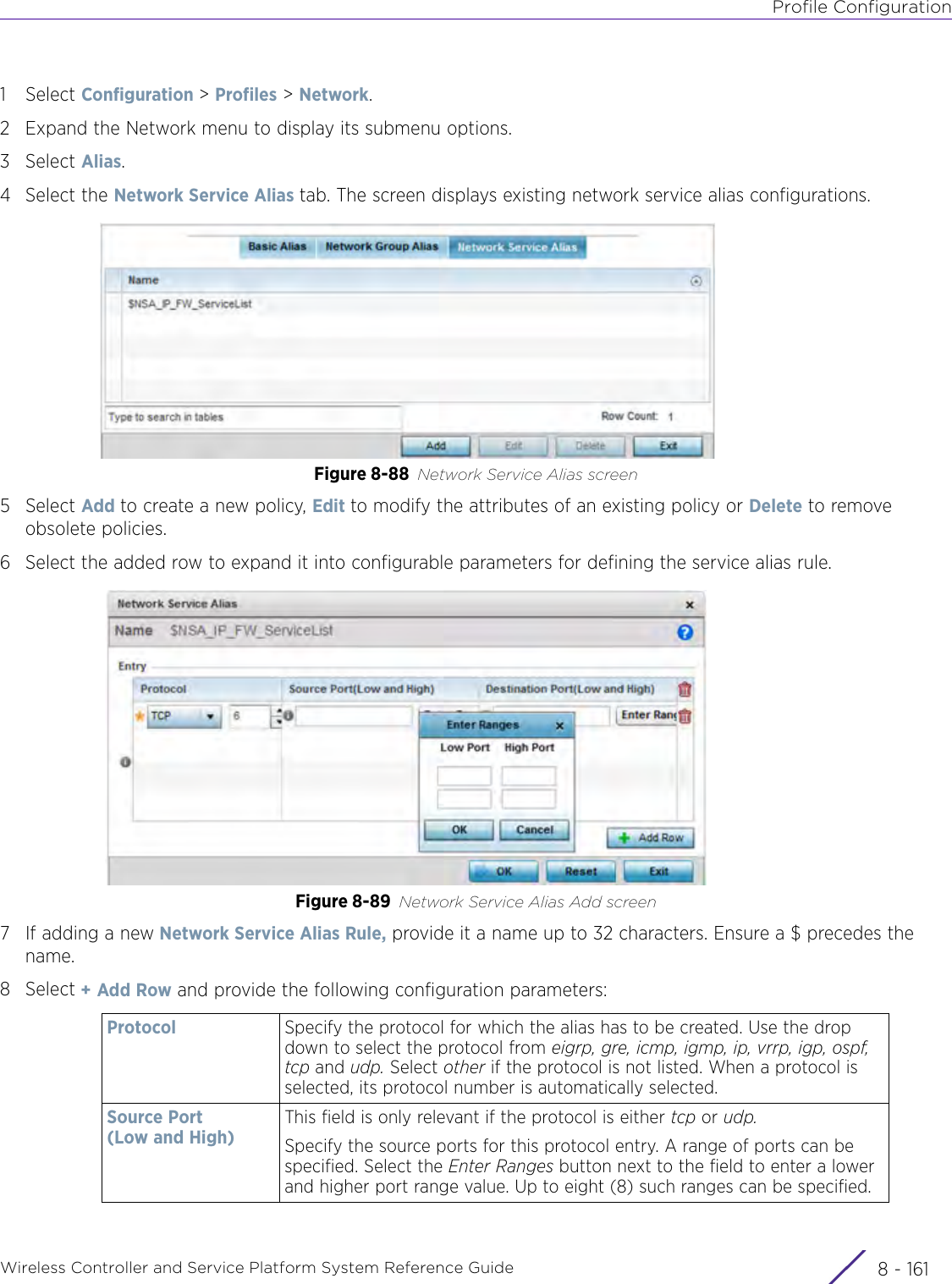
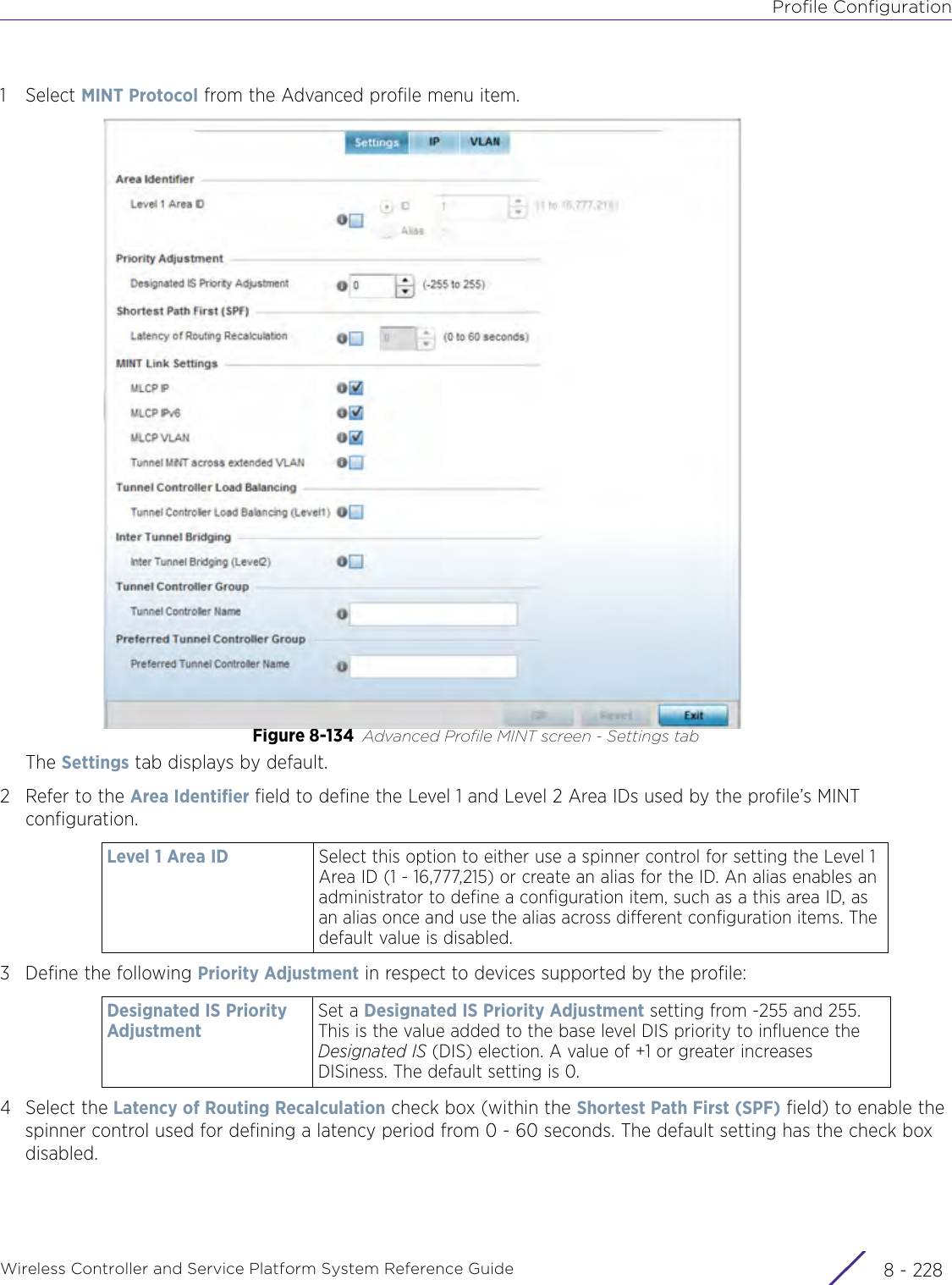
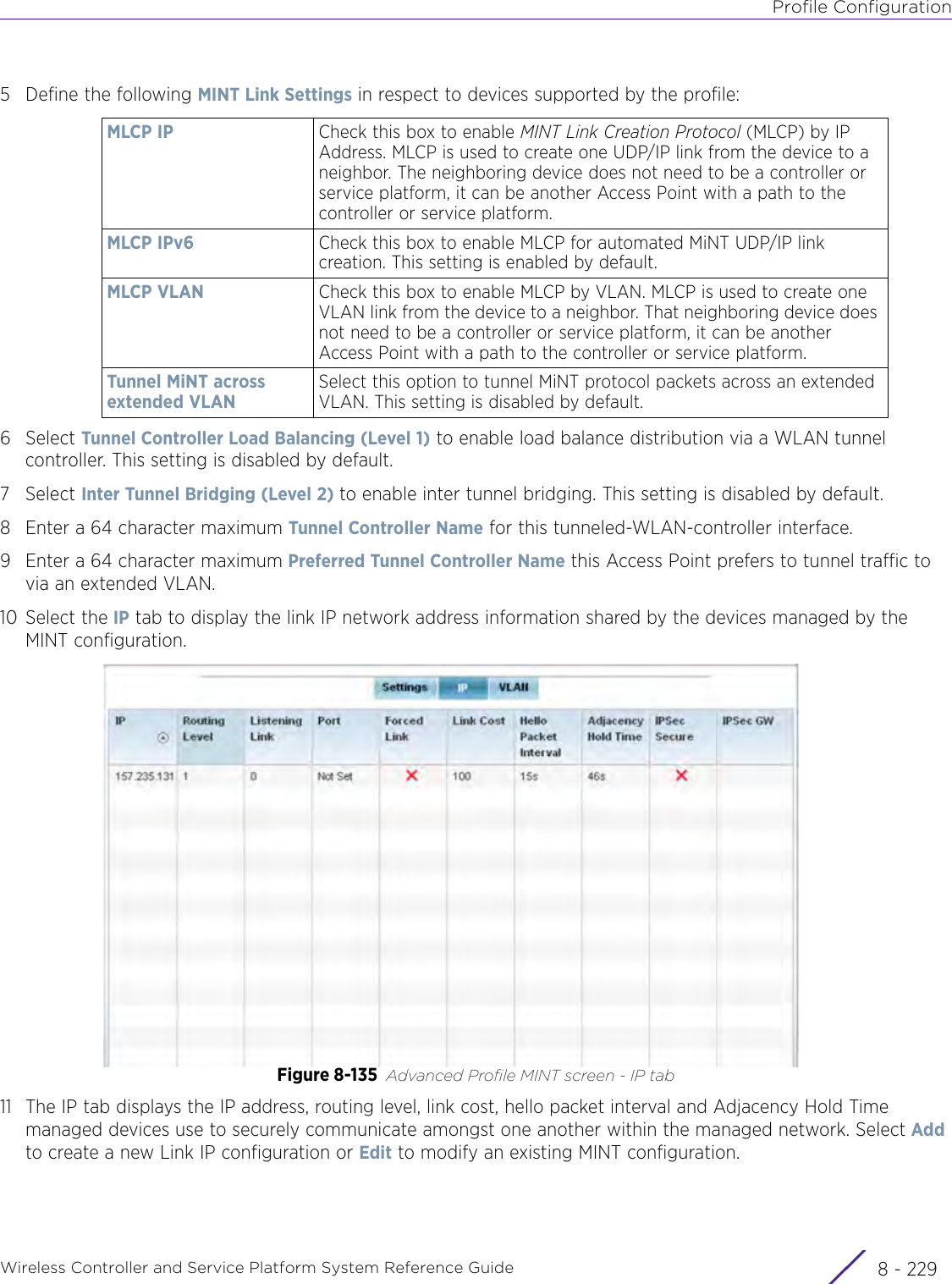
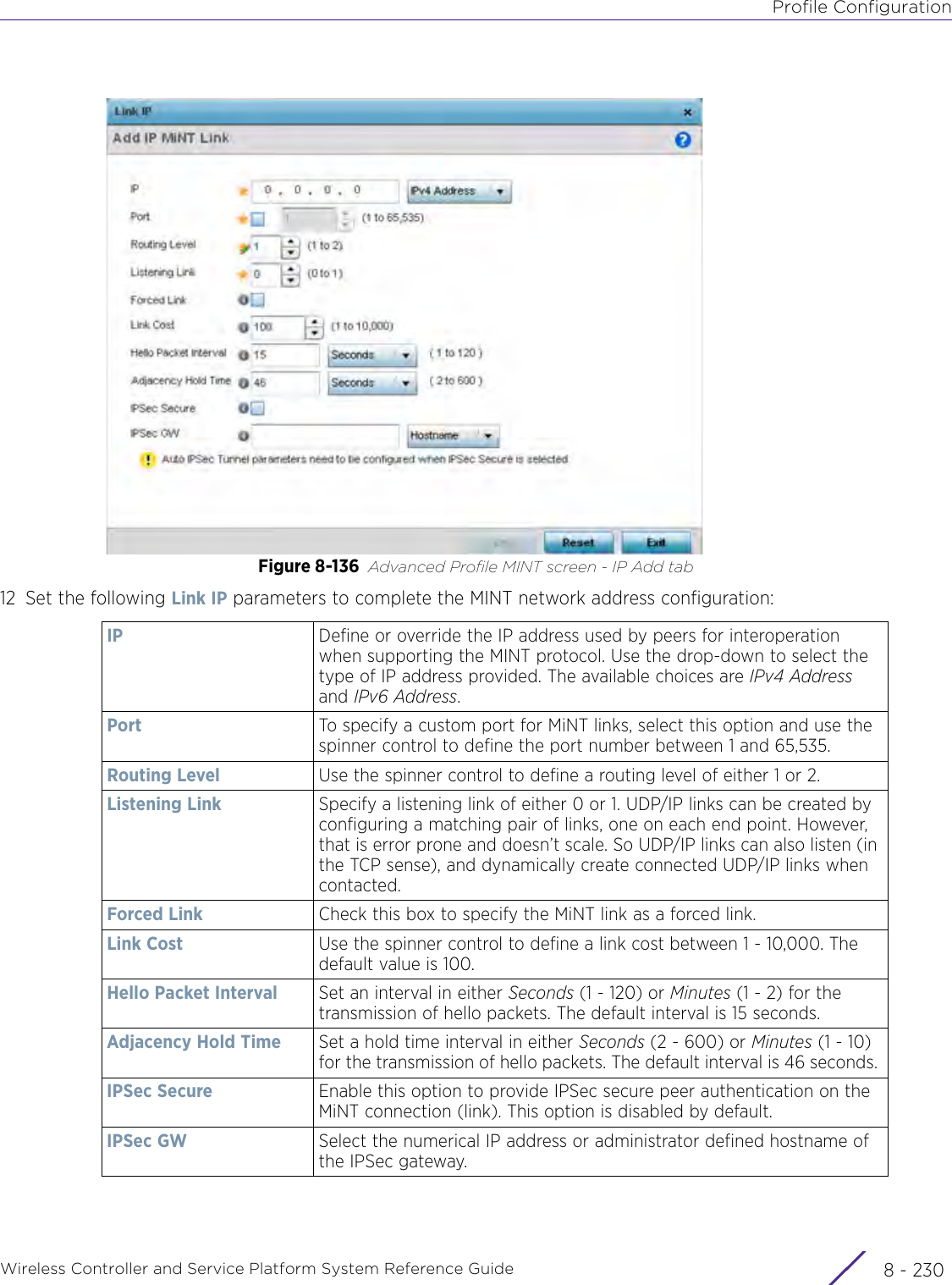
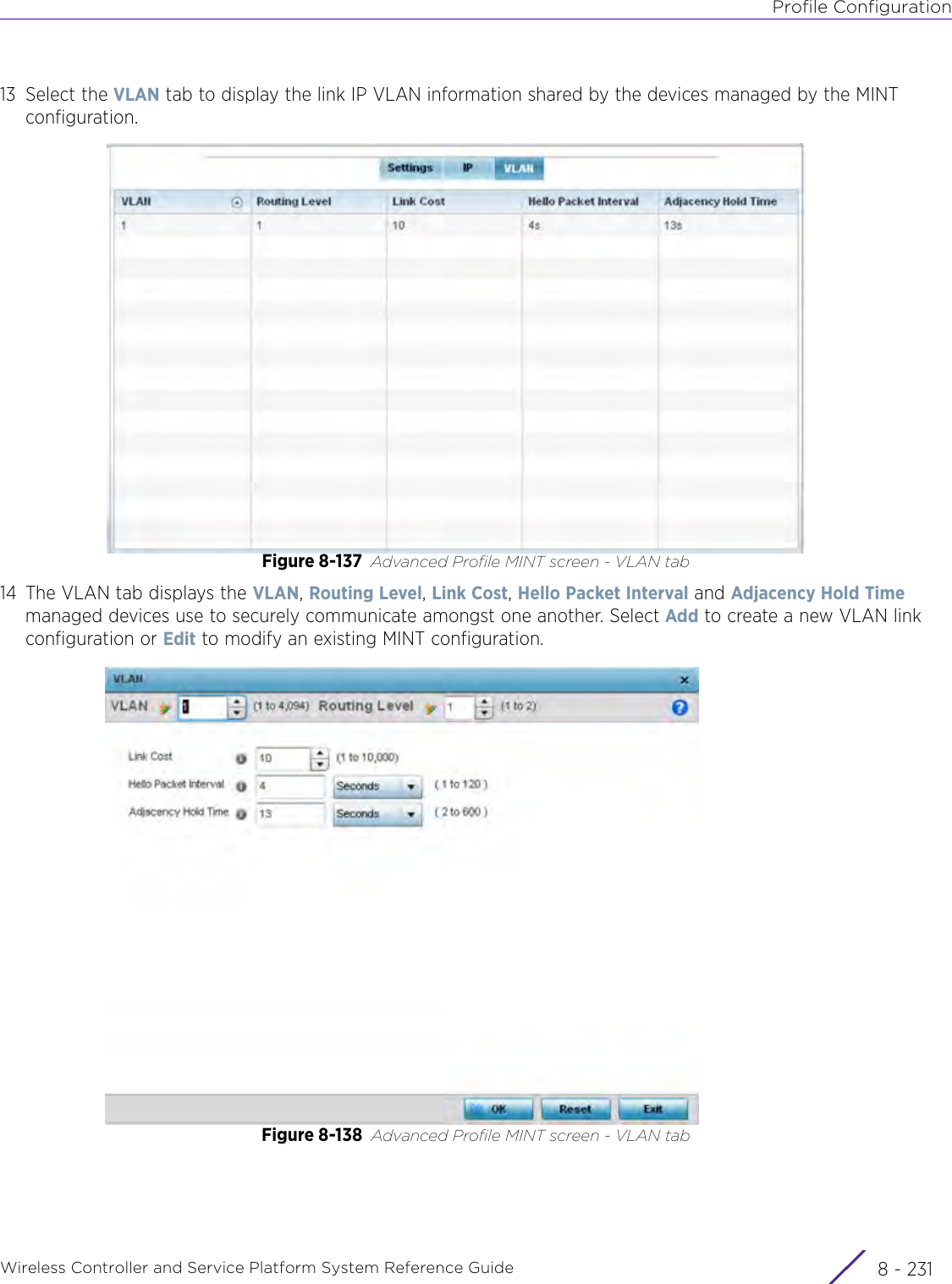
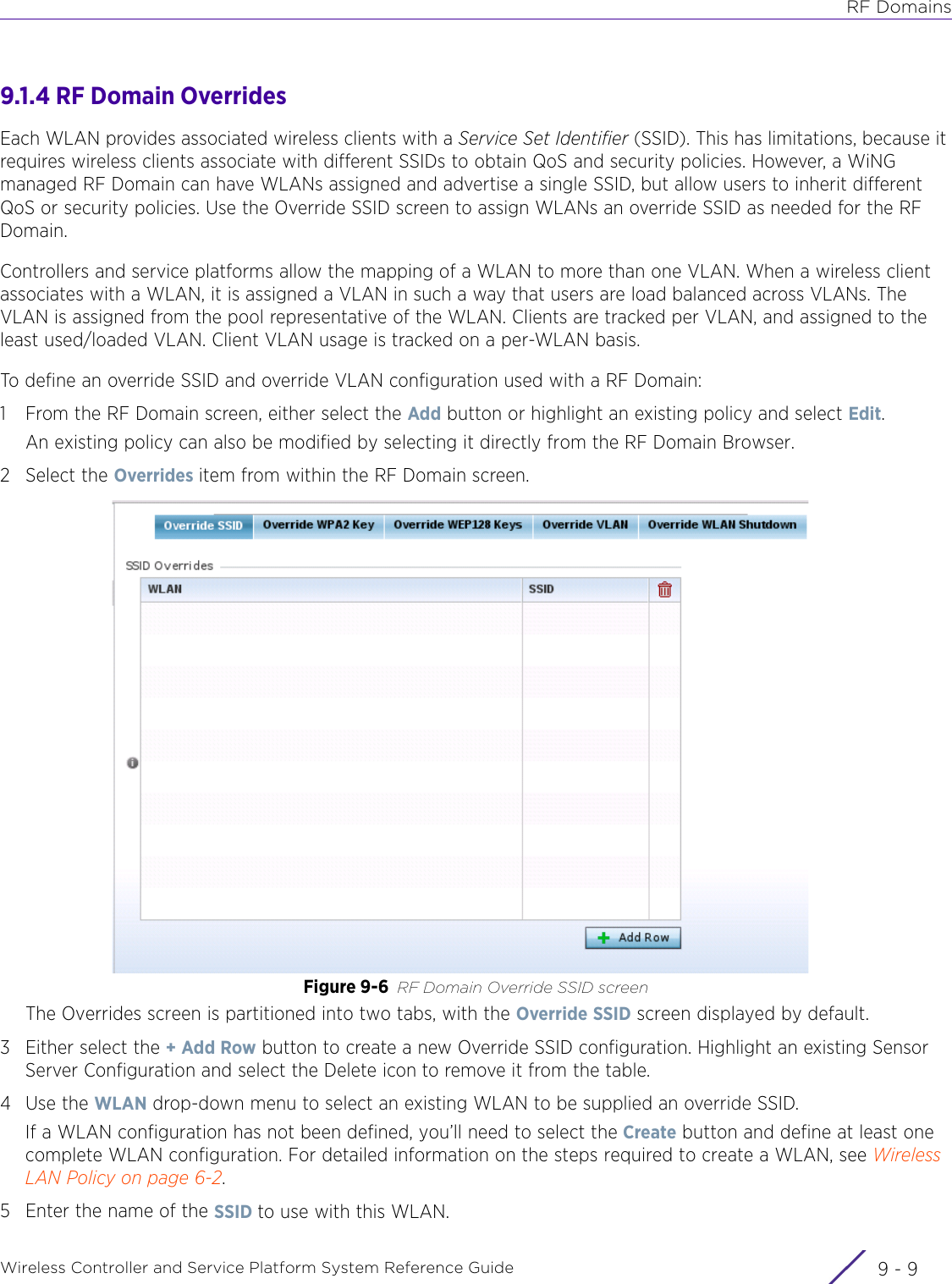
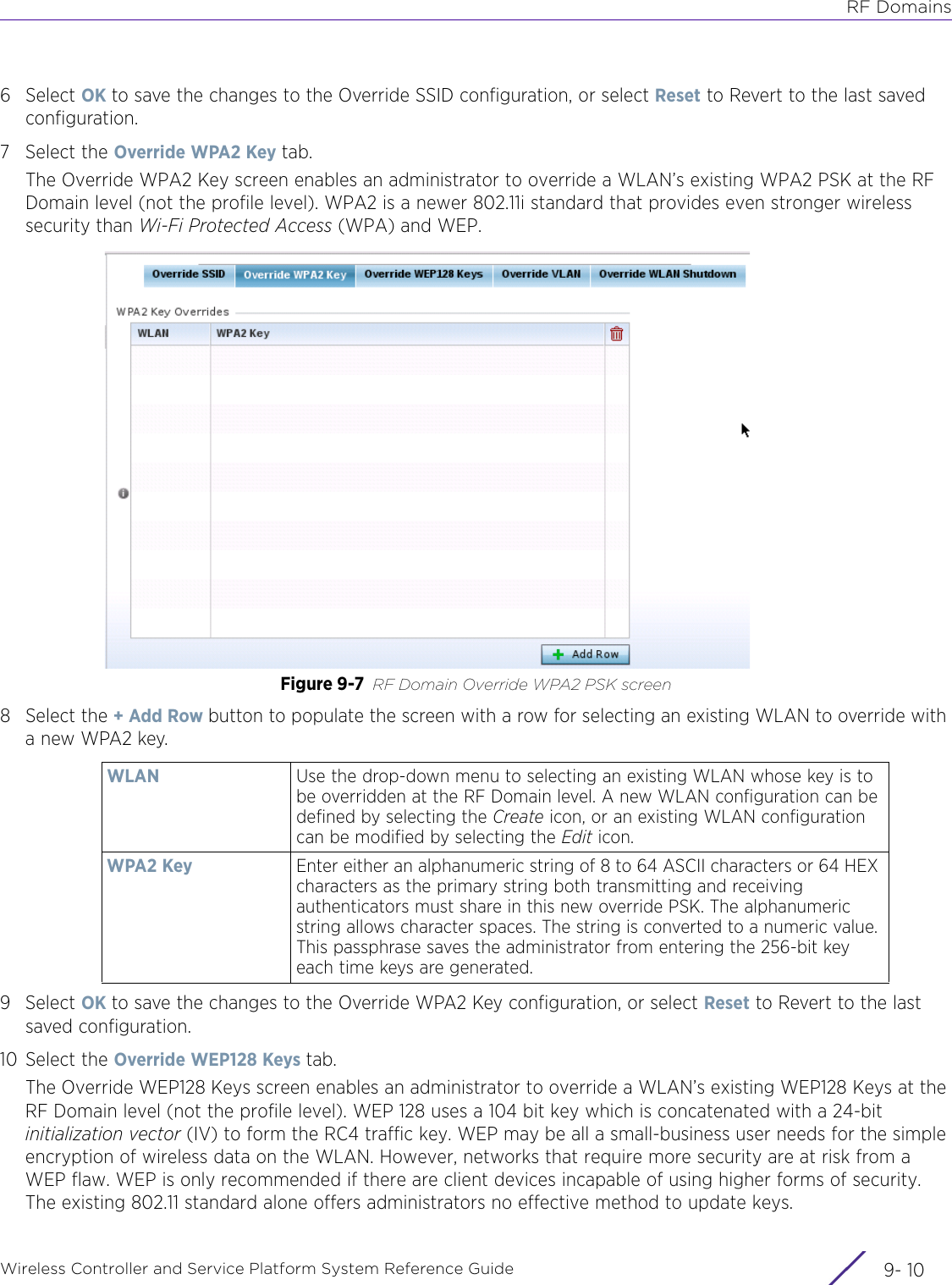
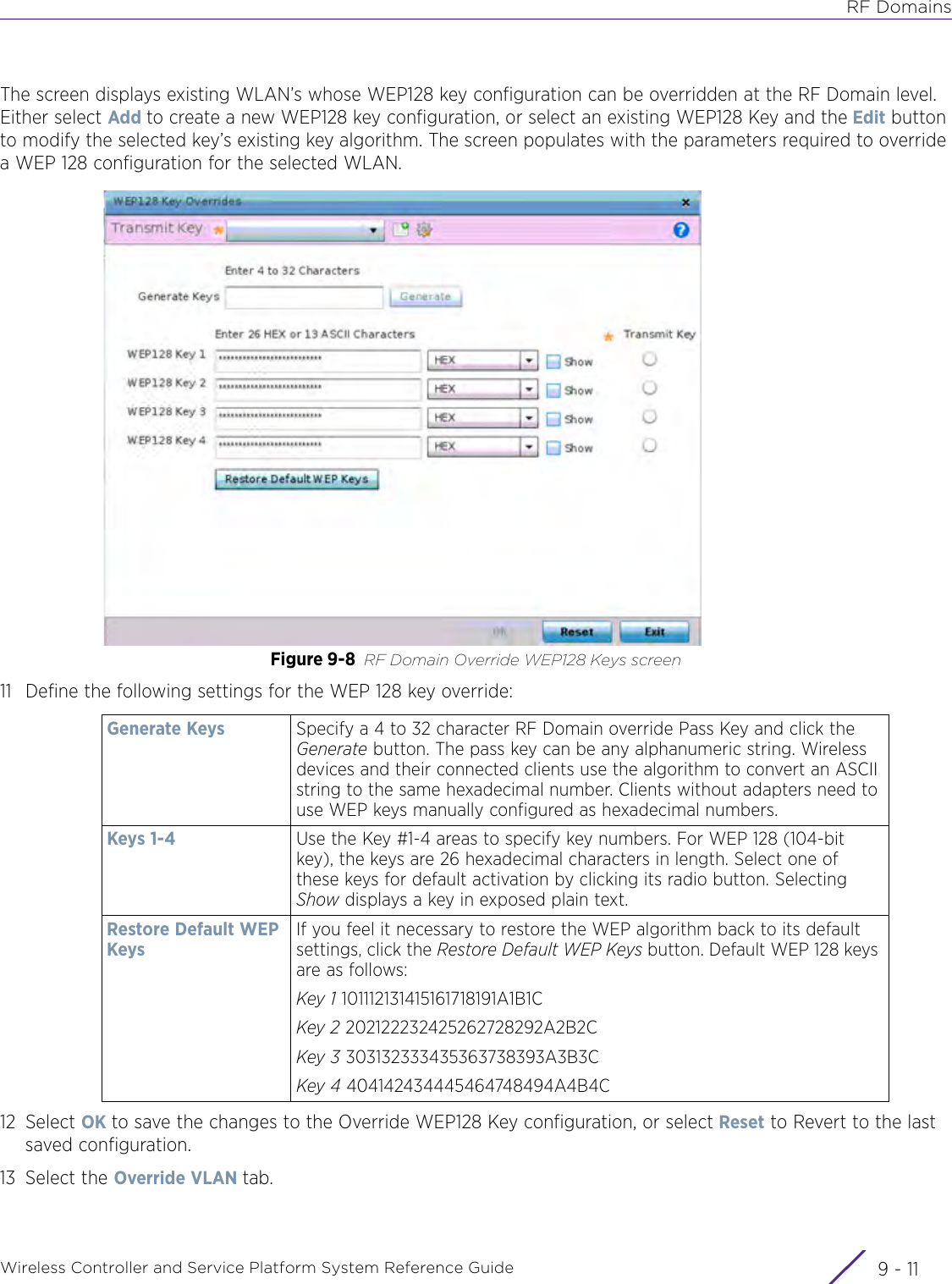
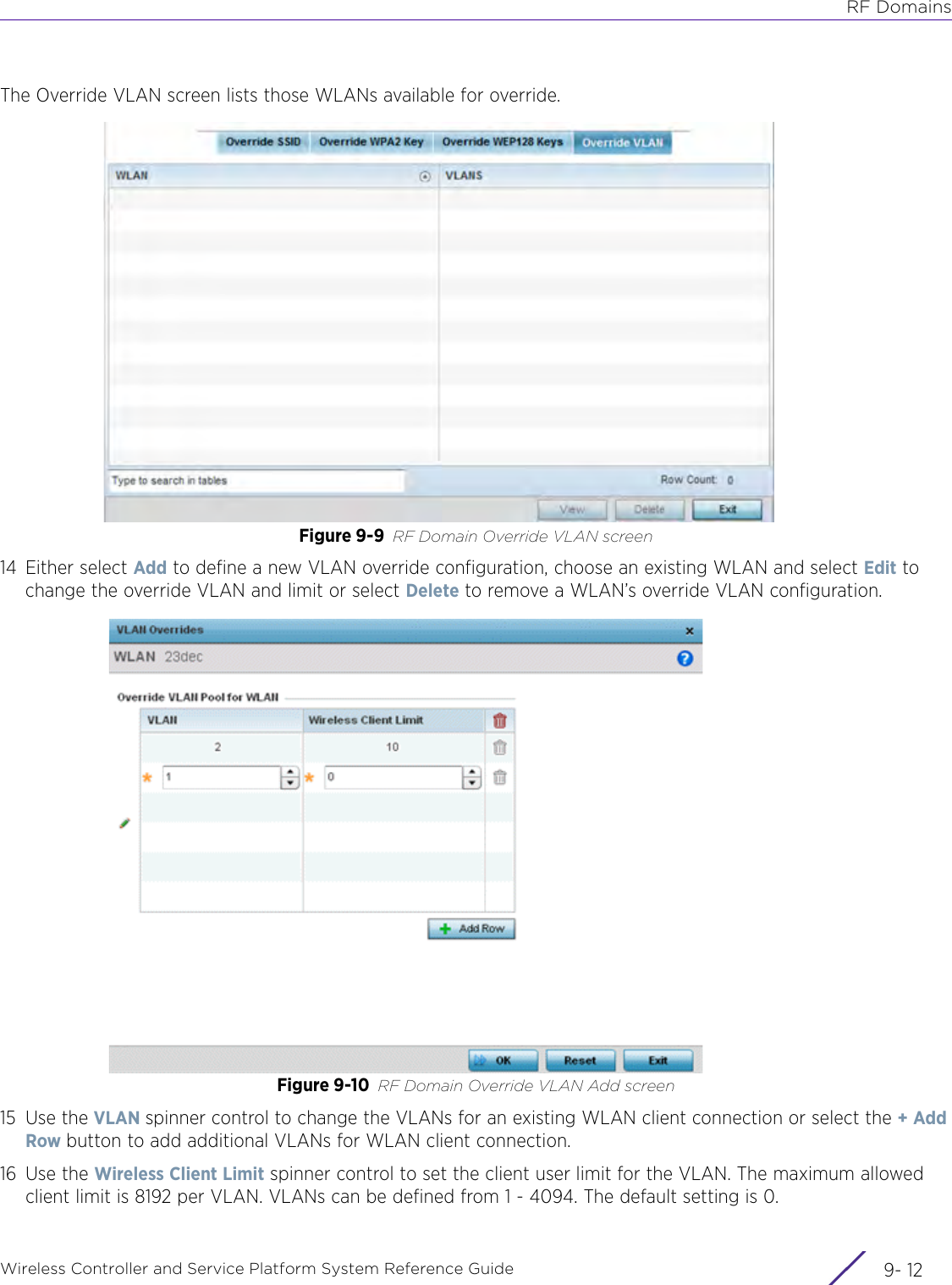
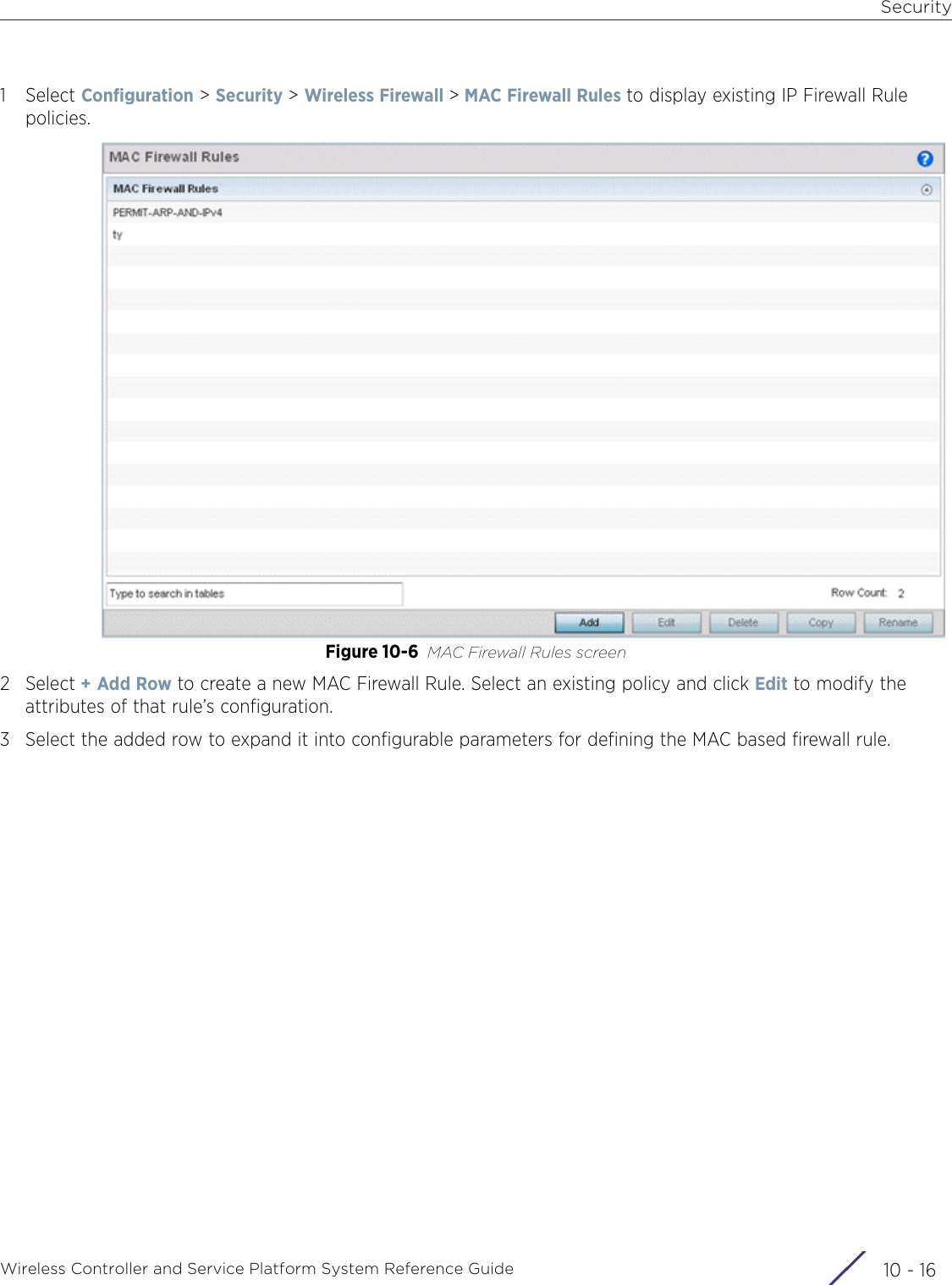
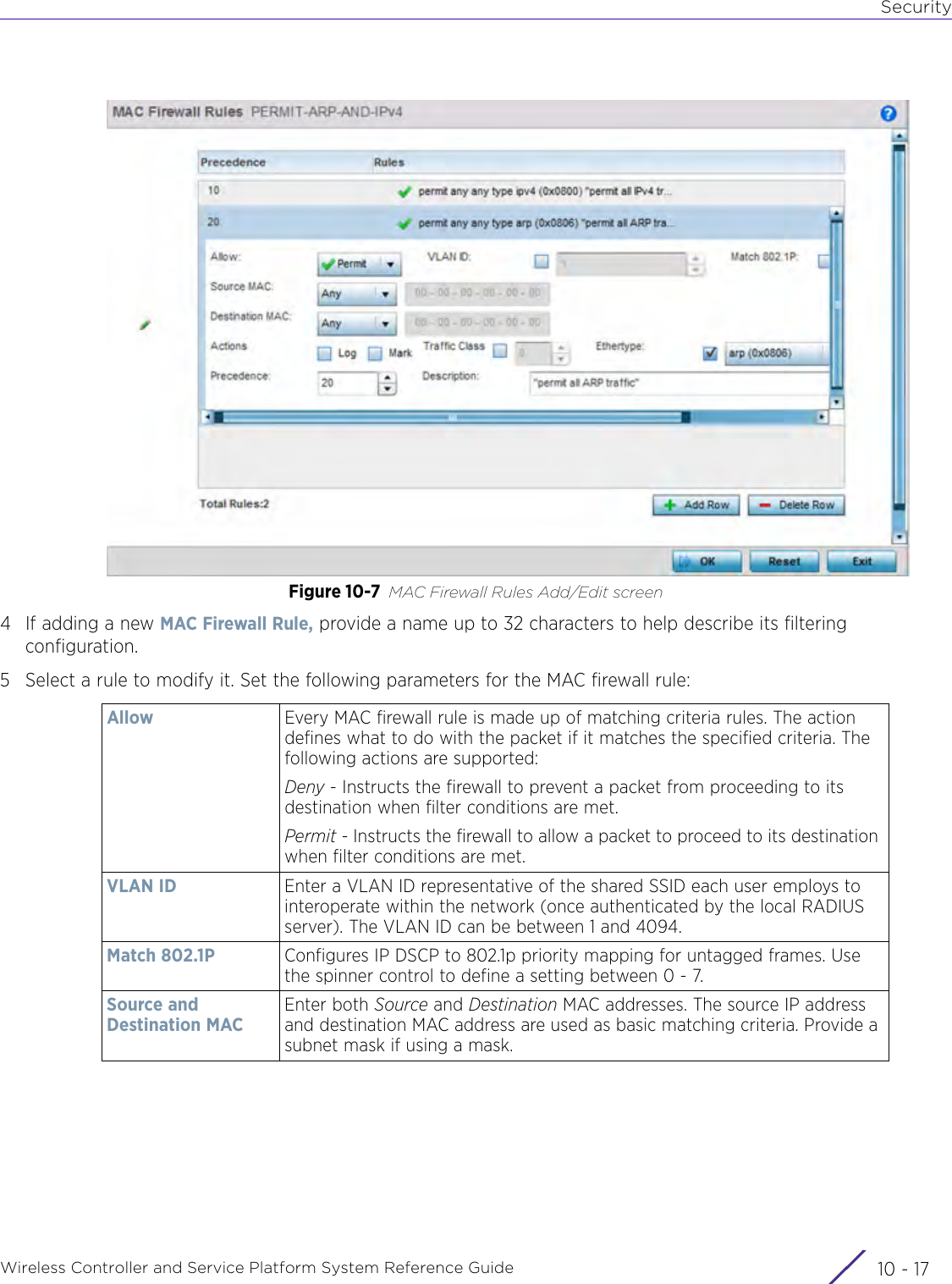
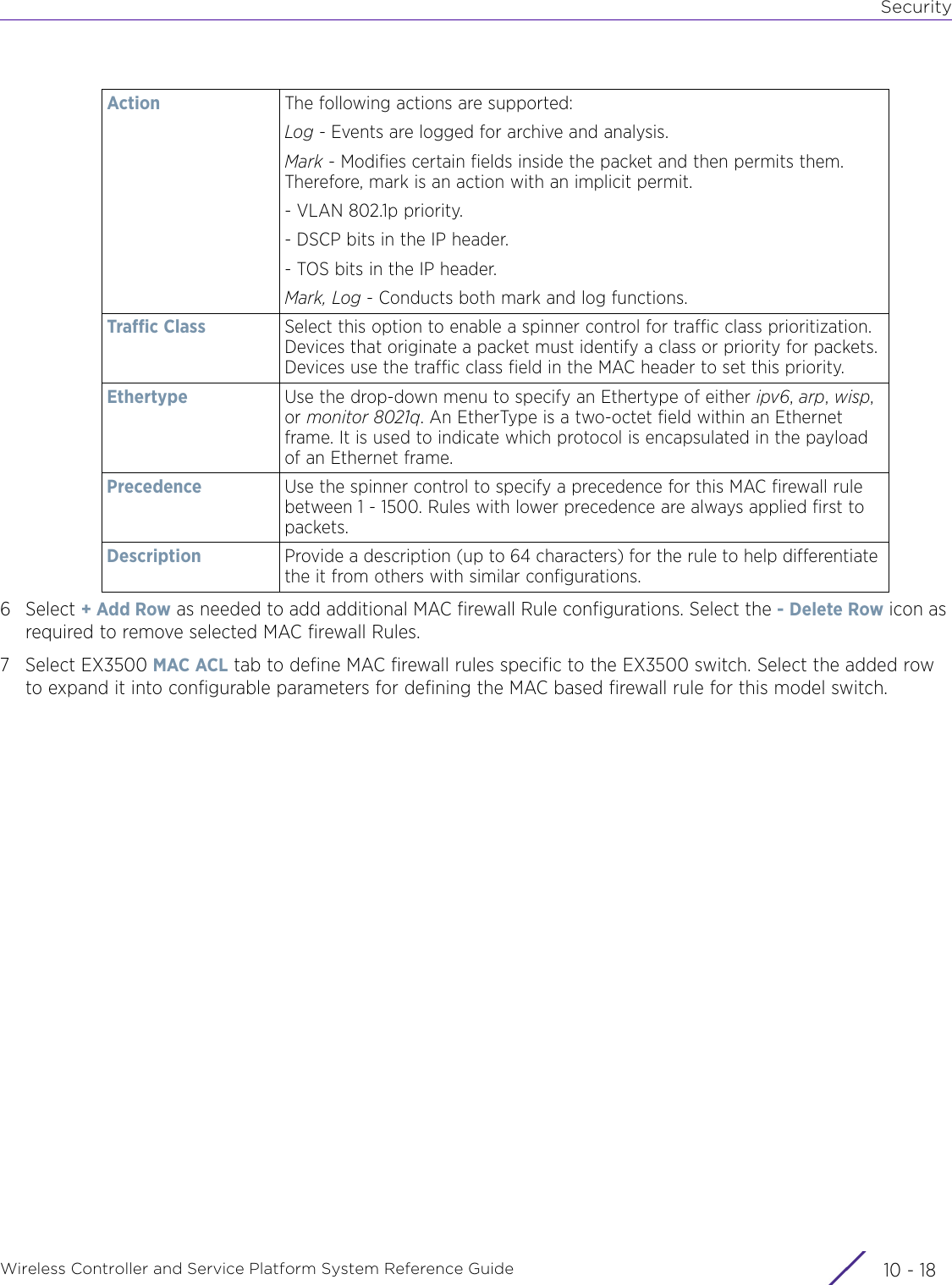
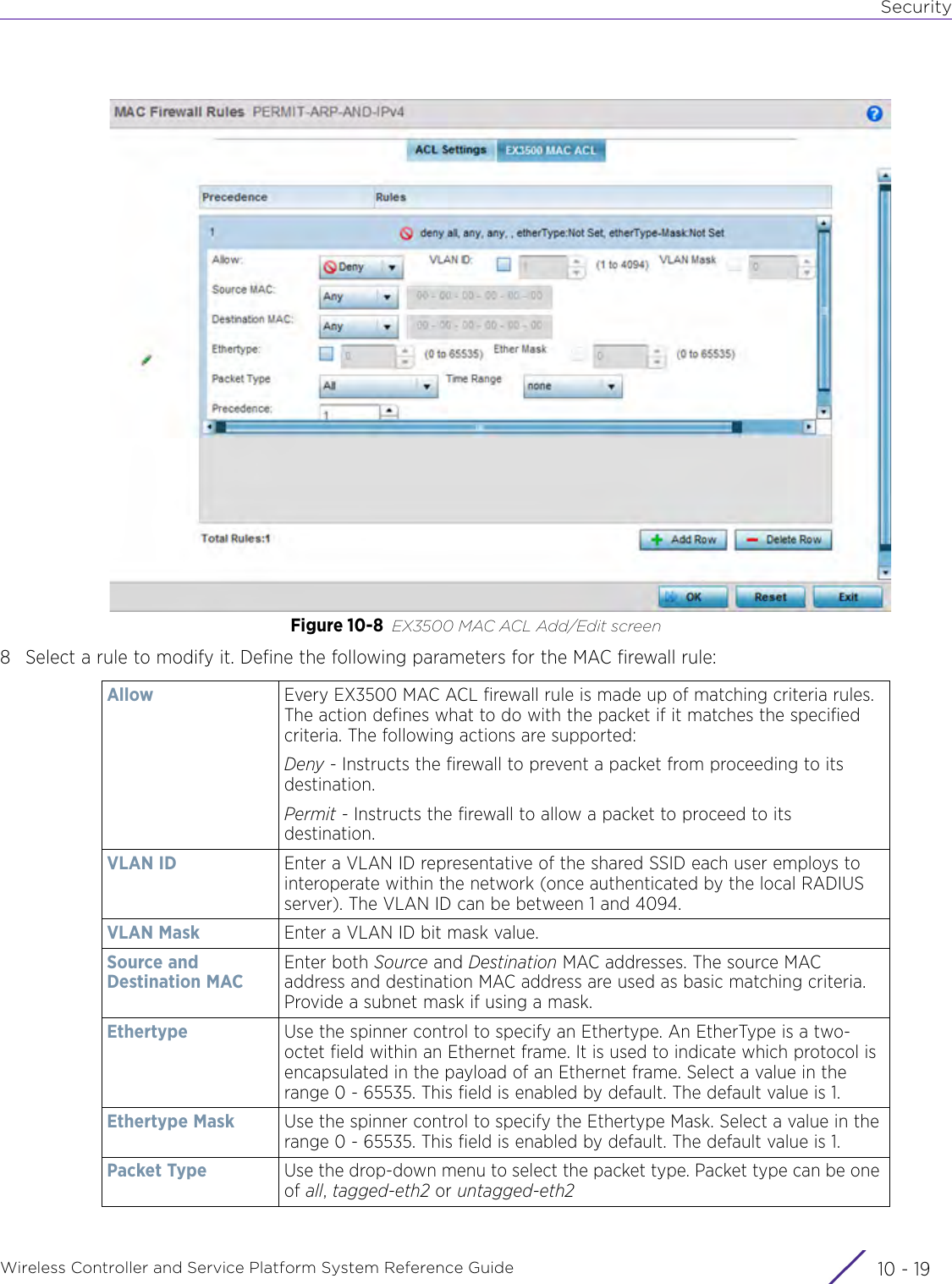
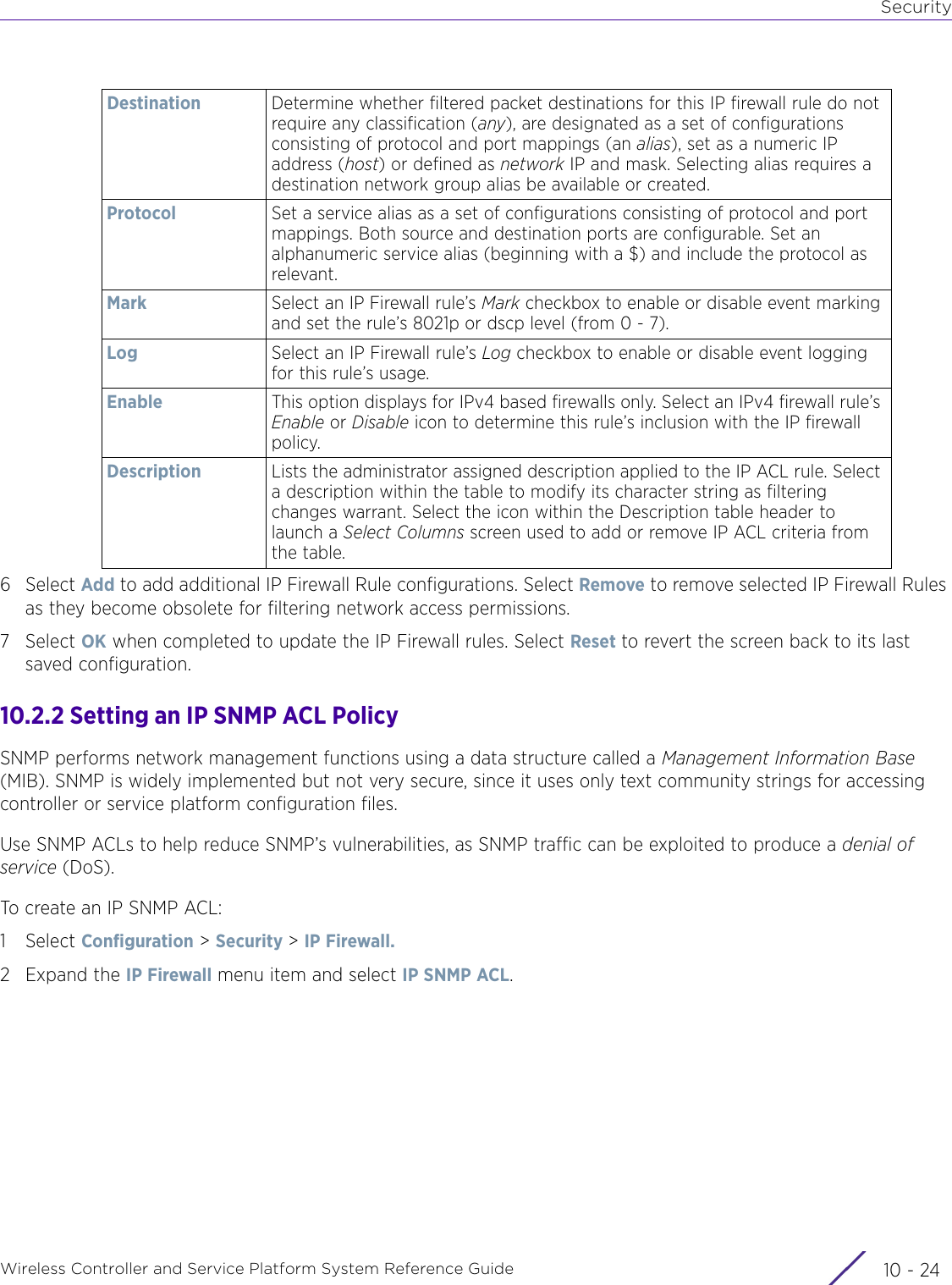
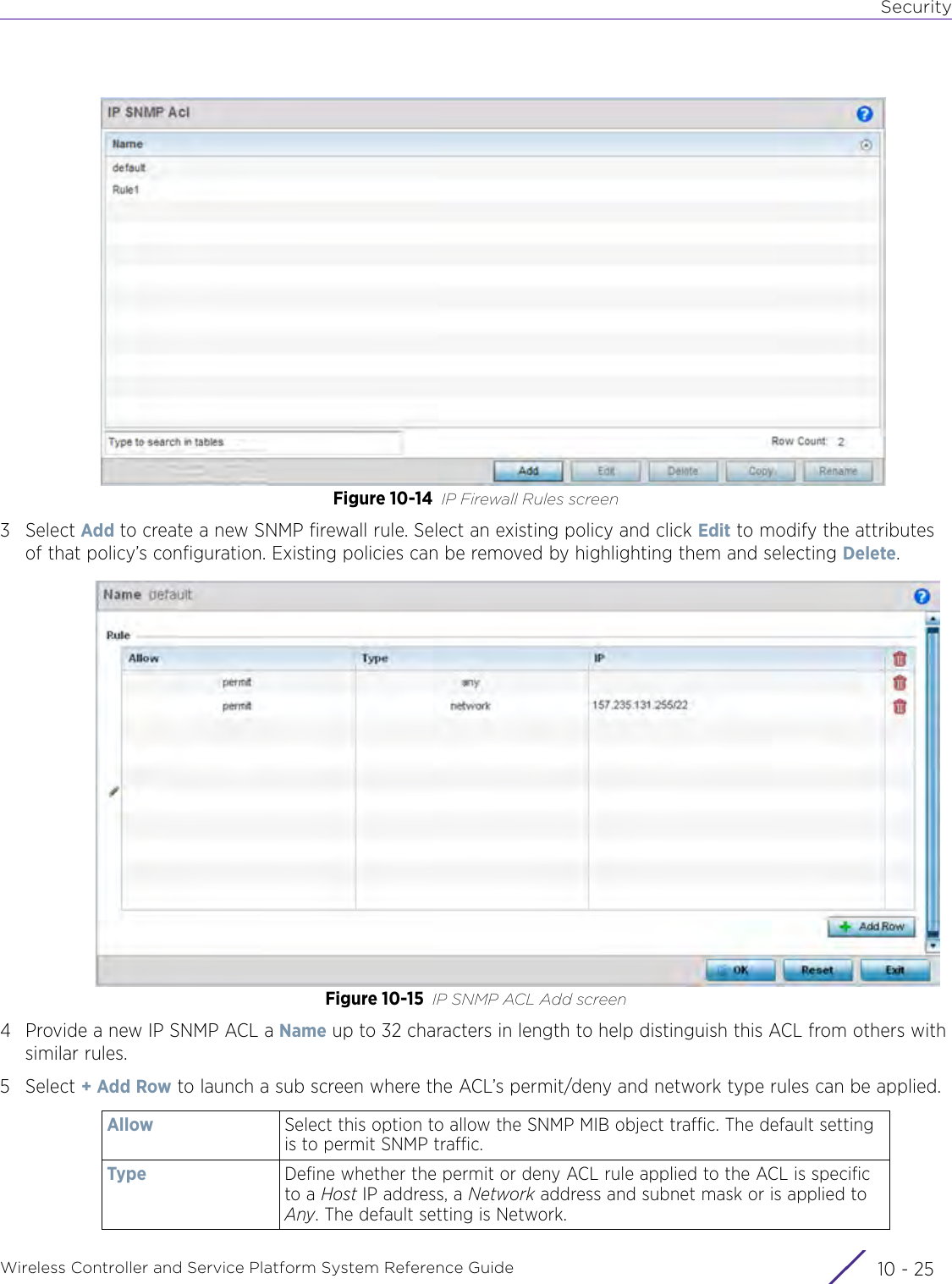
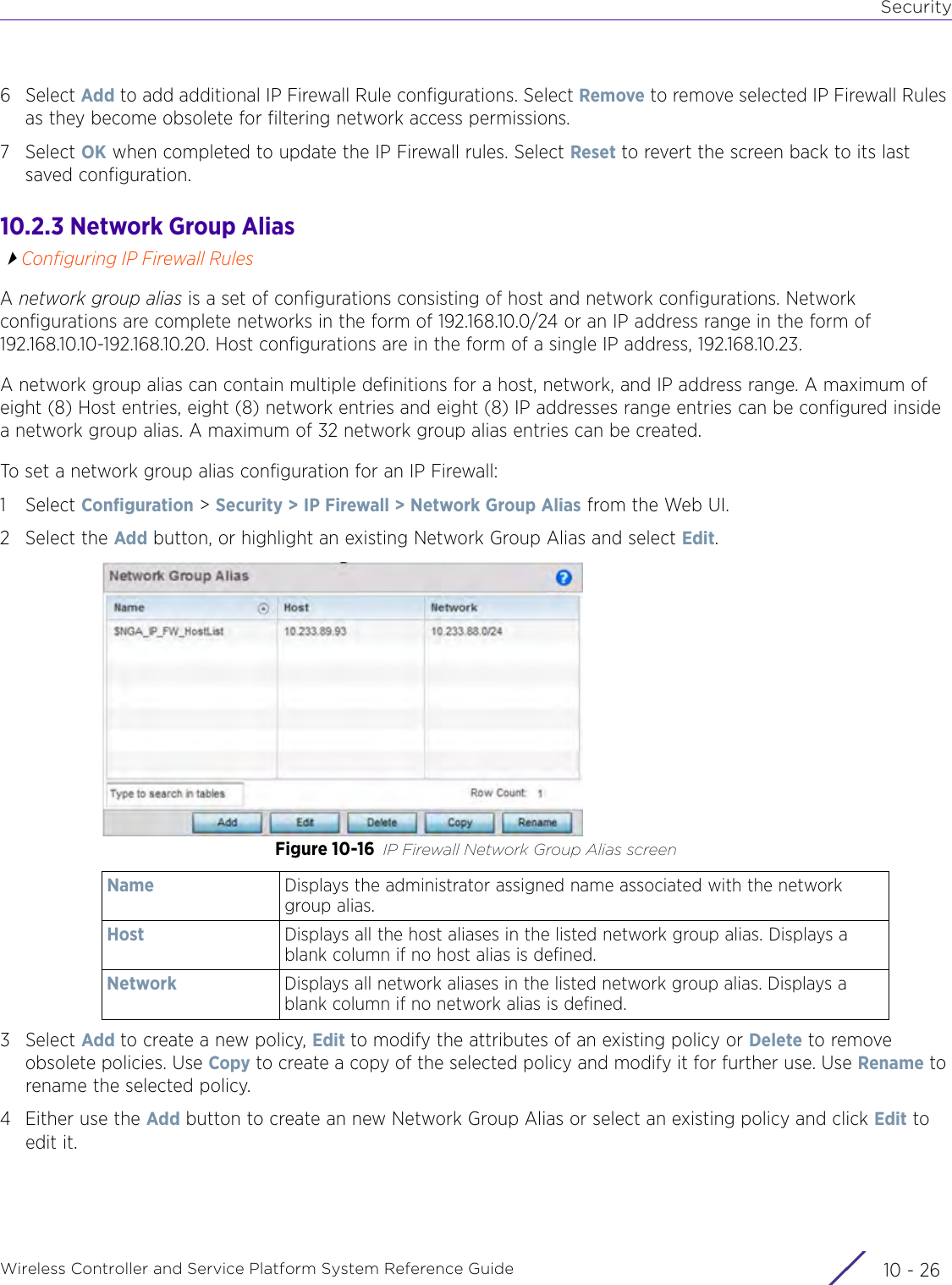
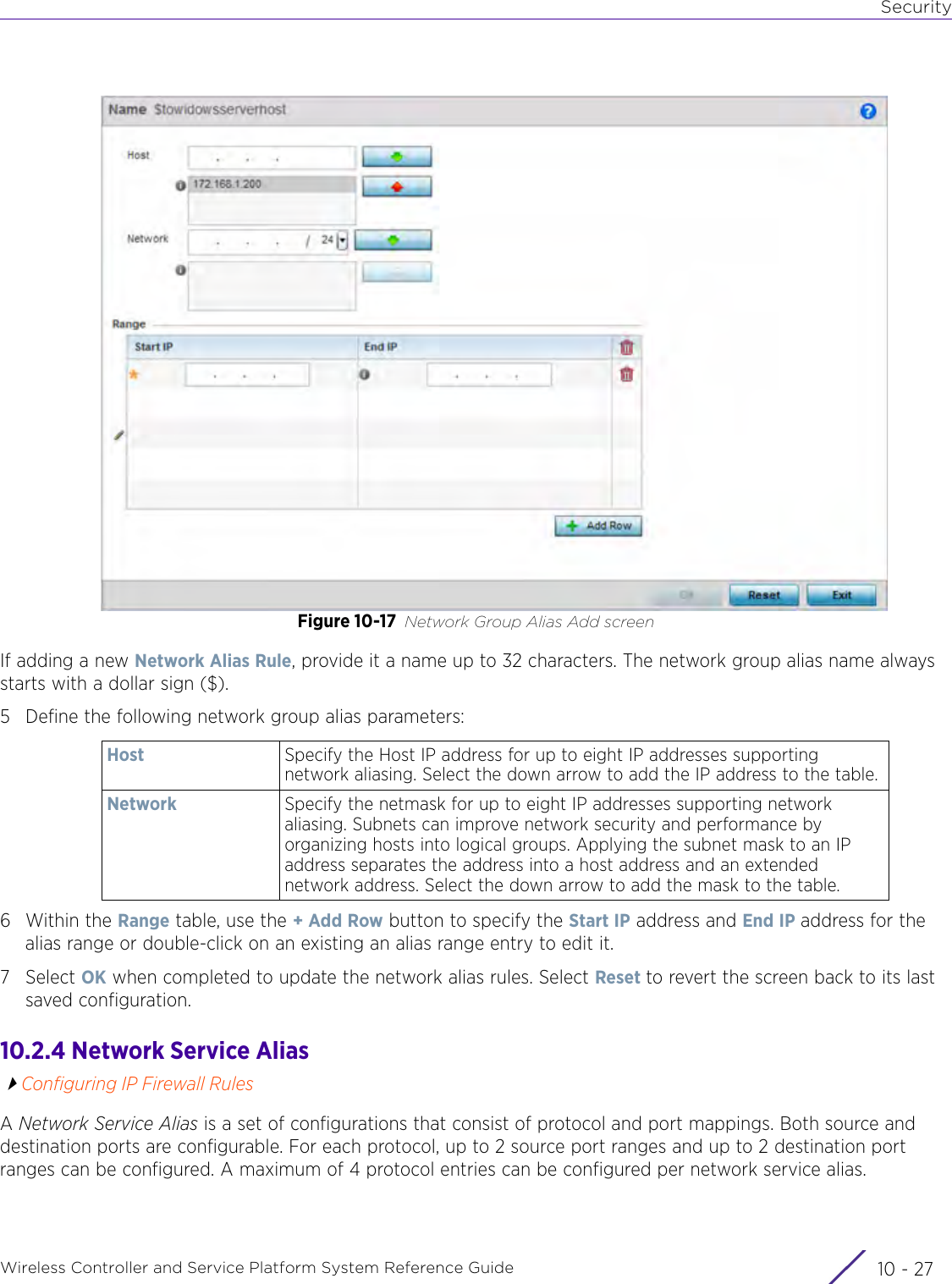
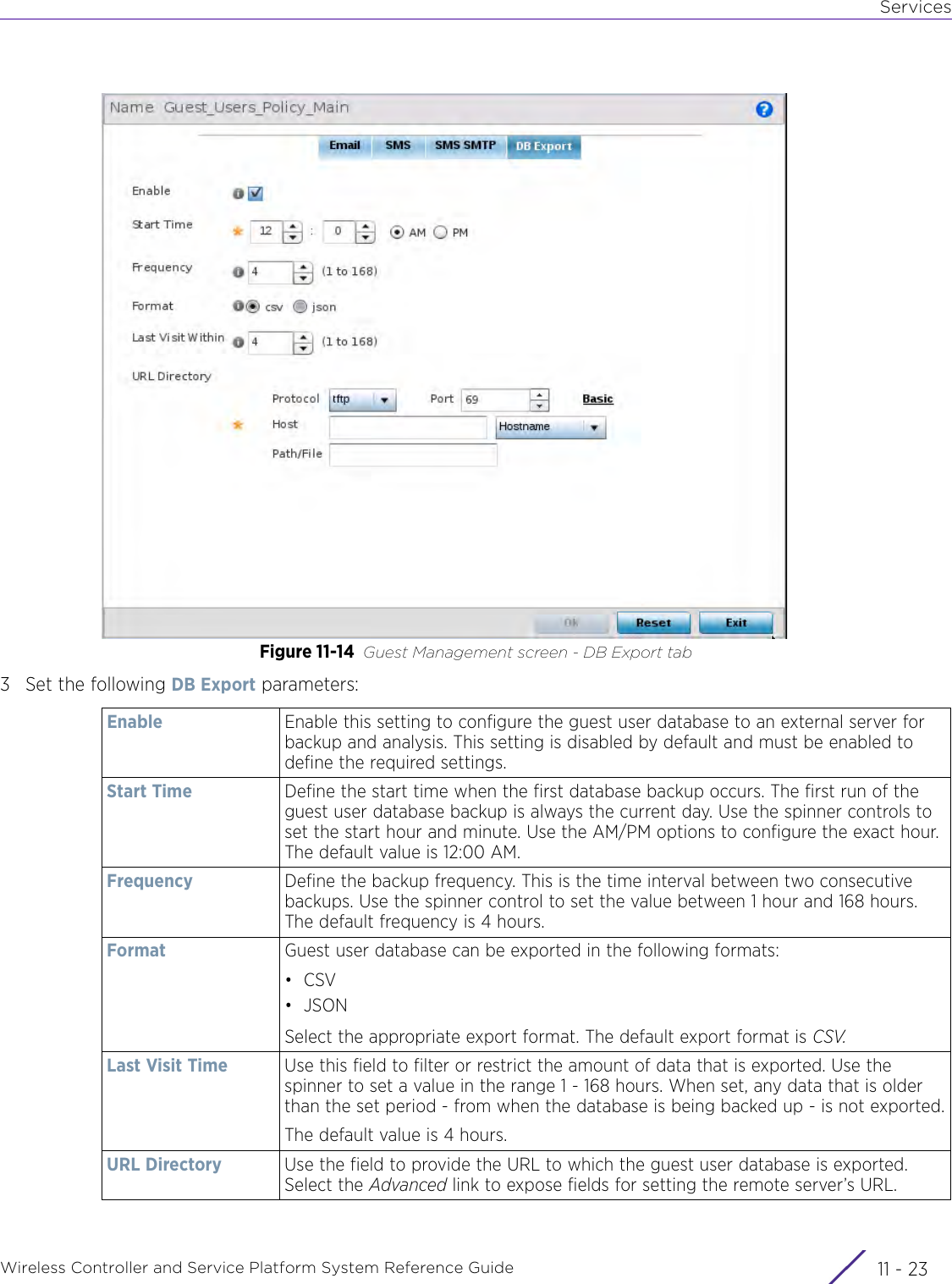
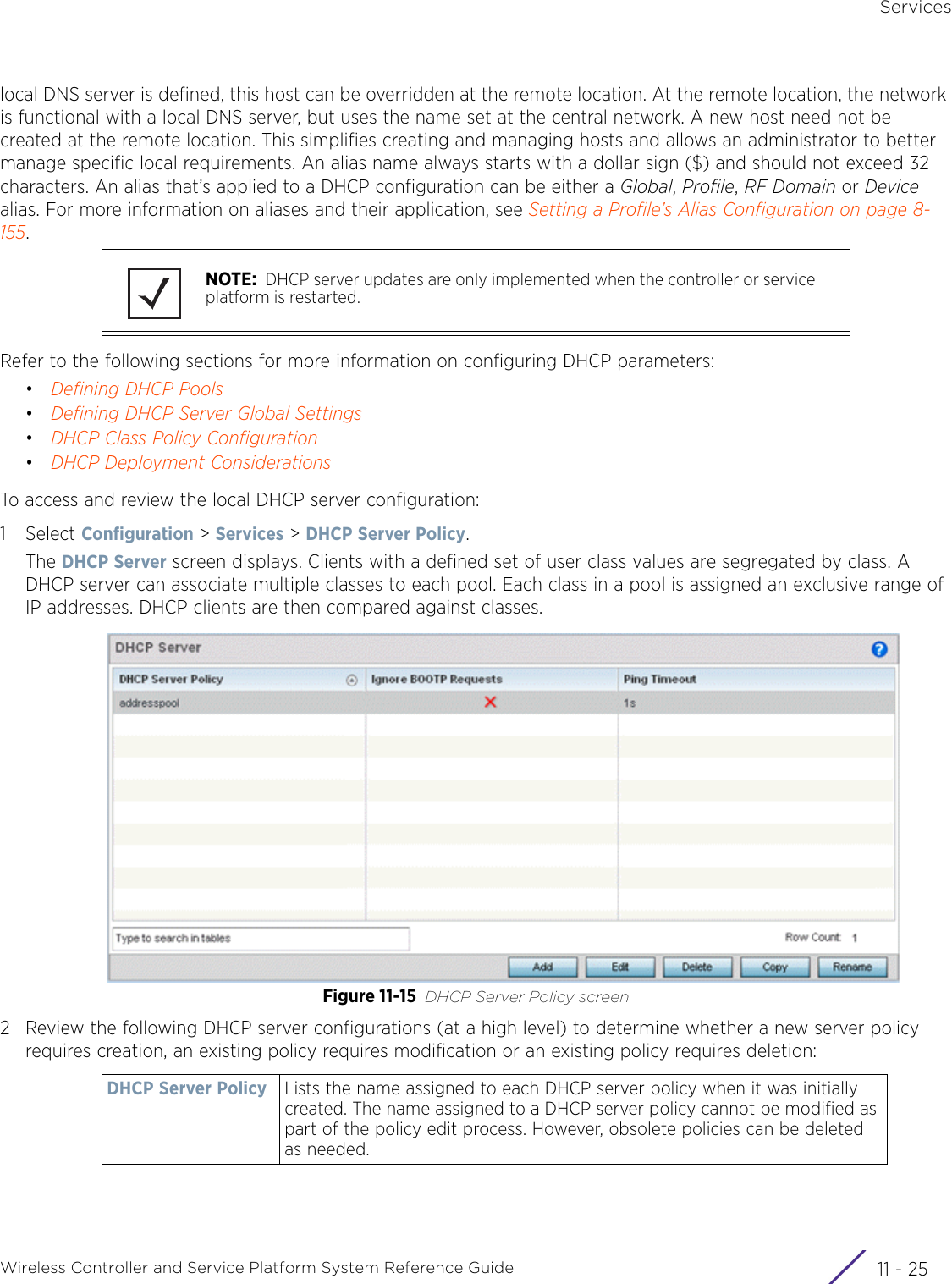
Extreme Networks AP3917E Wireless 802.11 a/ac+b/g/n Access Point User Manual WiNG 5 9 1 System Reference Guide Part 2
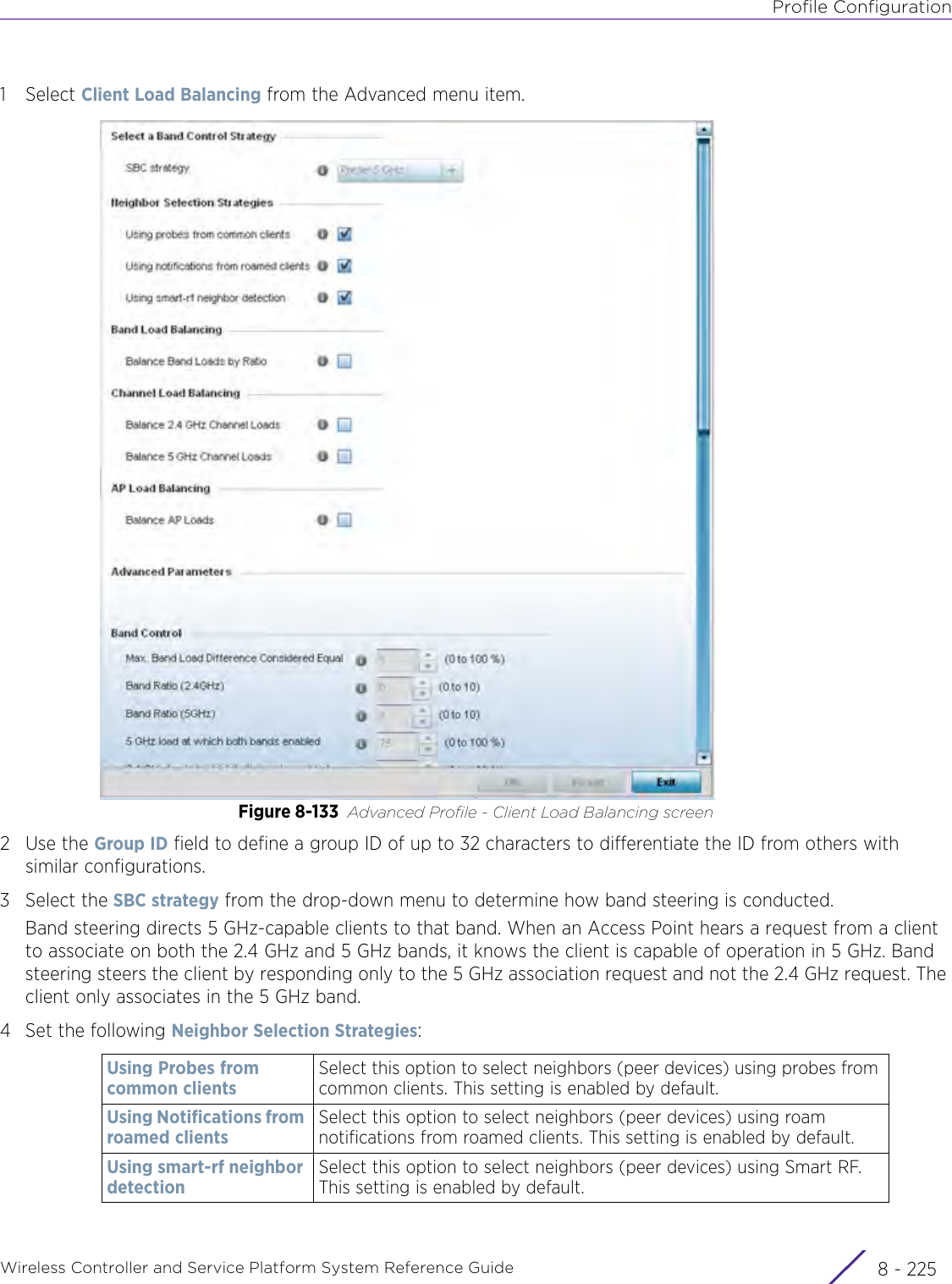
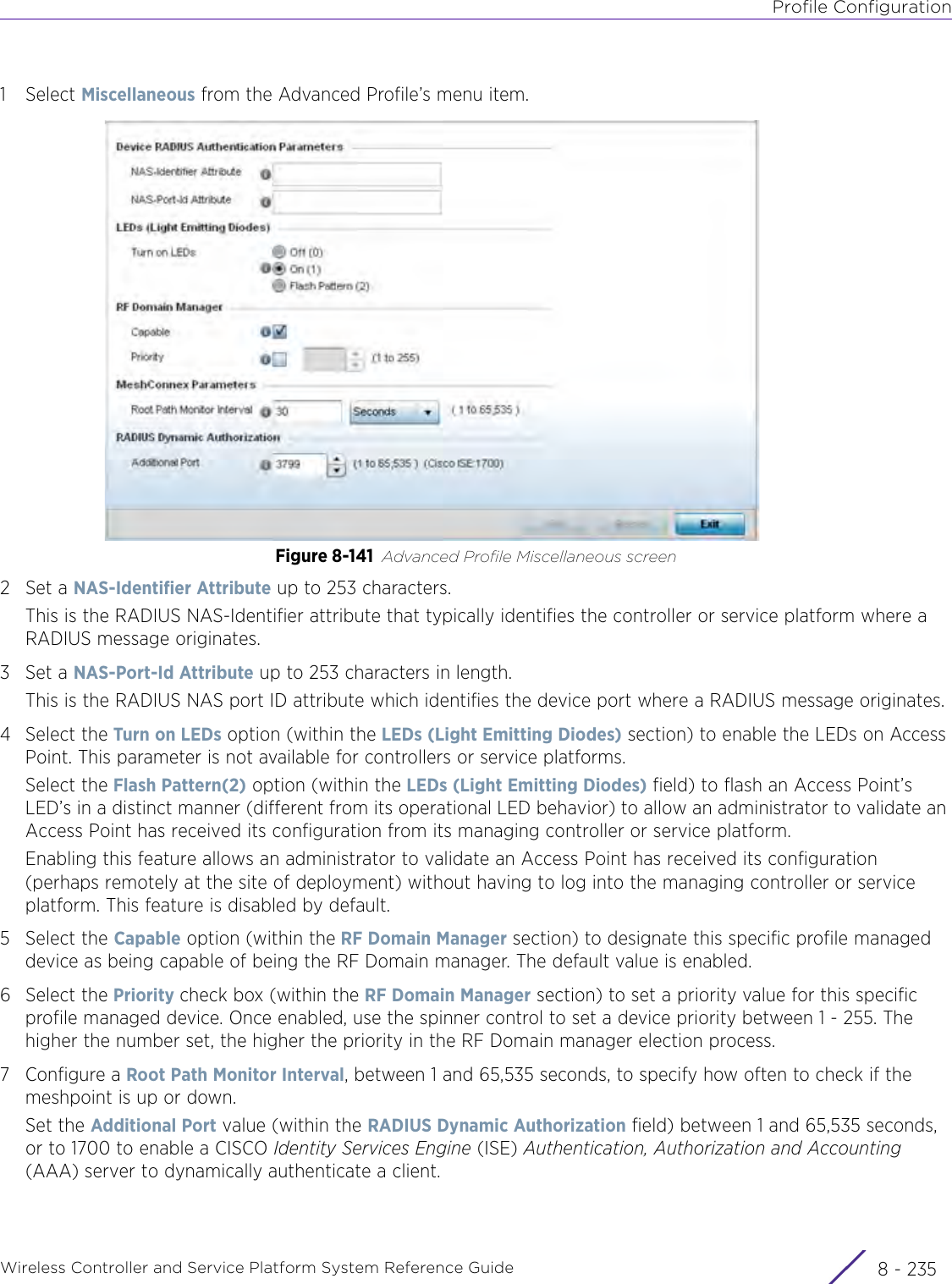
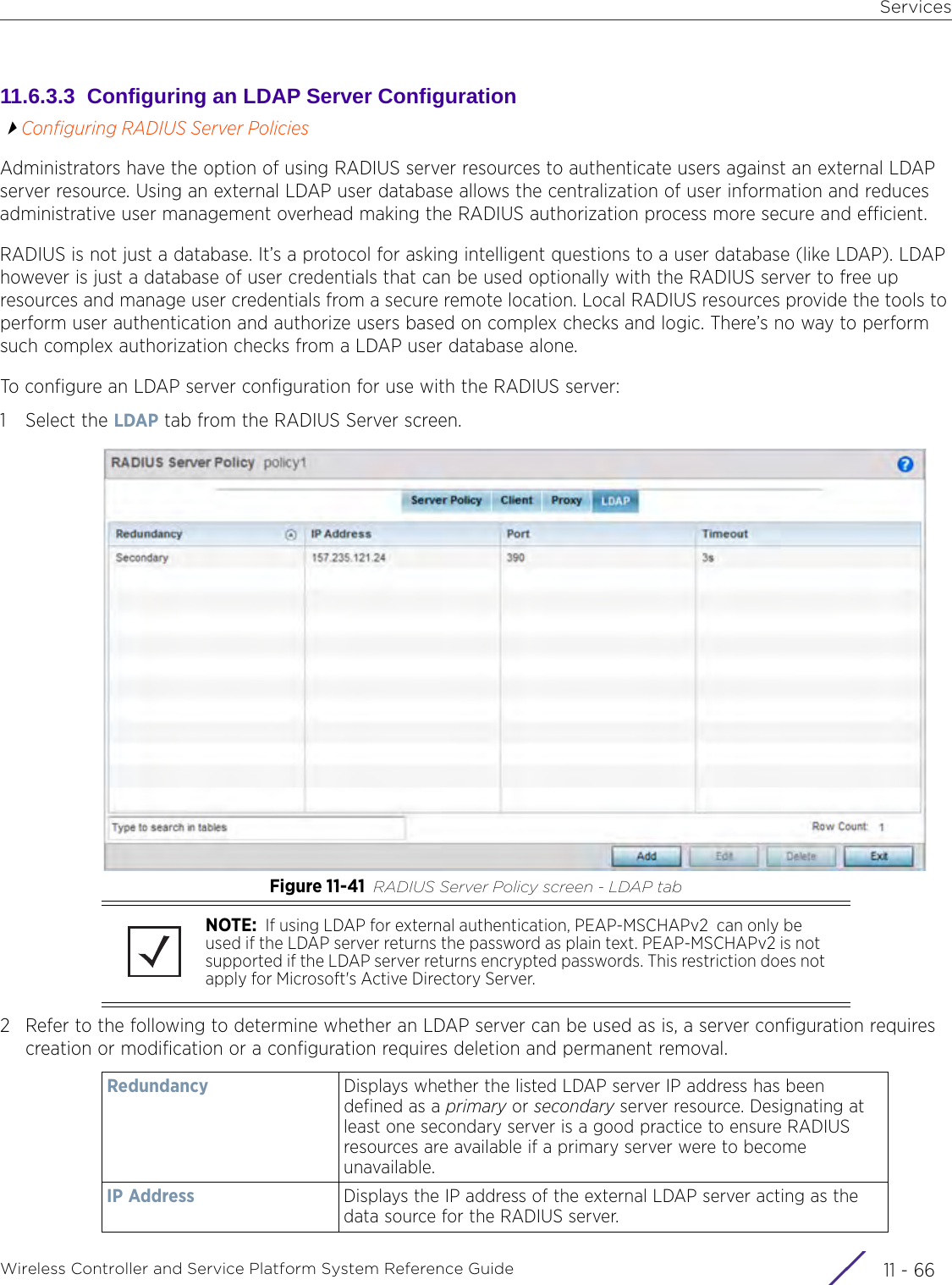
Extreme Networks, Inc. Wireless 802.11 a/ac+b/g/n Access Point WiNG 5 9 1 System Reference Guide Part 2
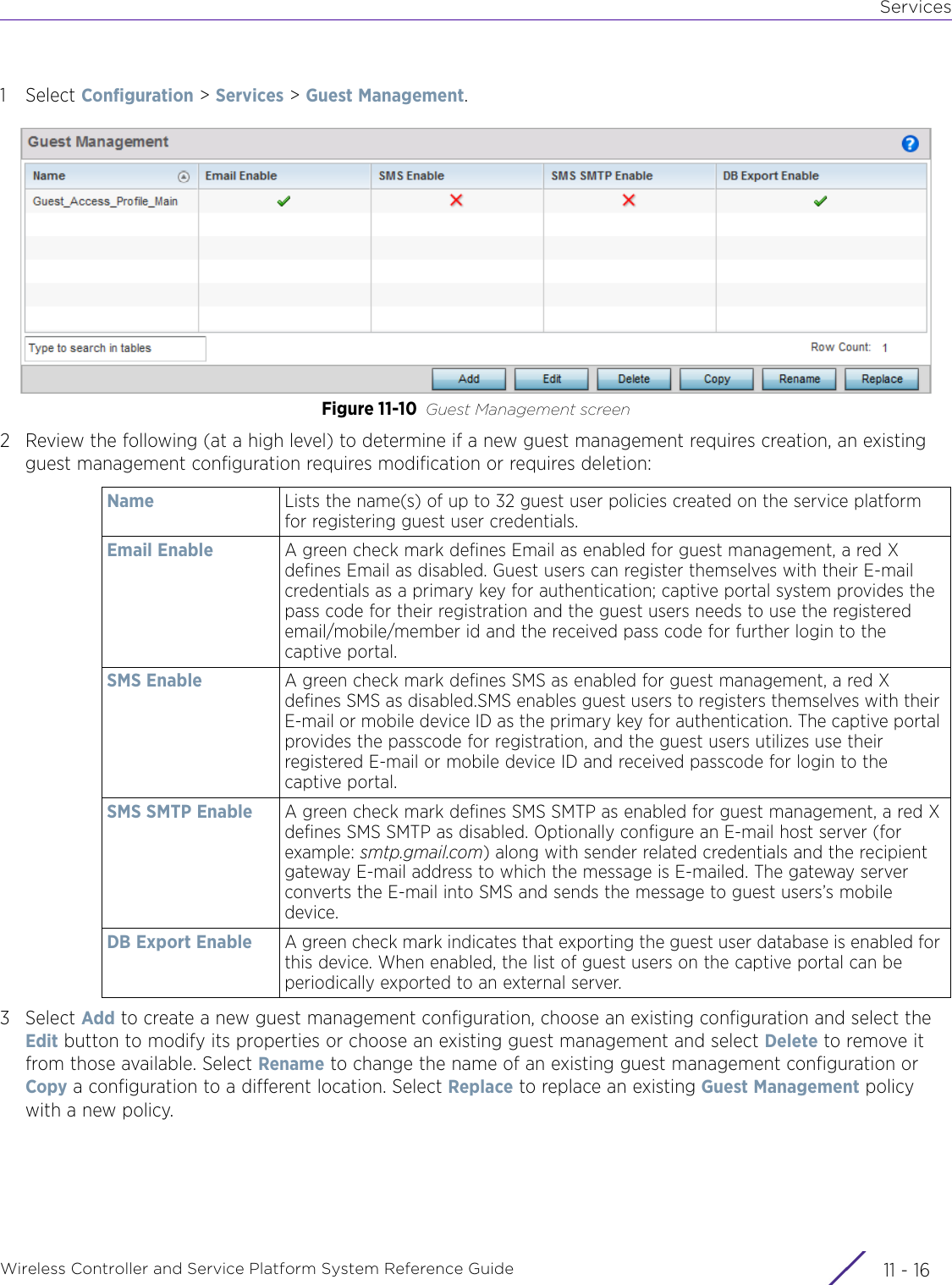
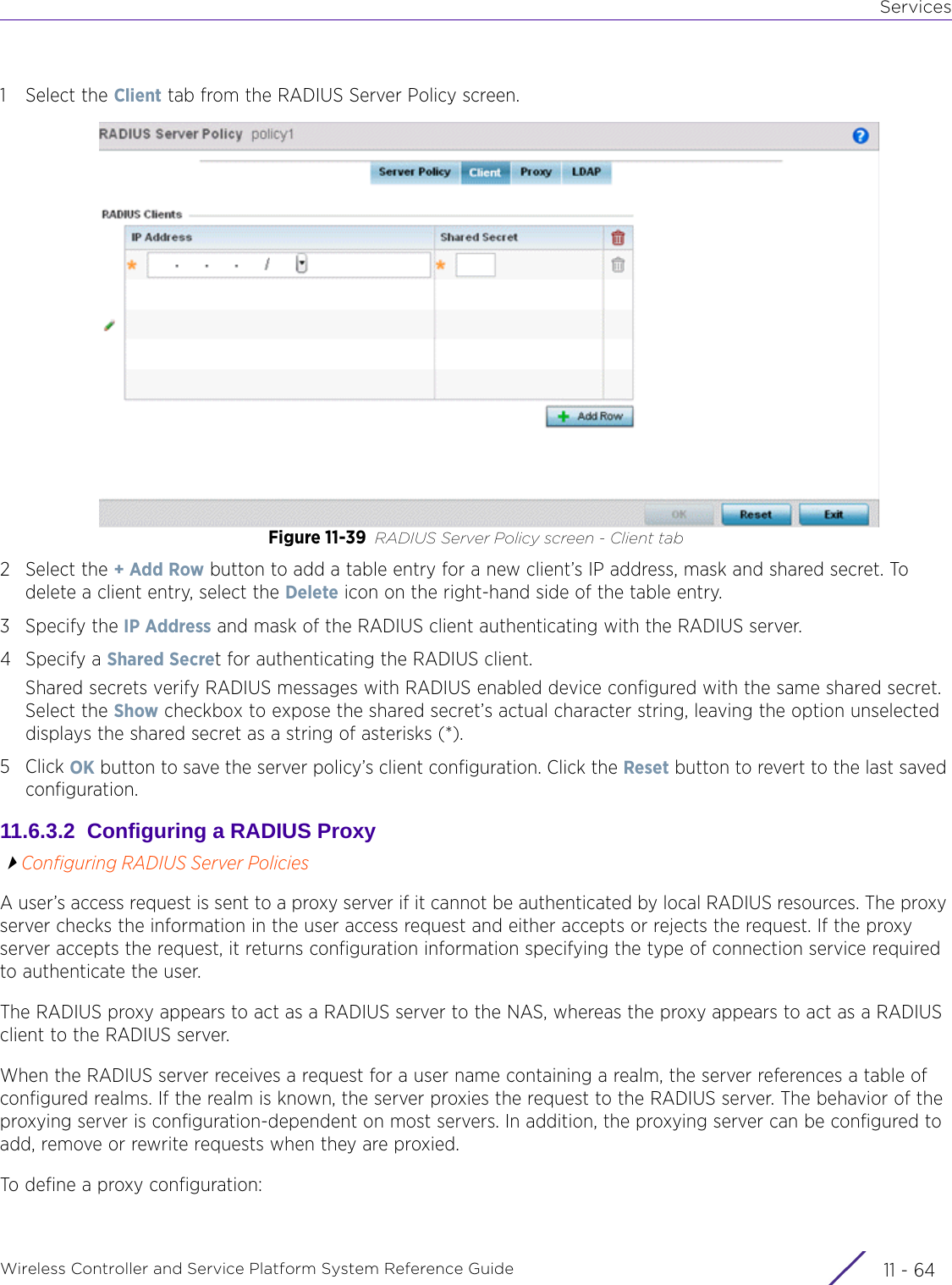
Contents
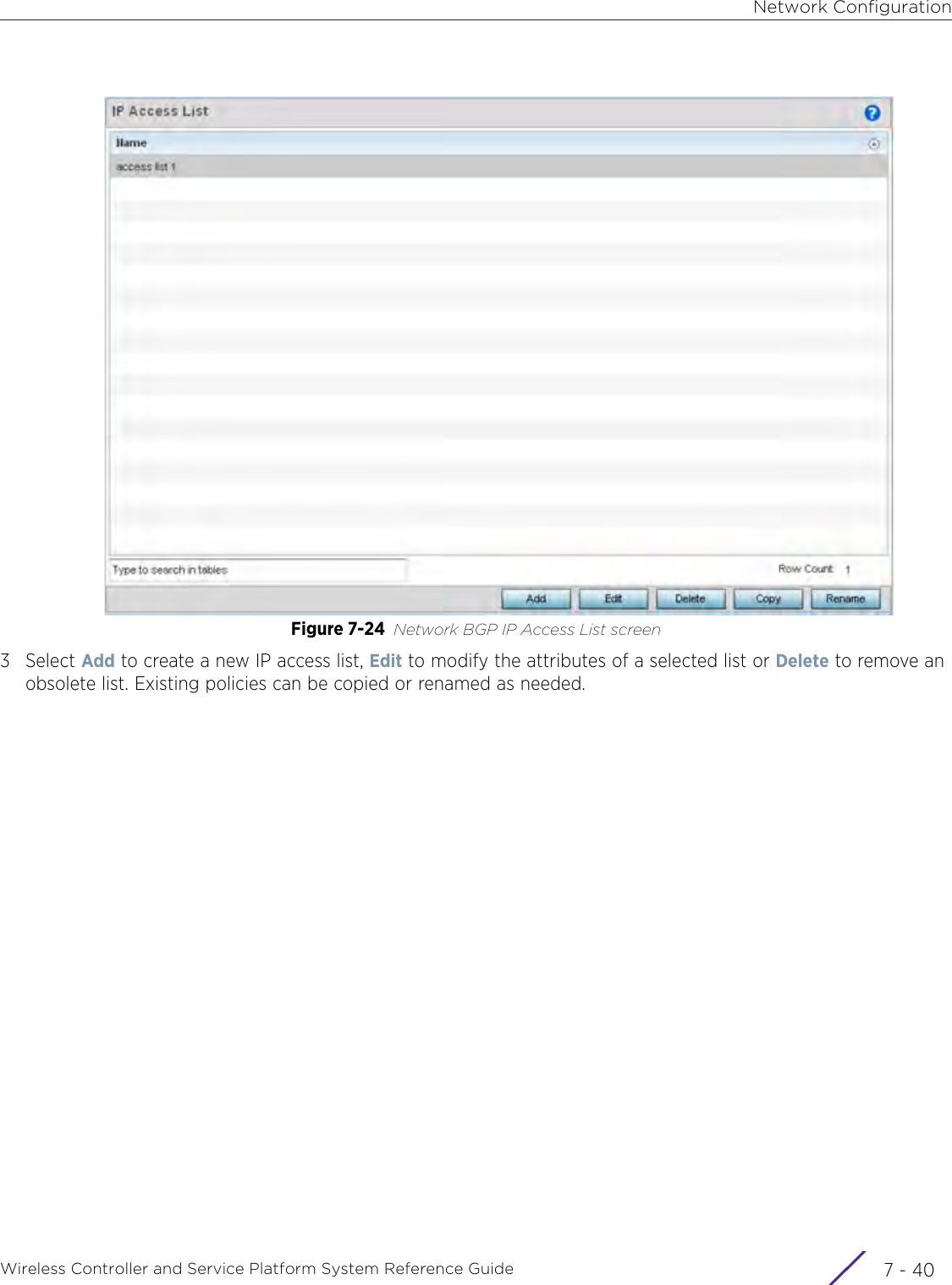
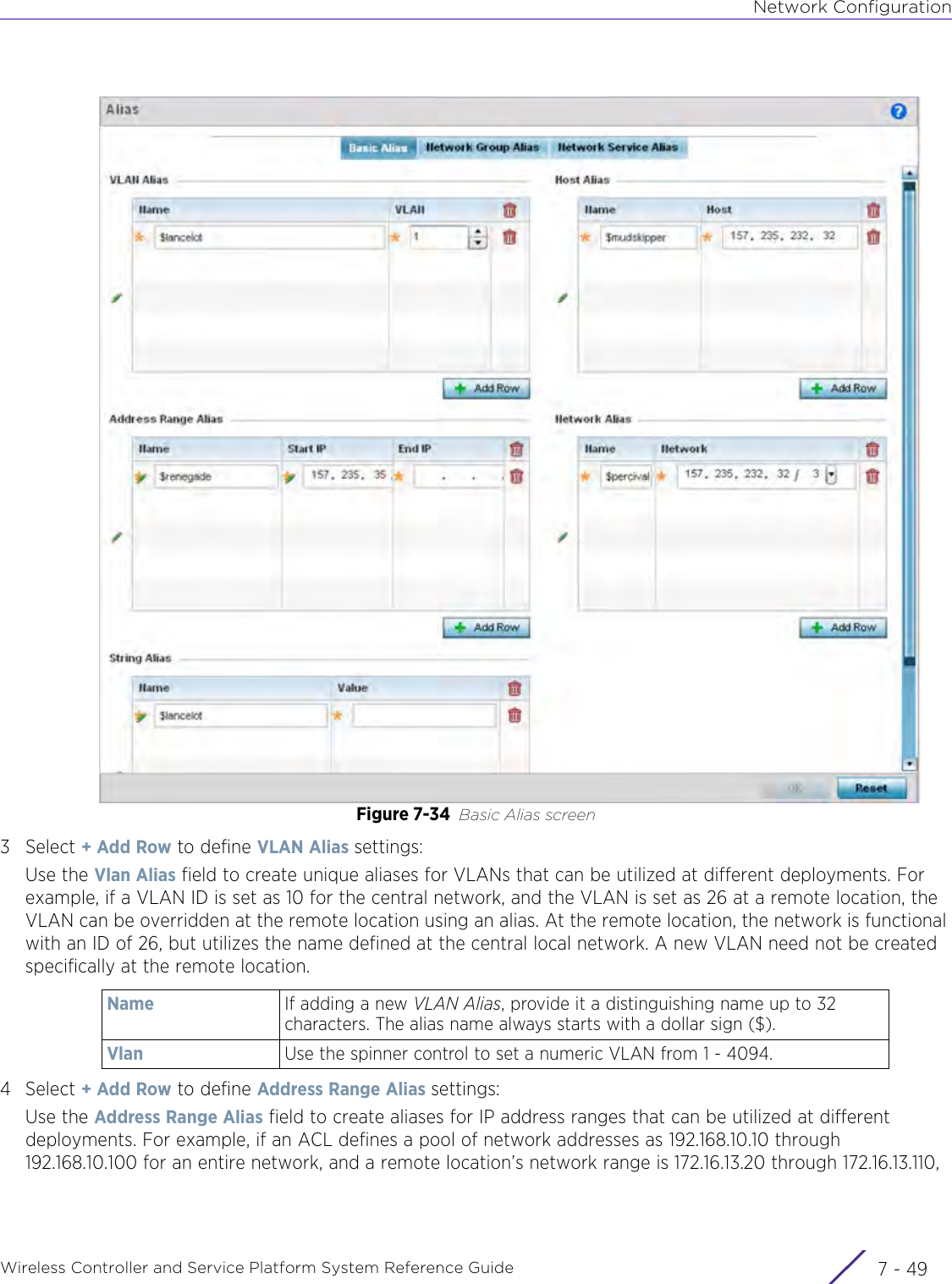
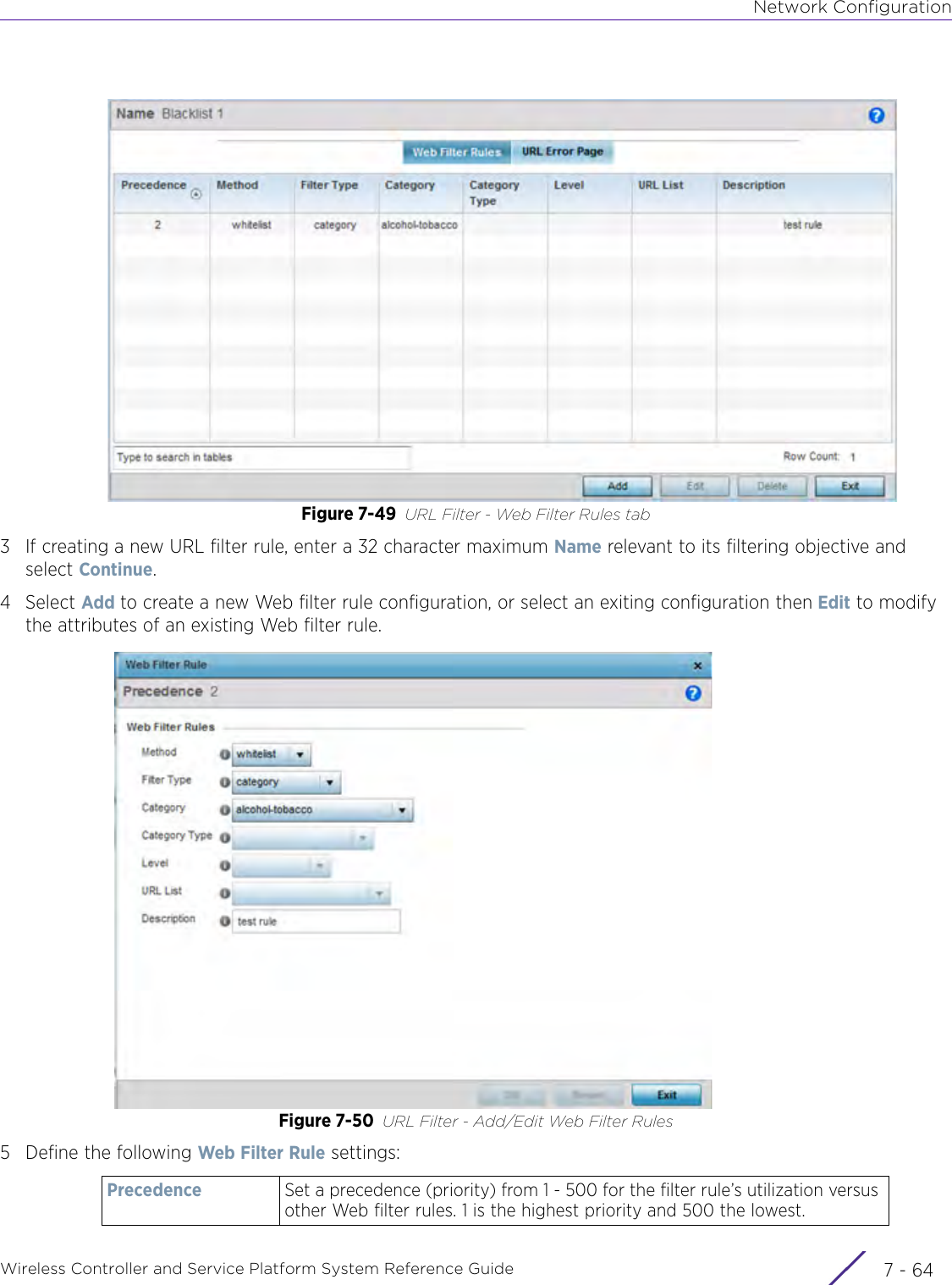
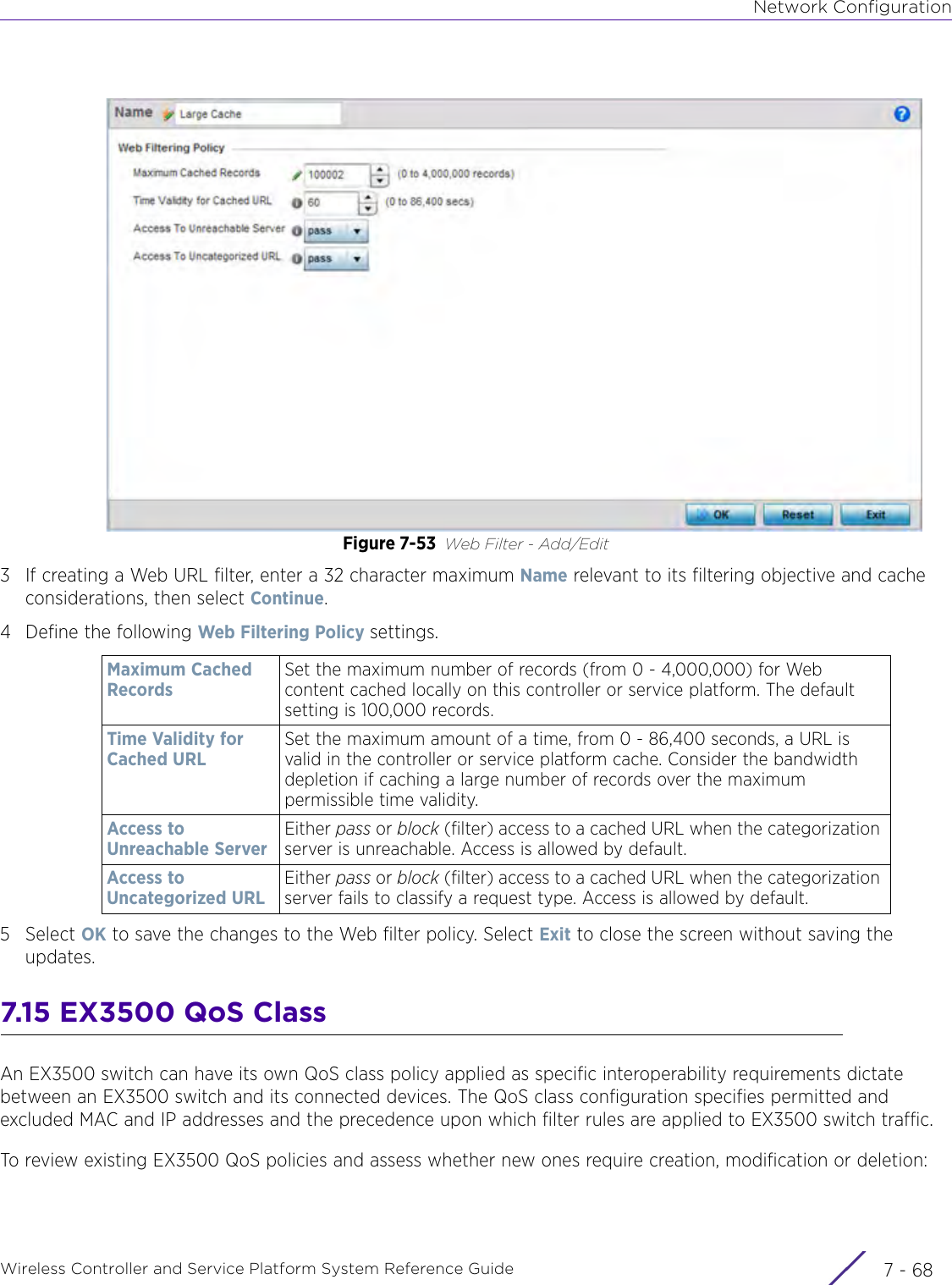
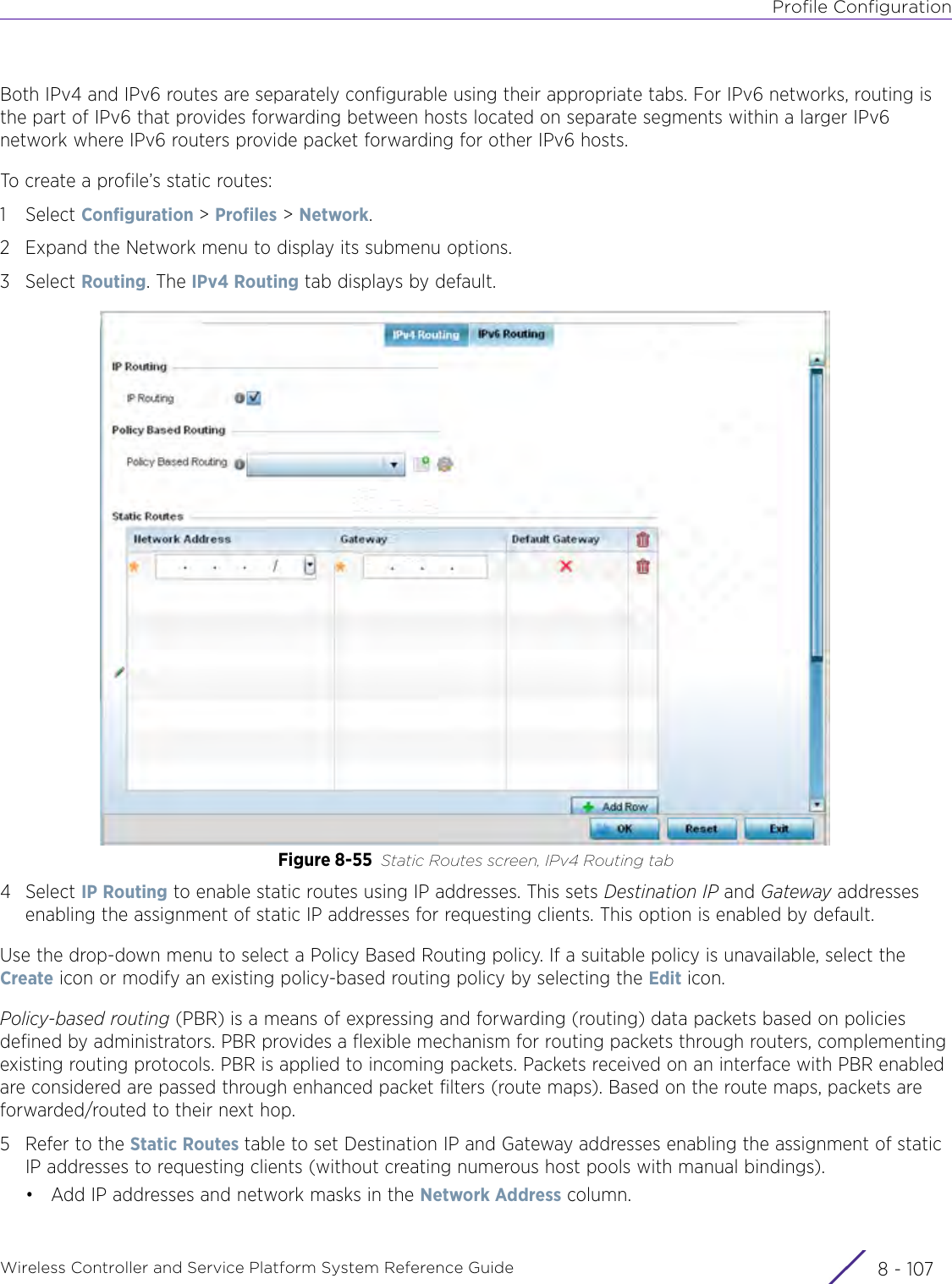
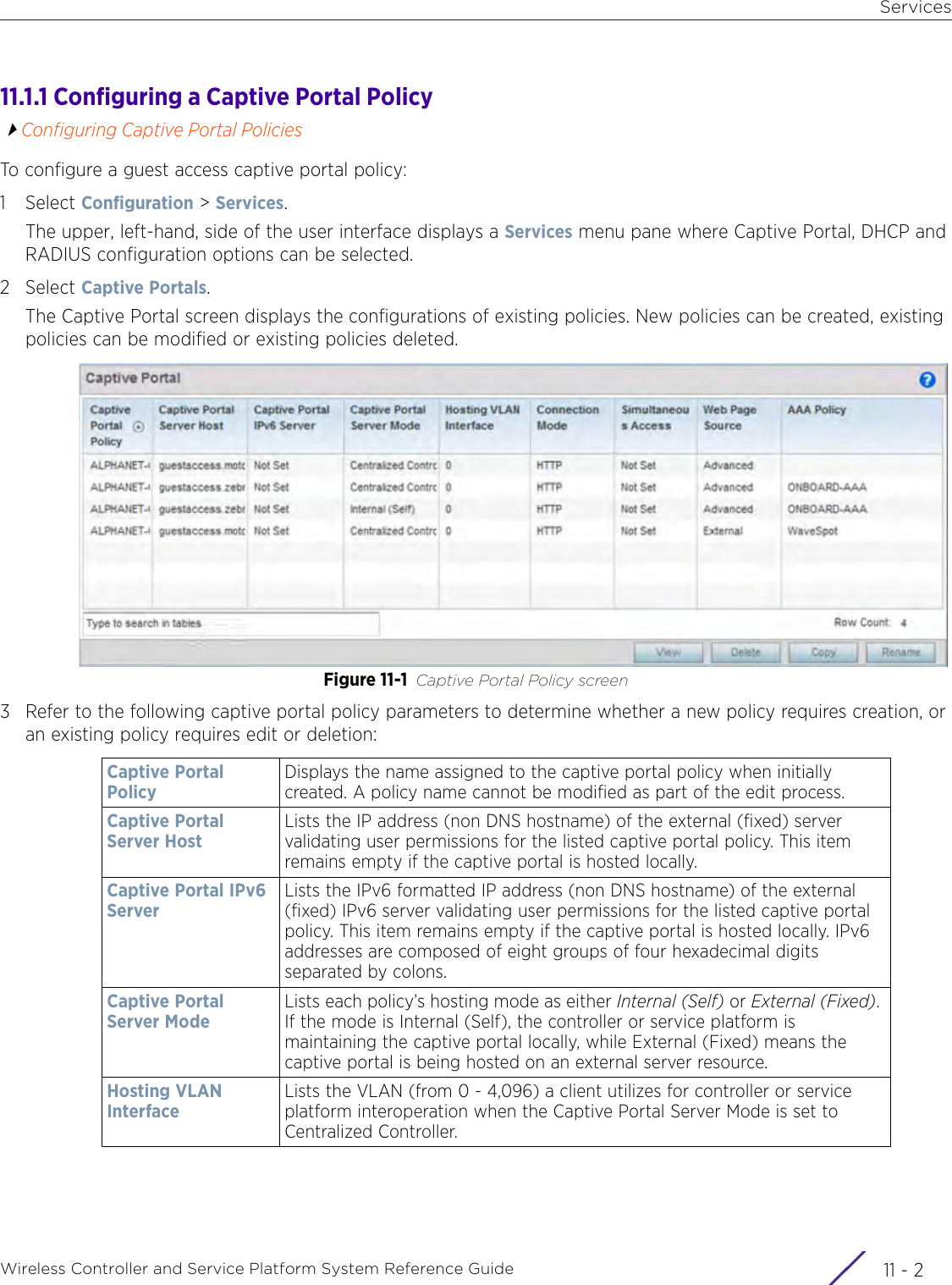
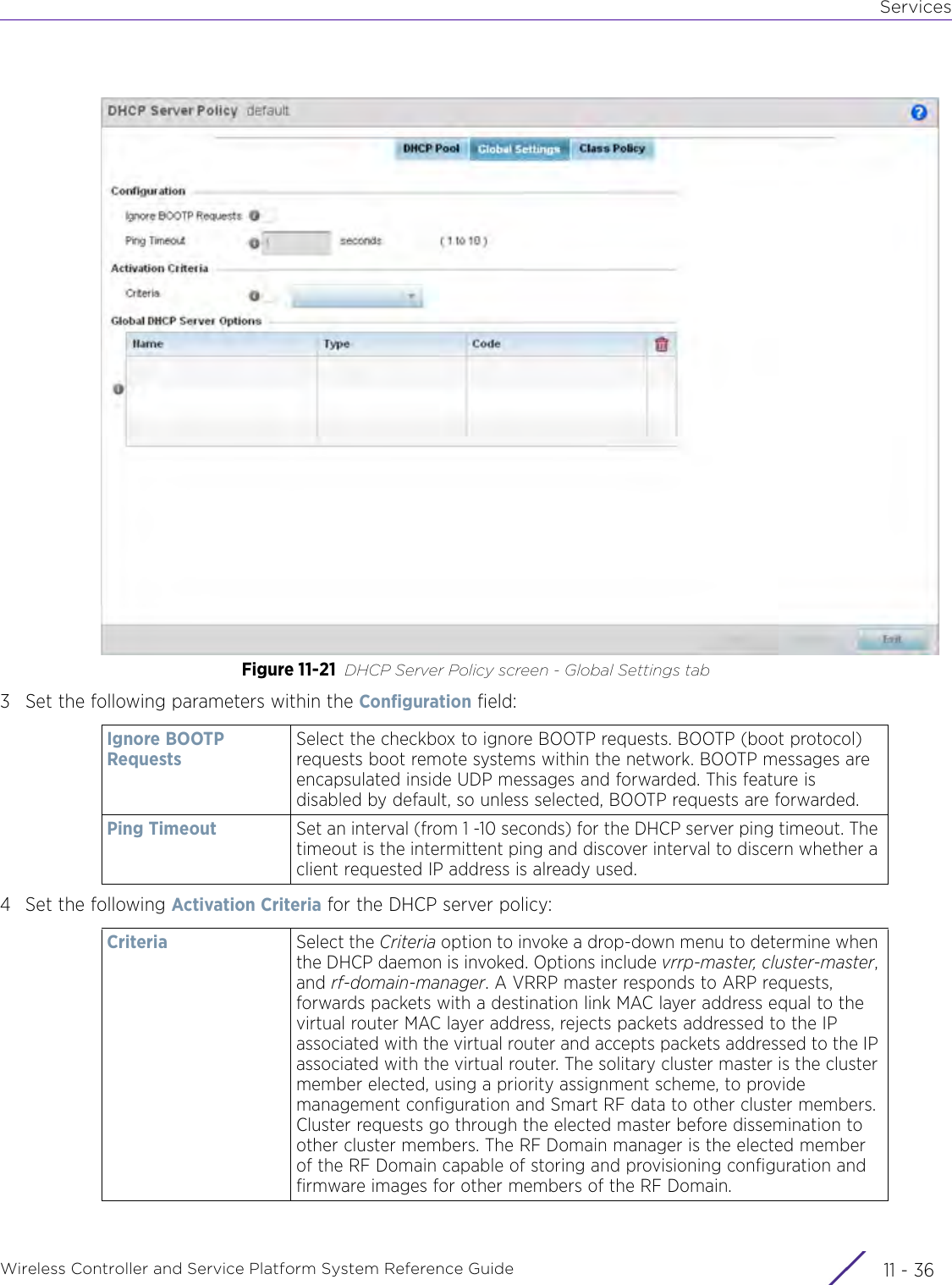
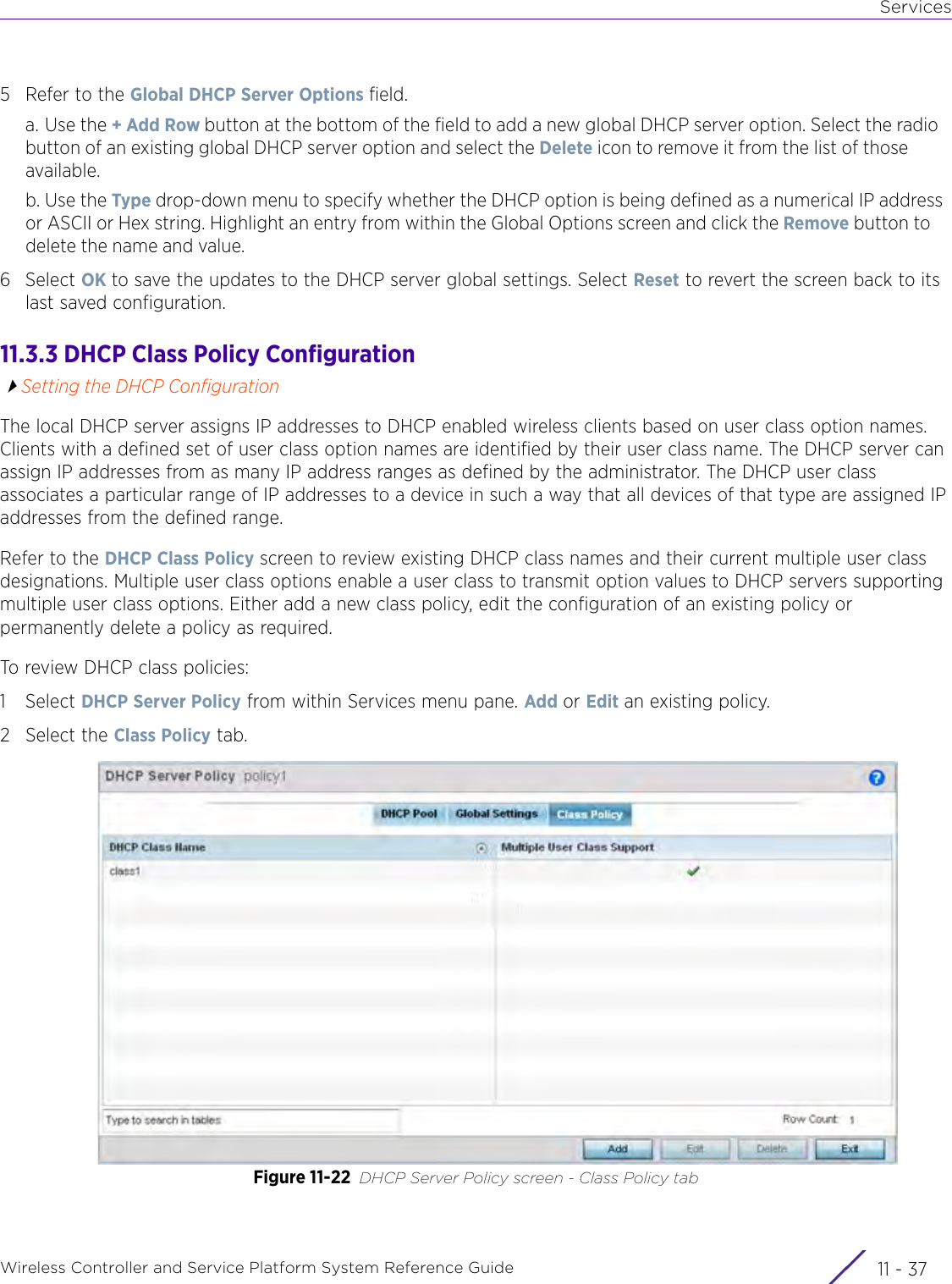
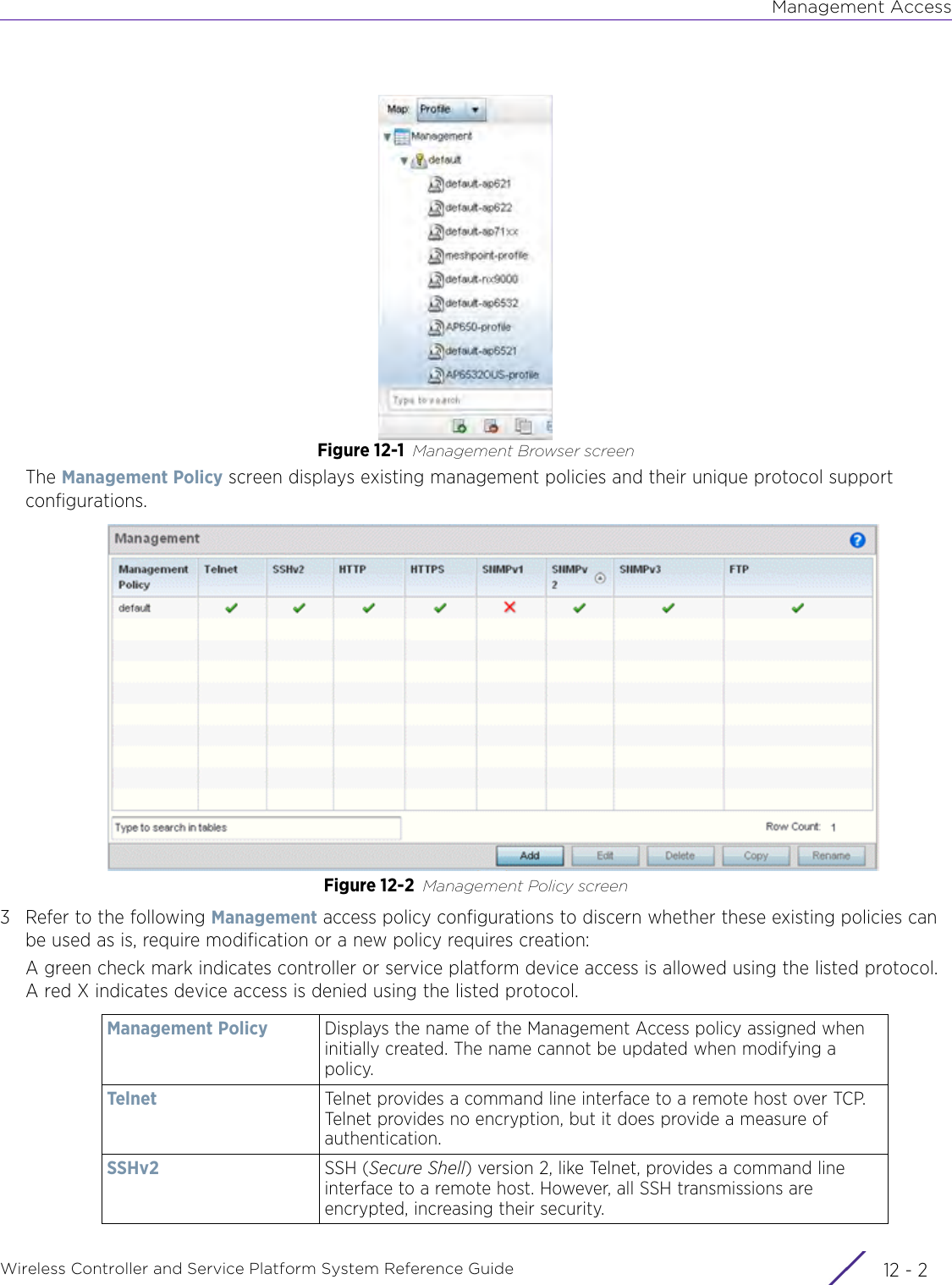
- 1. User Manual-AP3917e
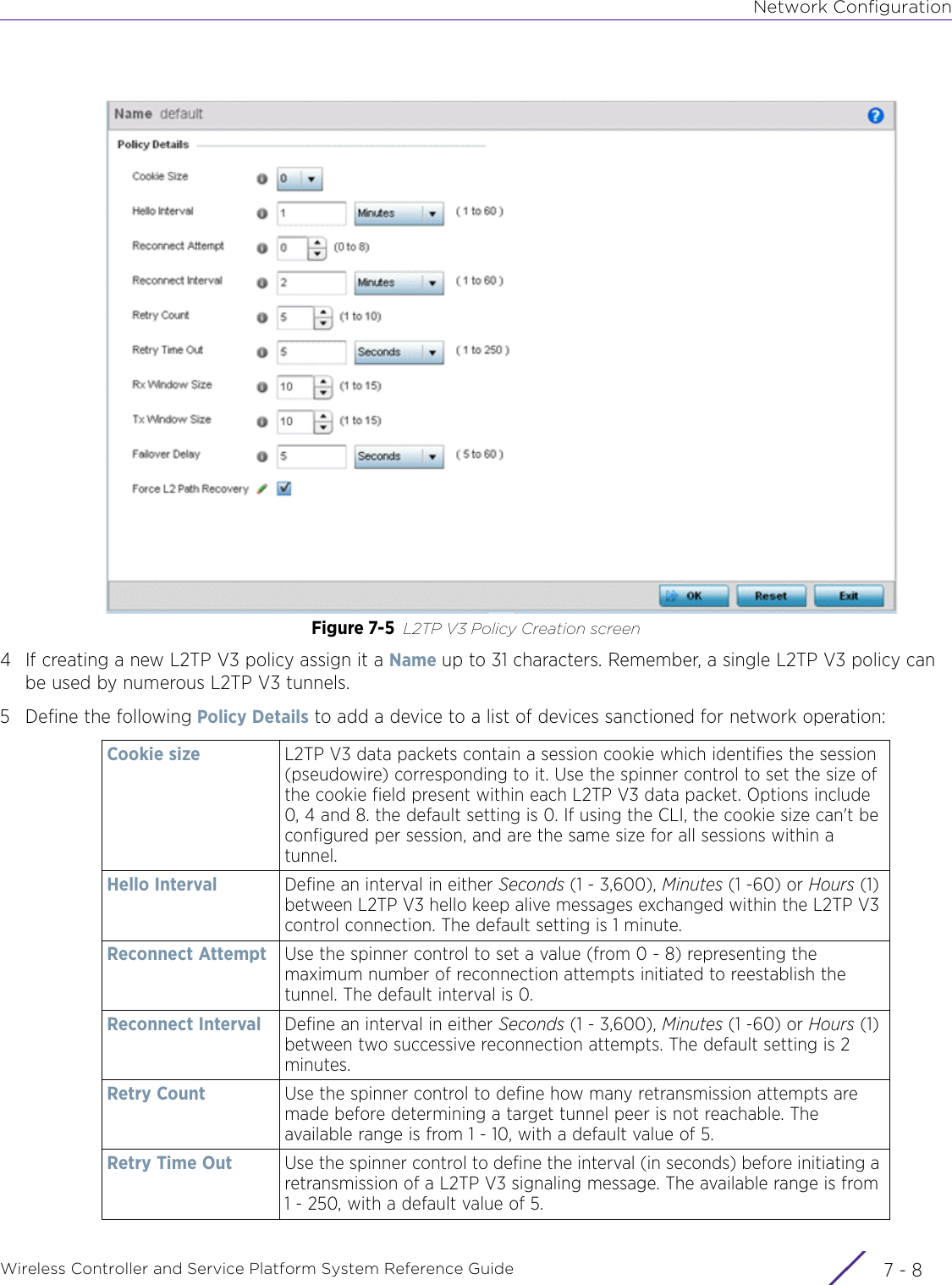
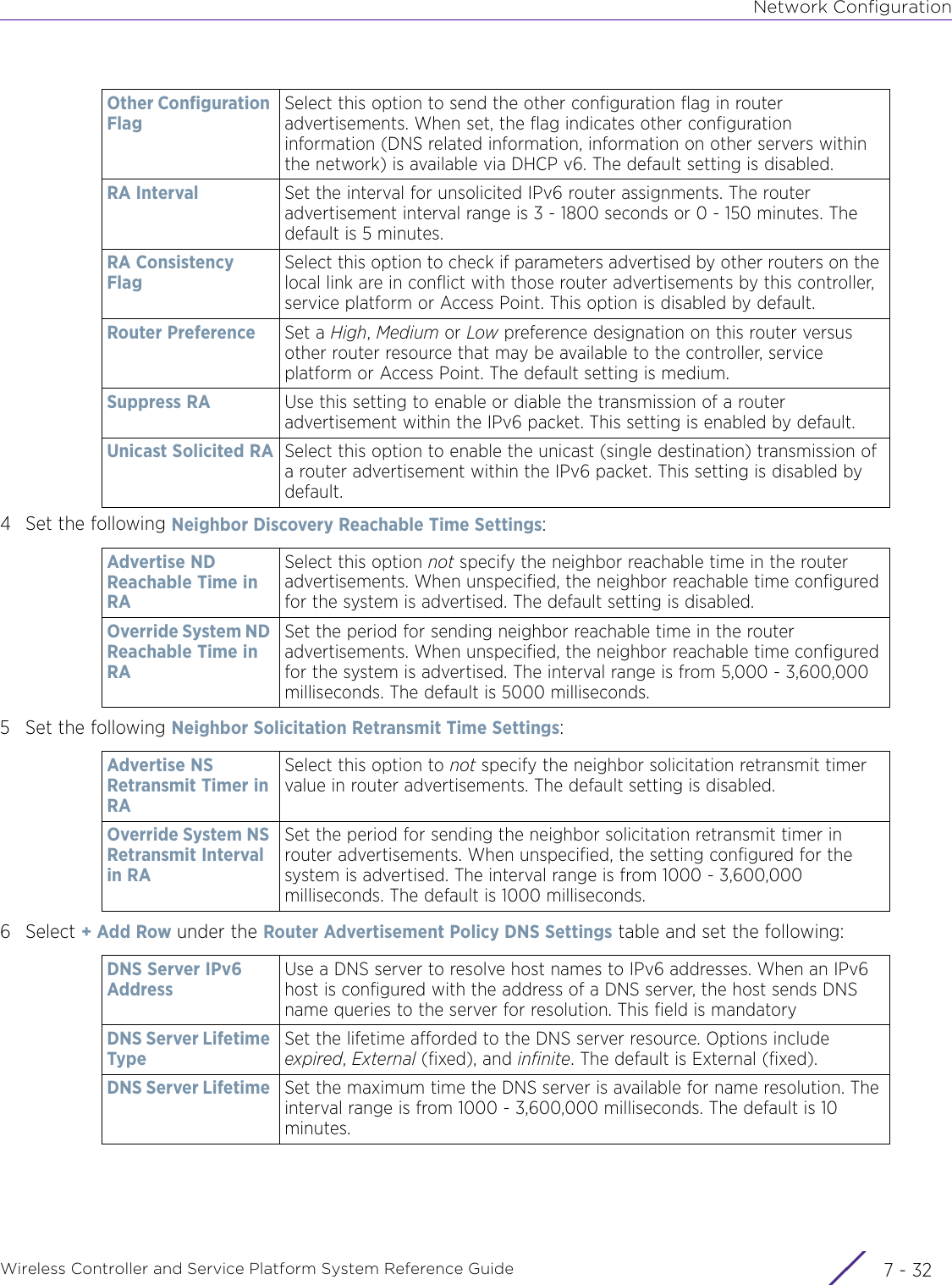
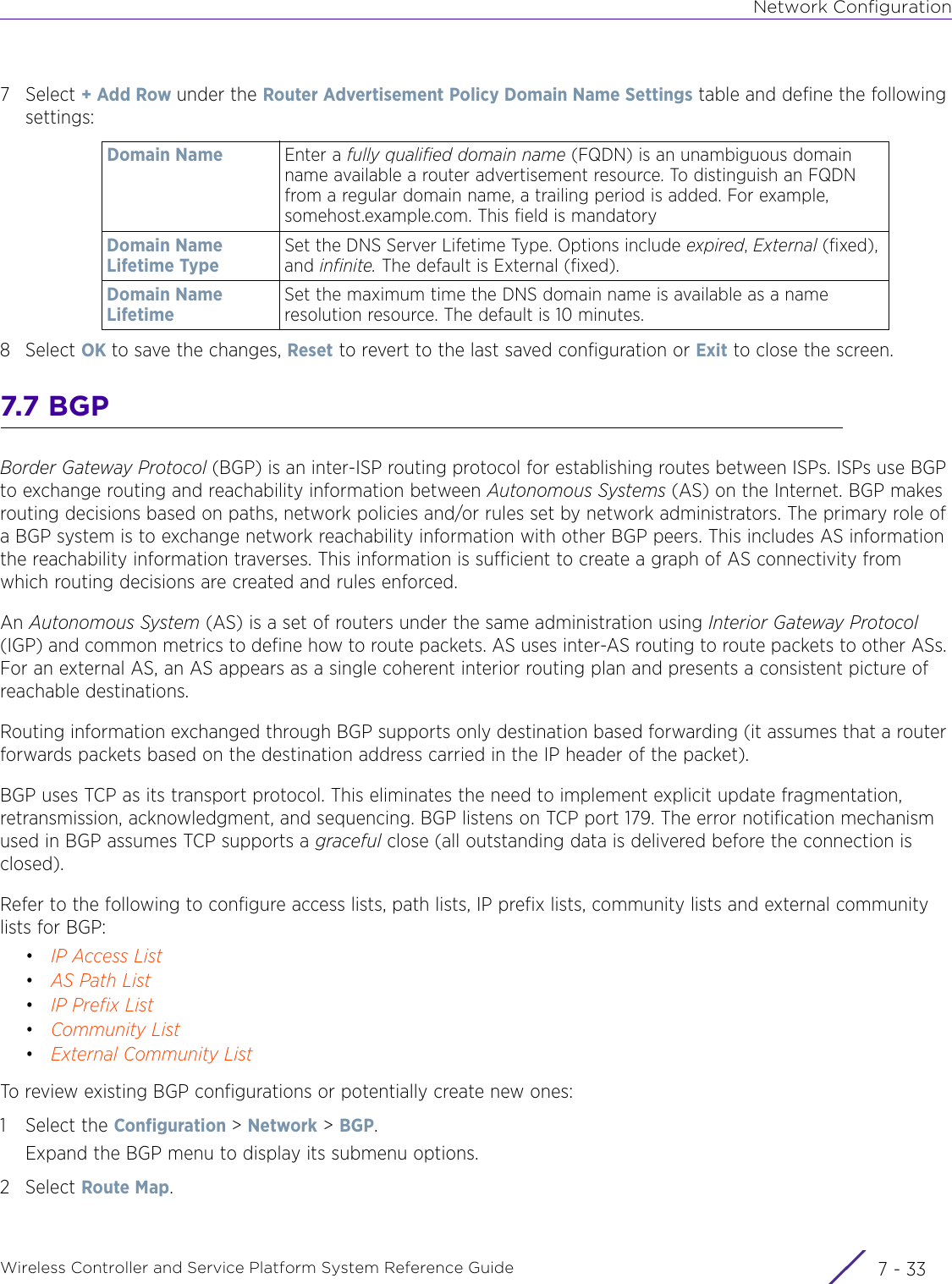
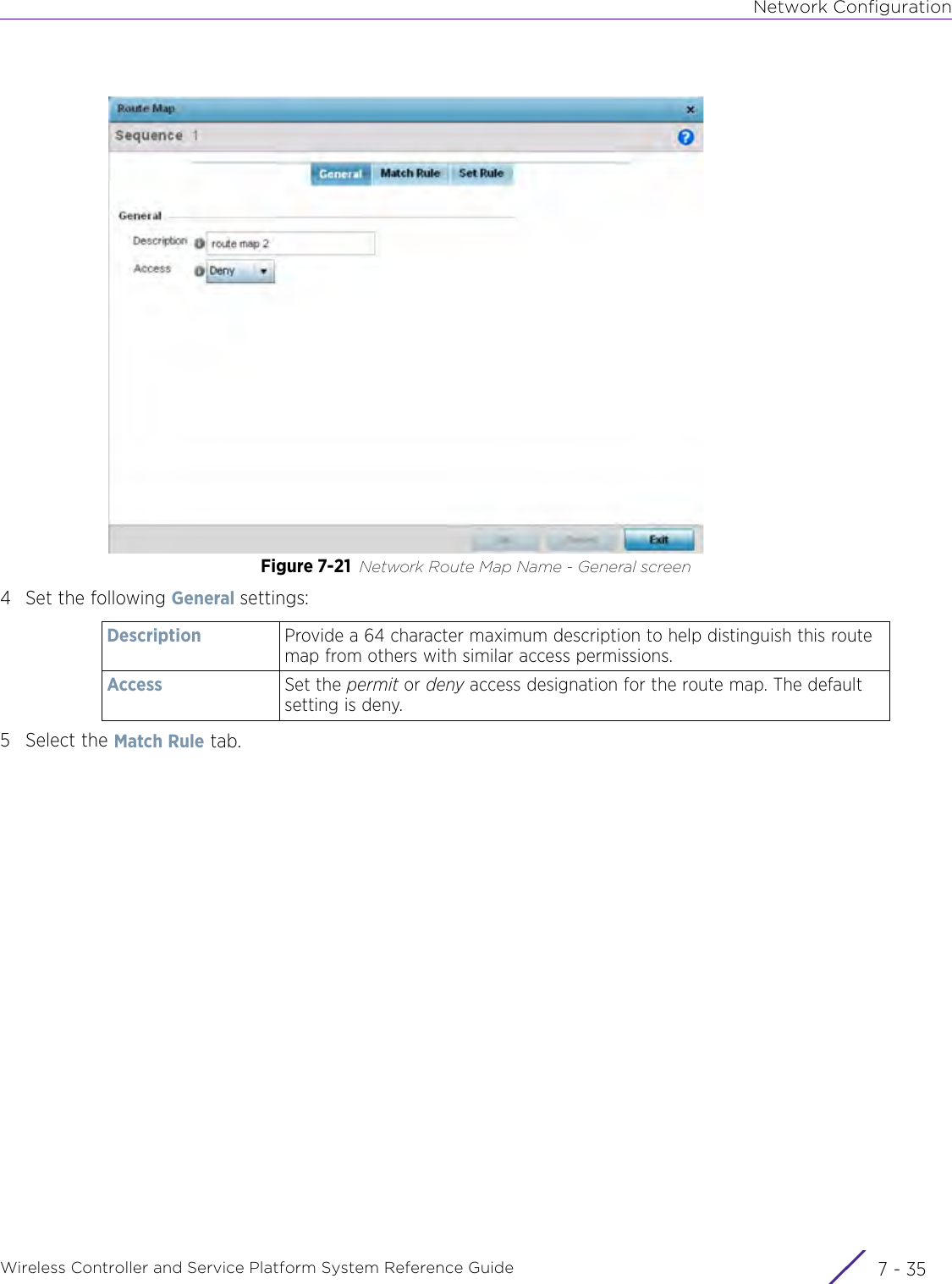
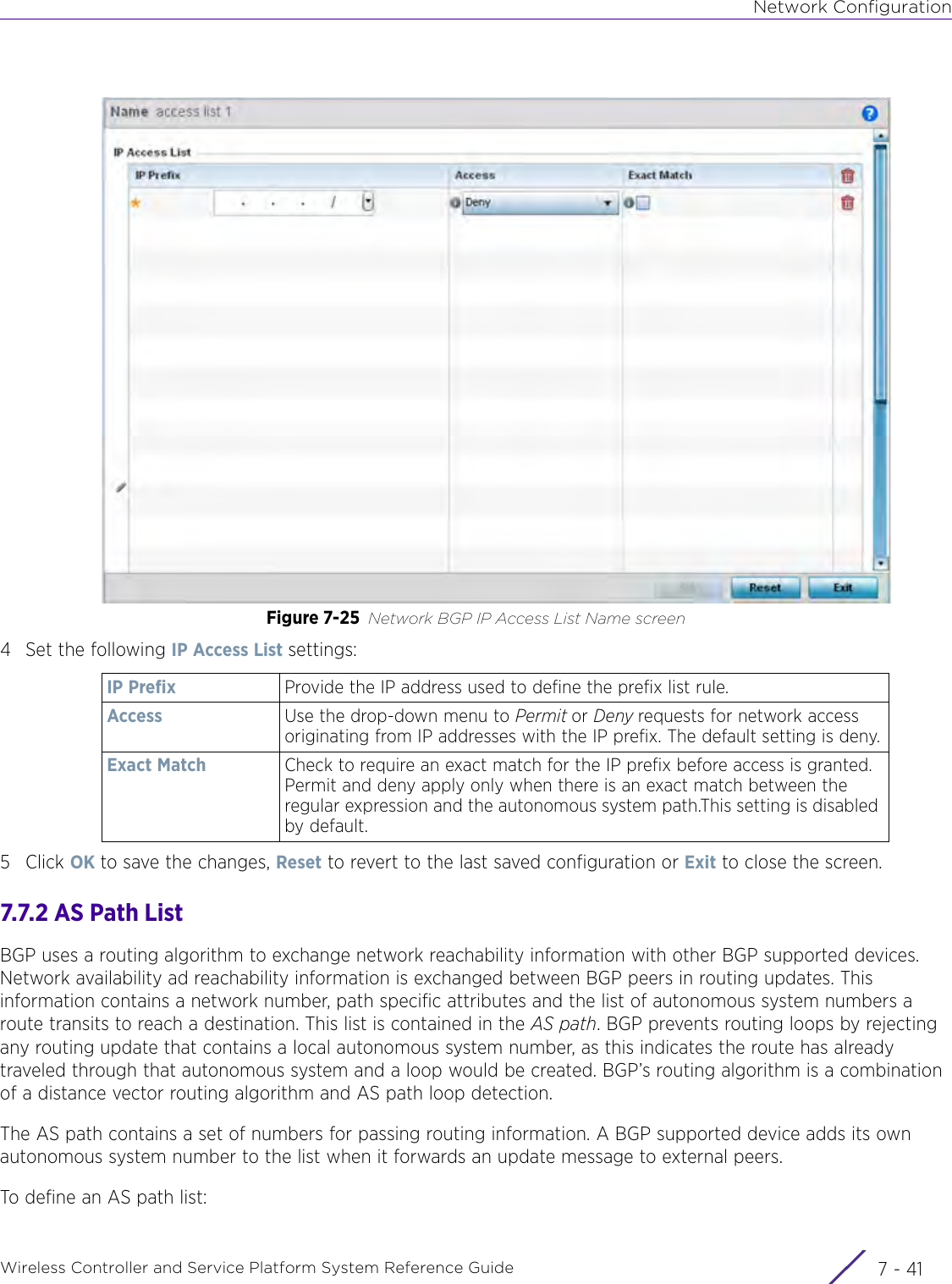
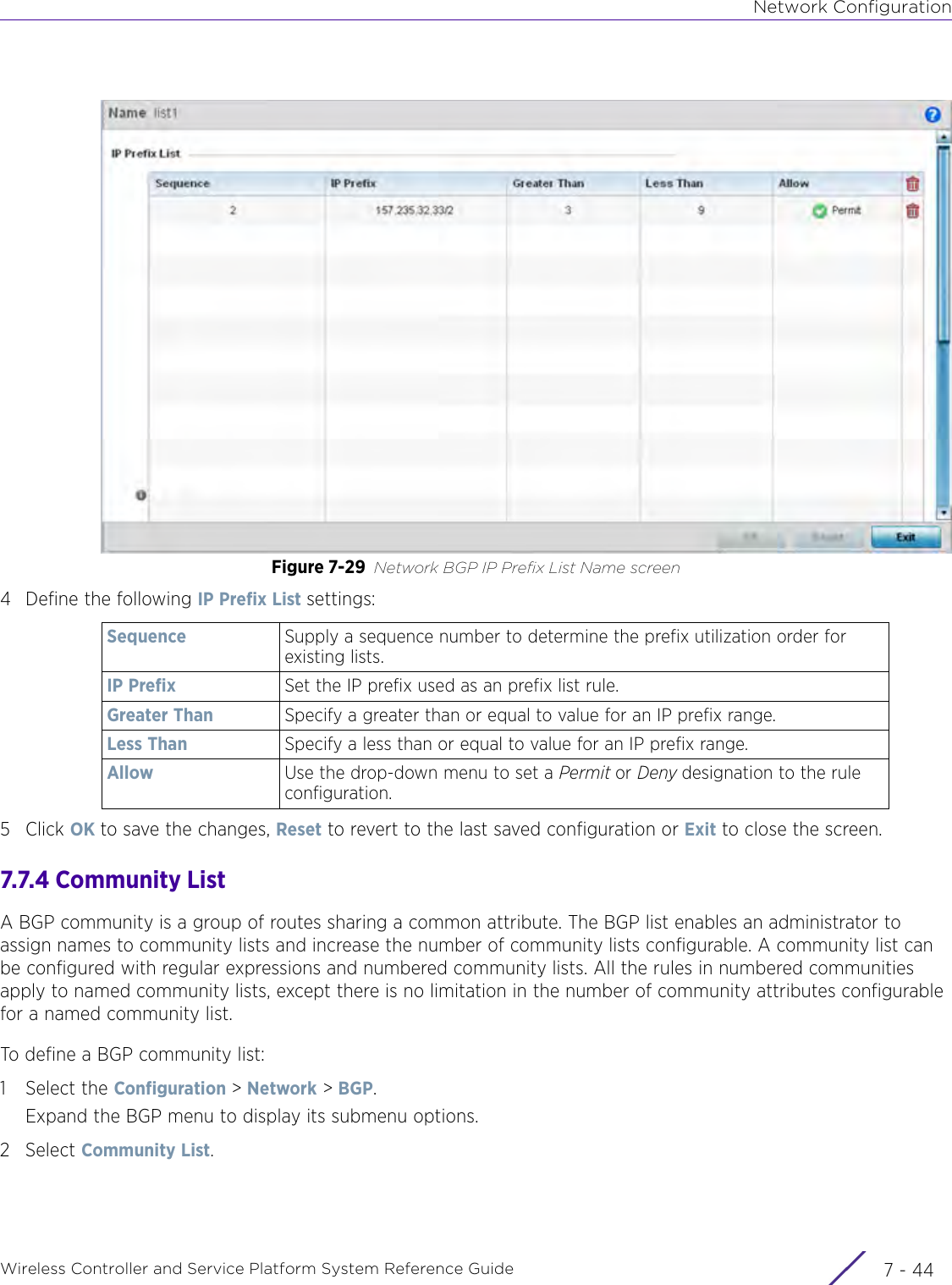
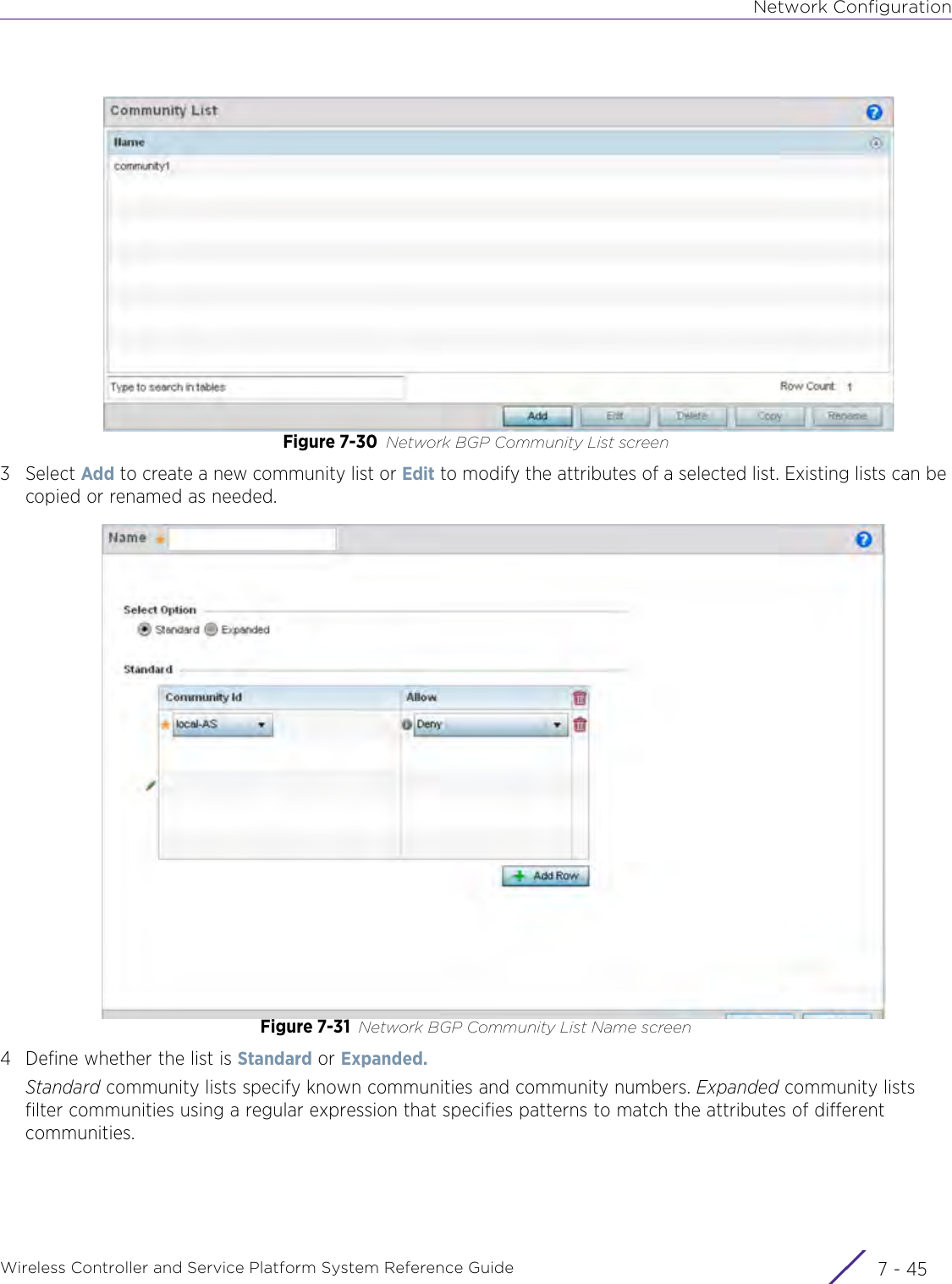
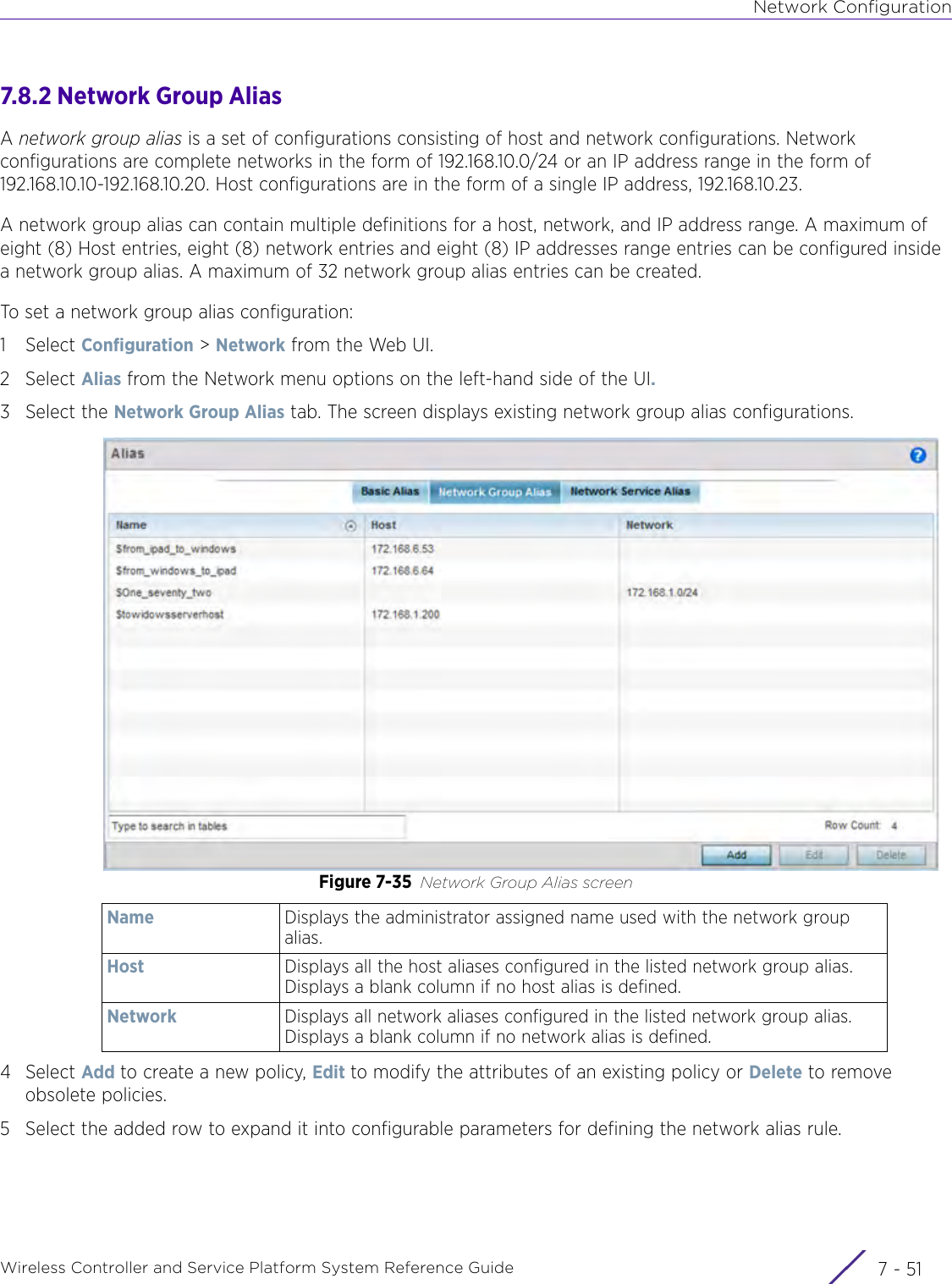
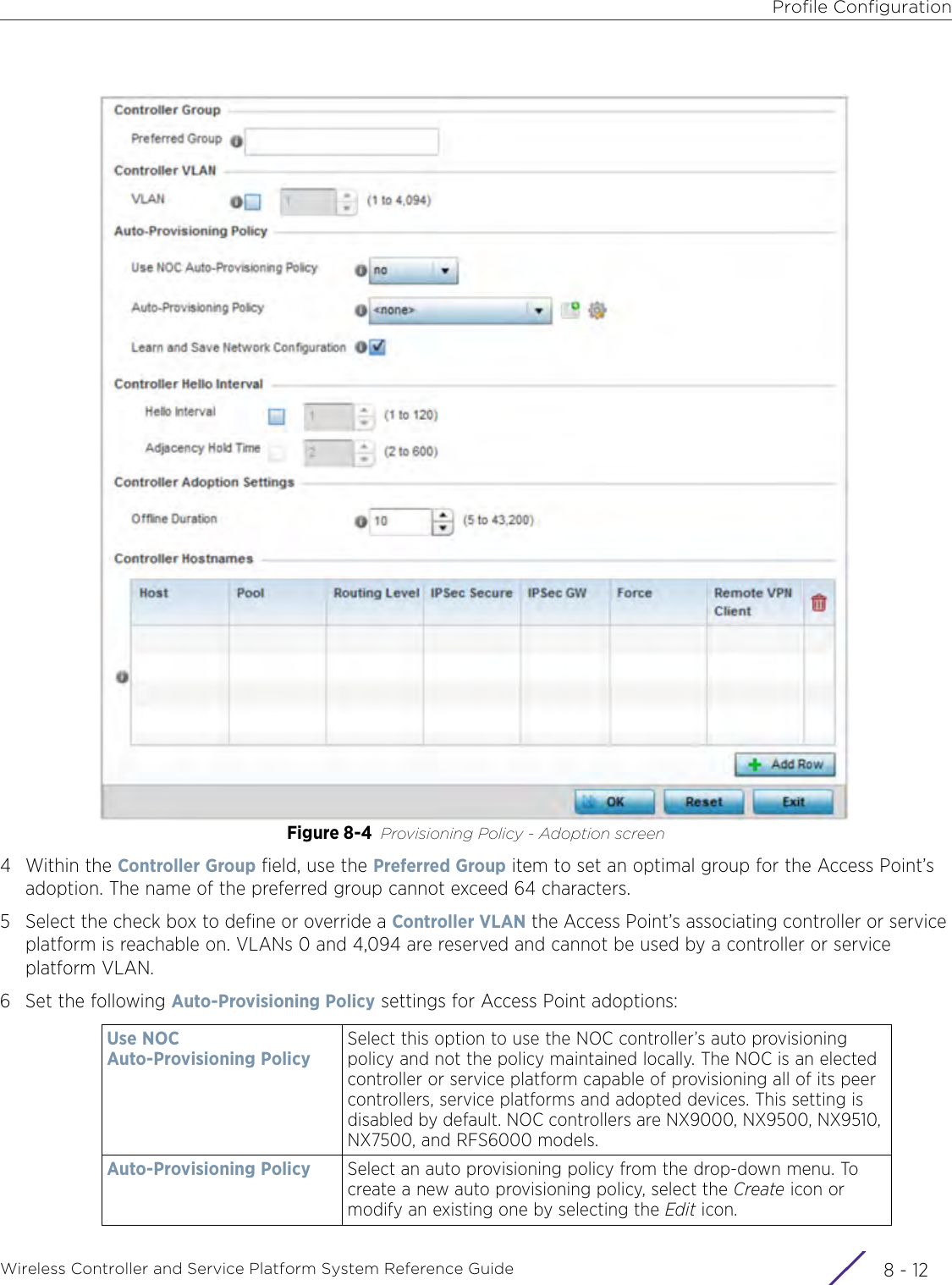
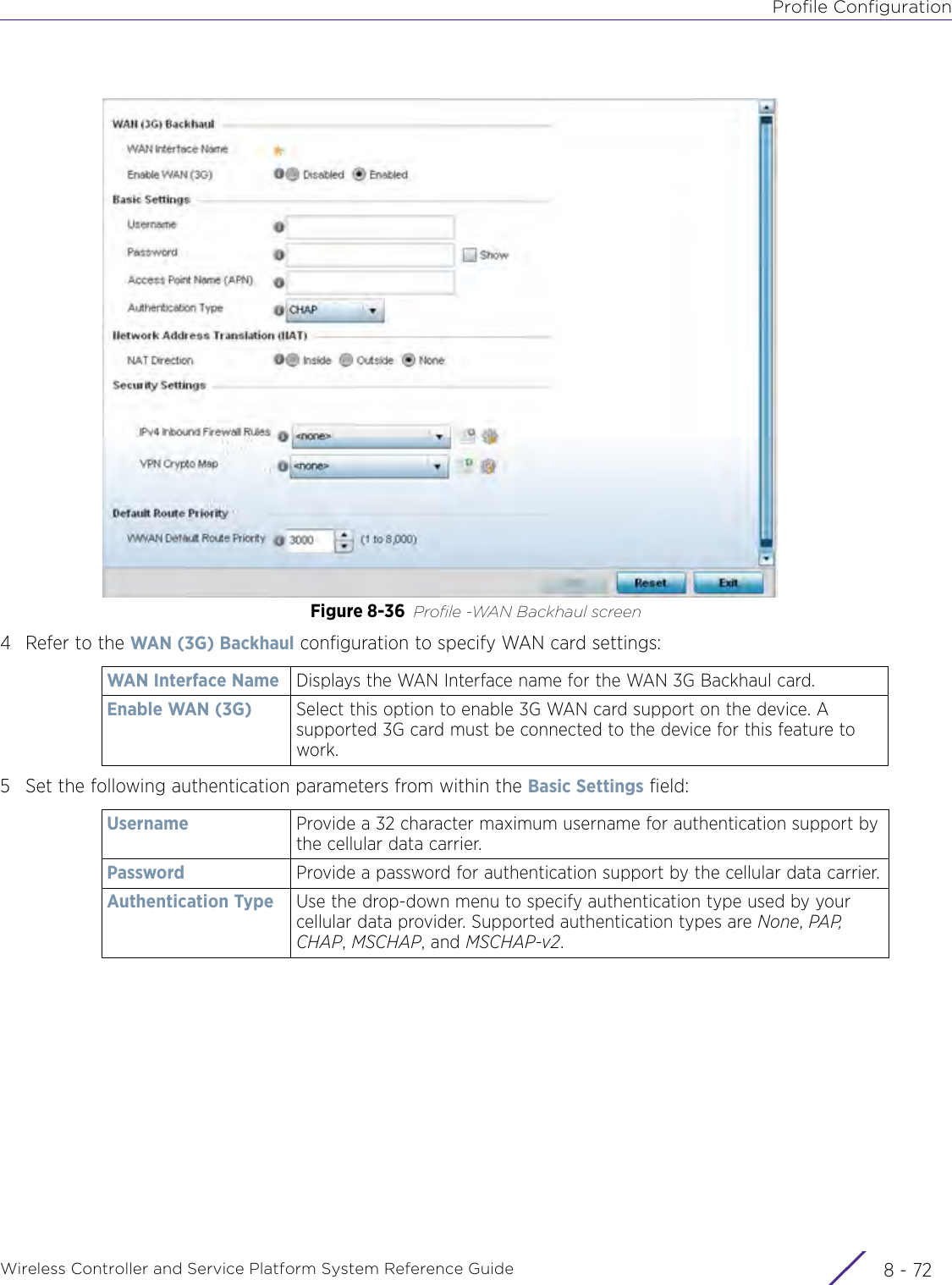
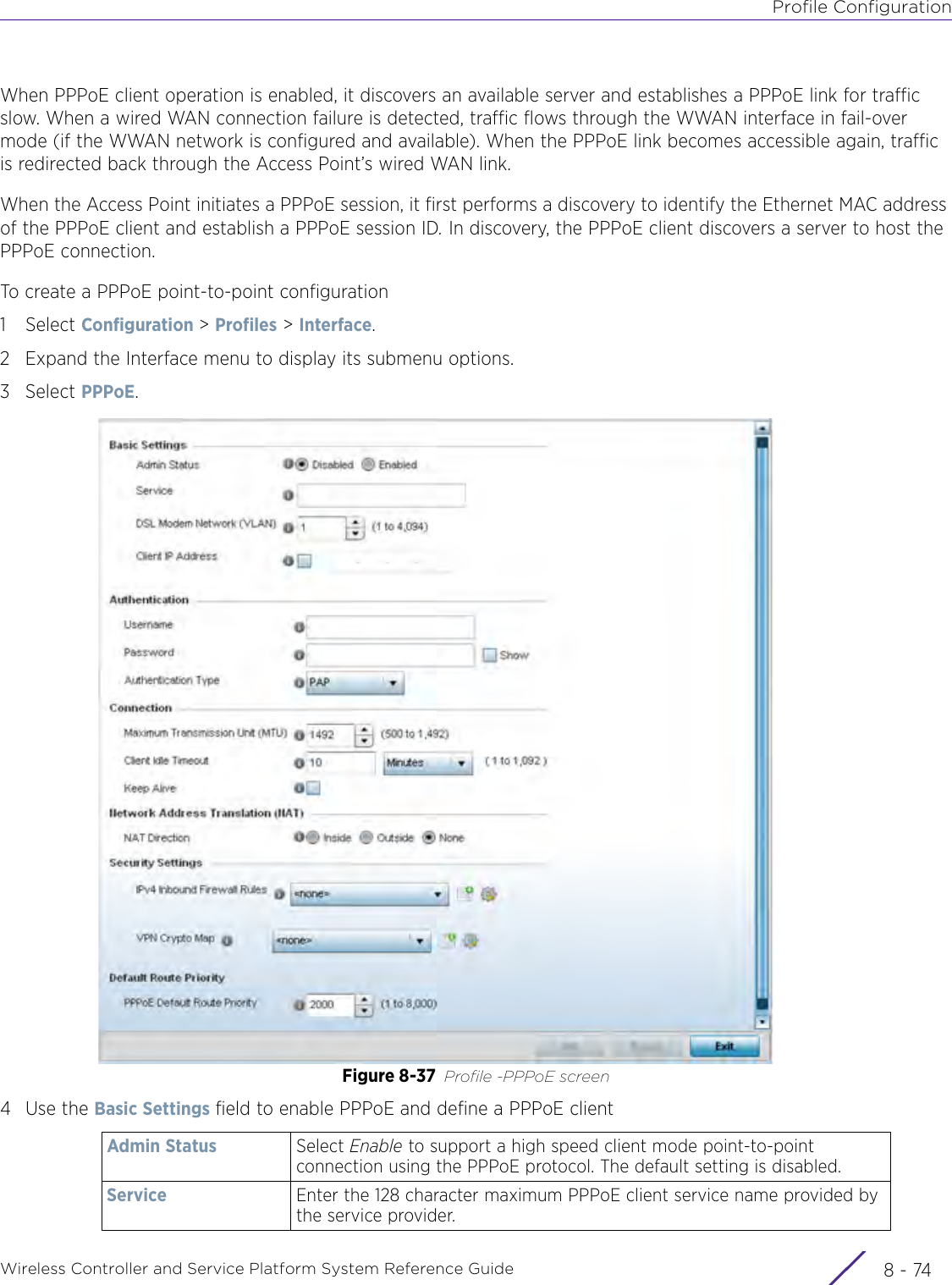
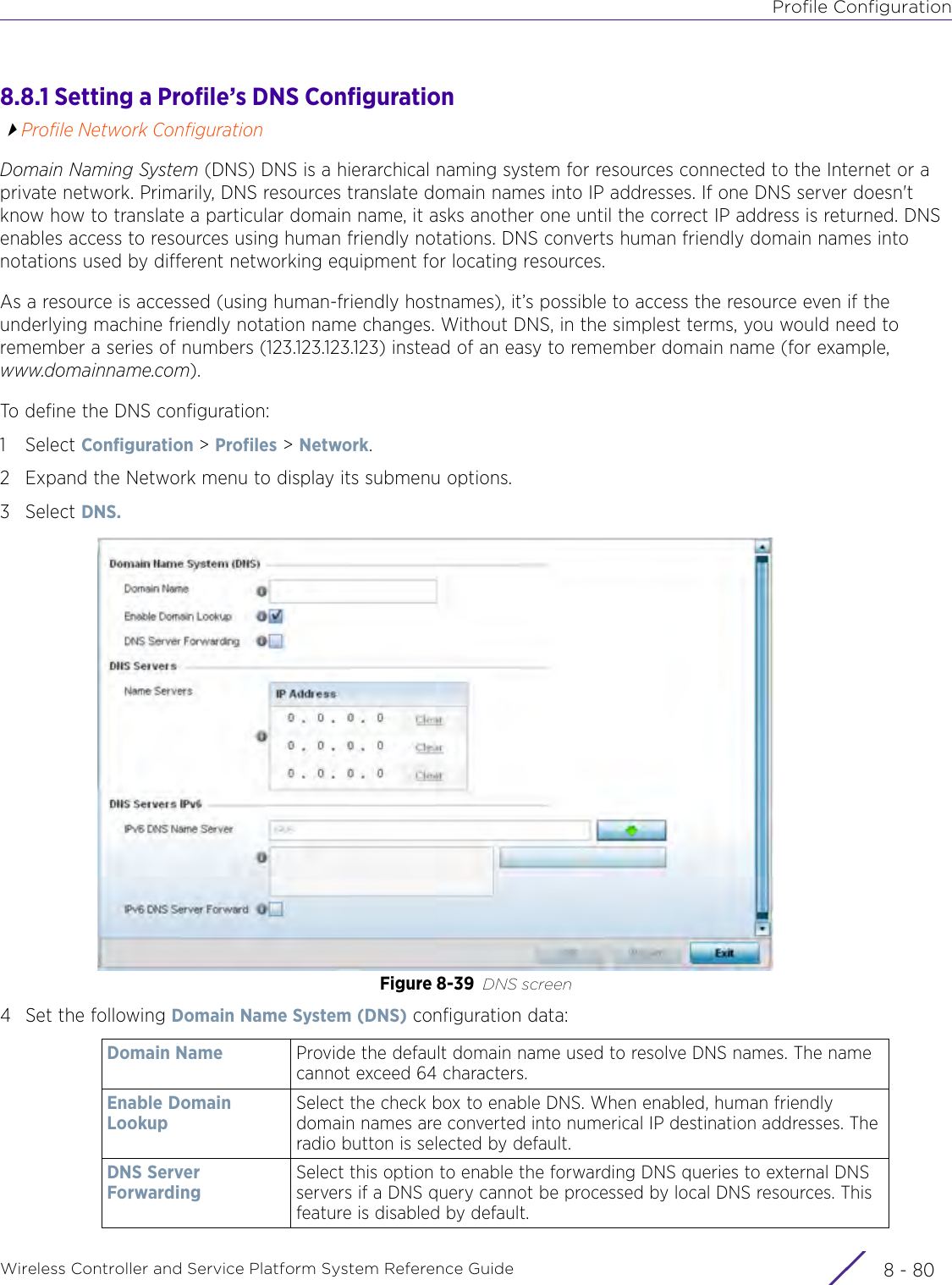
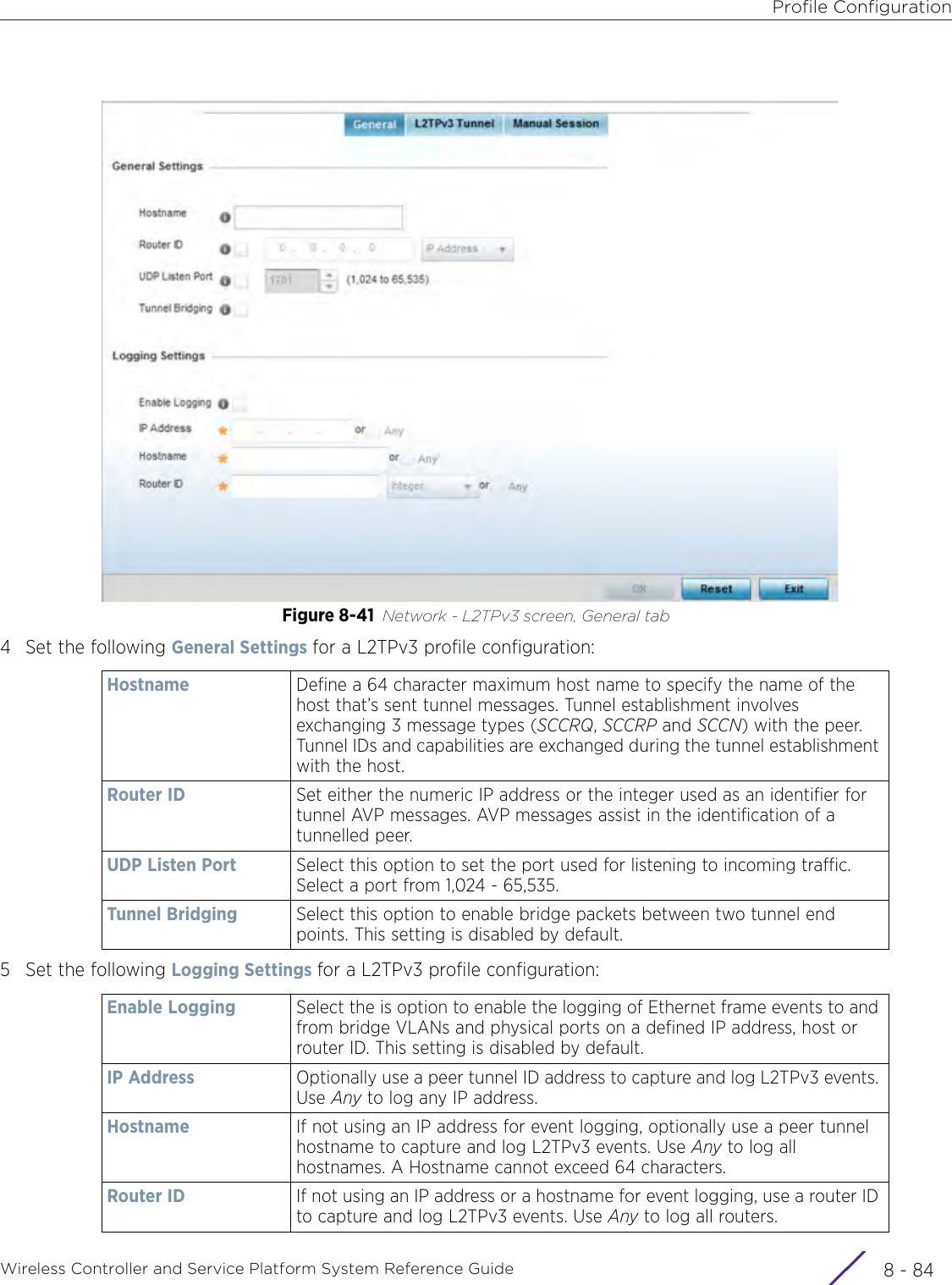
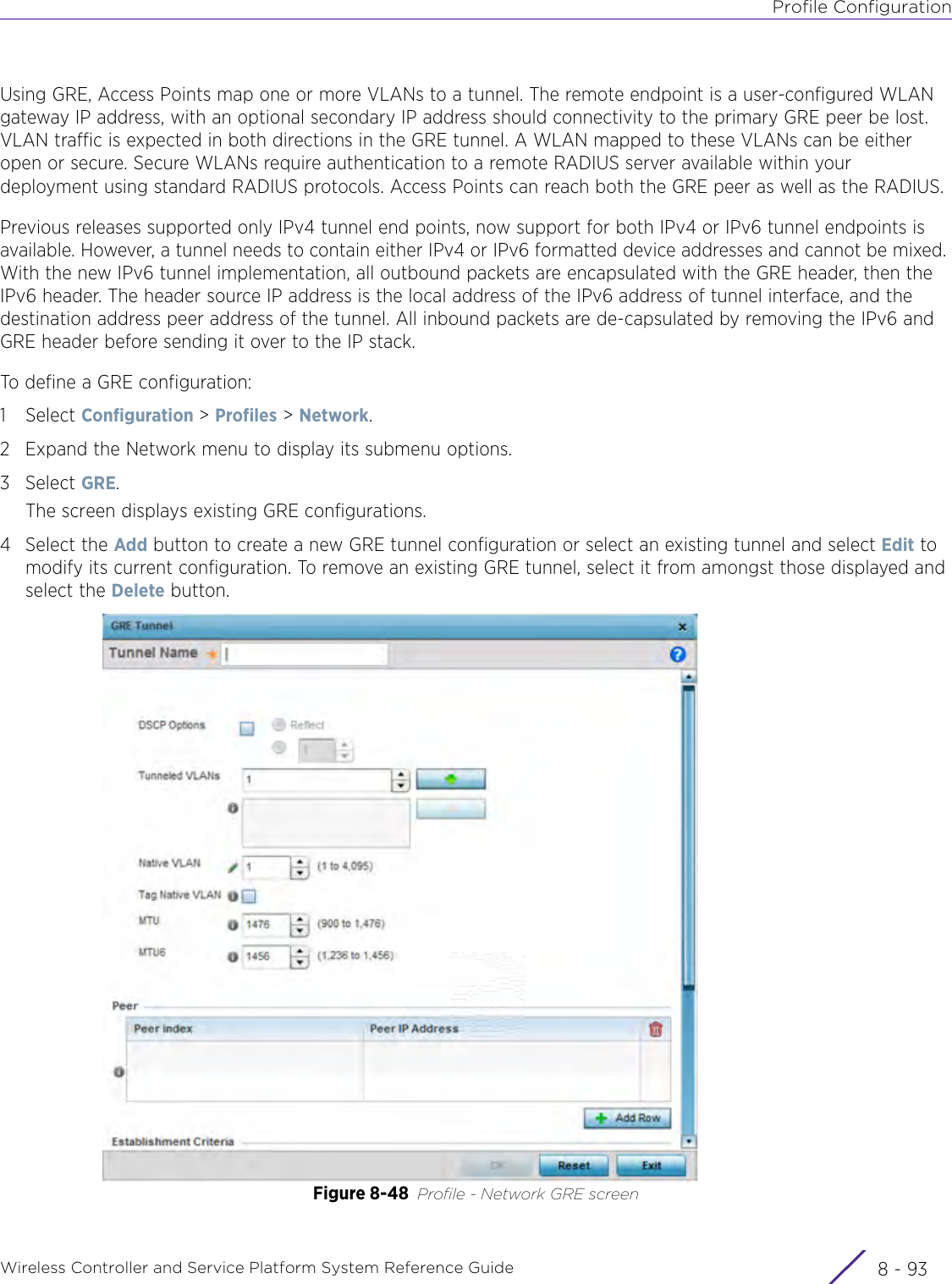
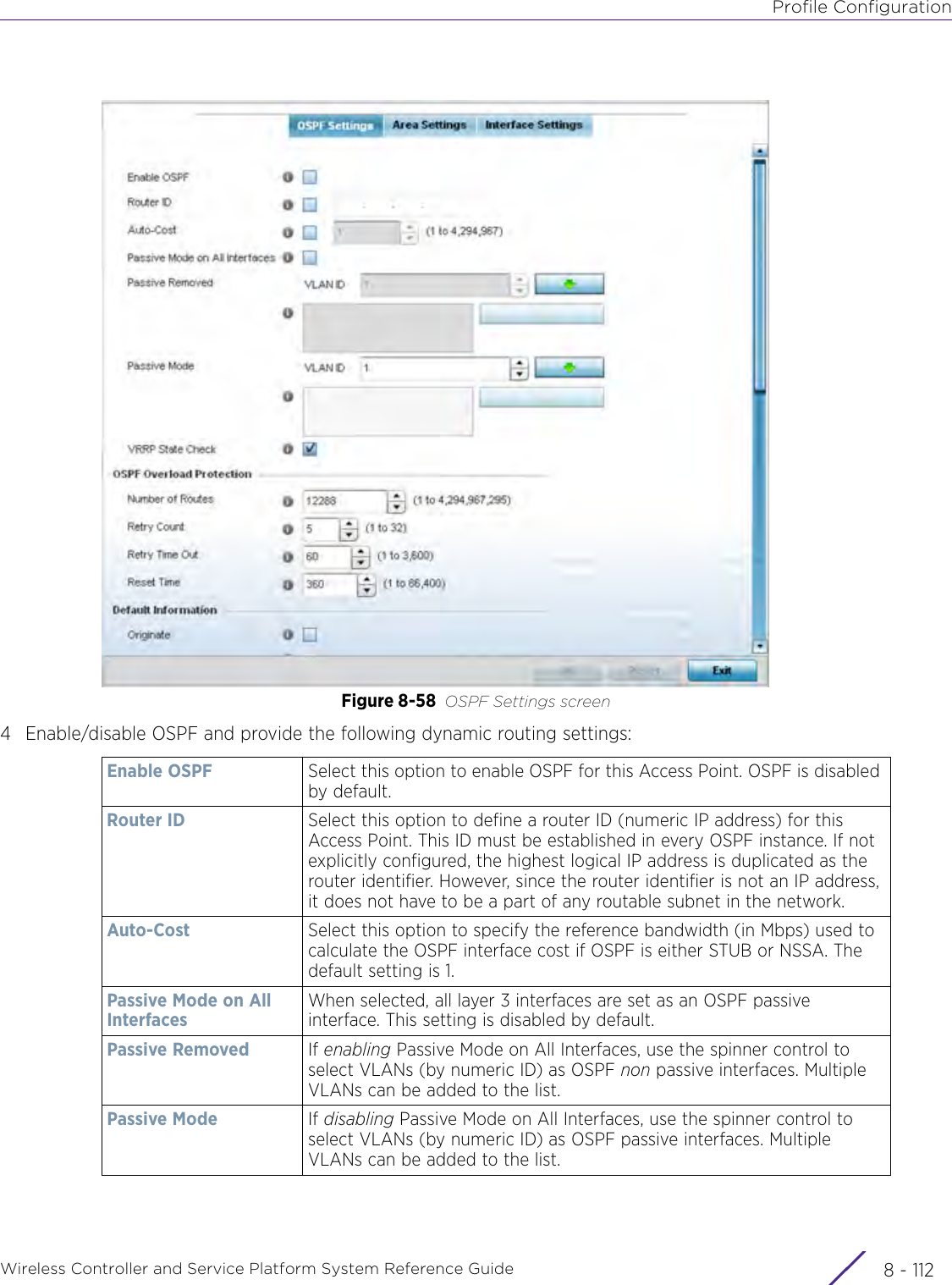
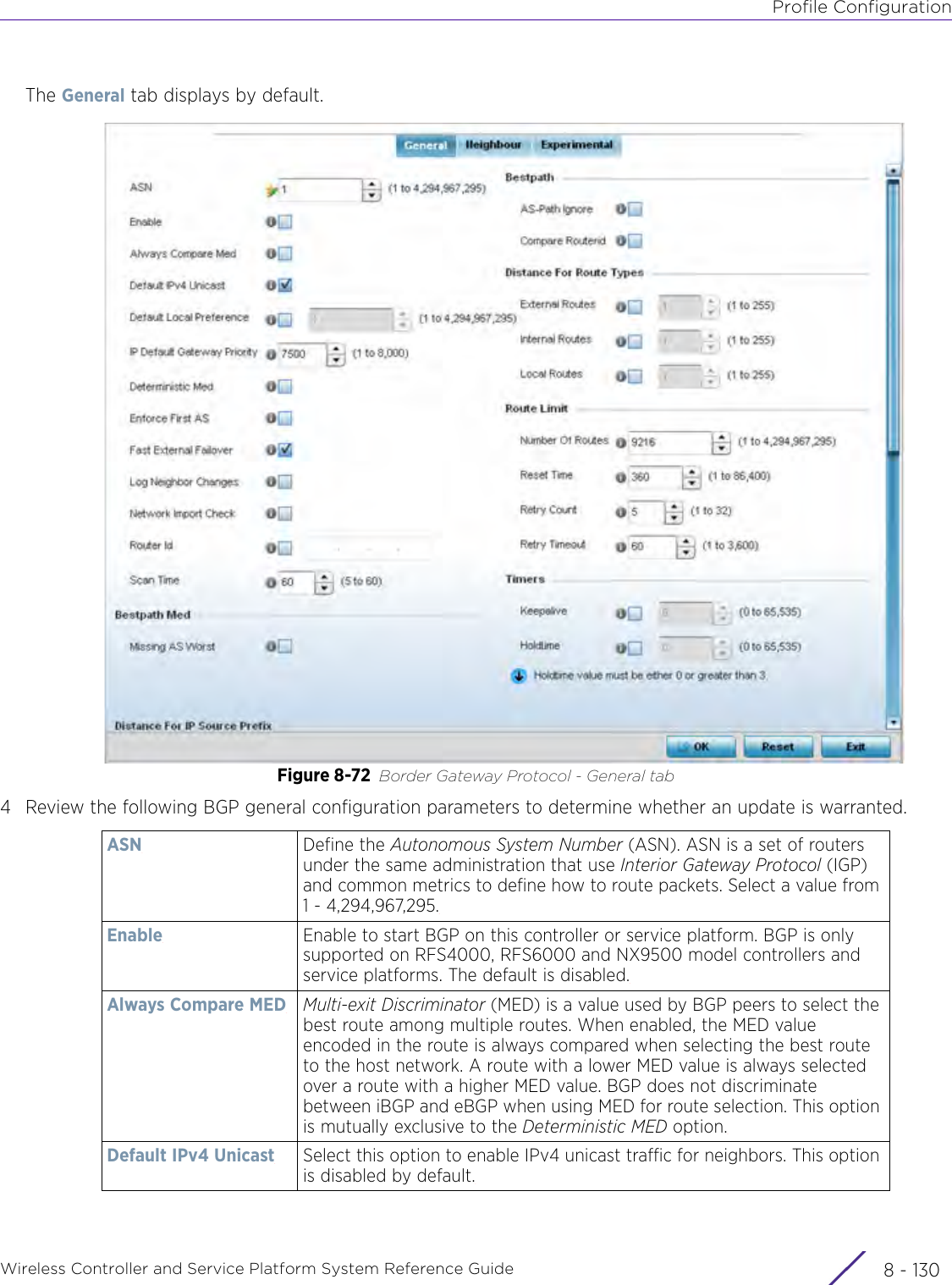
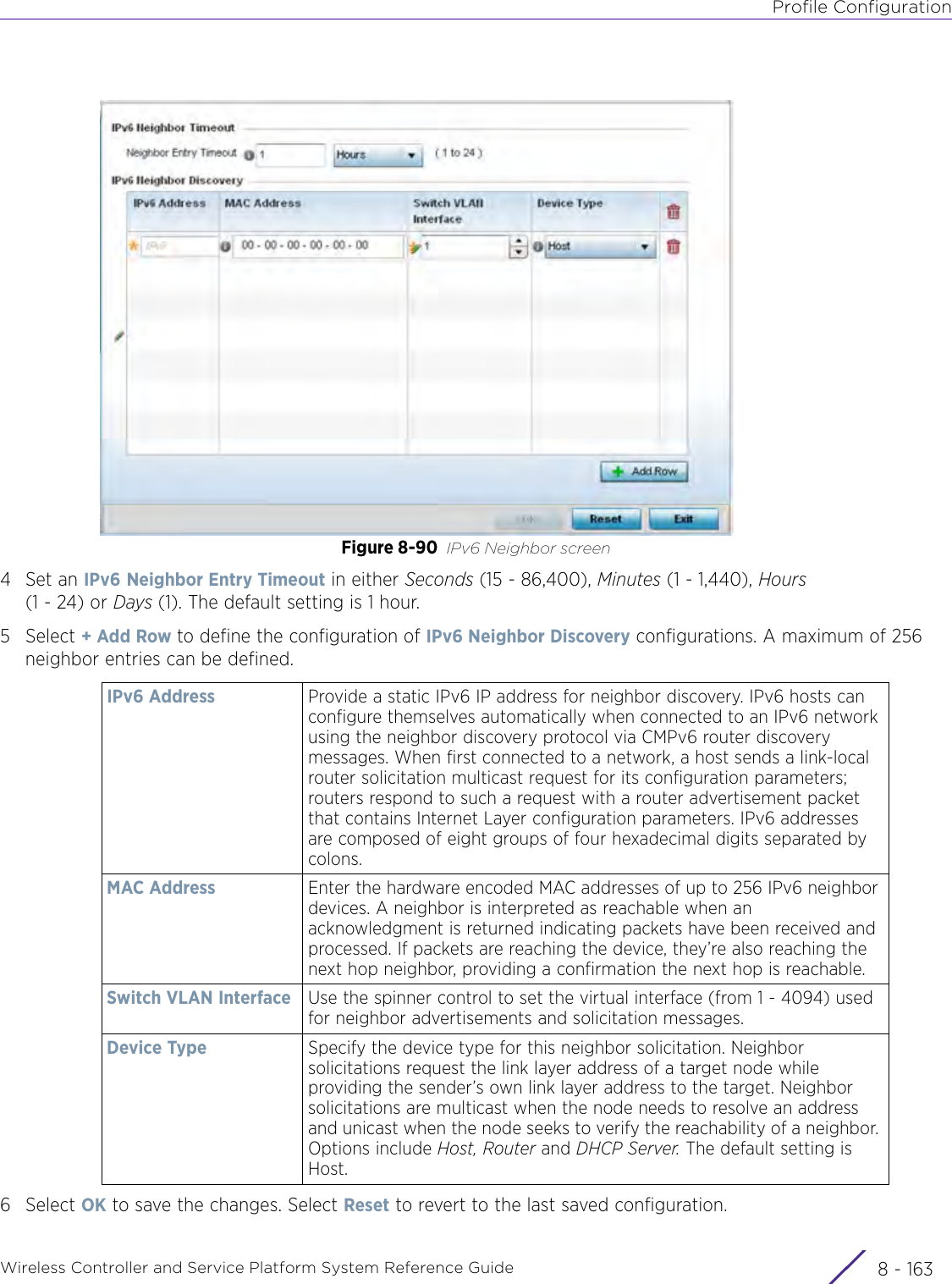
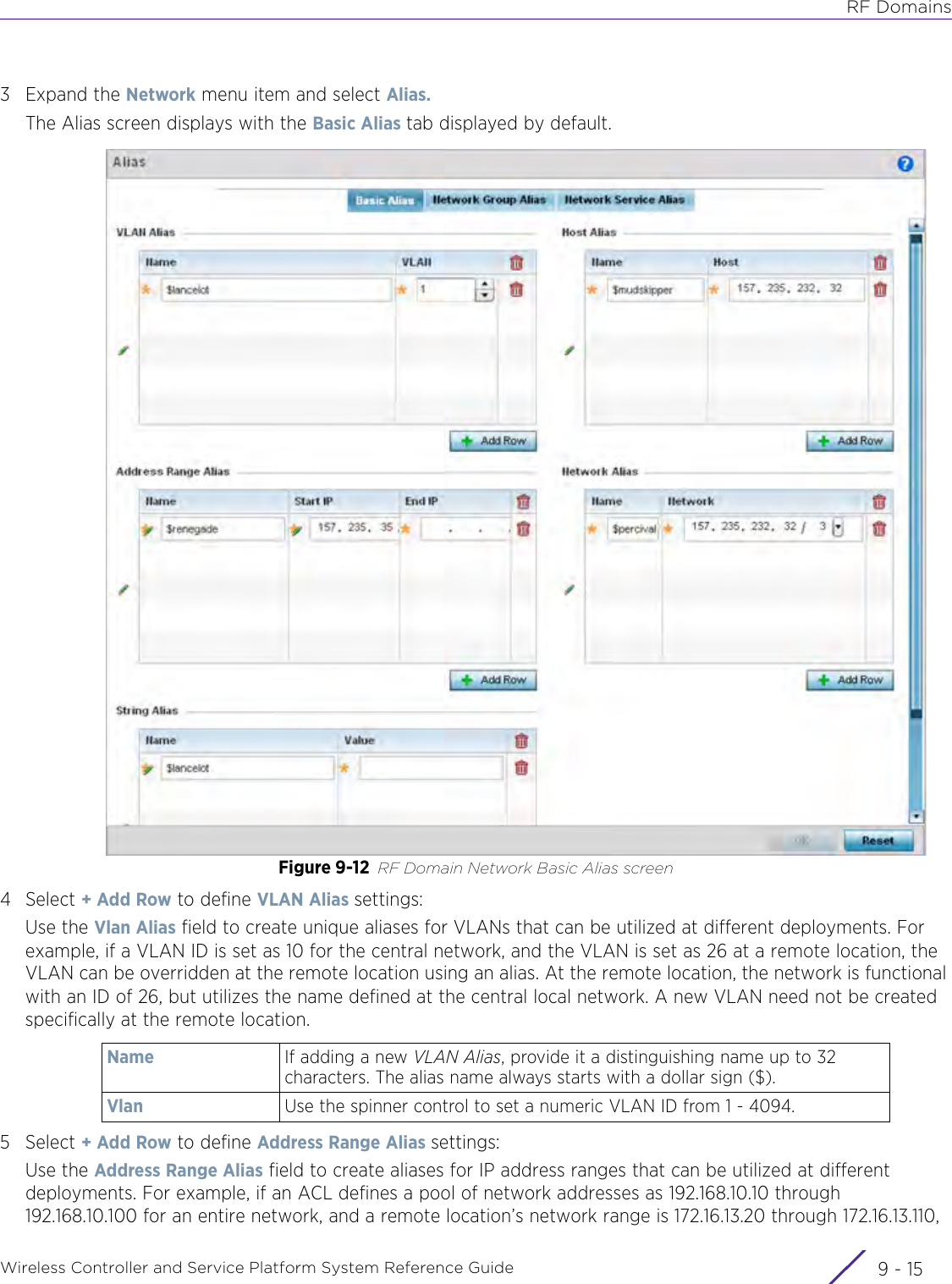
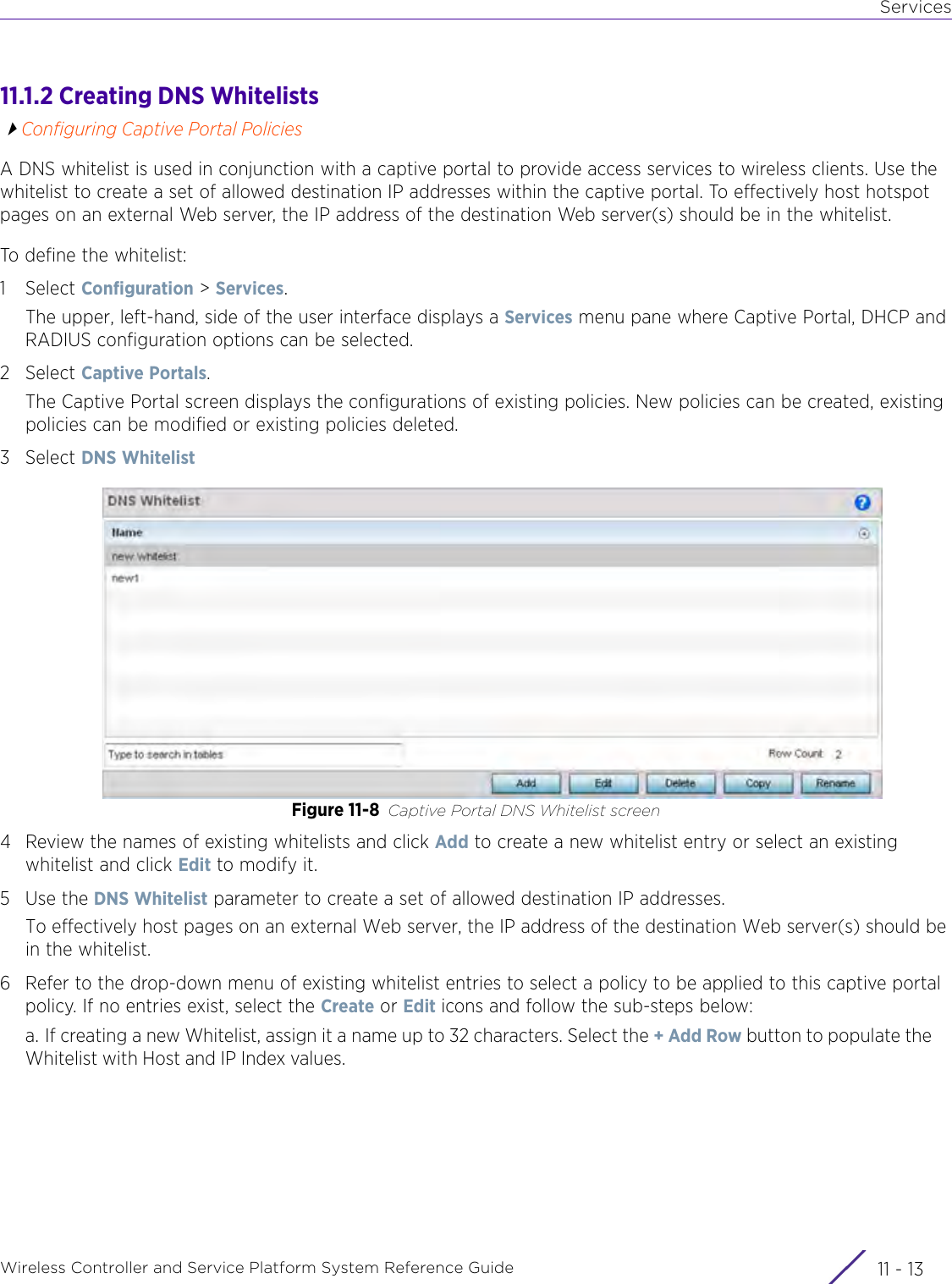
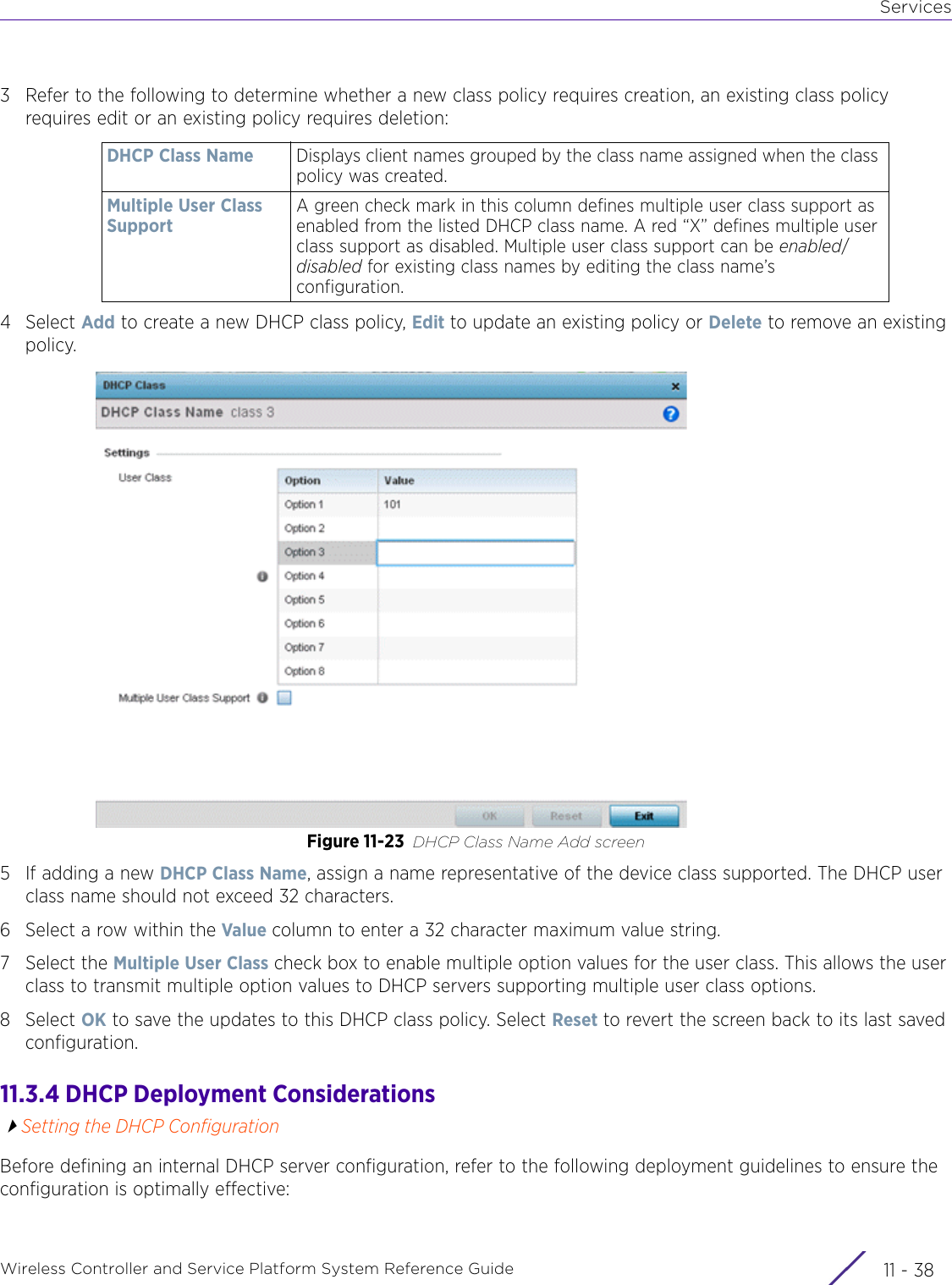
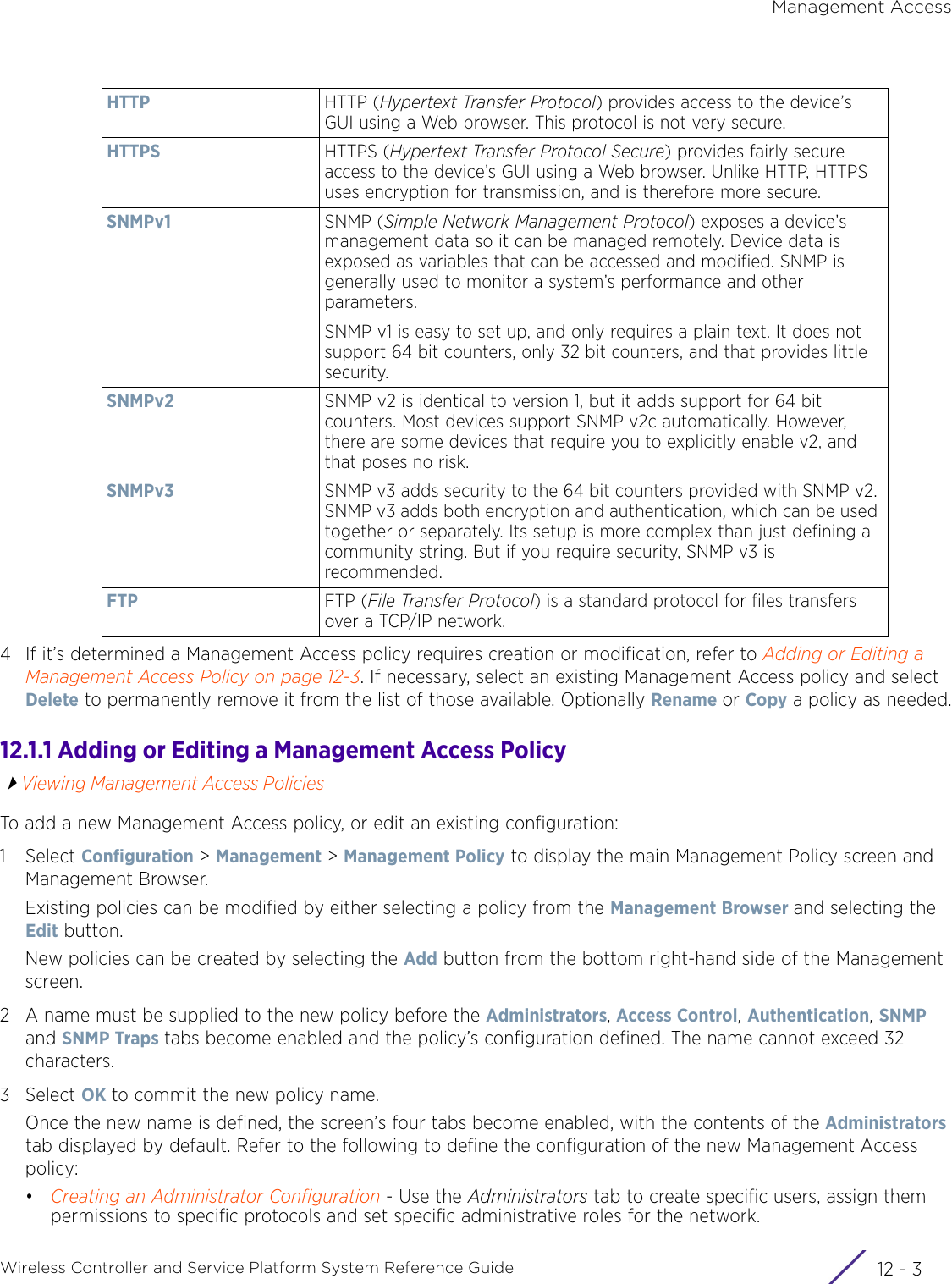
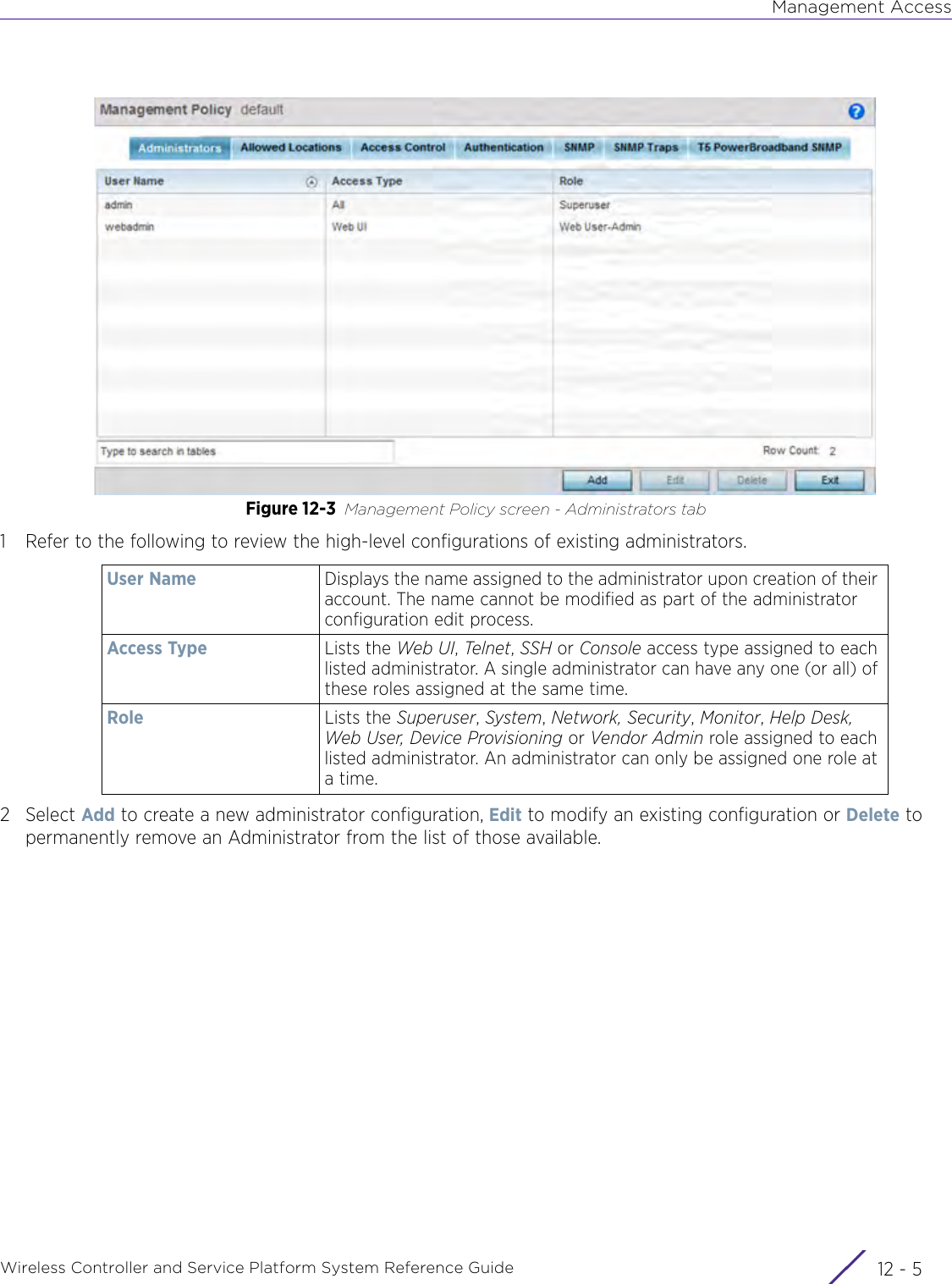
- 2. User Manual-AP7662
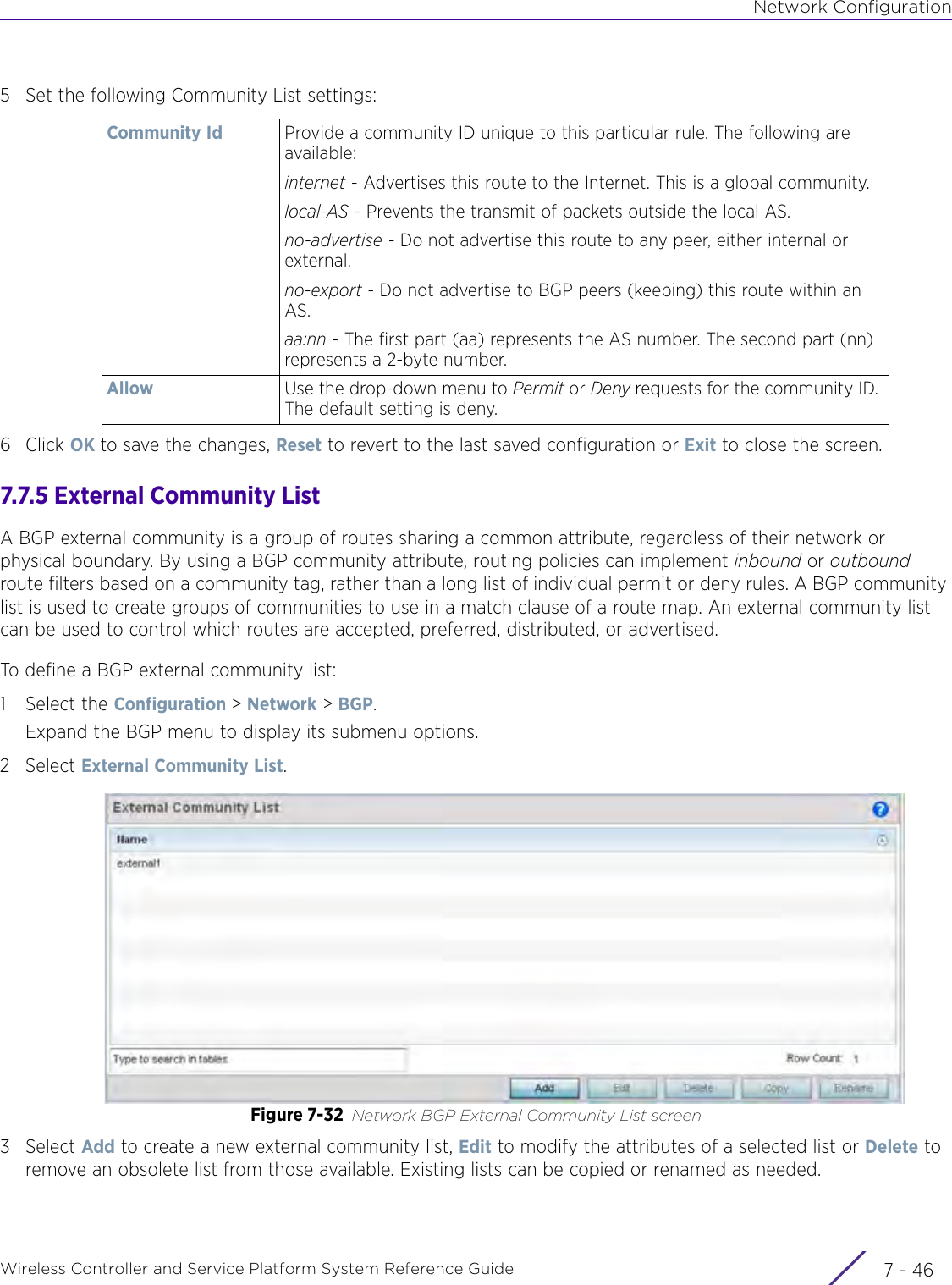
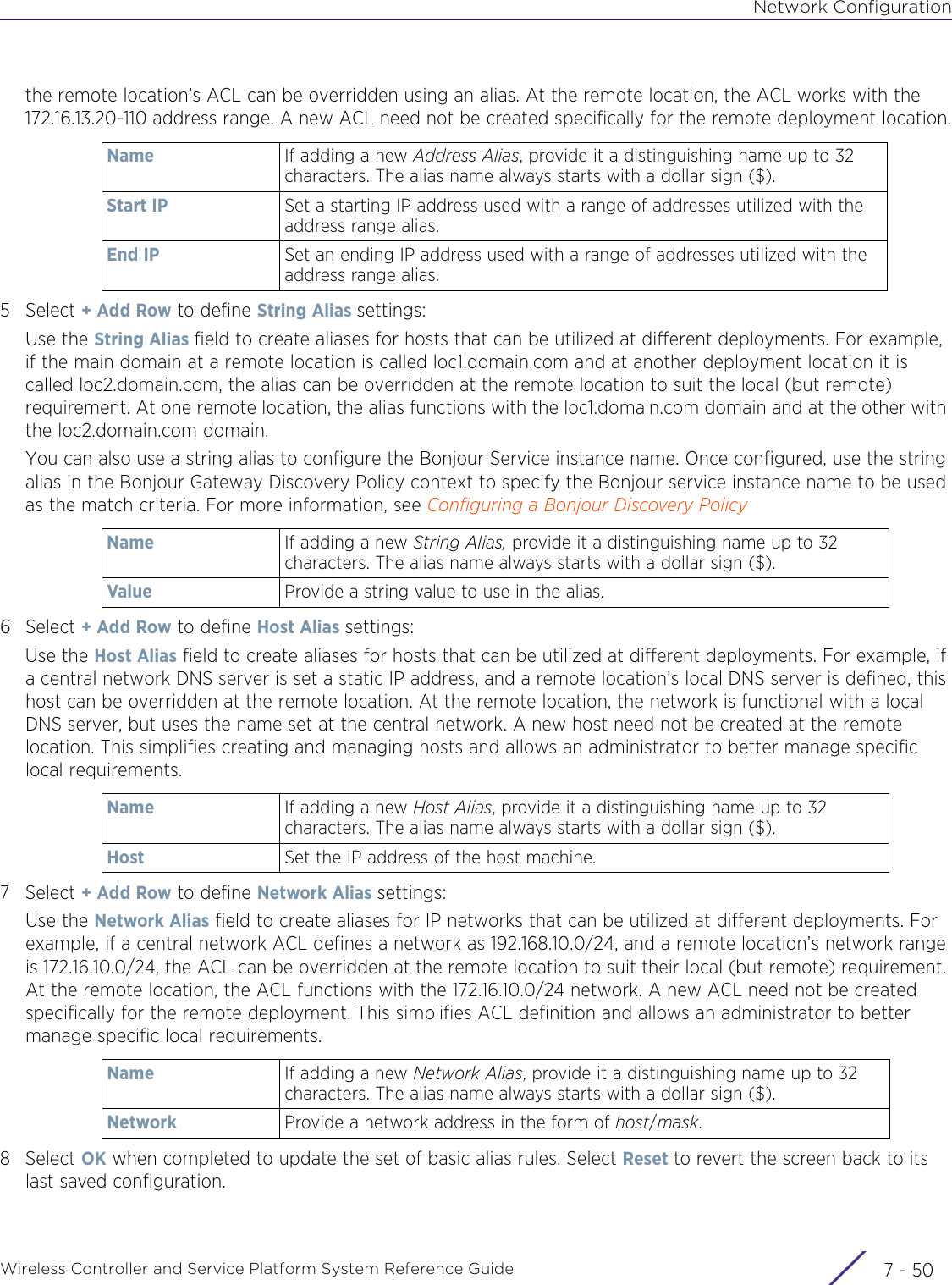
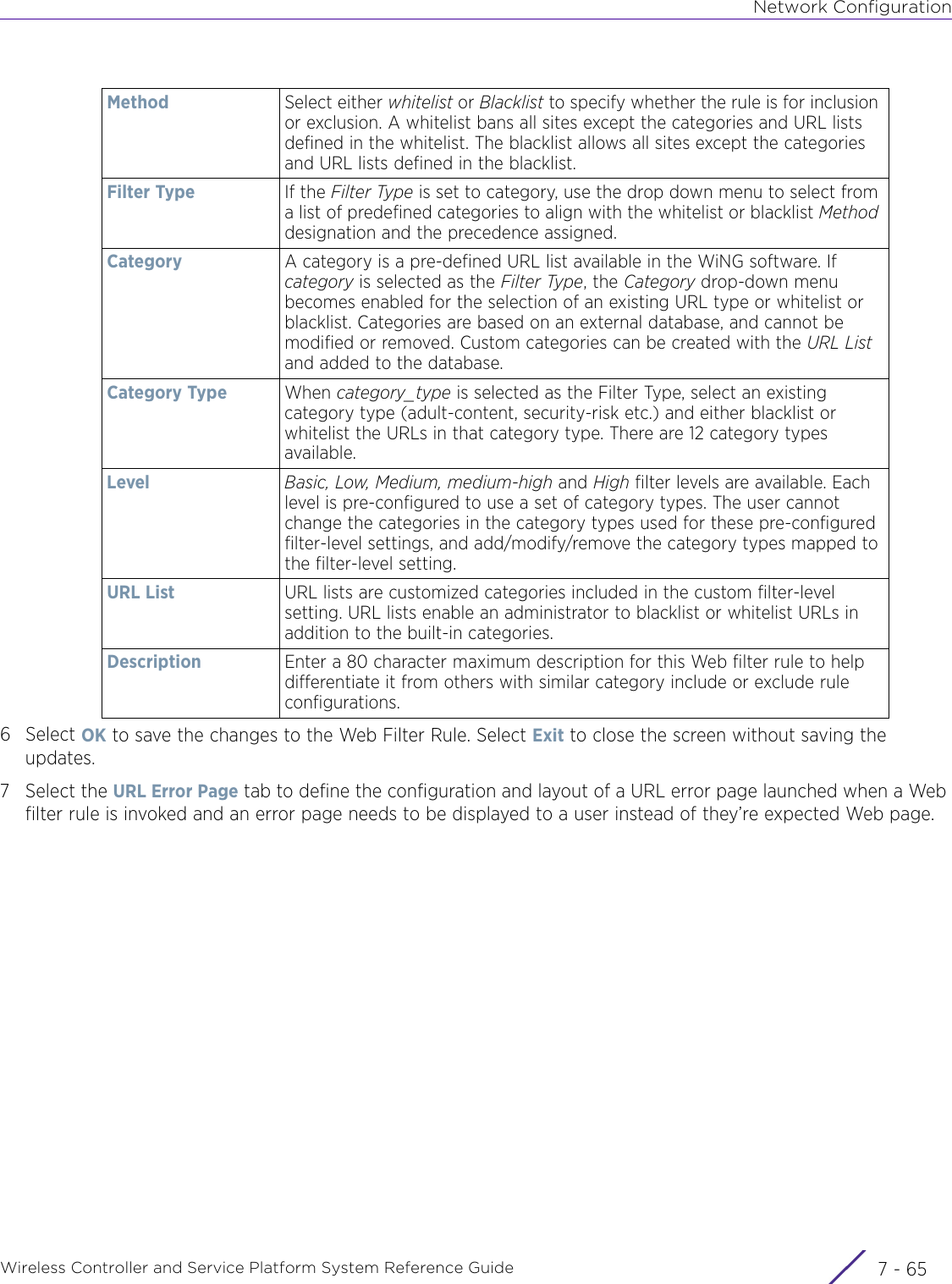
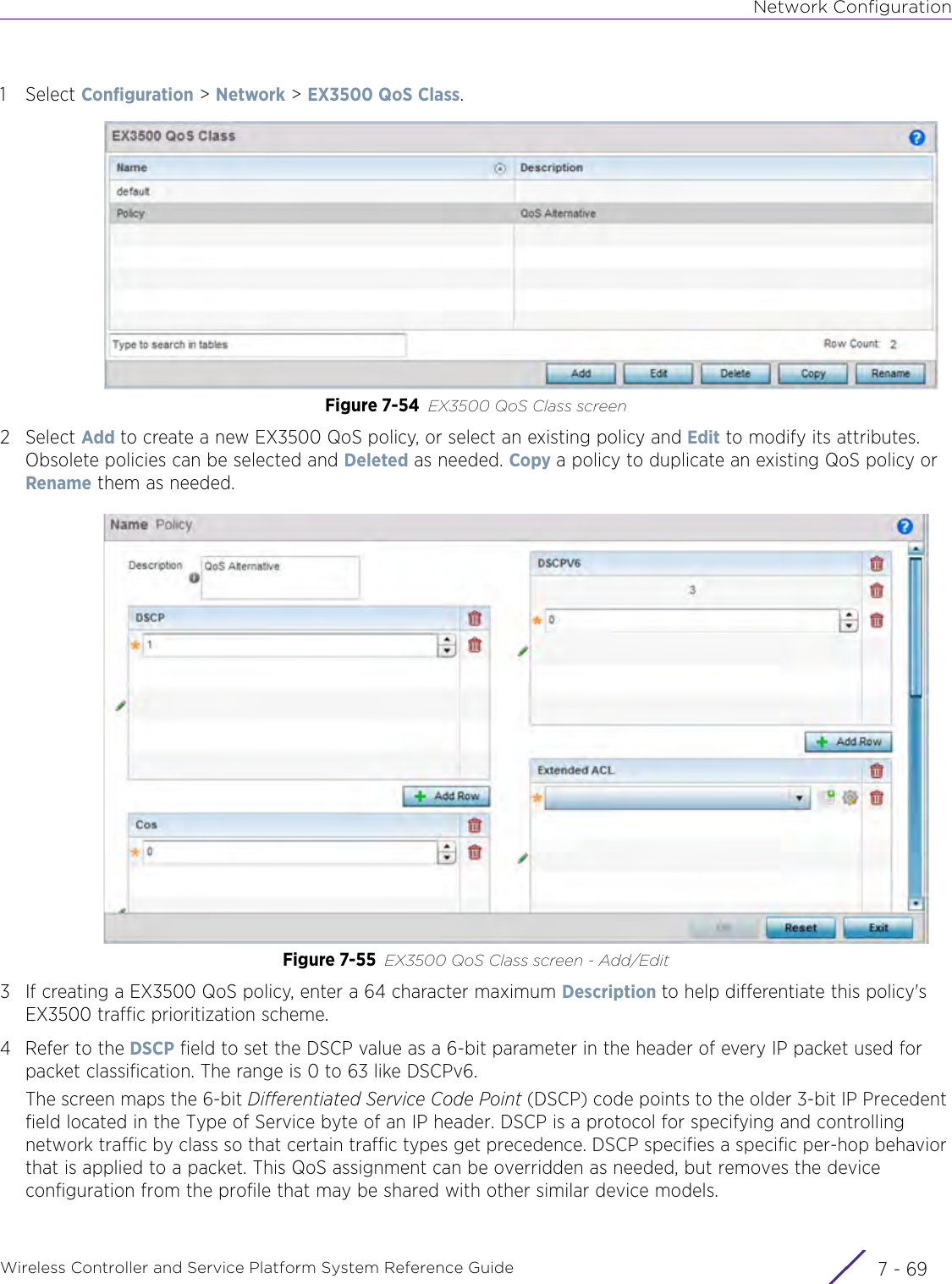
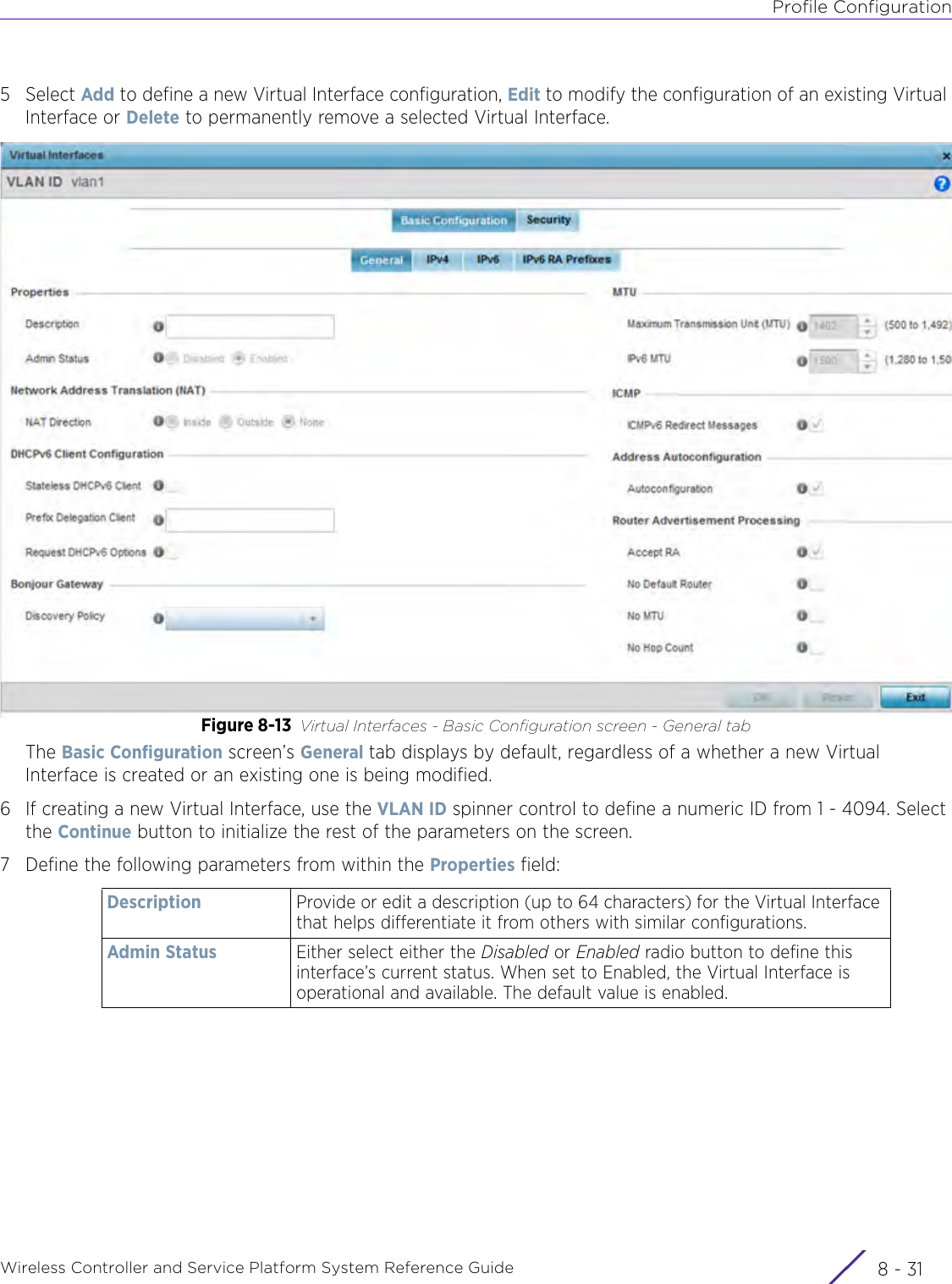
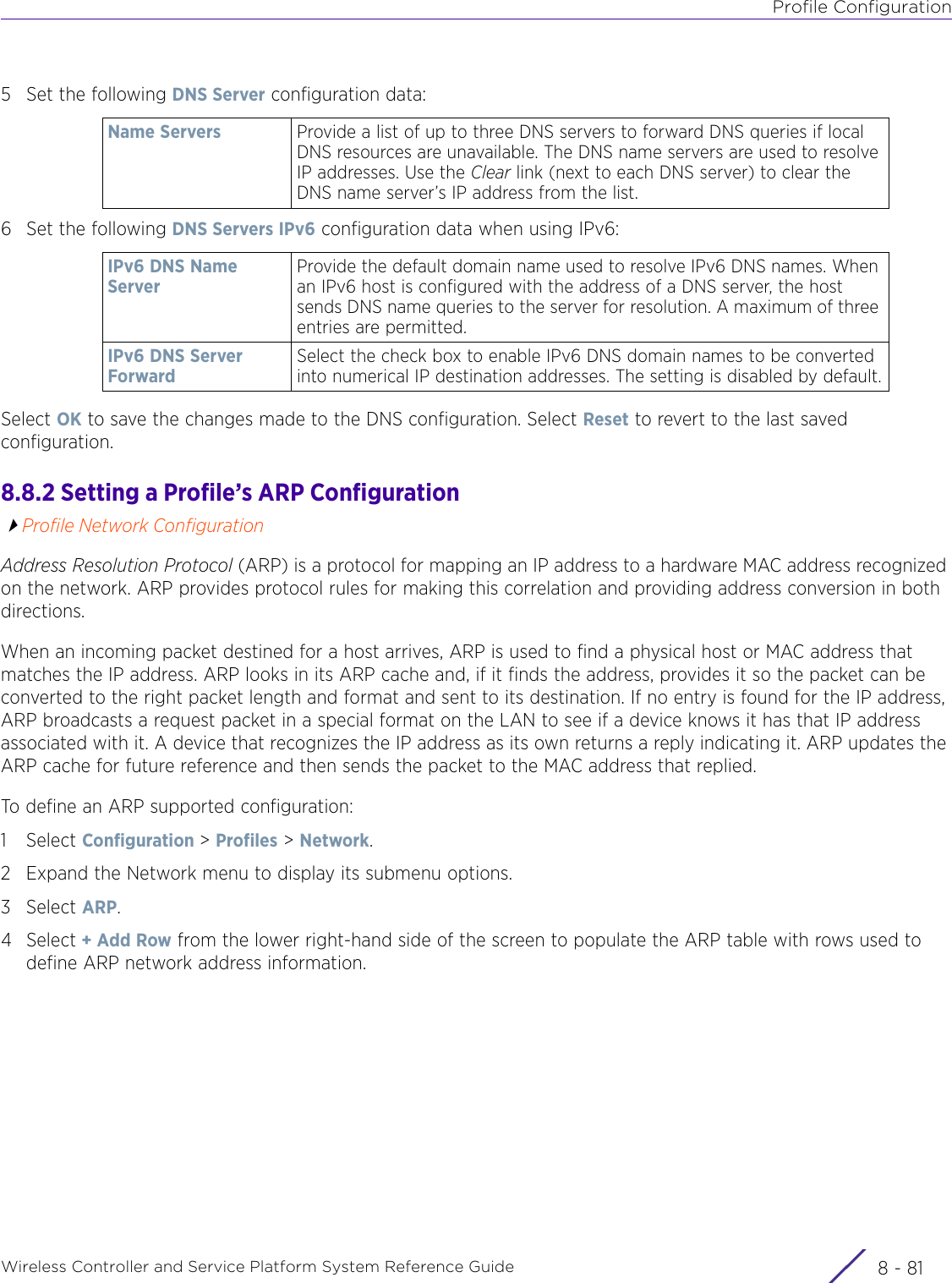
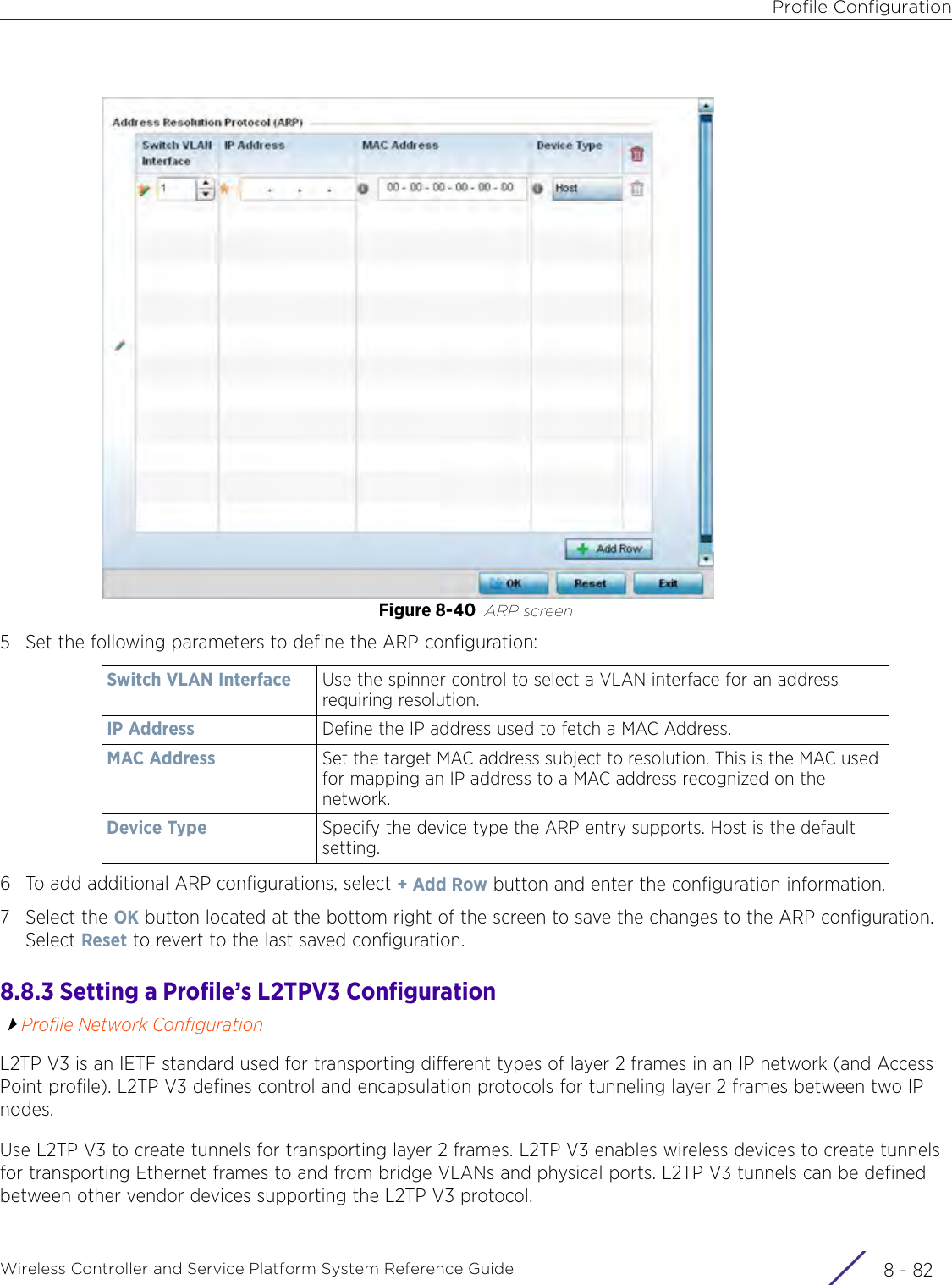
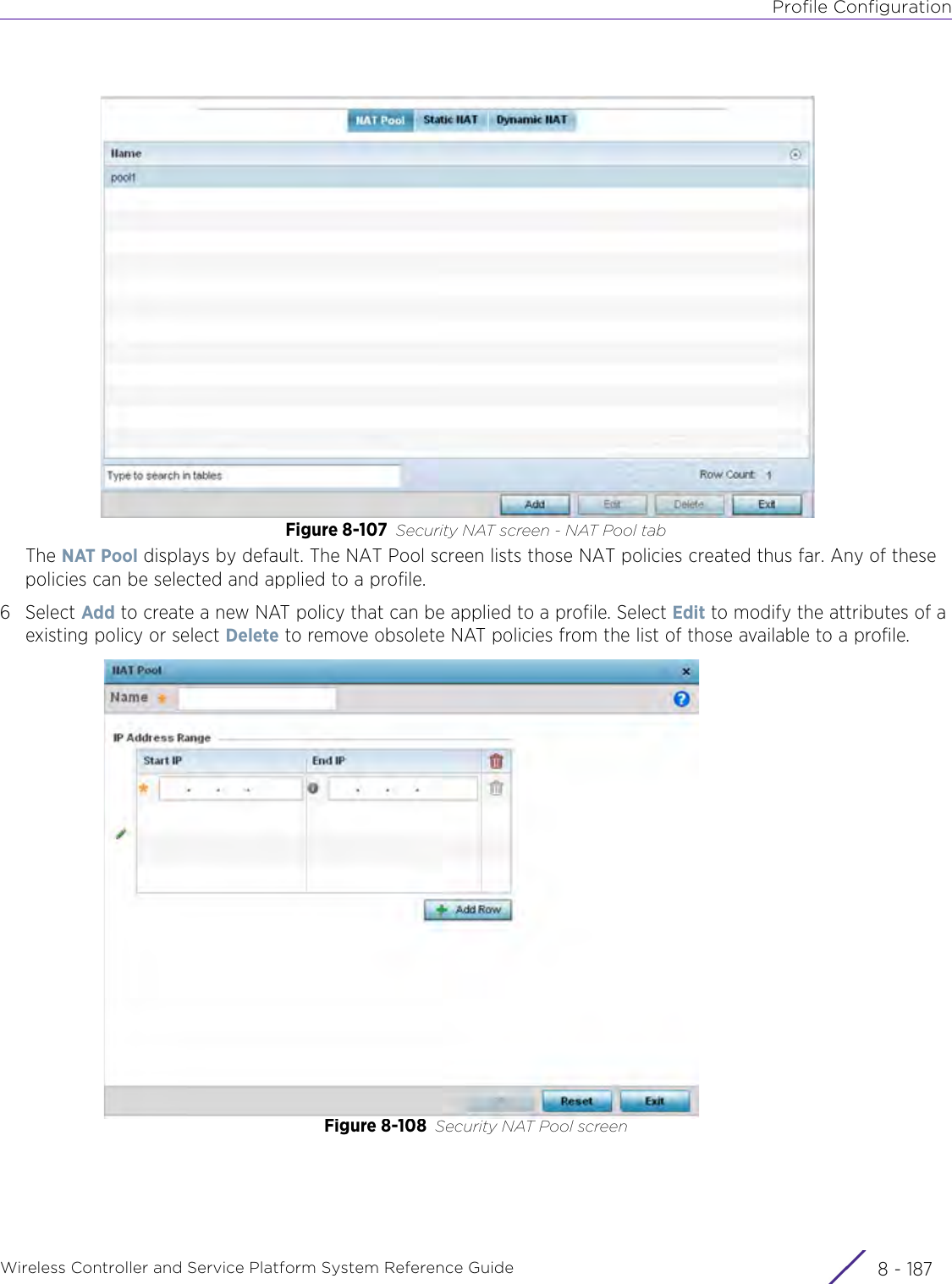
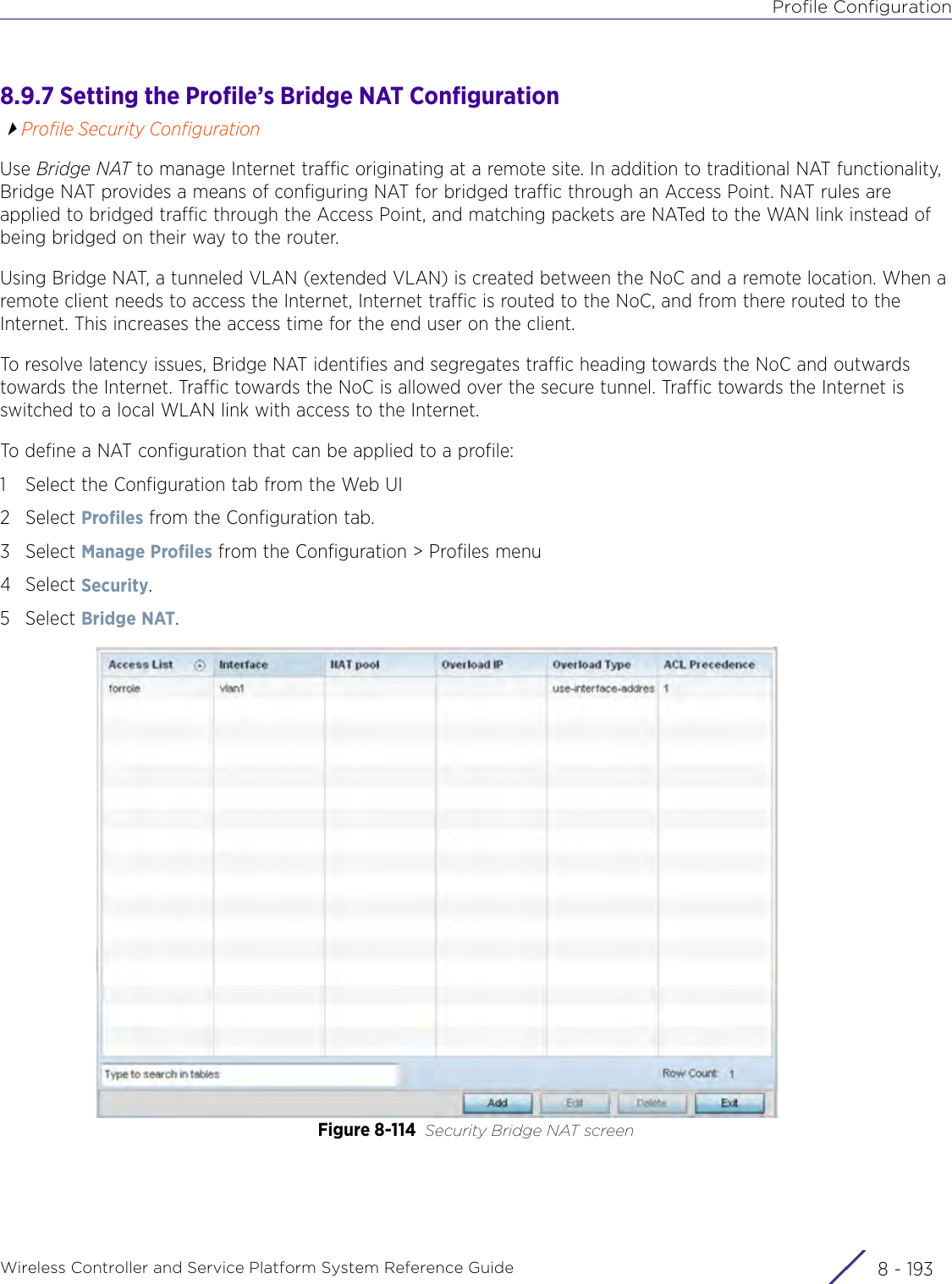
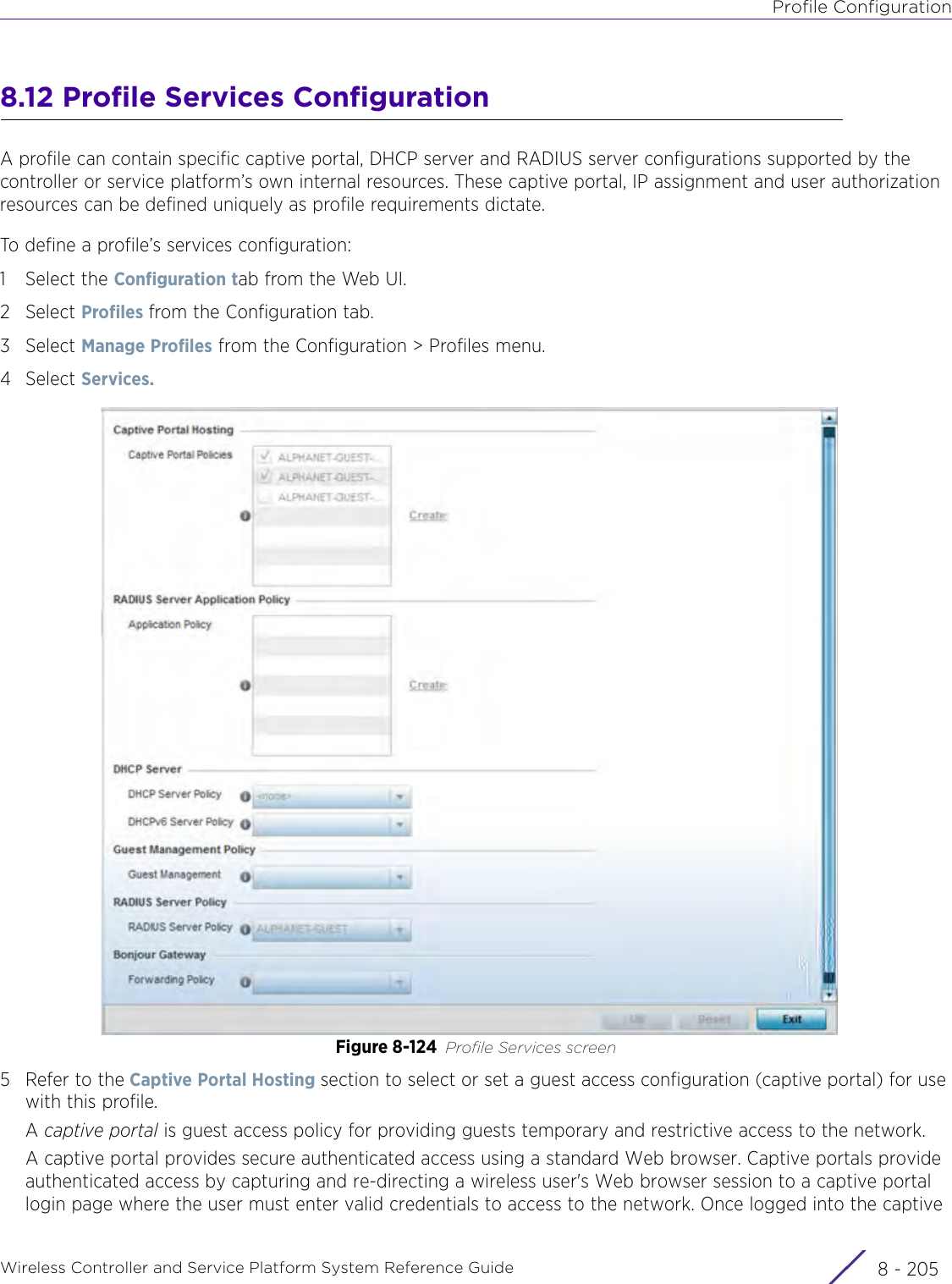
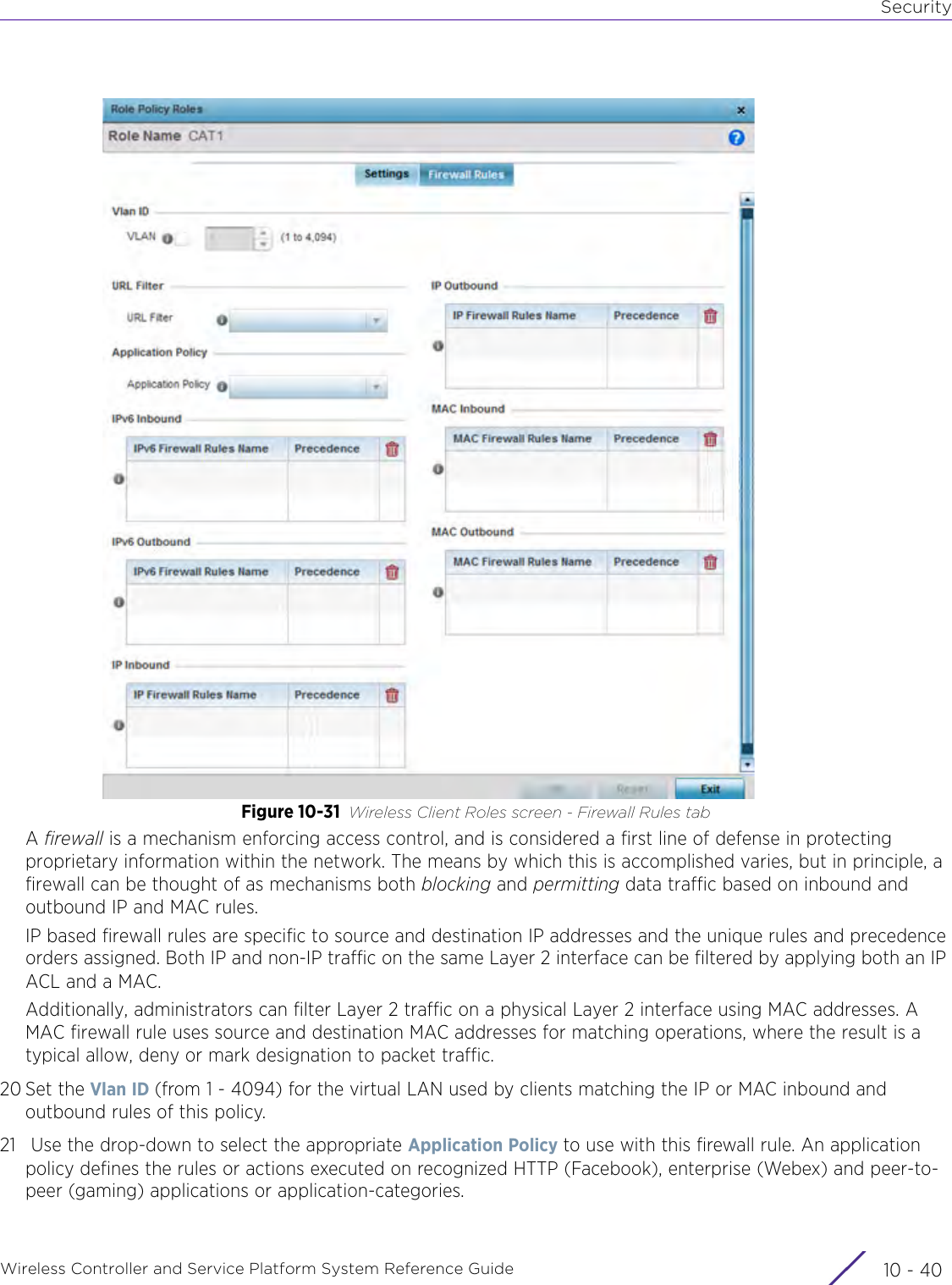
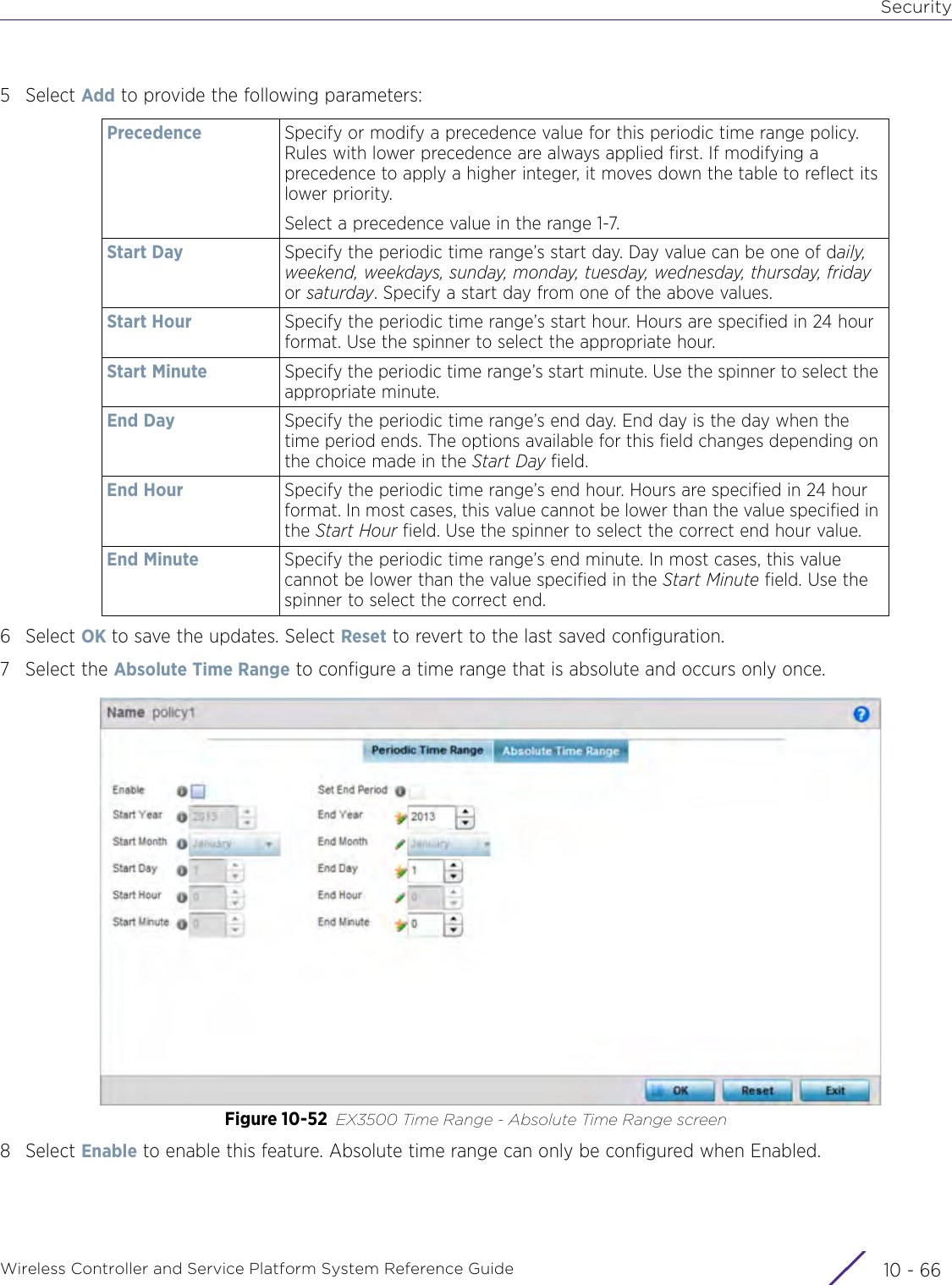
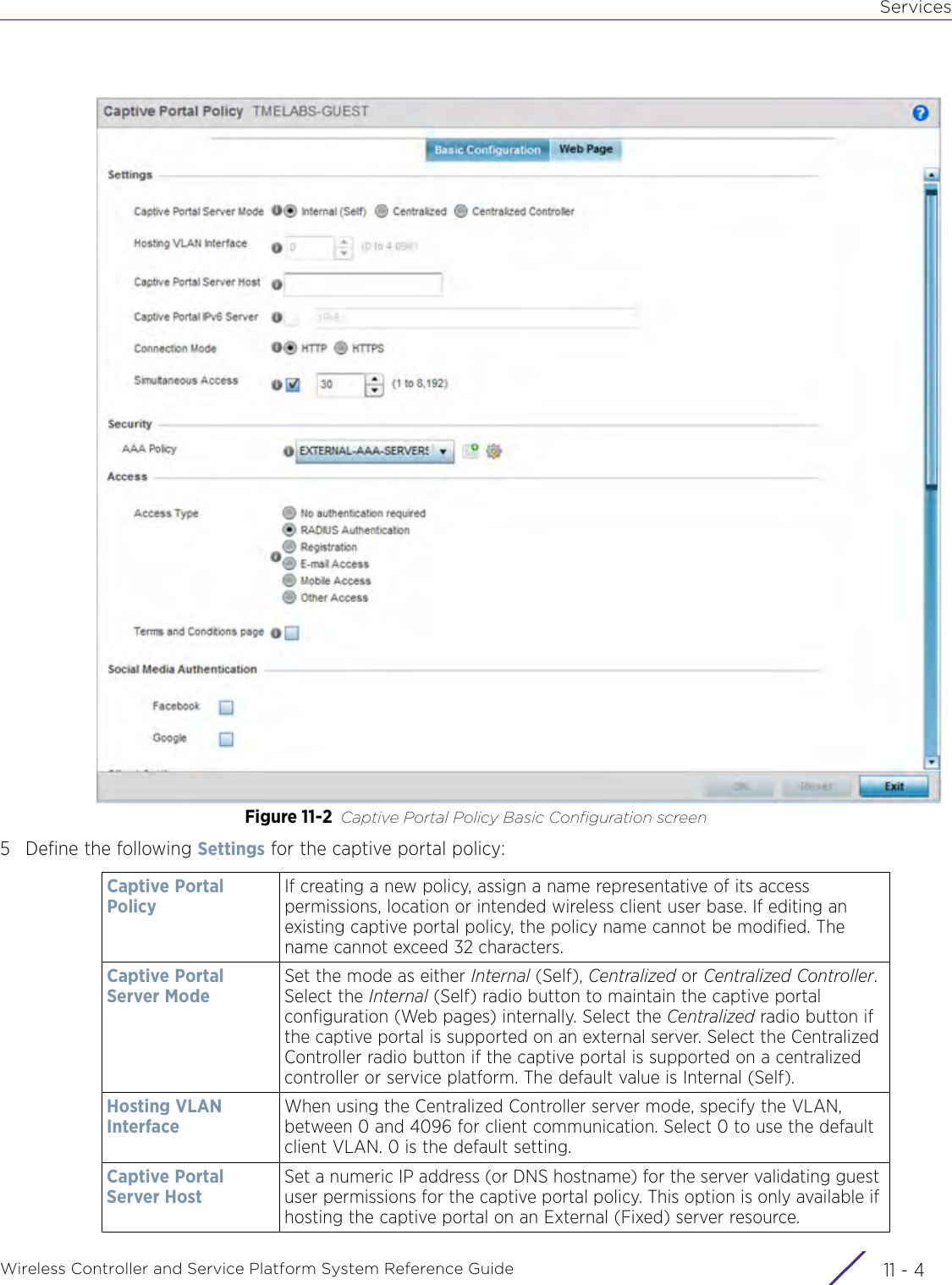
- 3. User Manual-AP3917e R1
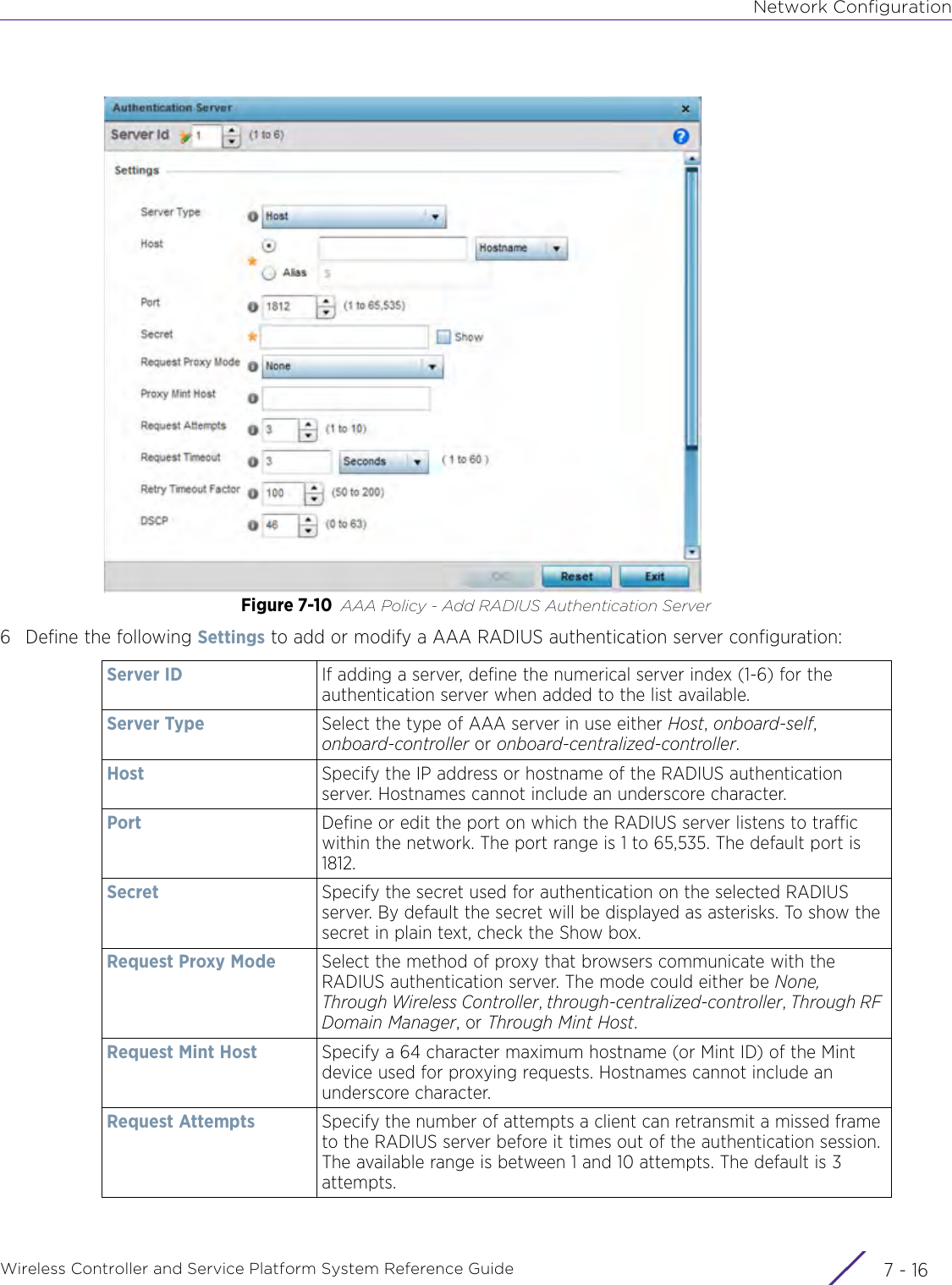
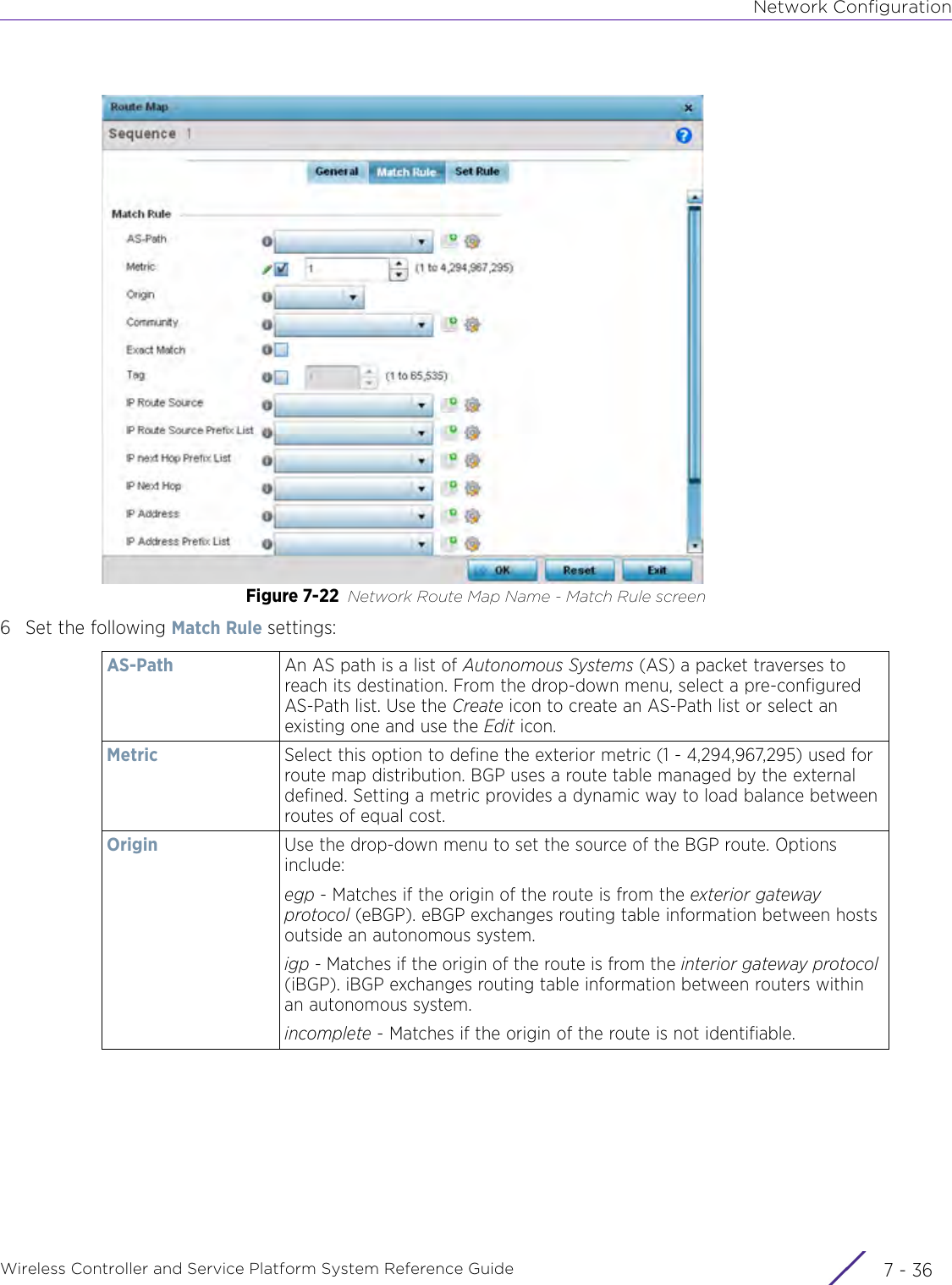
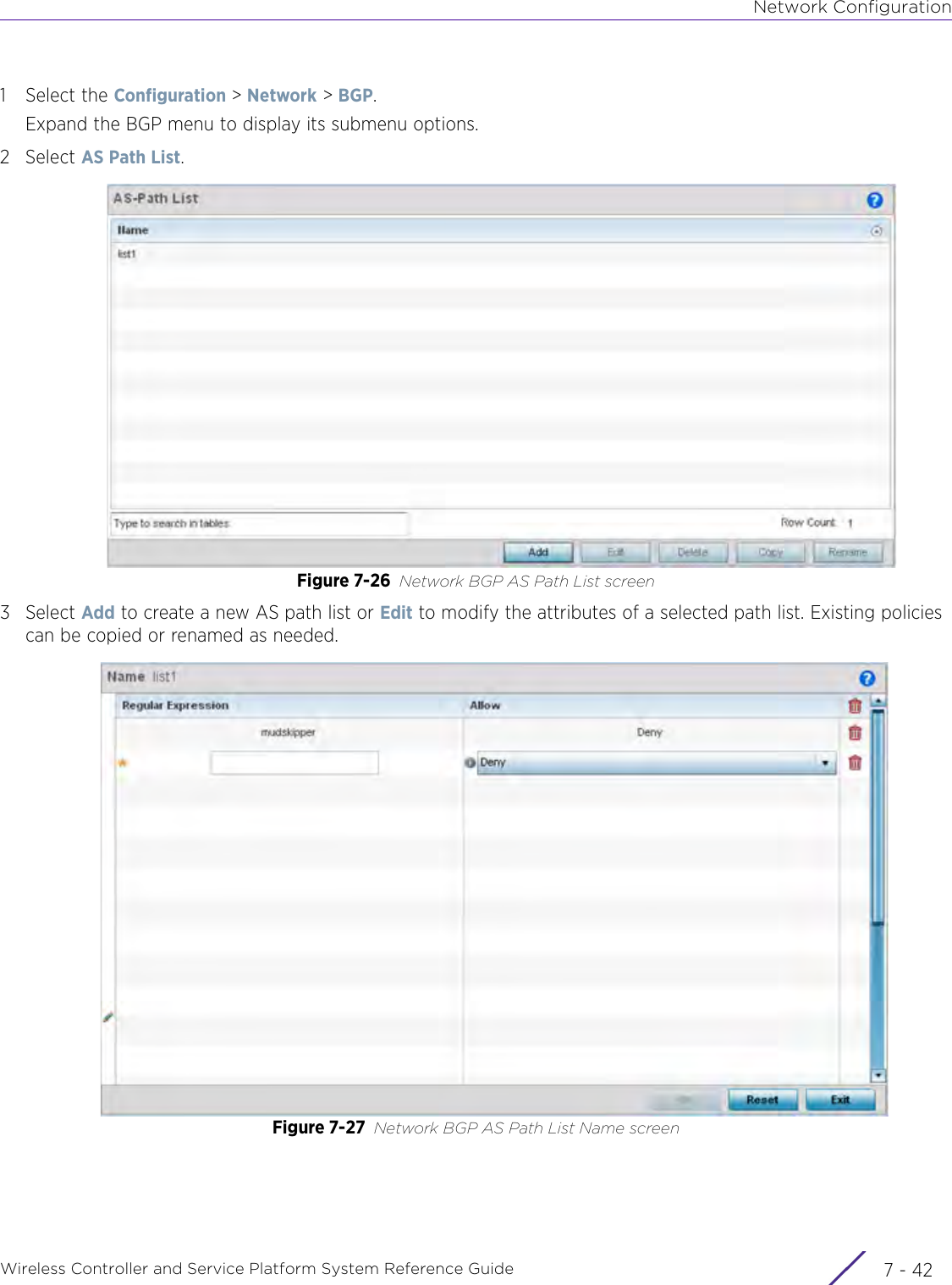
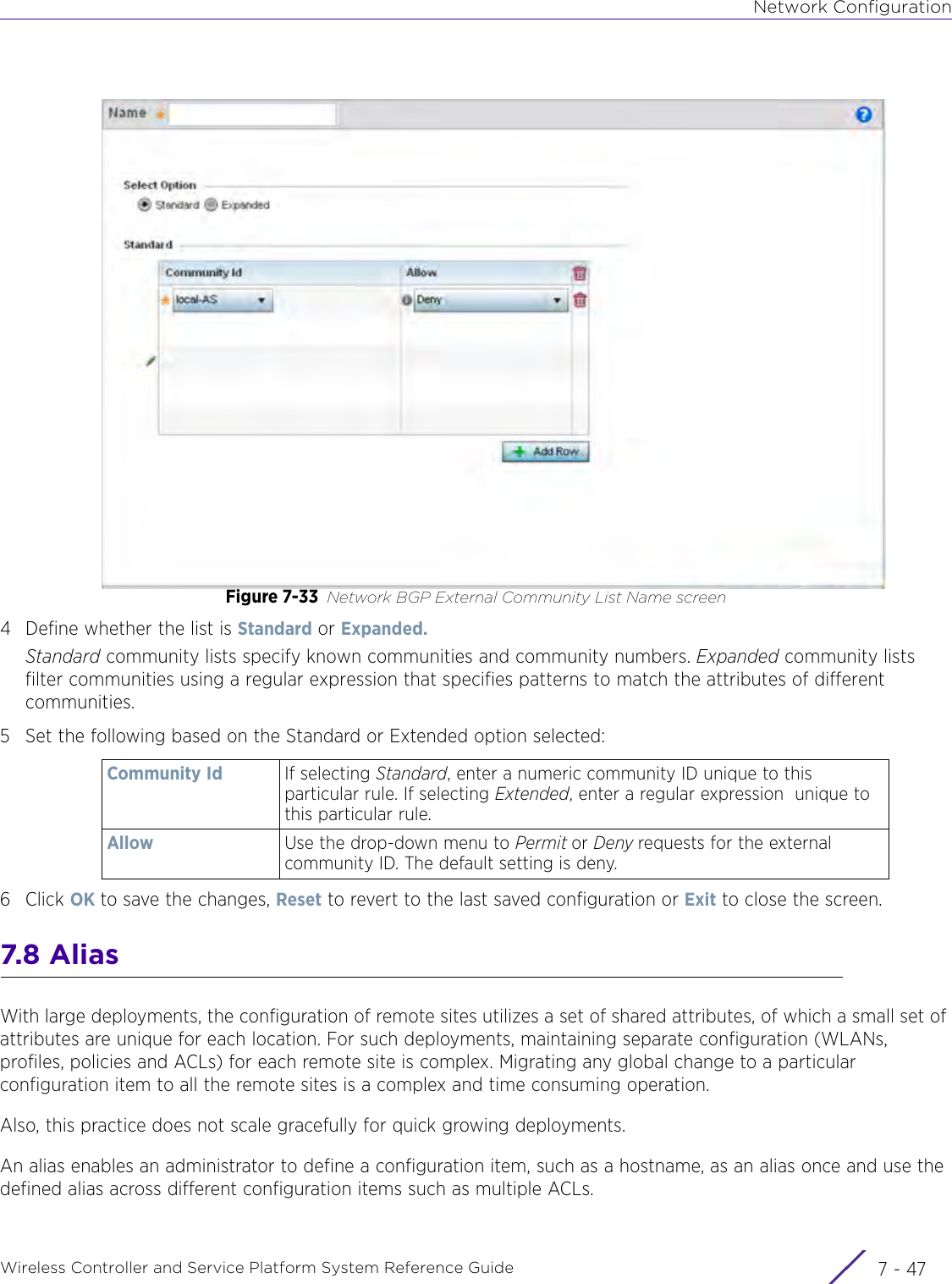
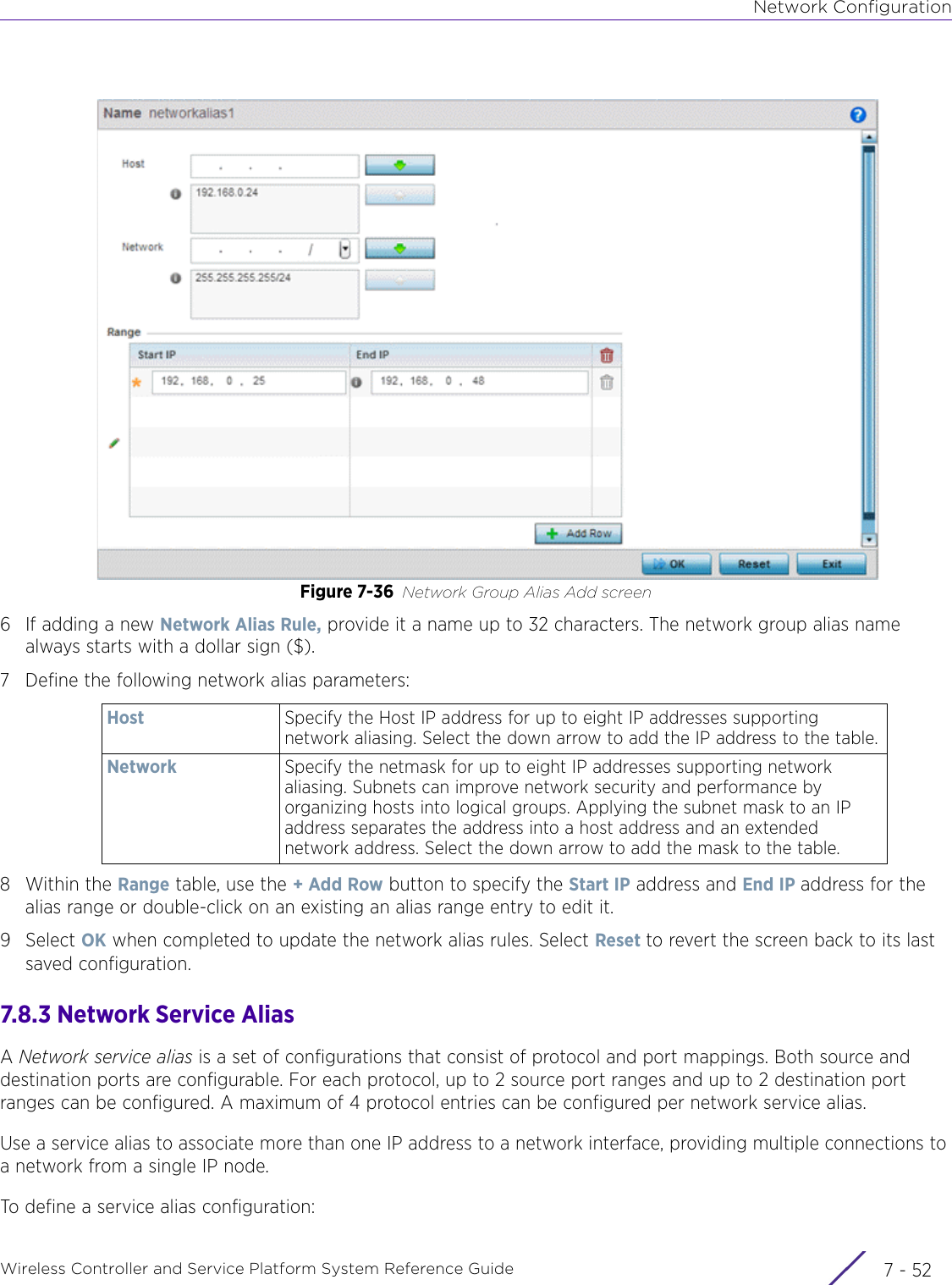
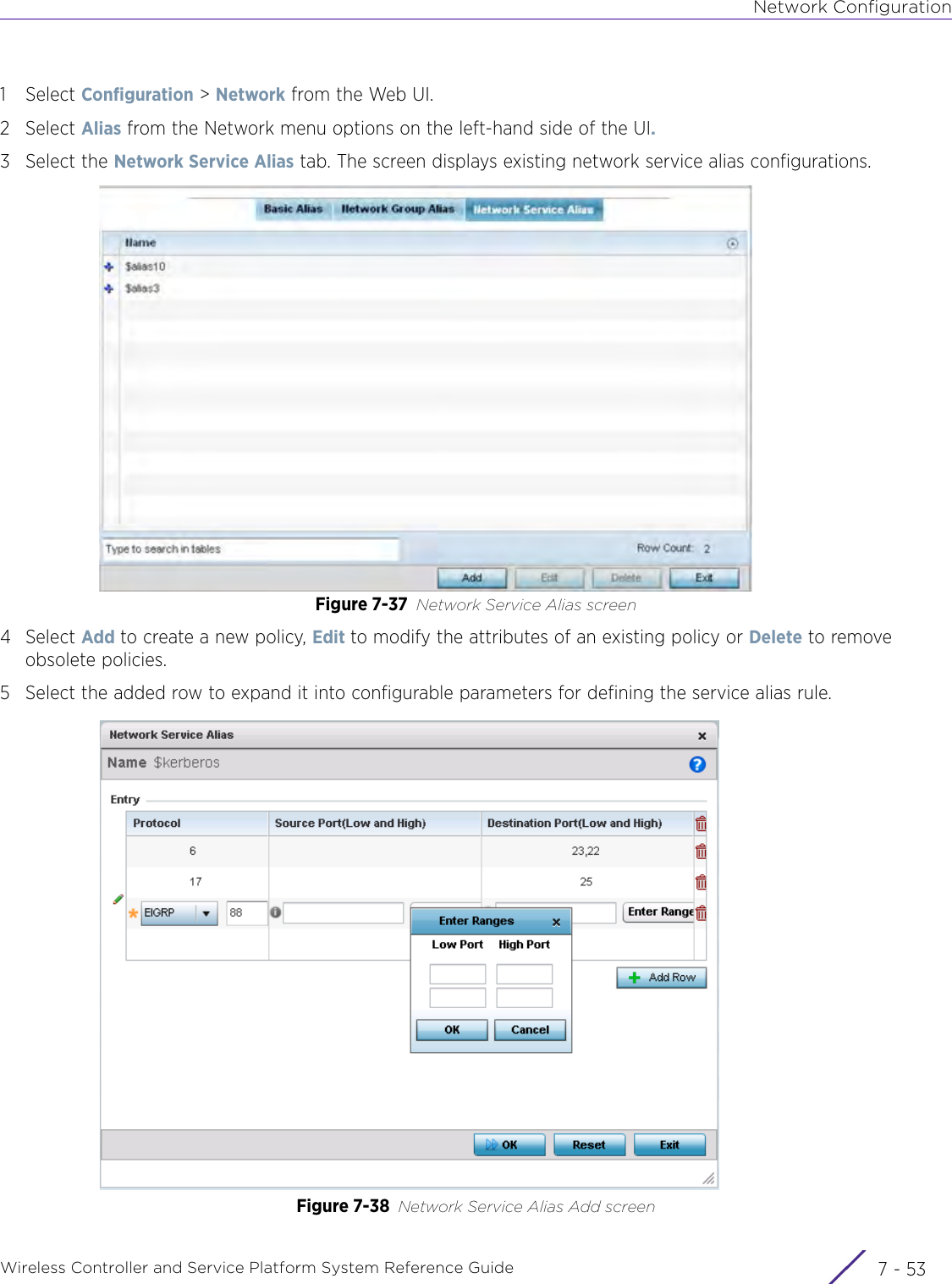
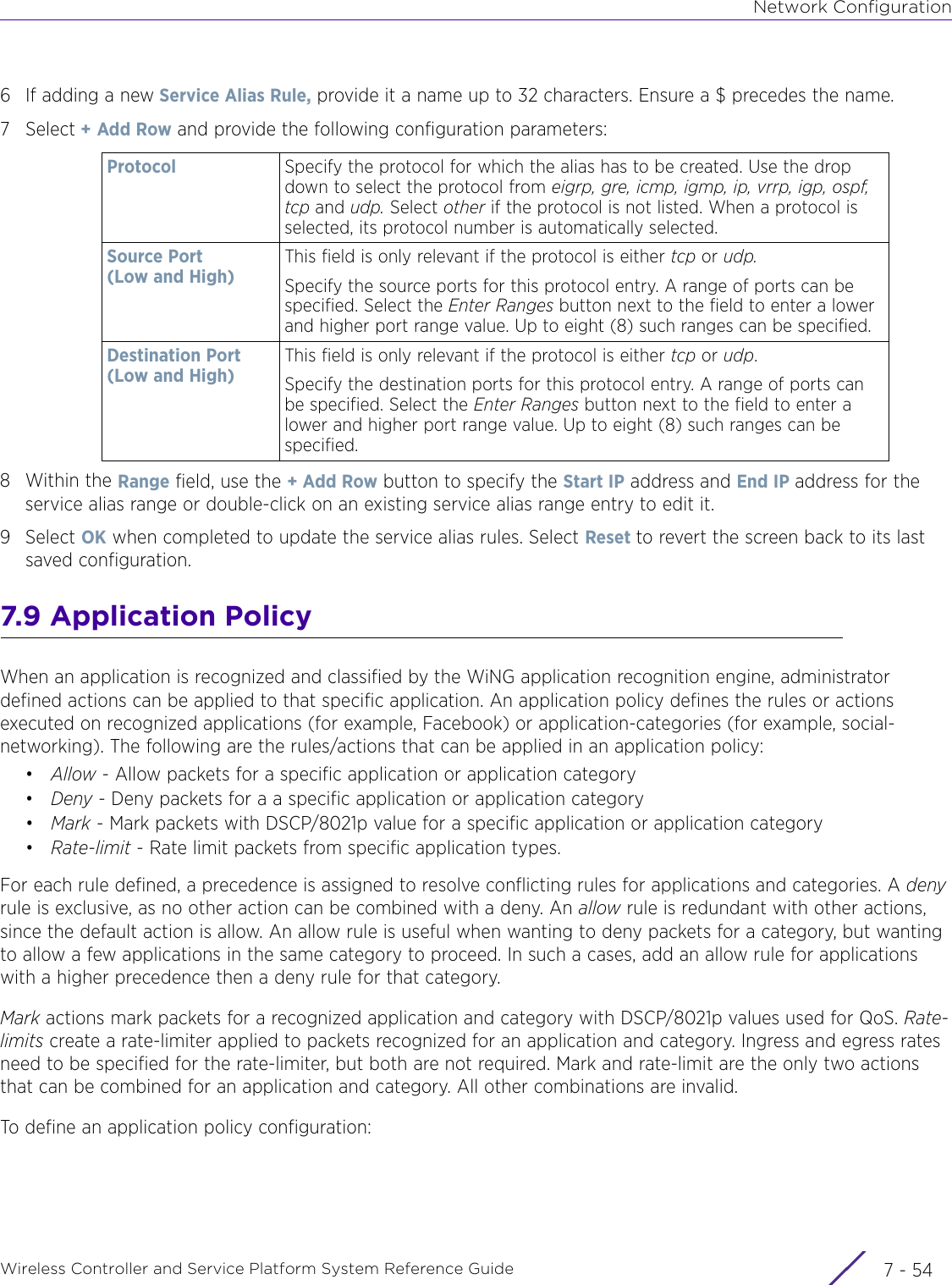
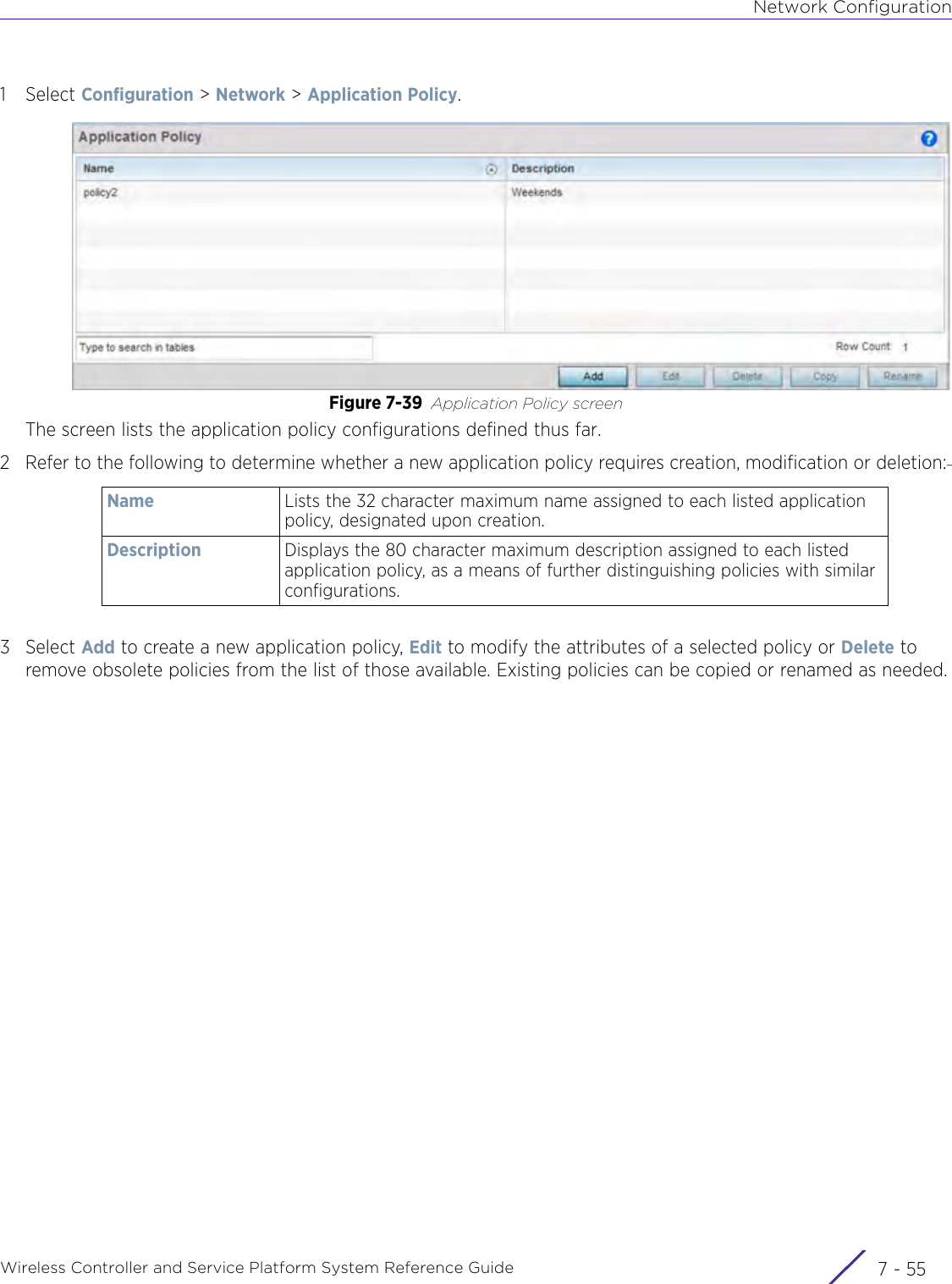
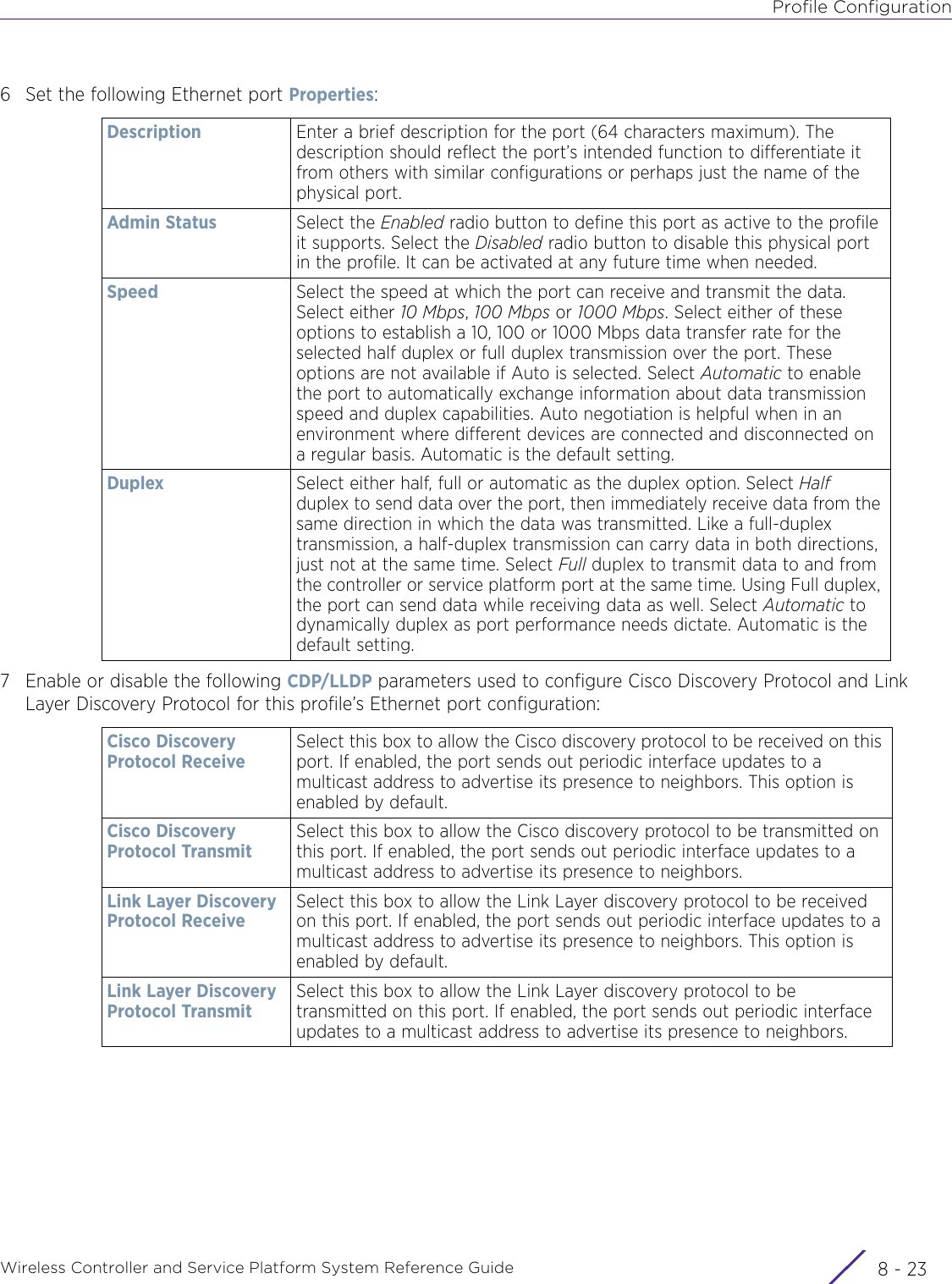
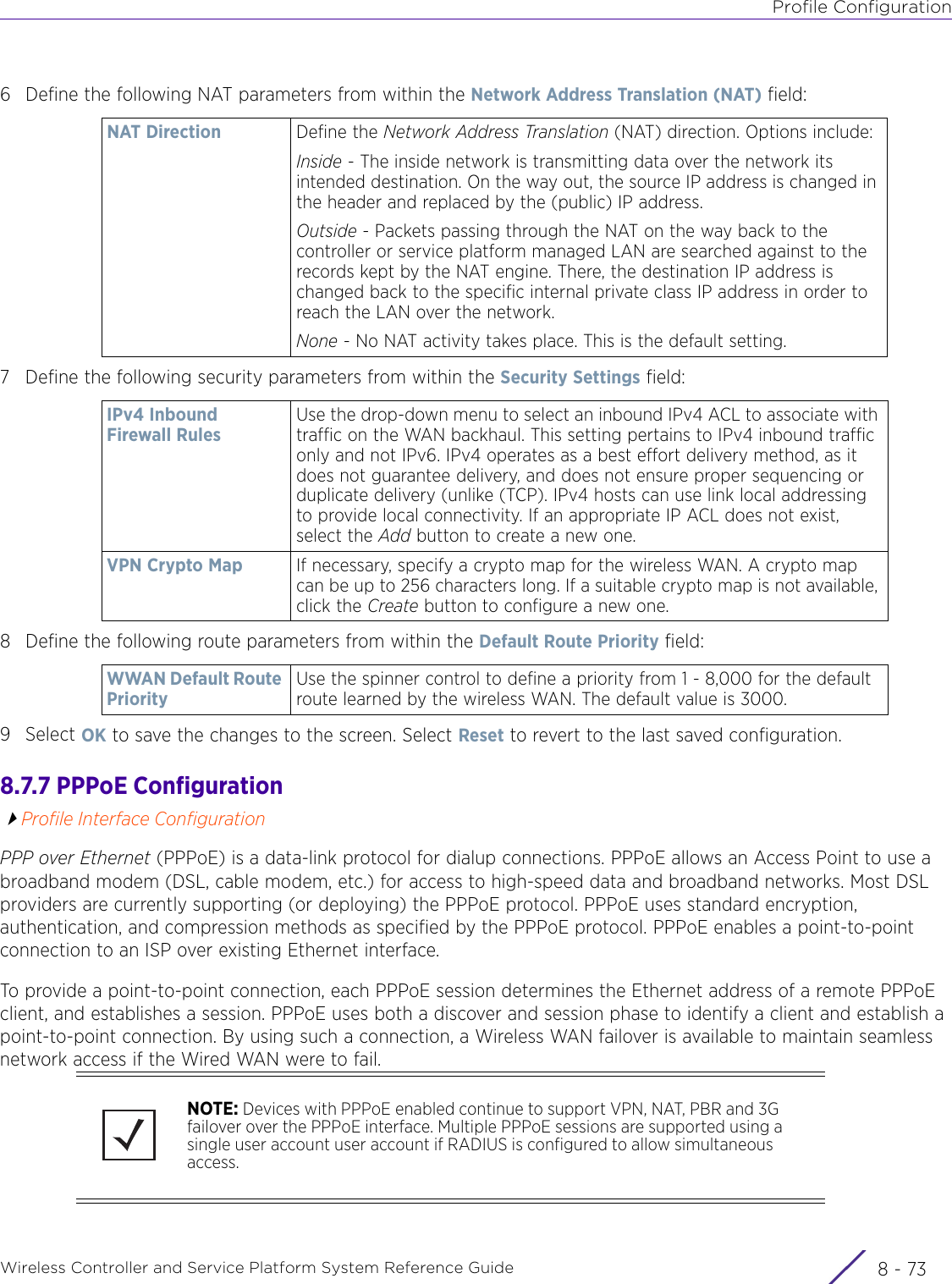
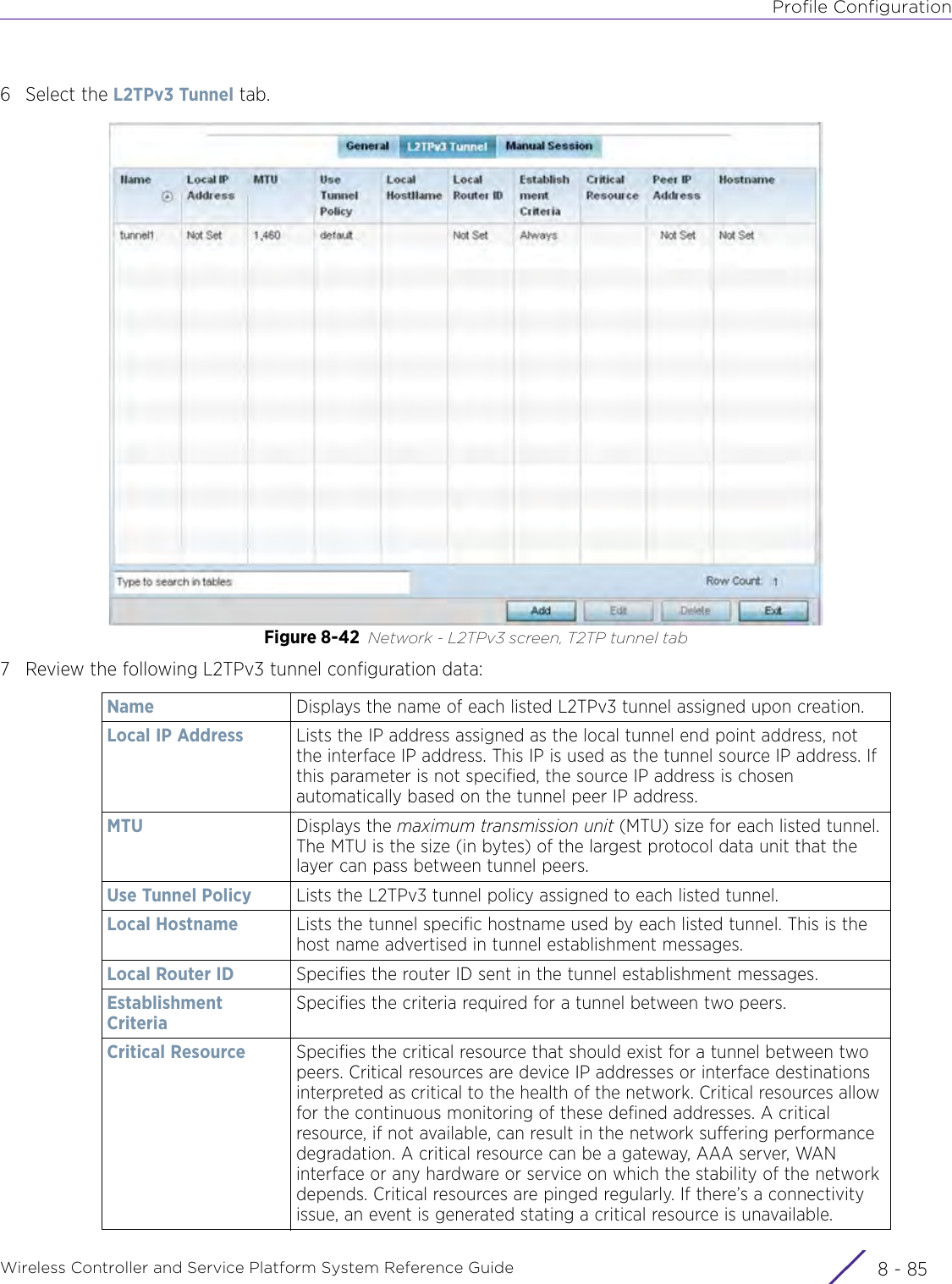
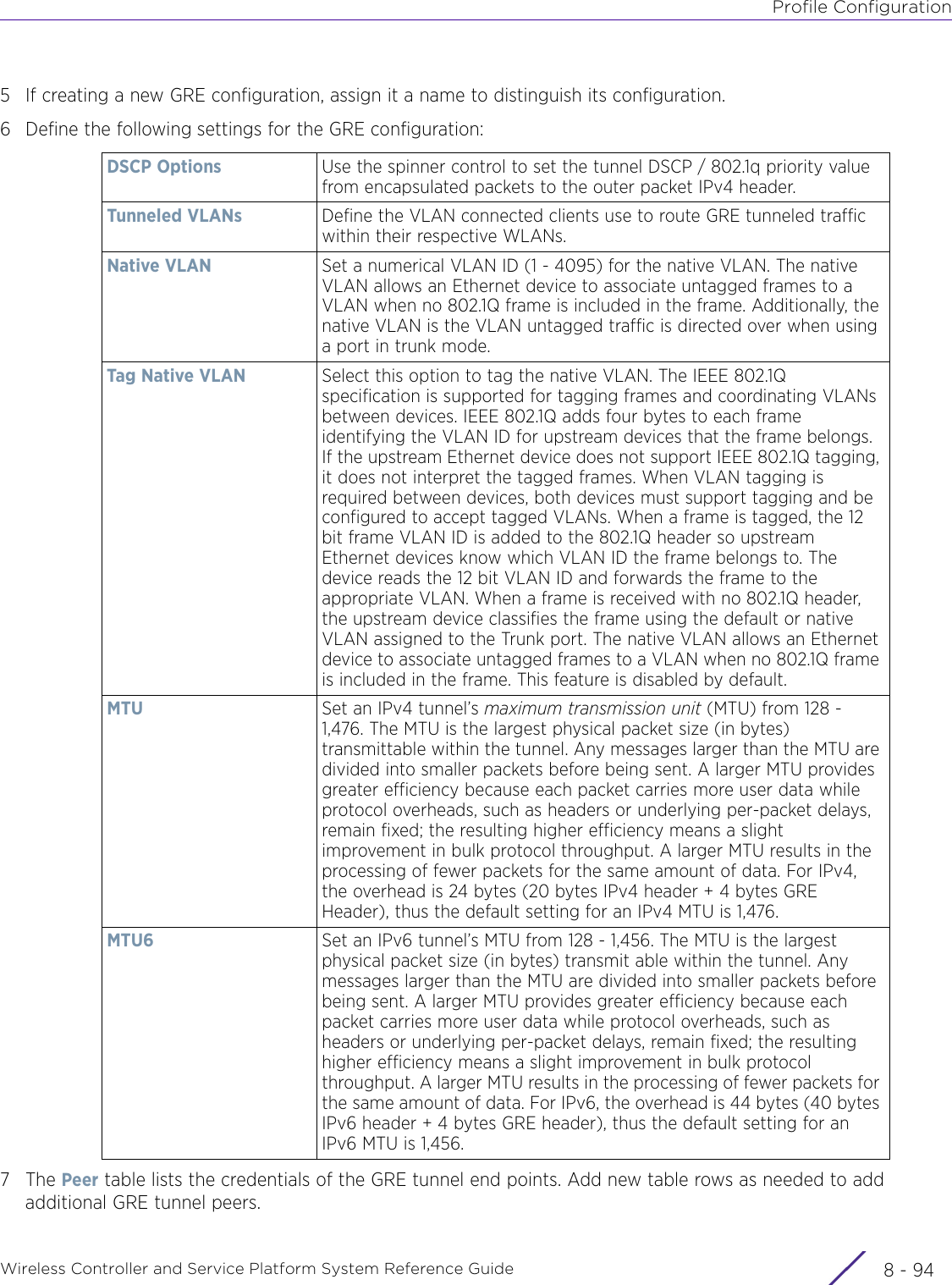
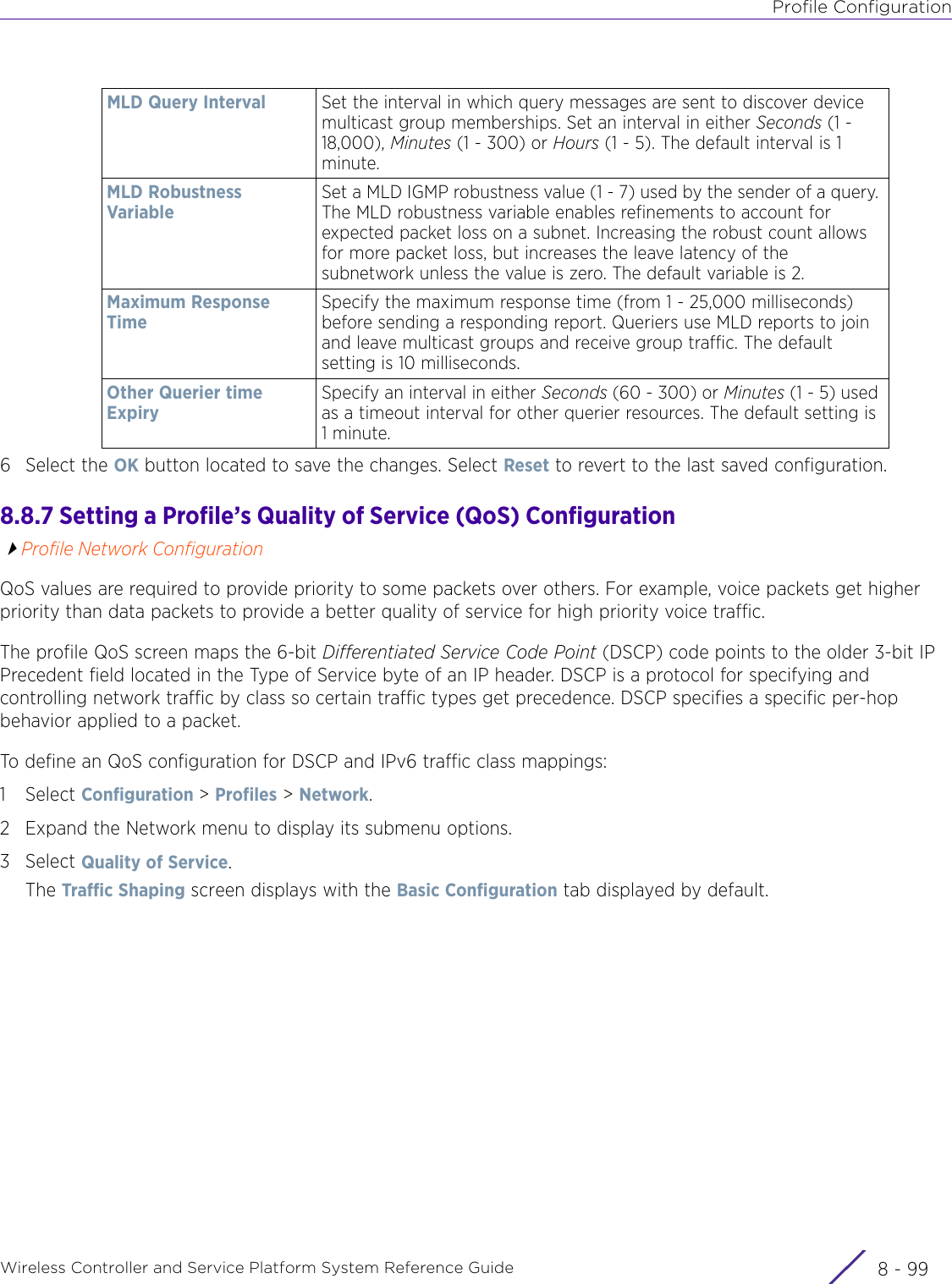
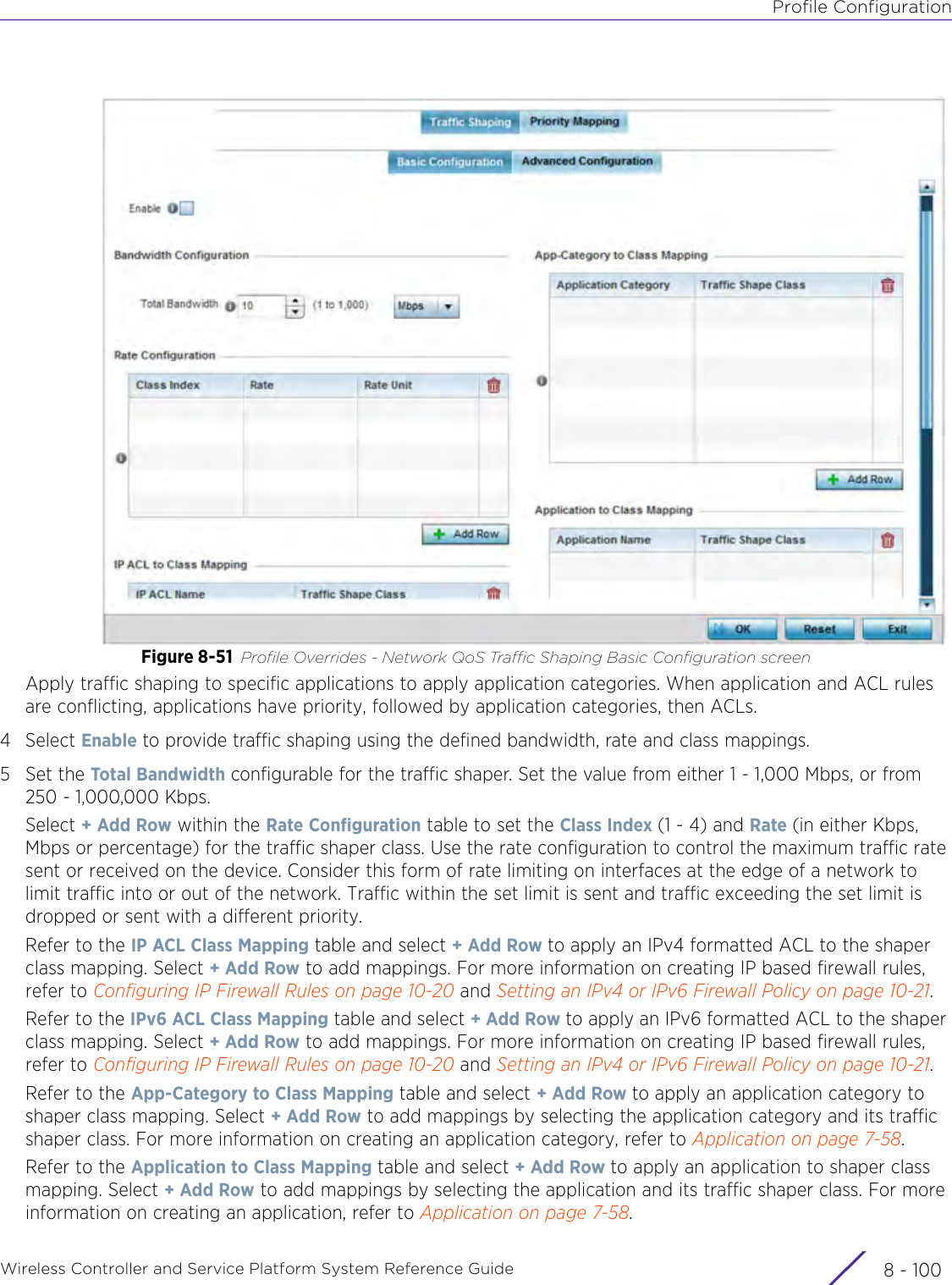
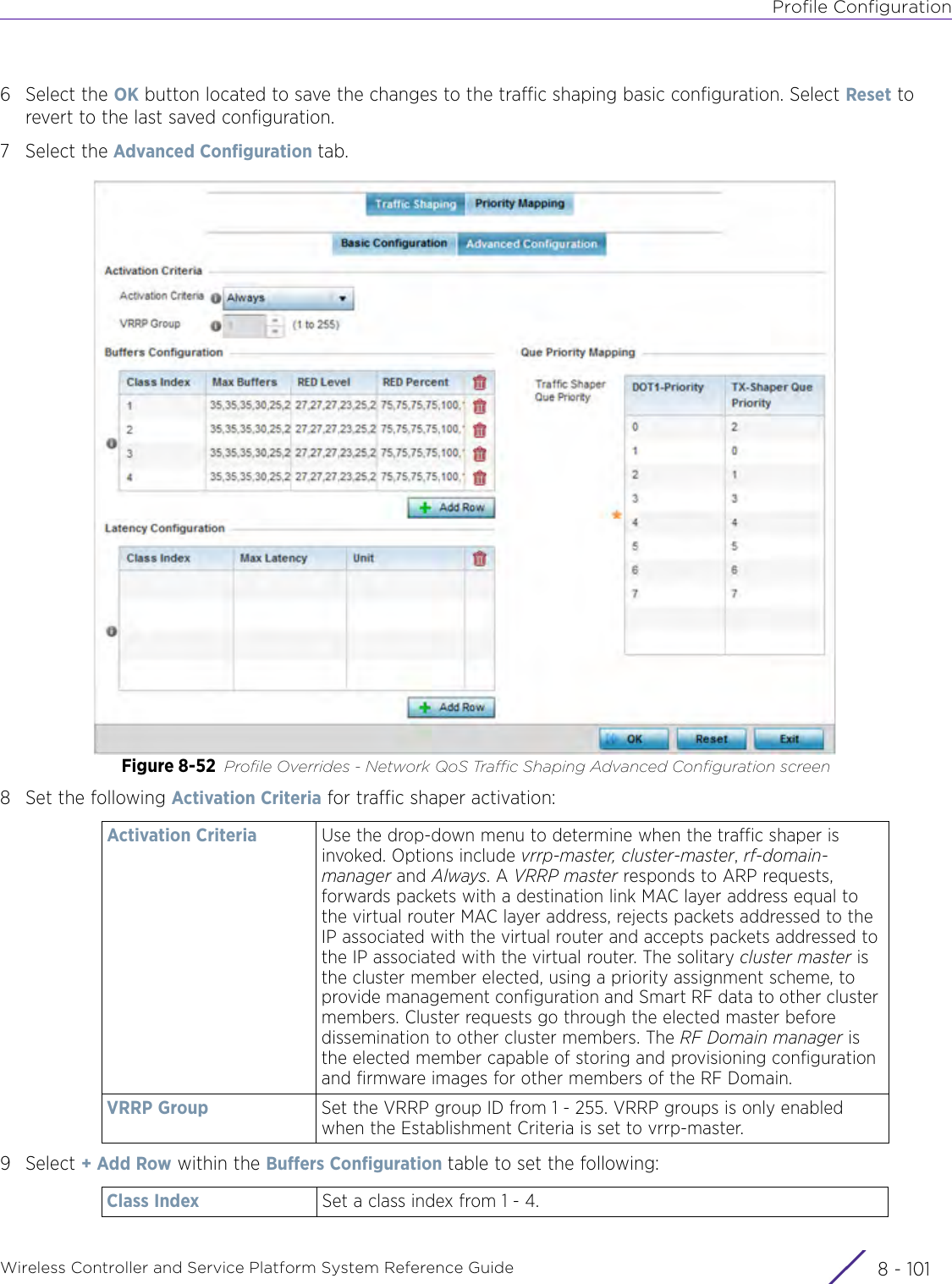
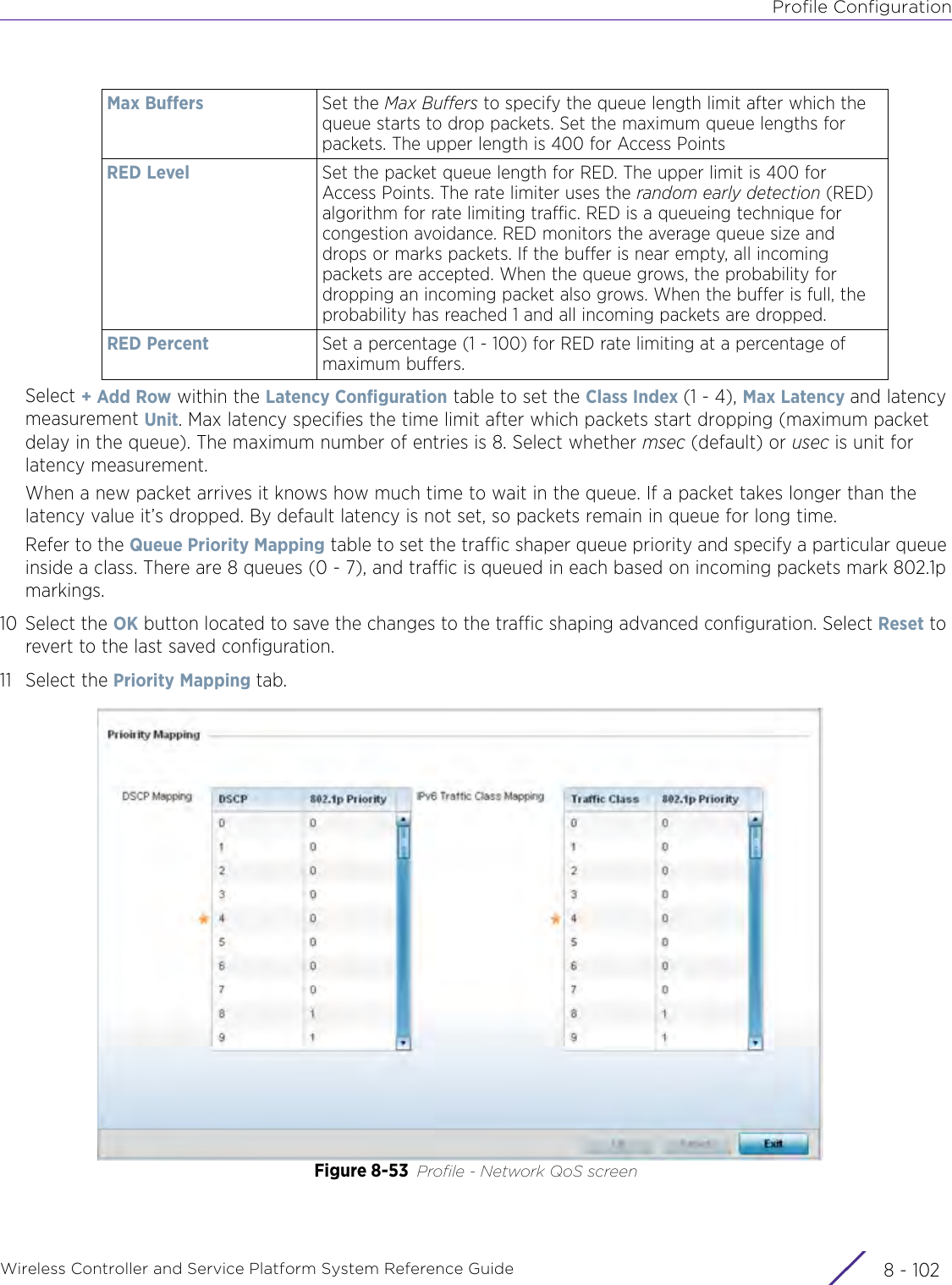
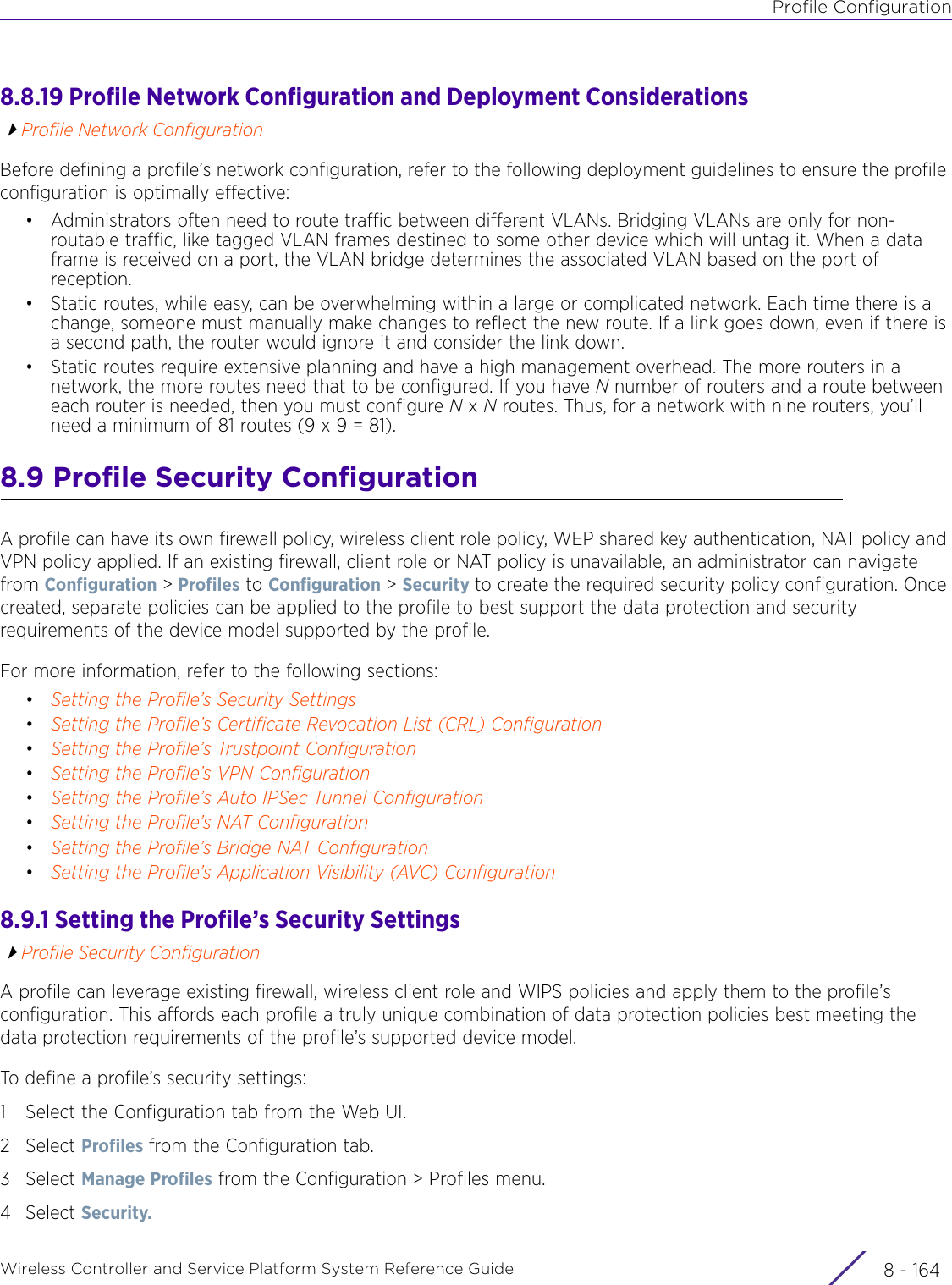
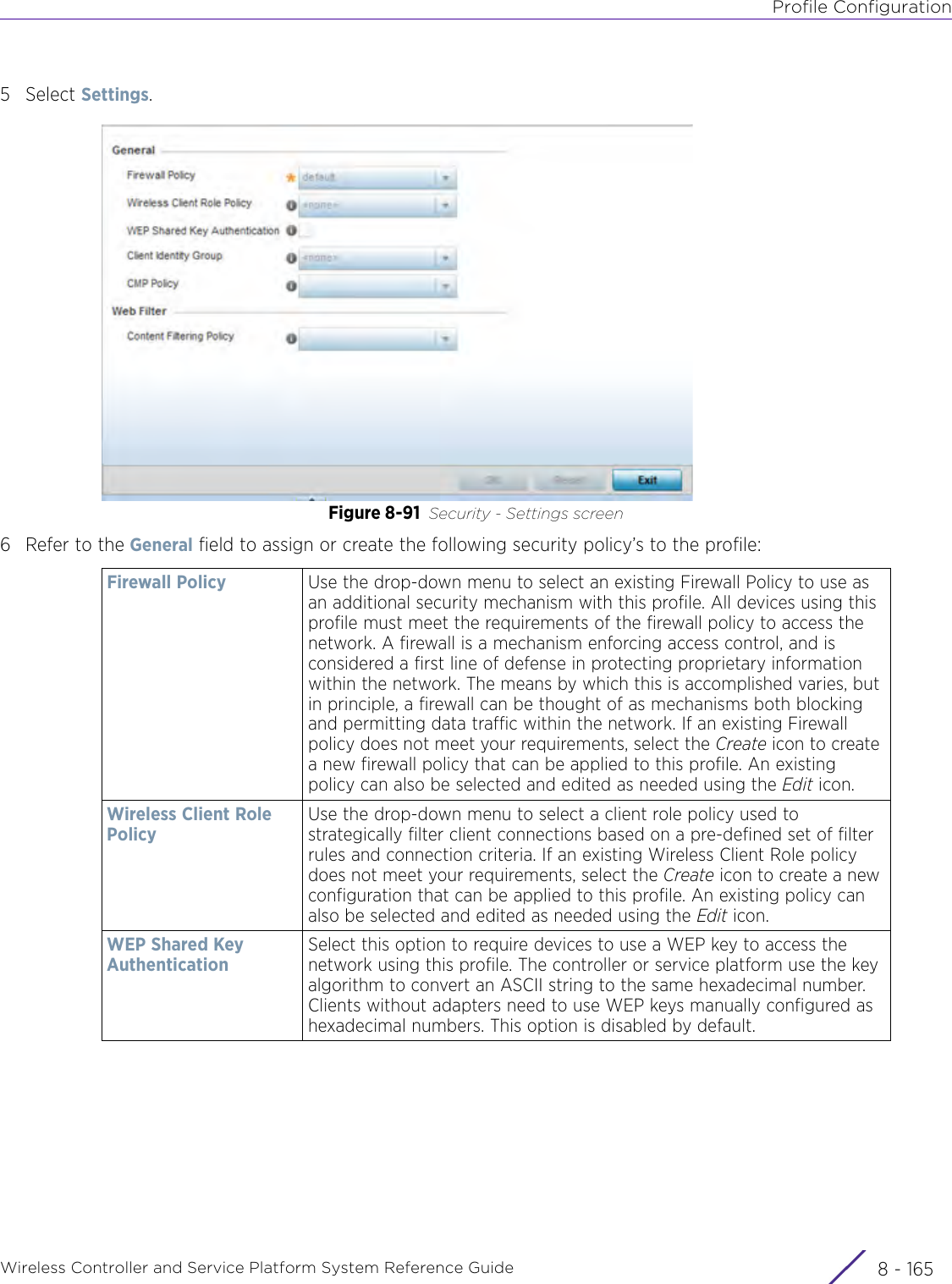
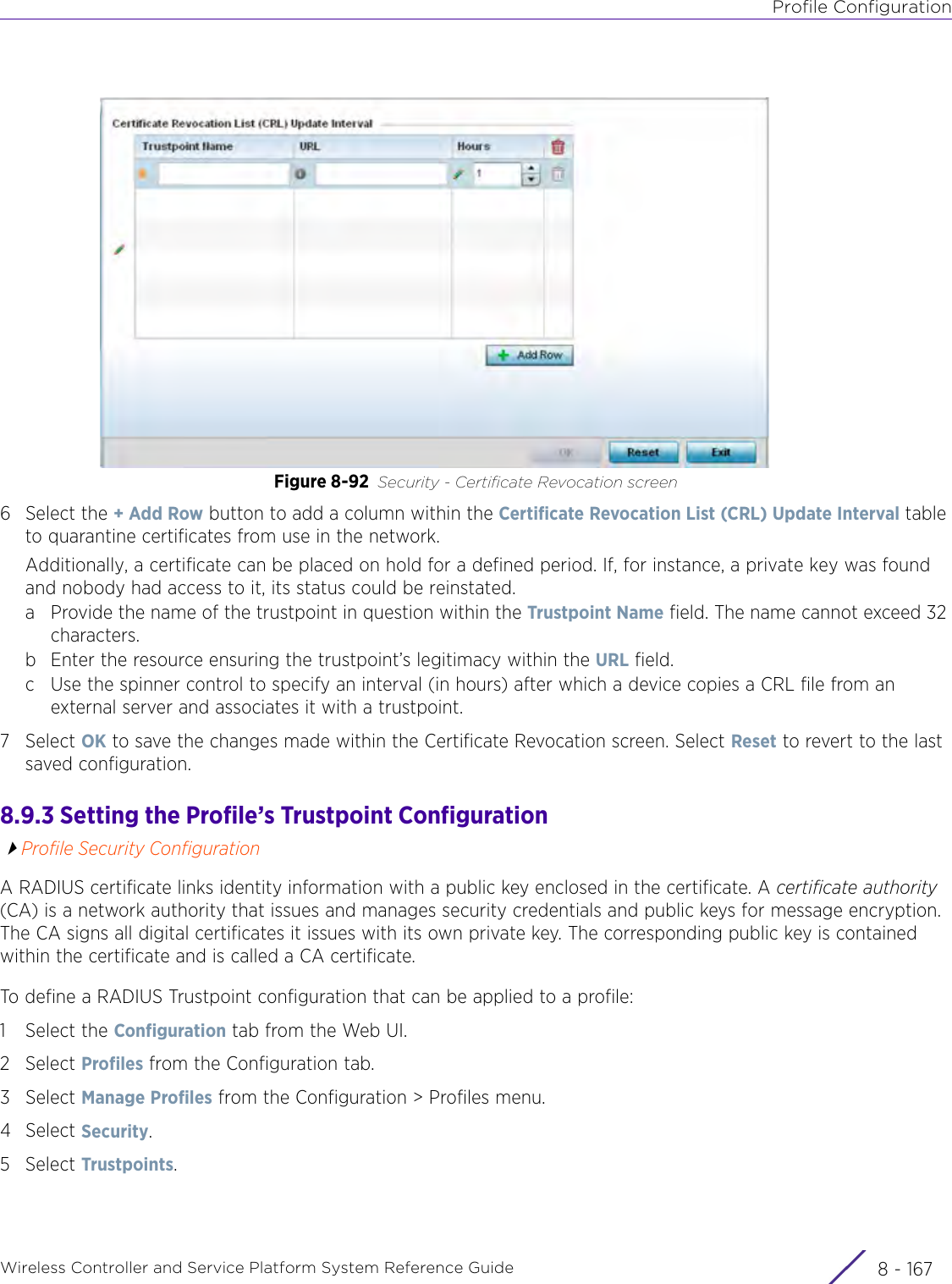
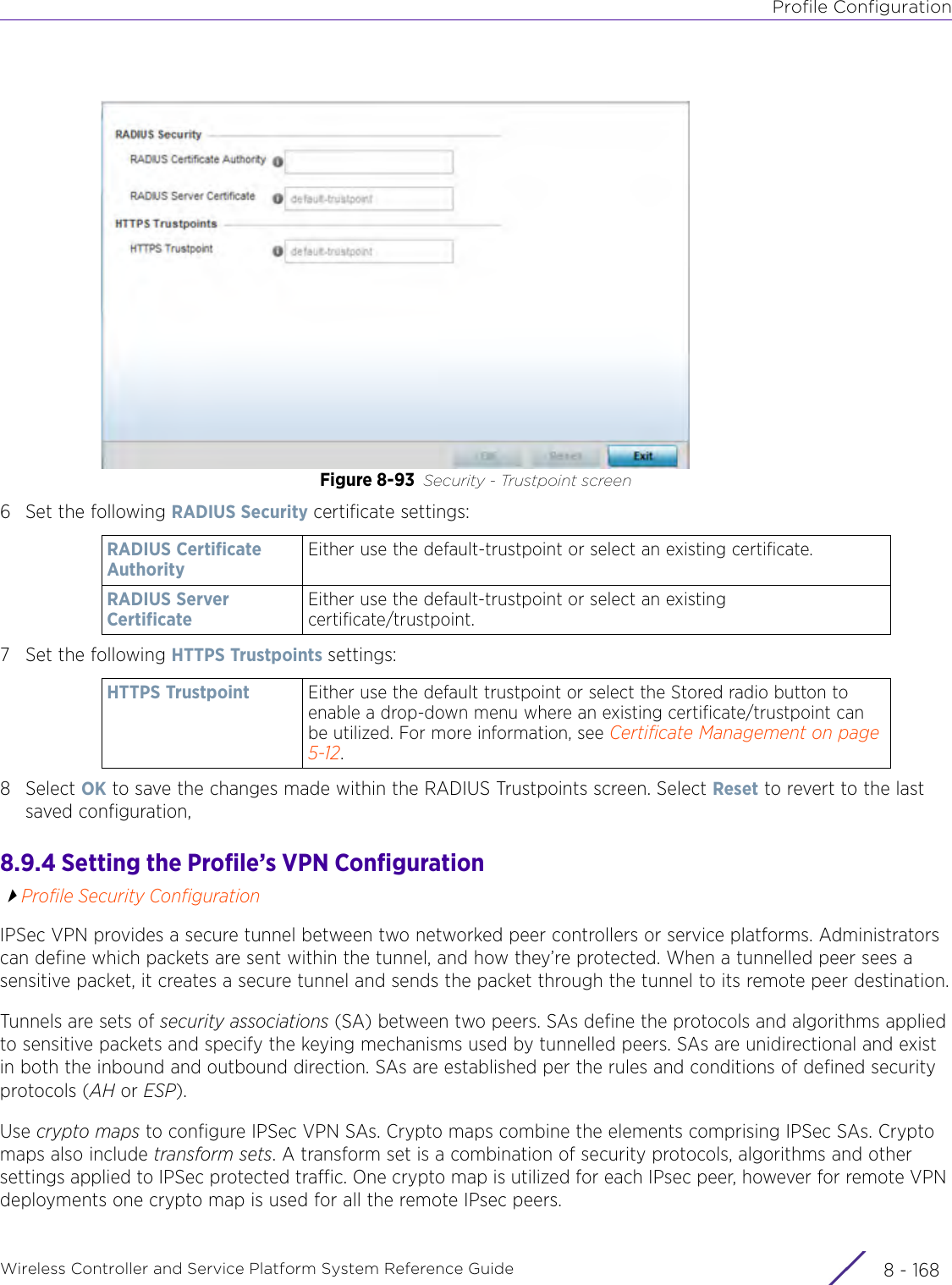
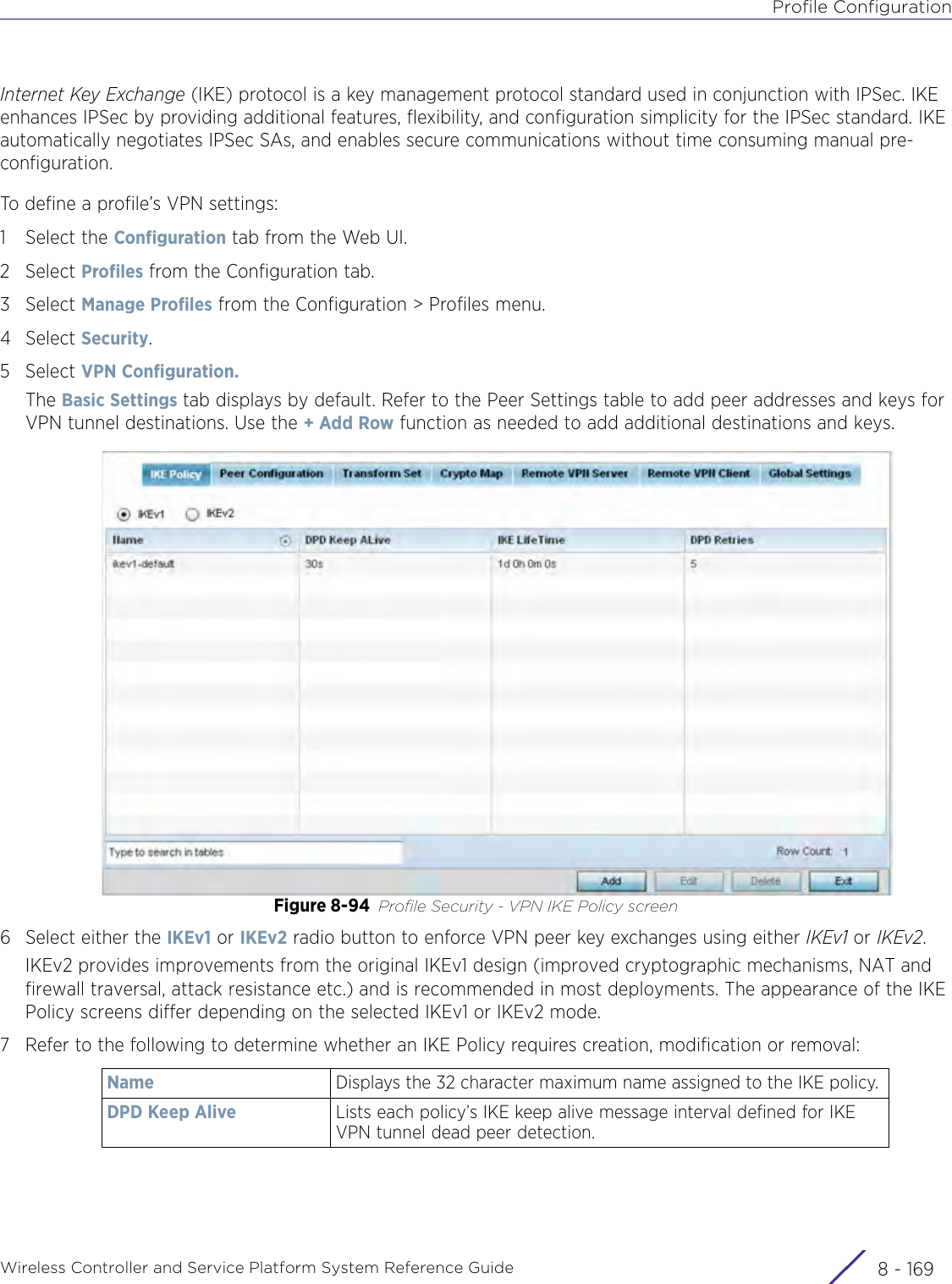
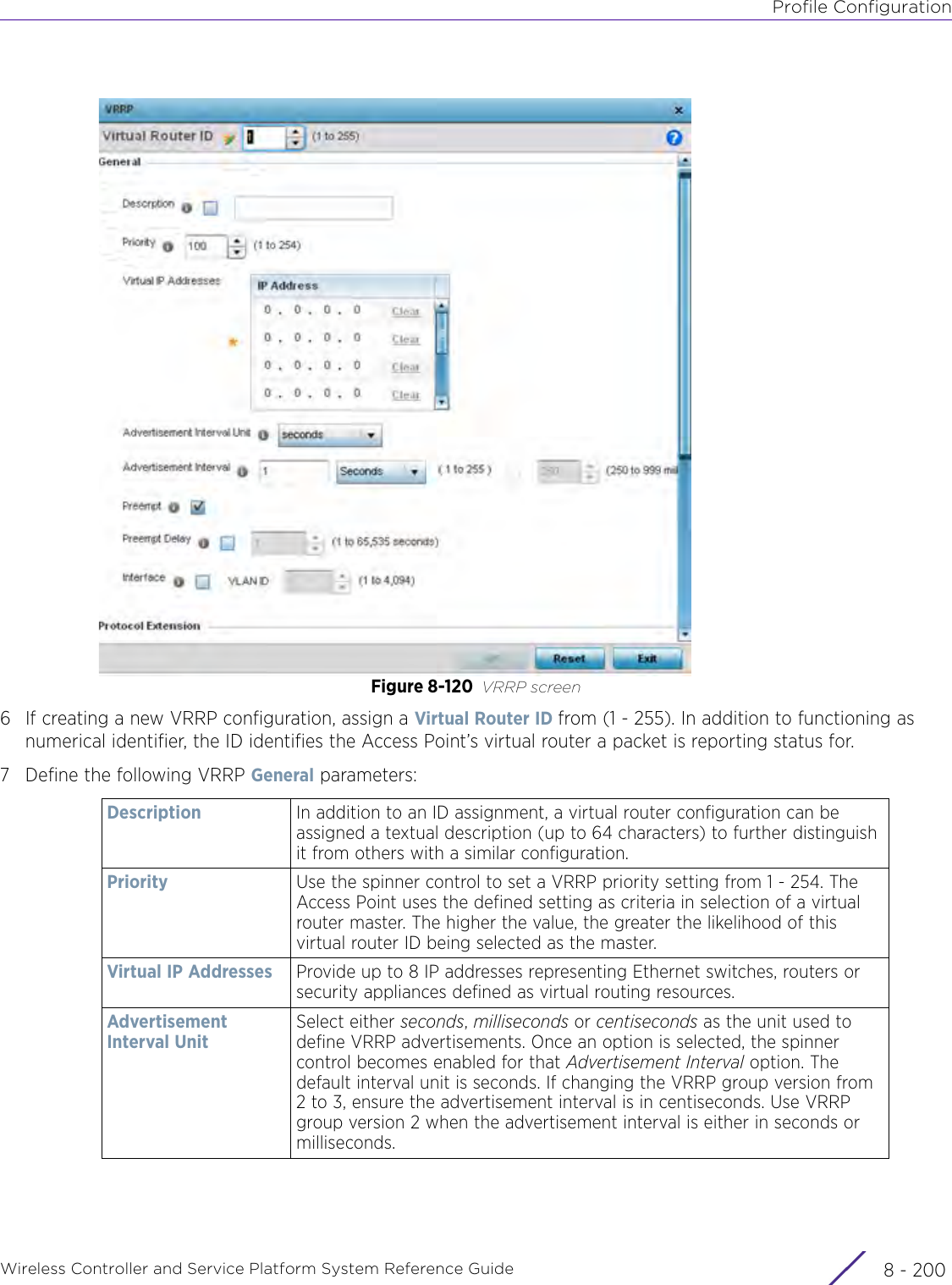
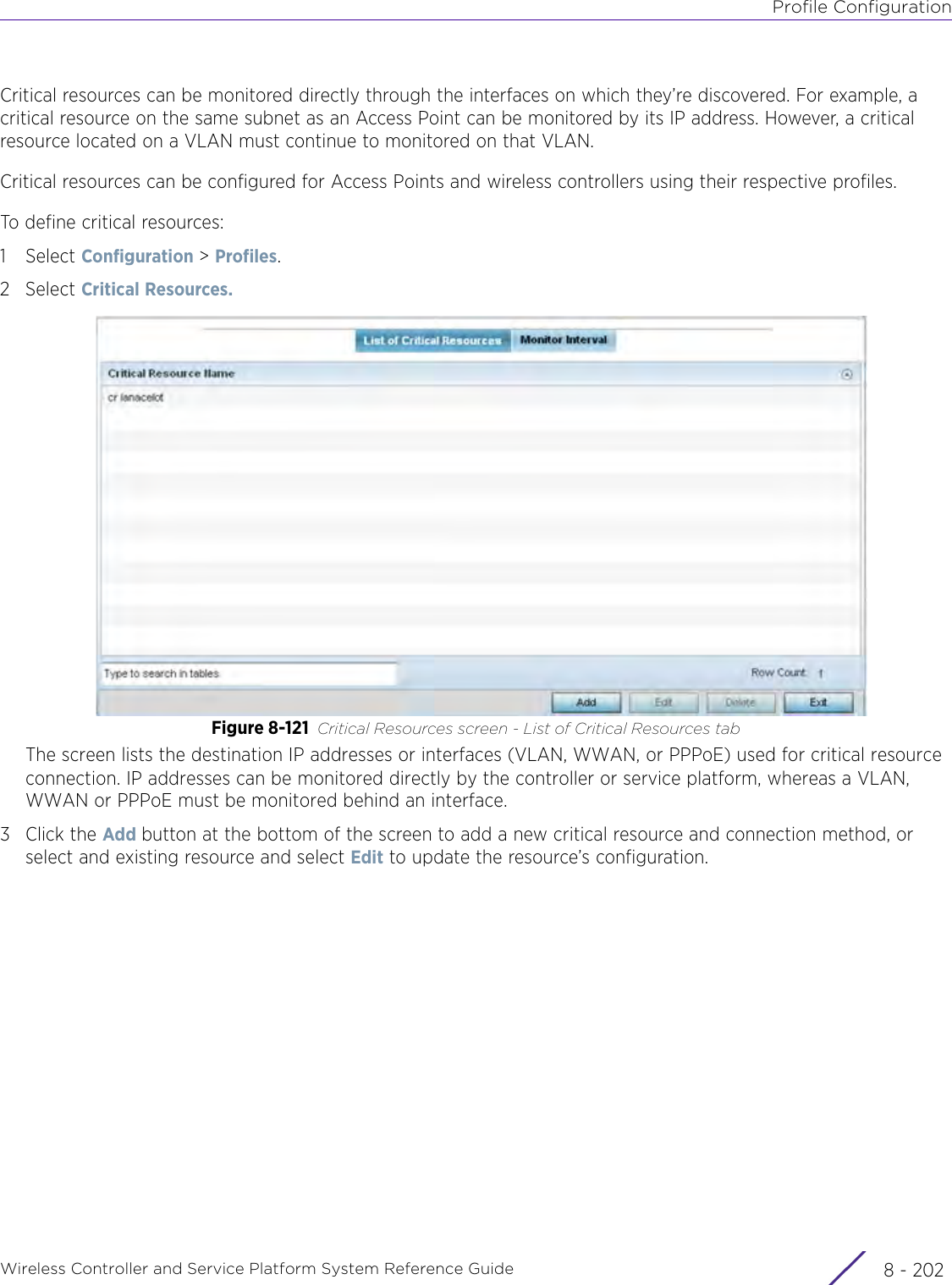
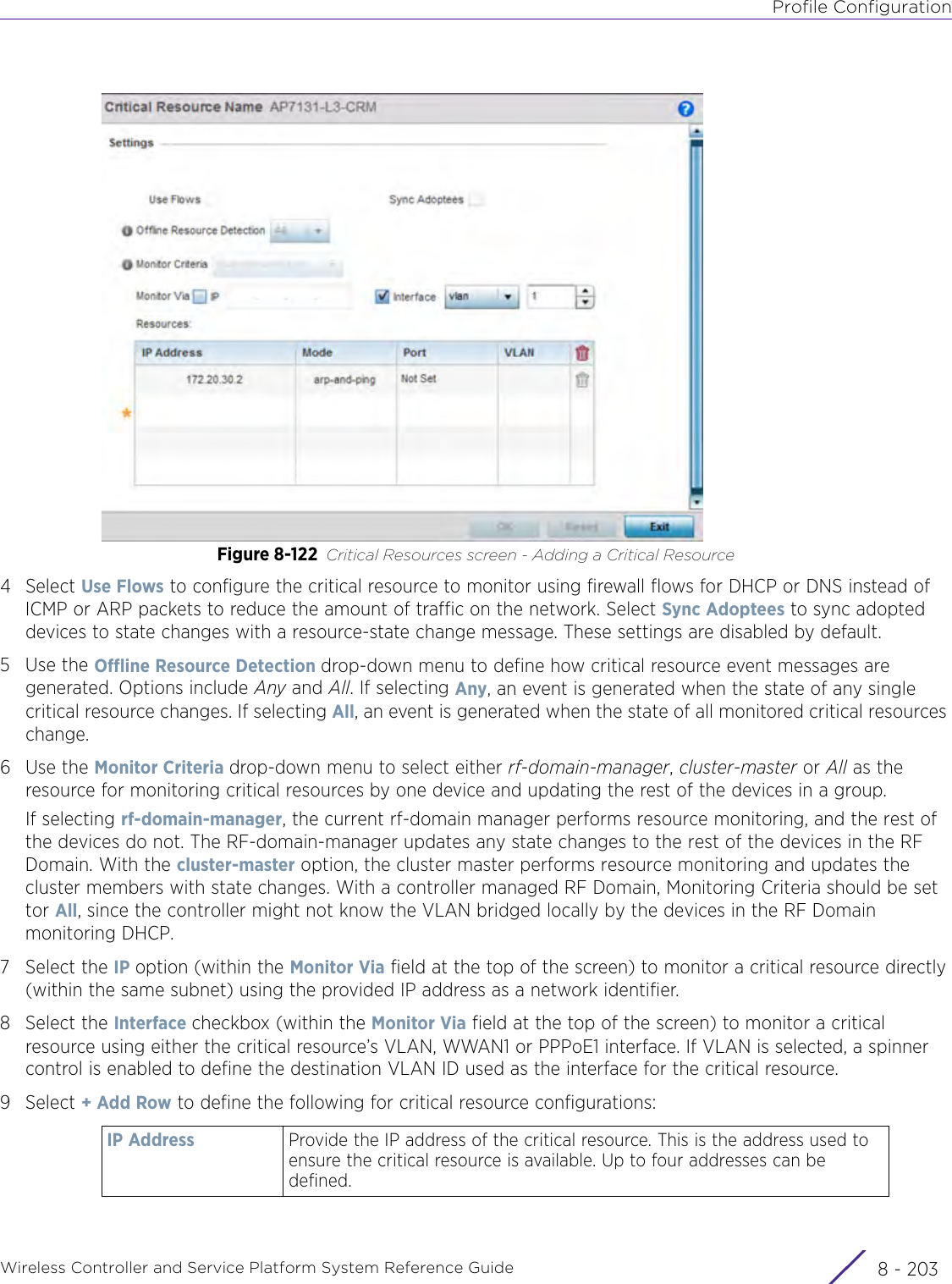
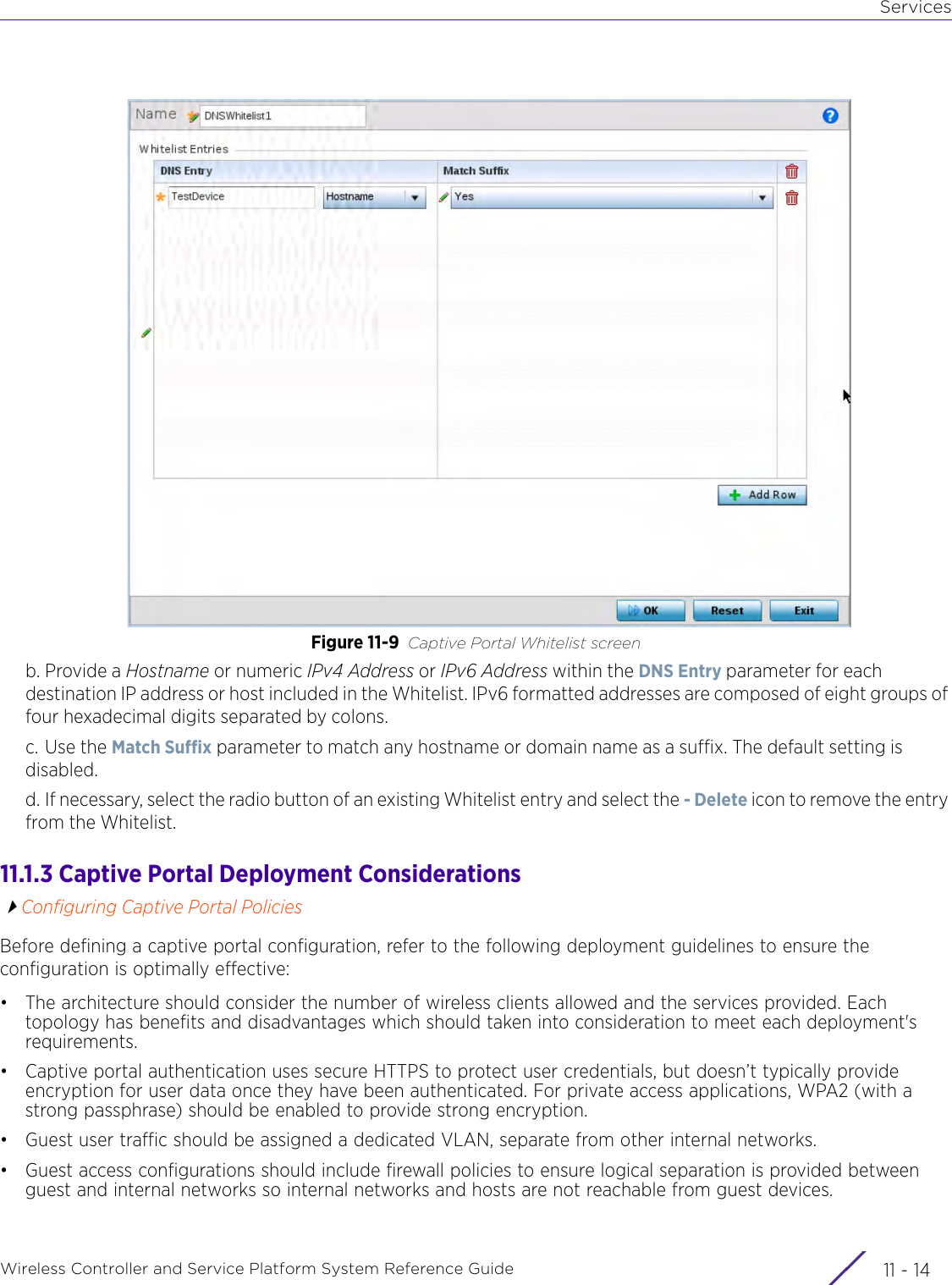
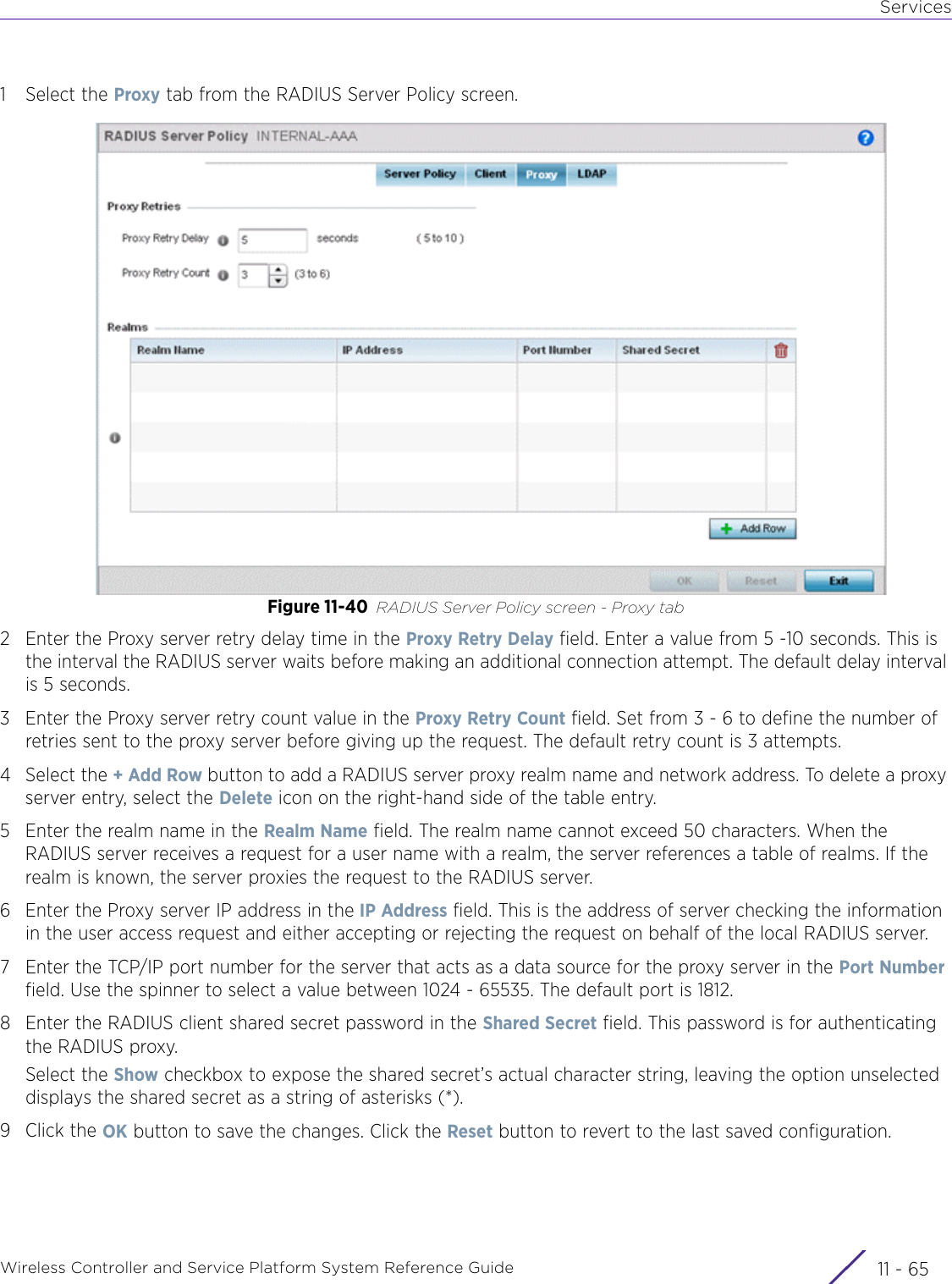
- 4. User Manual-AP7662 R1
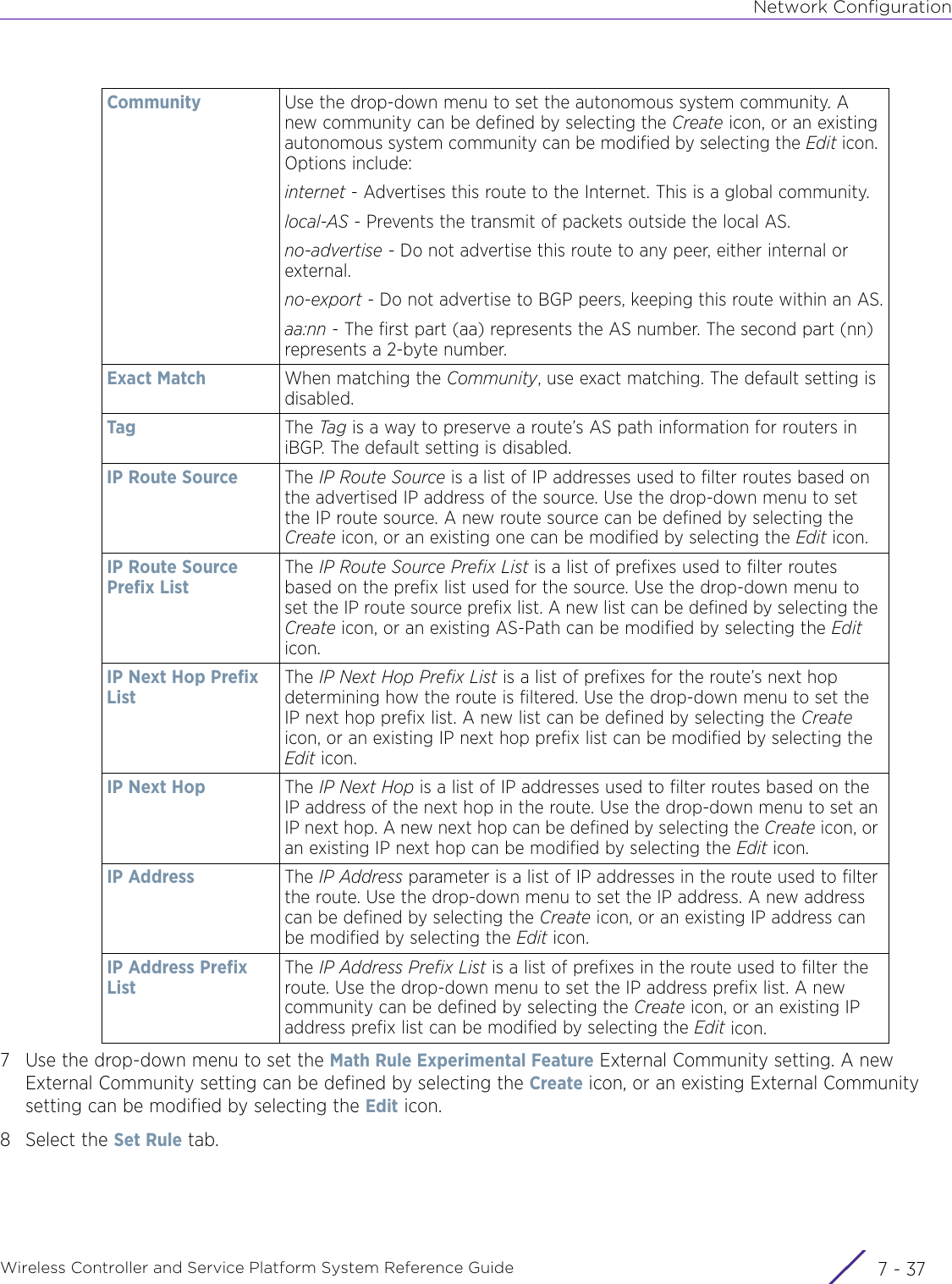
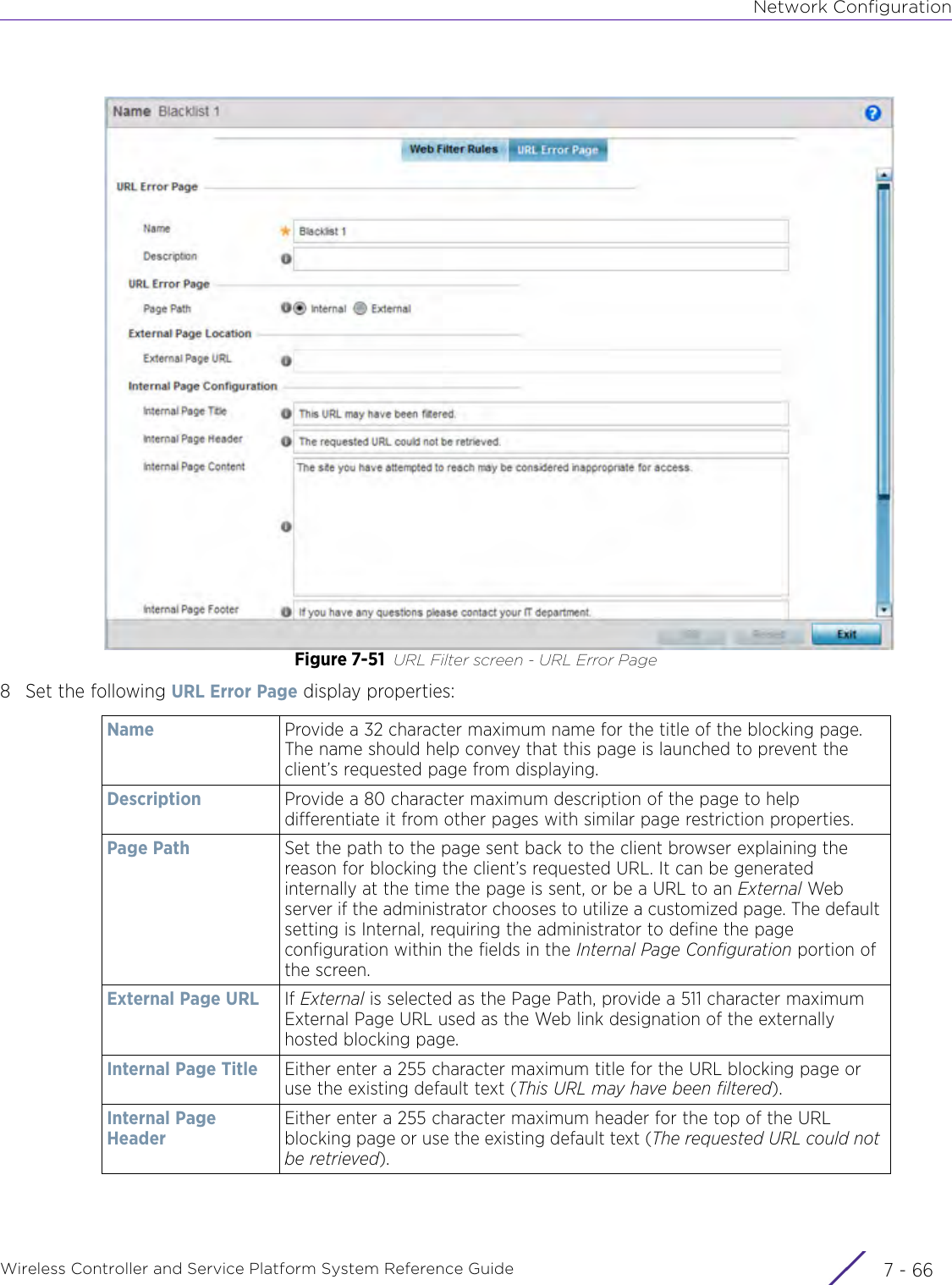
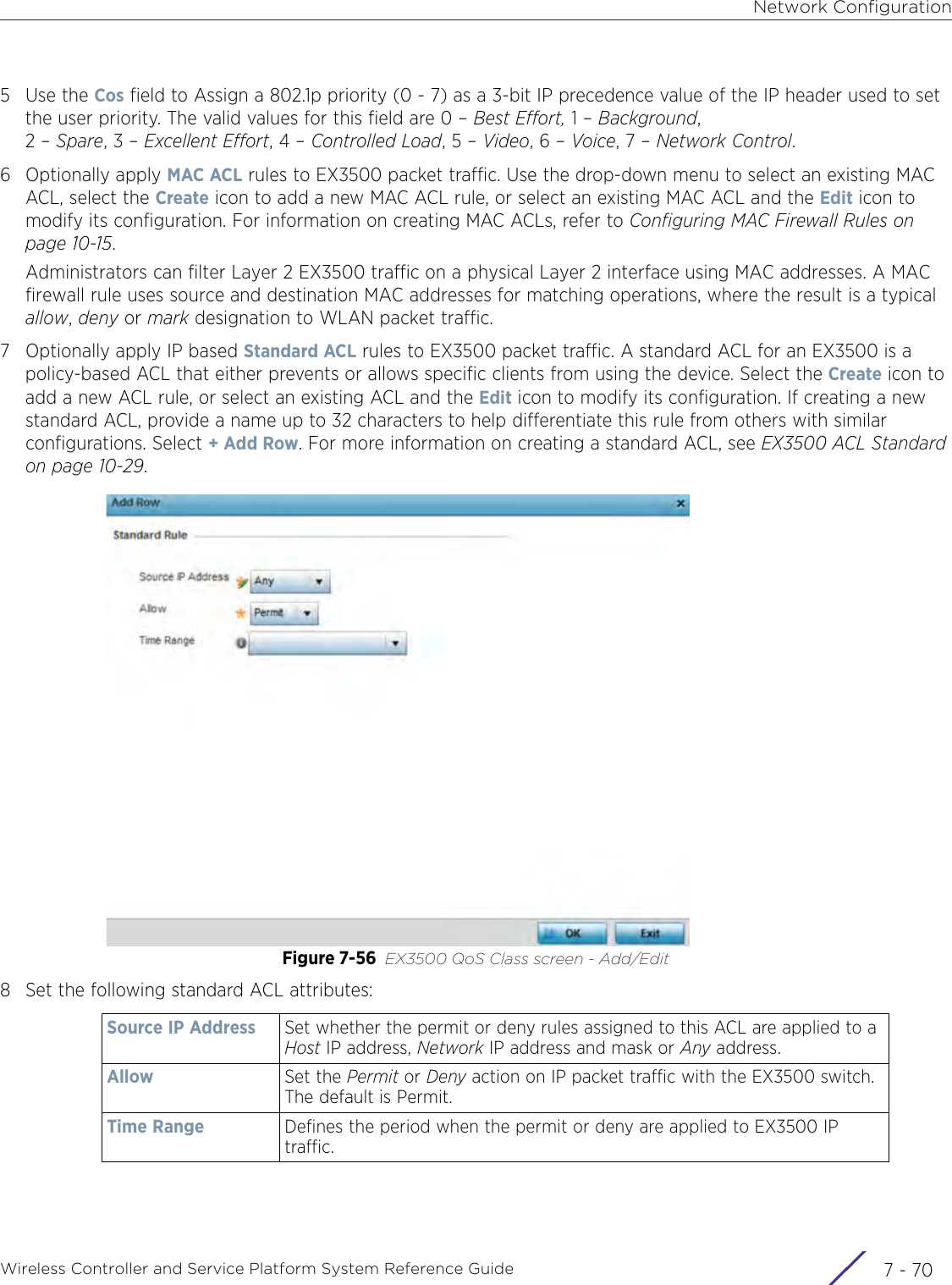
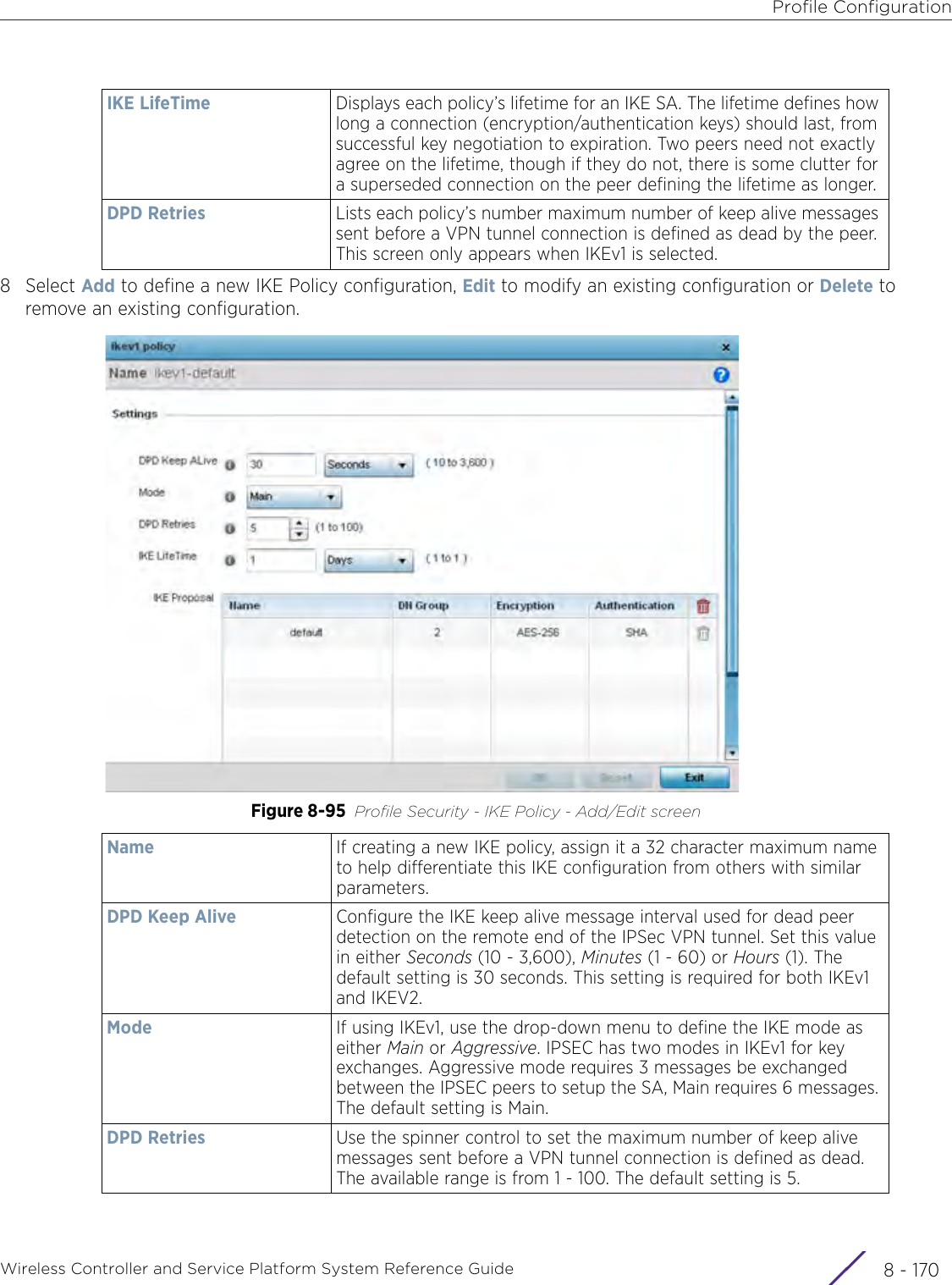
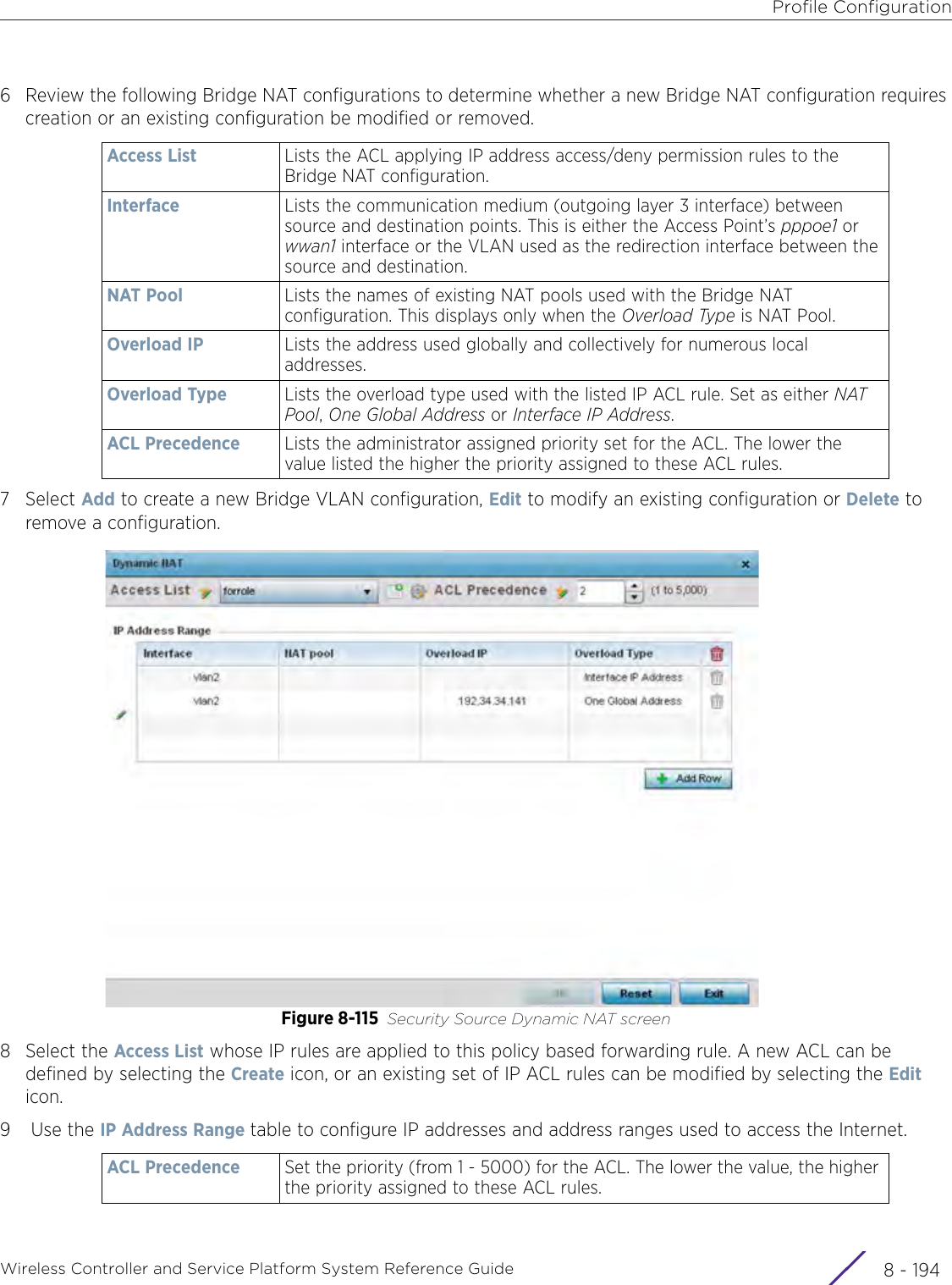
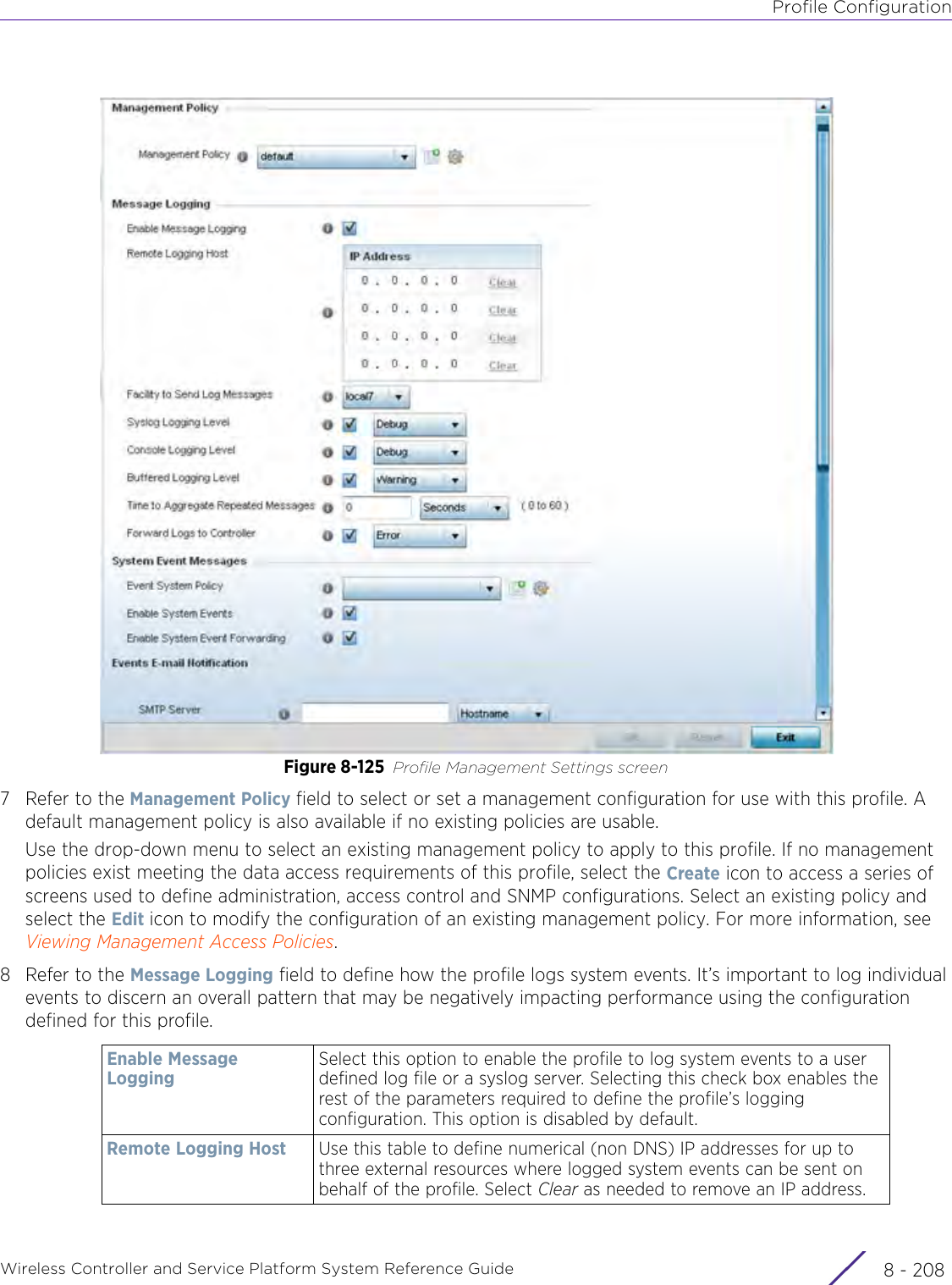
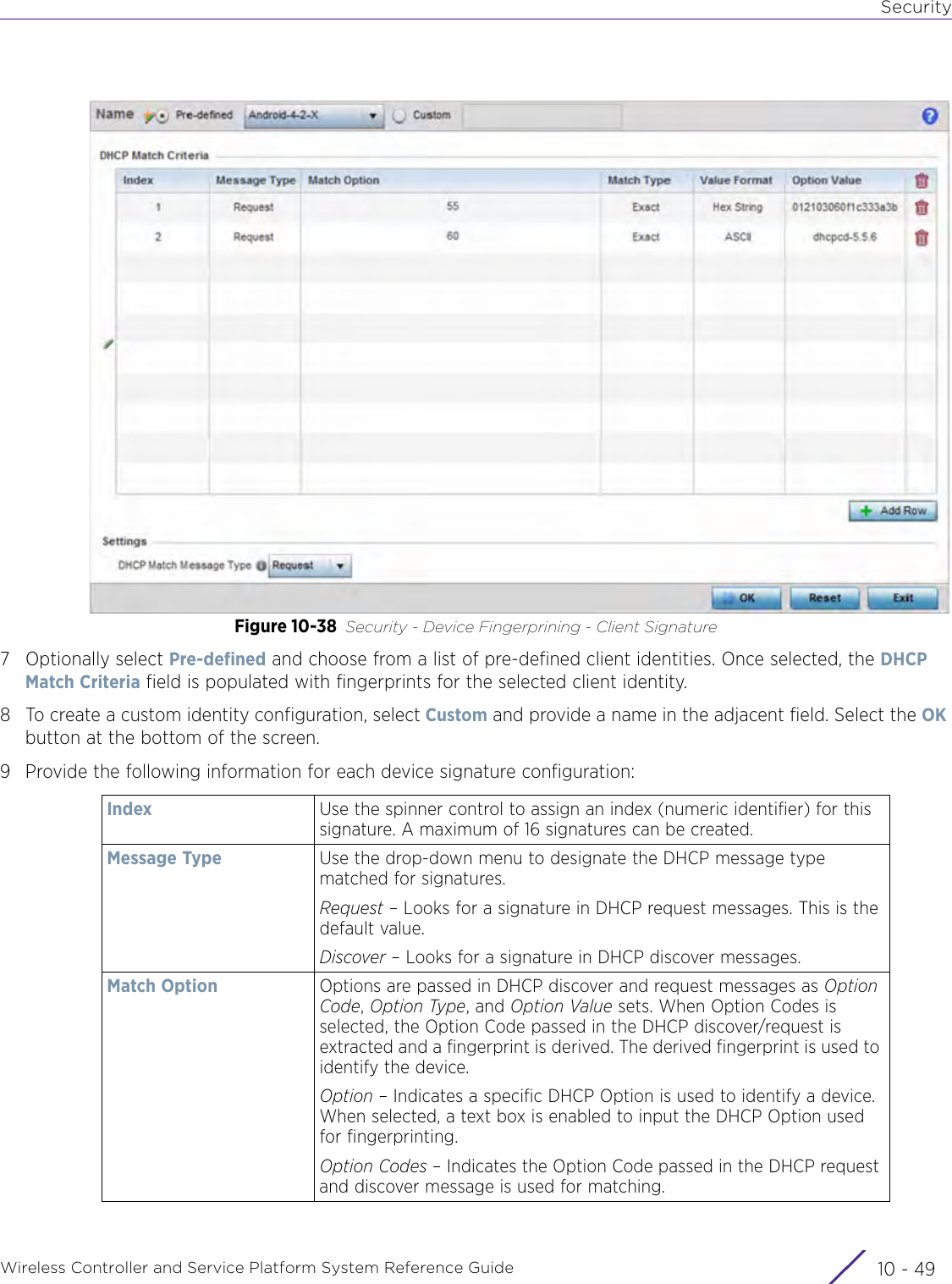
- 5. WiNG 5.9.1 System Reference Guide Part 1
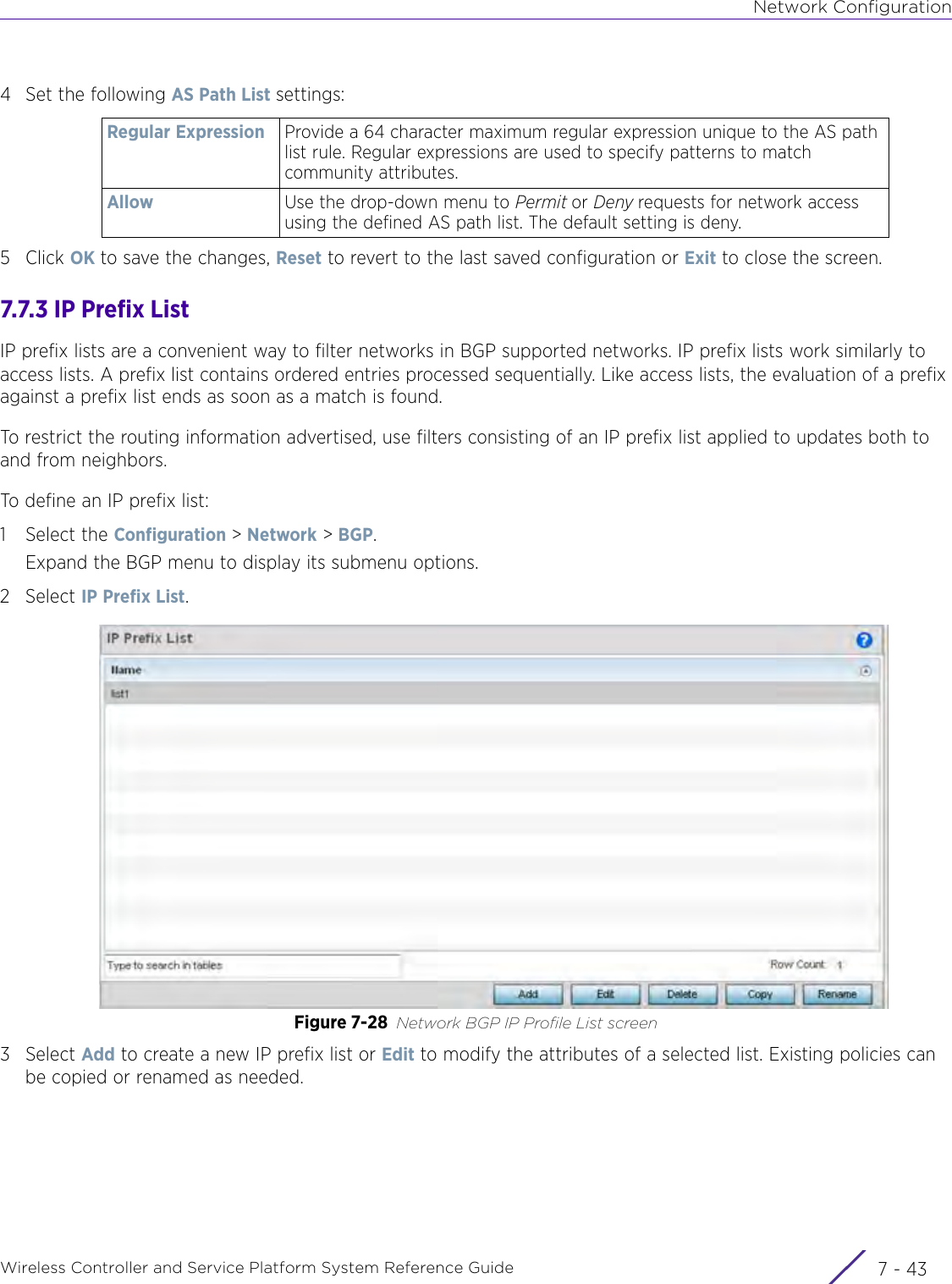
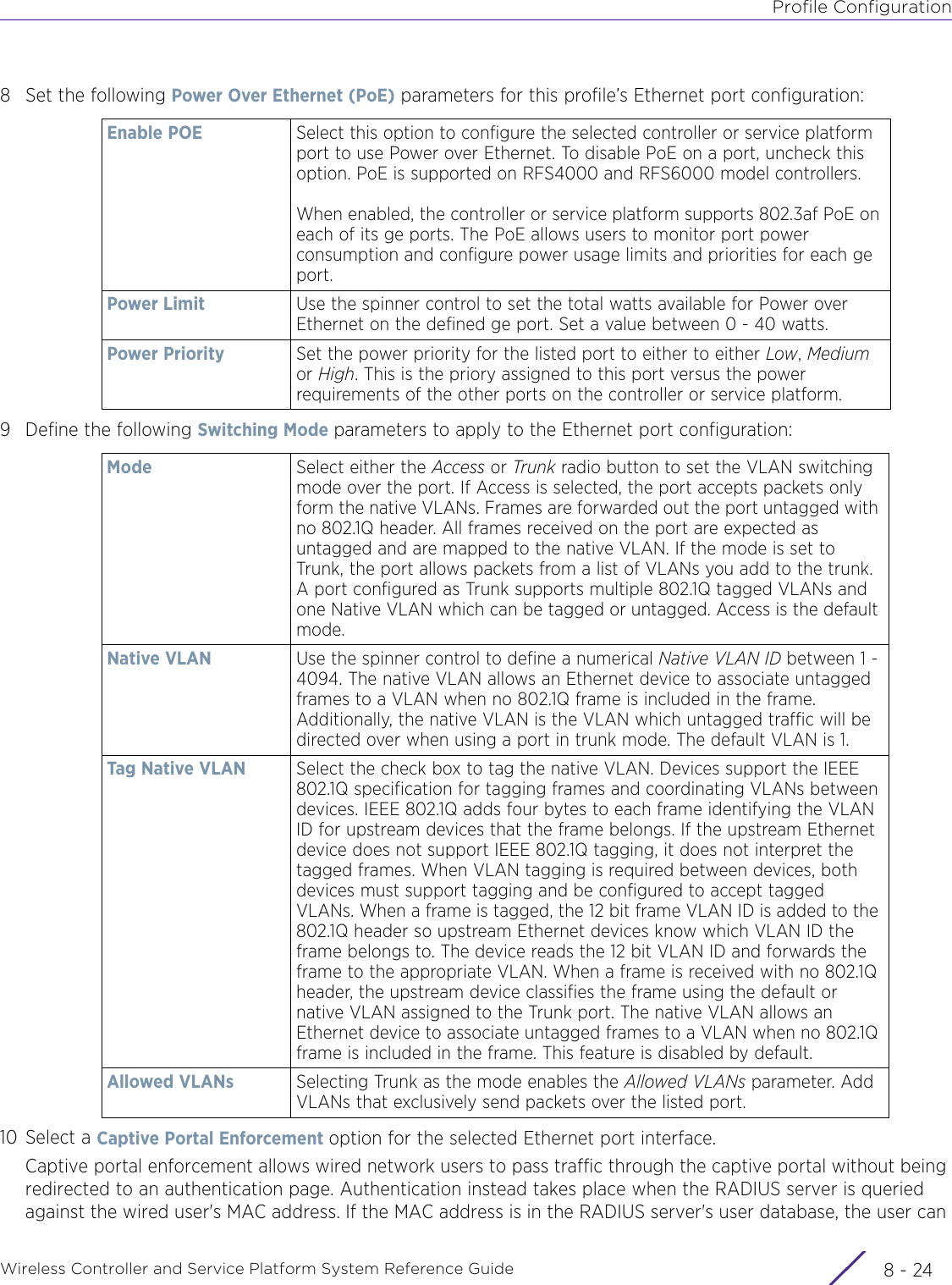
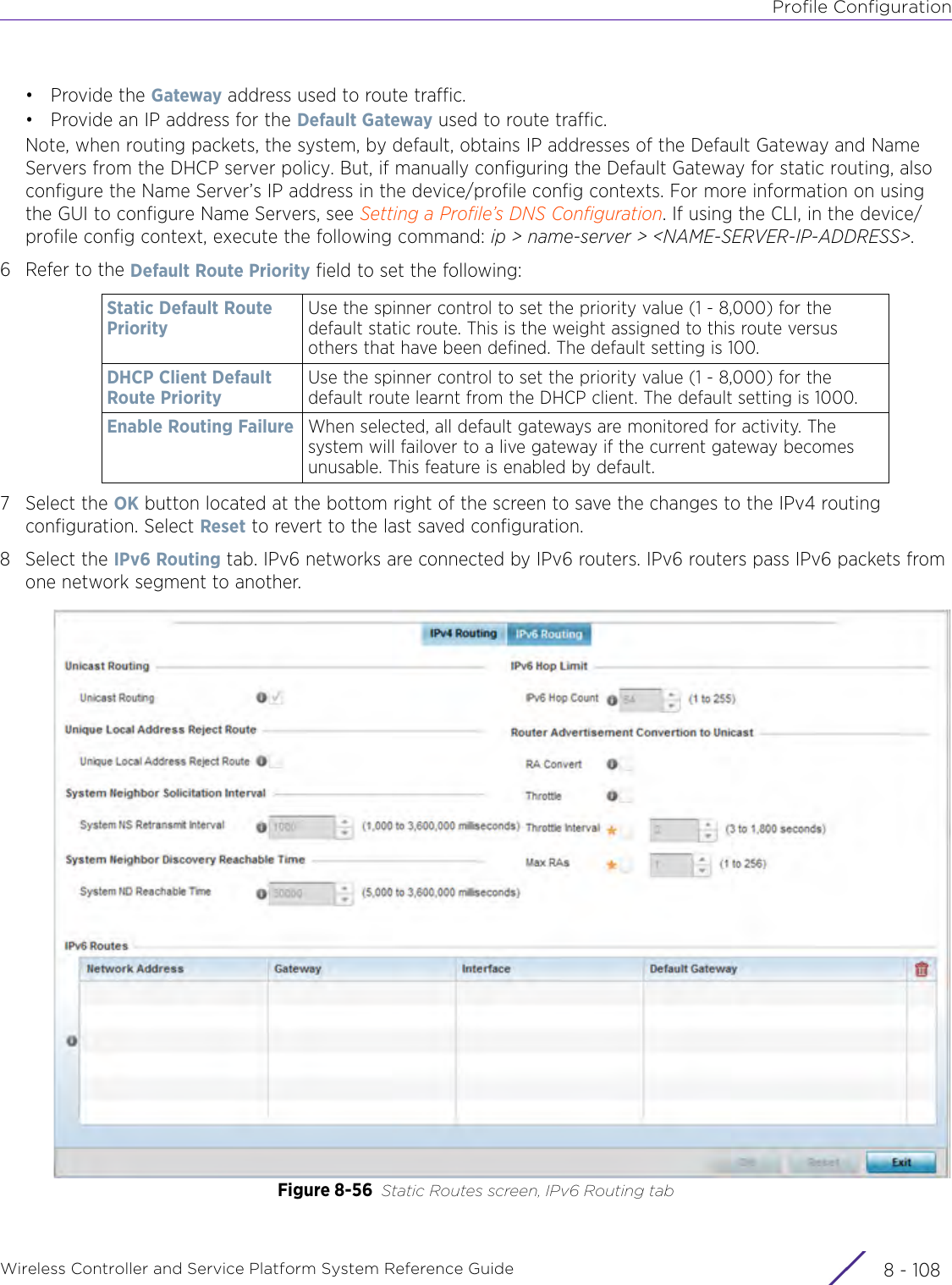
- 6. WiNG 5.9.1 System Reference Guide Part 2
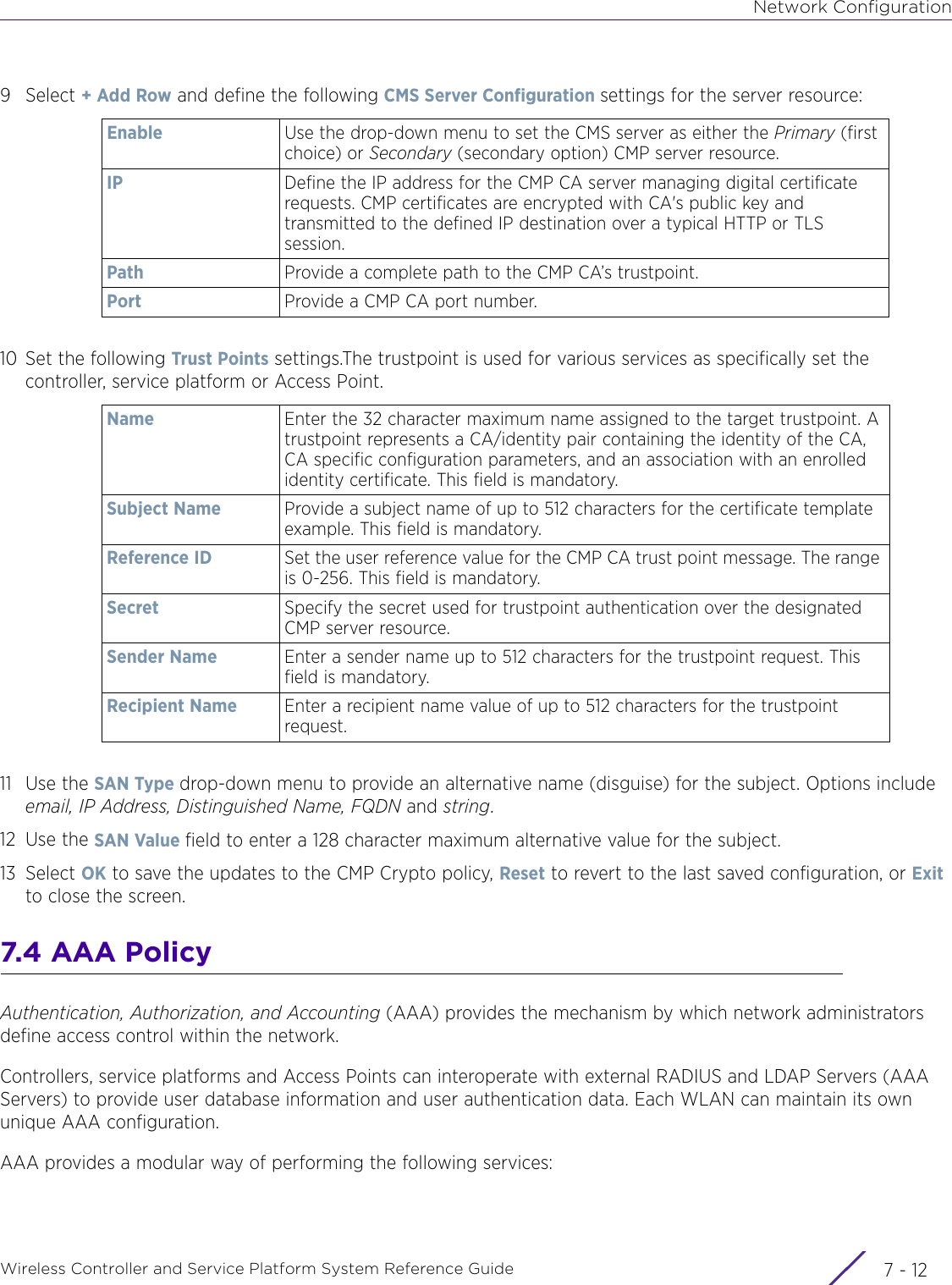
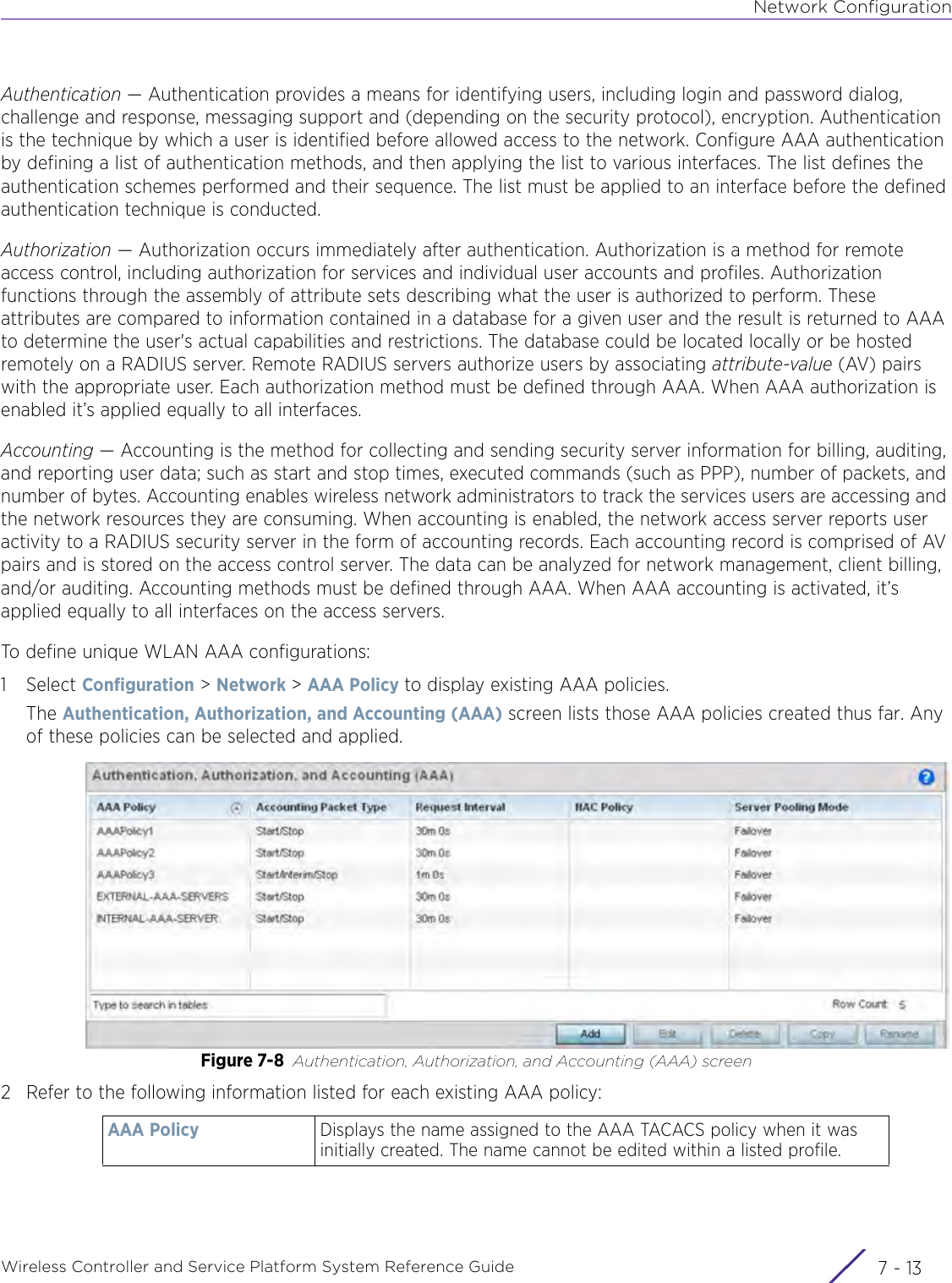
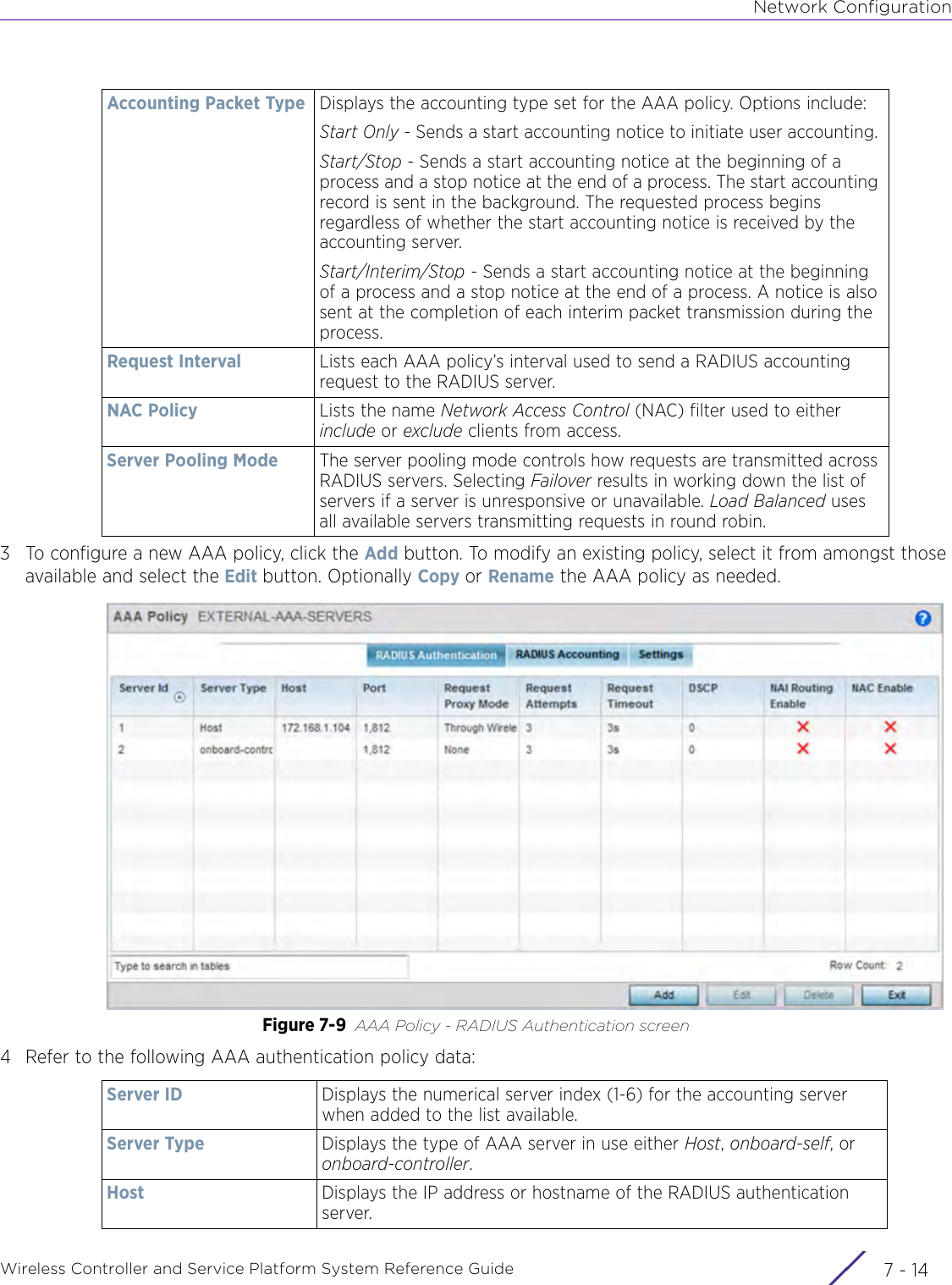
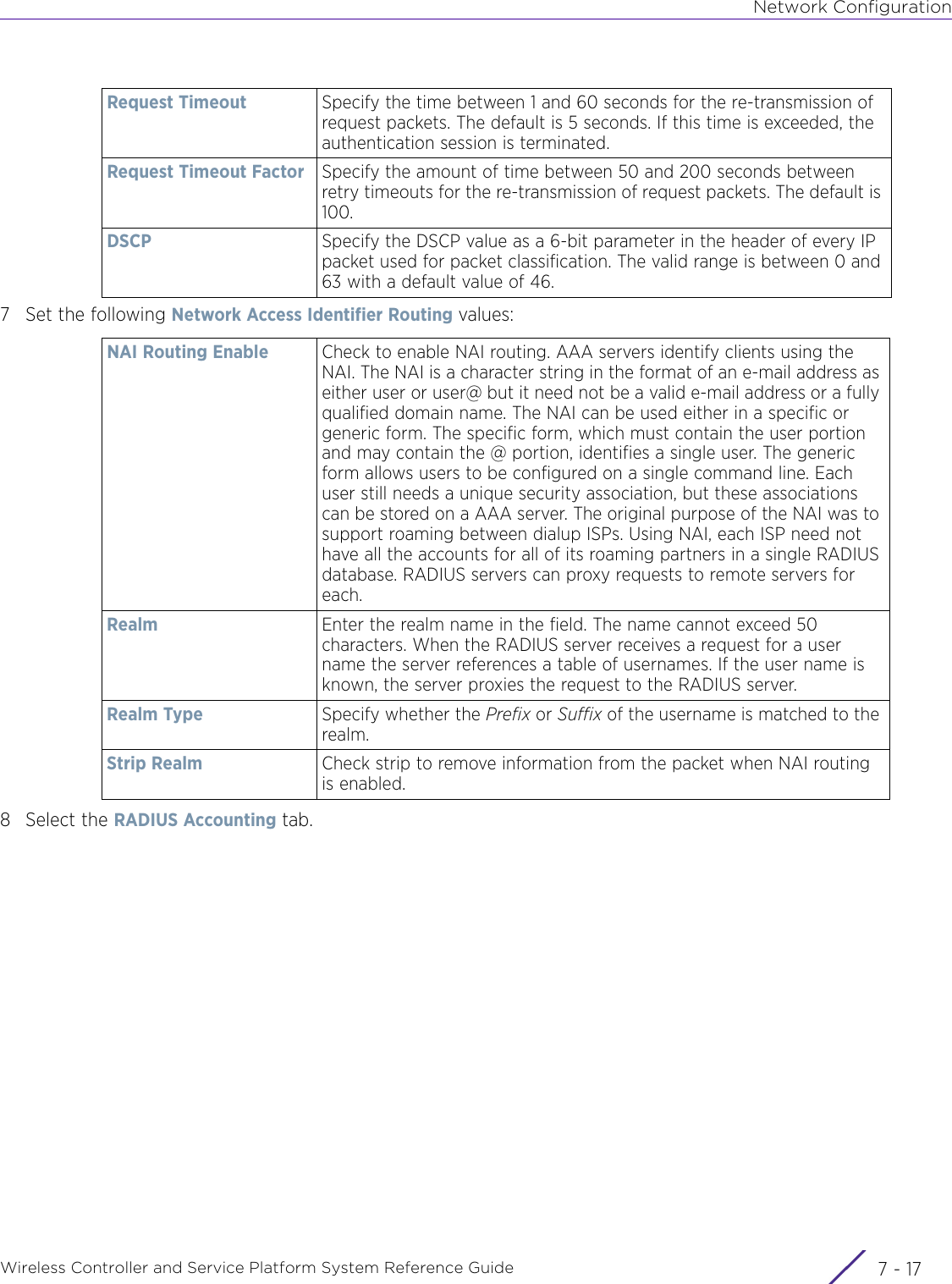
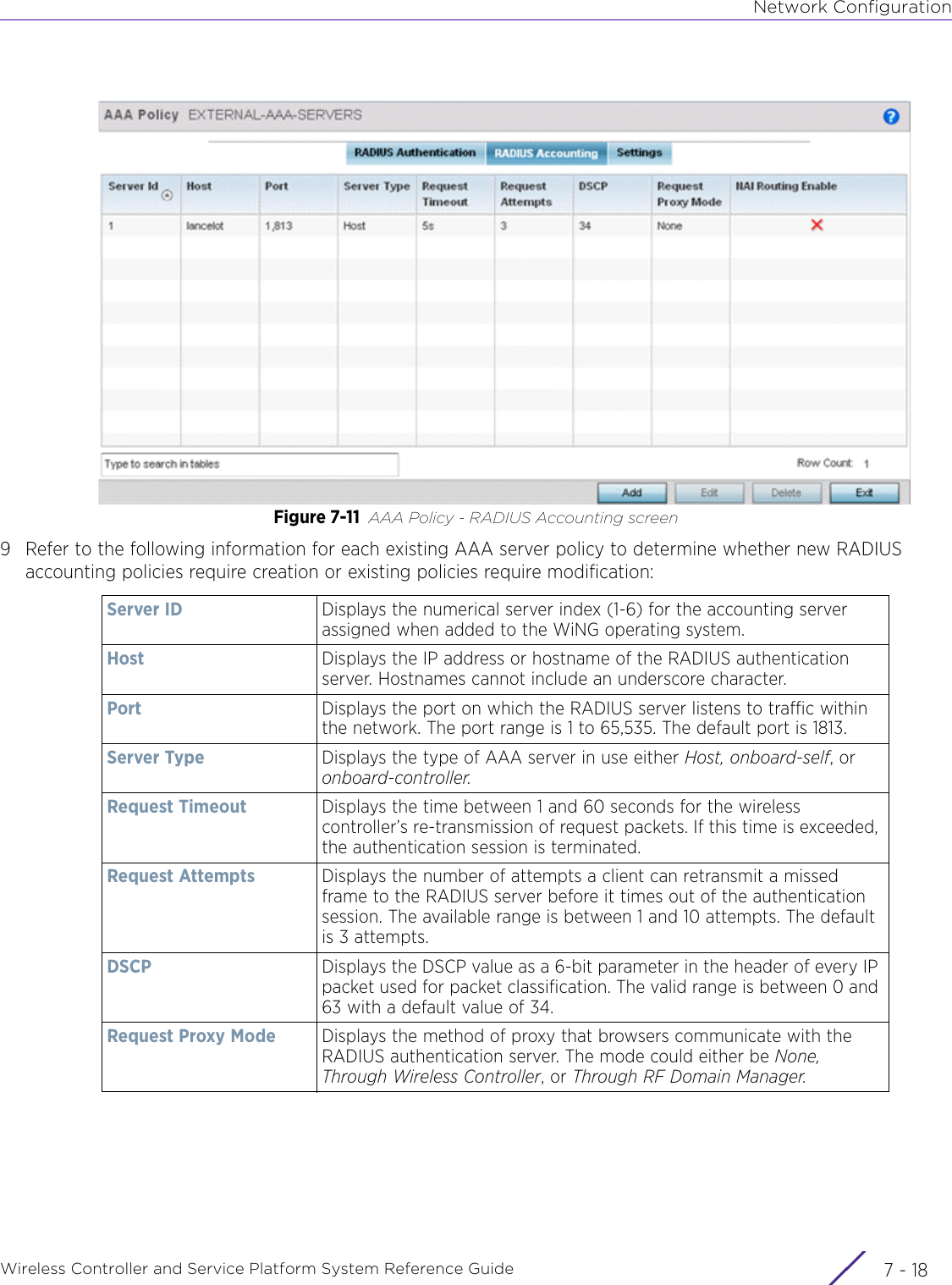
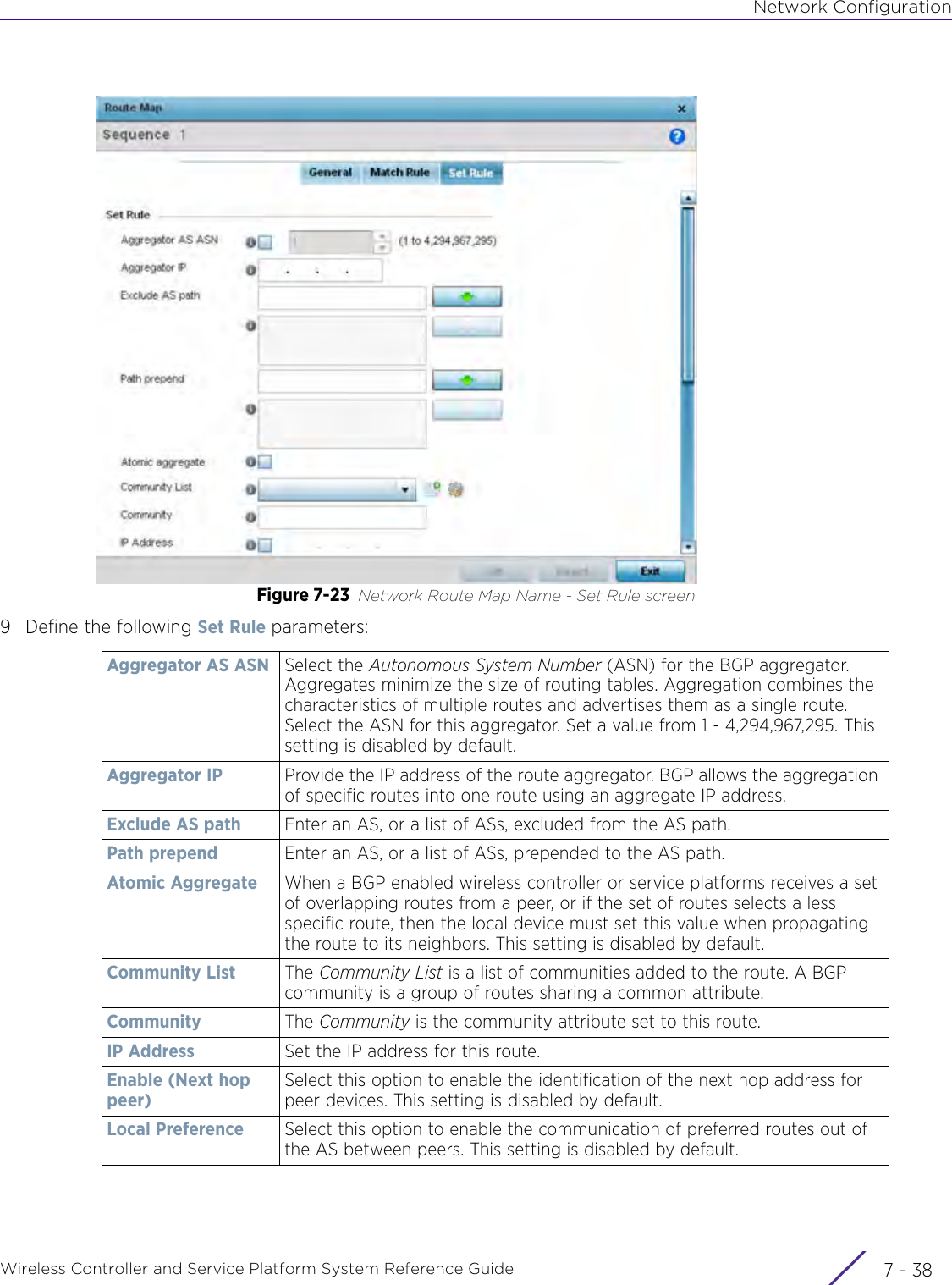
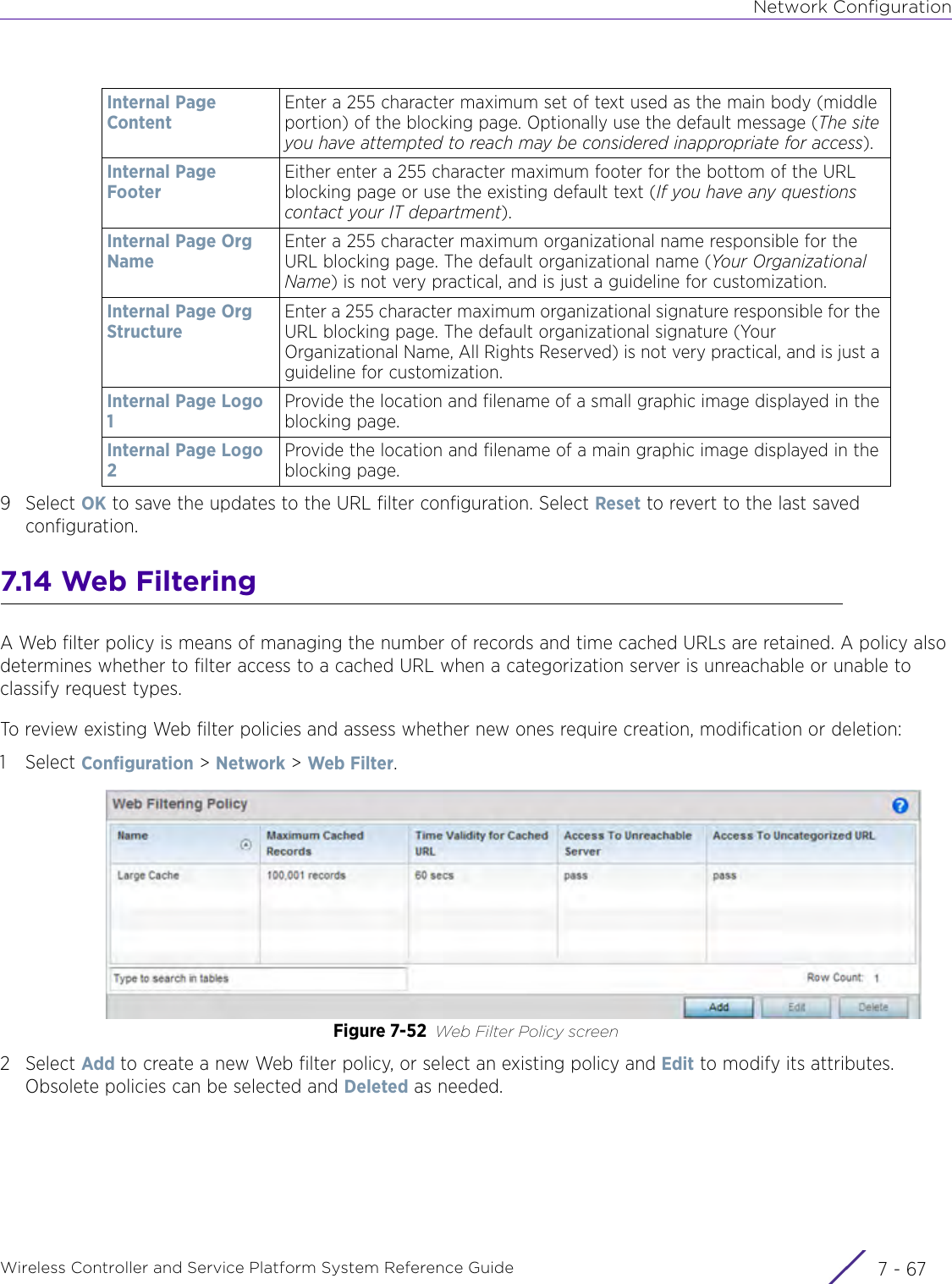
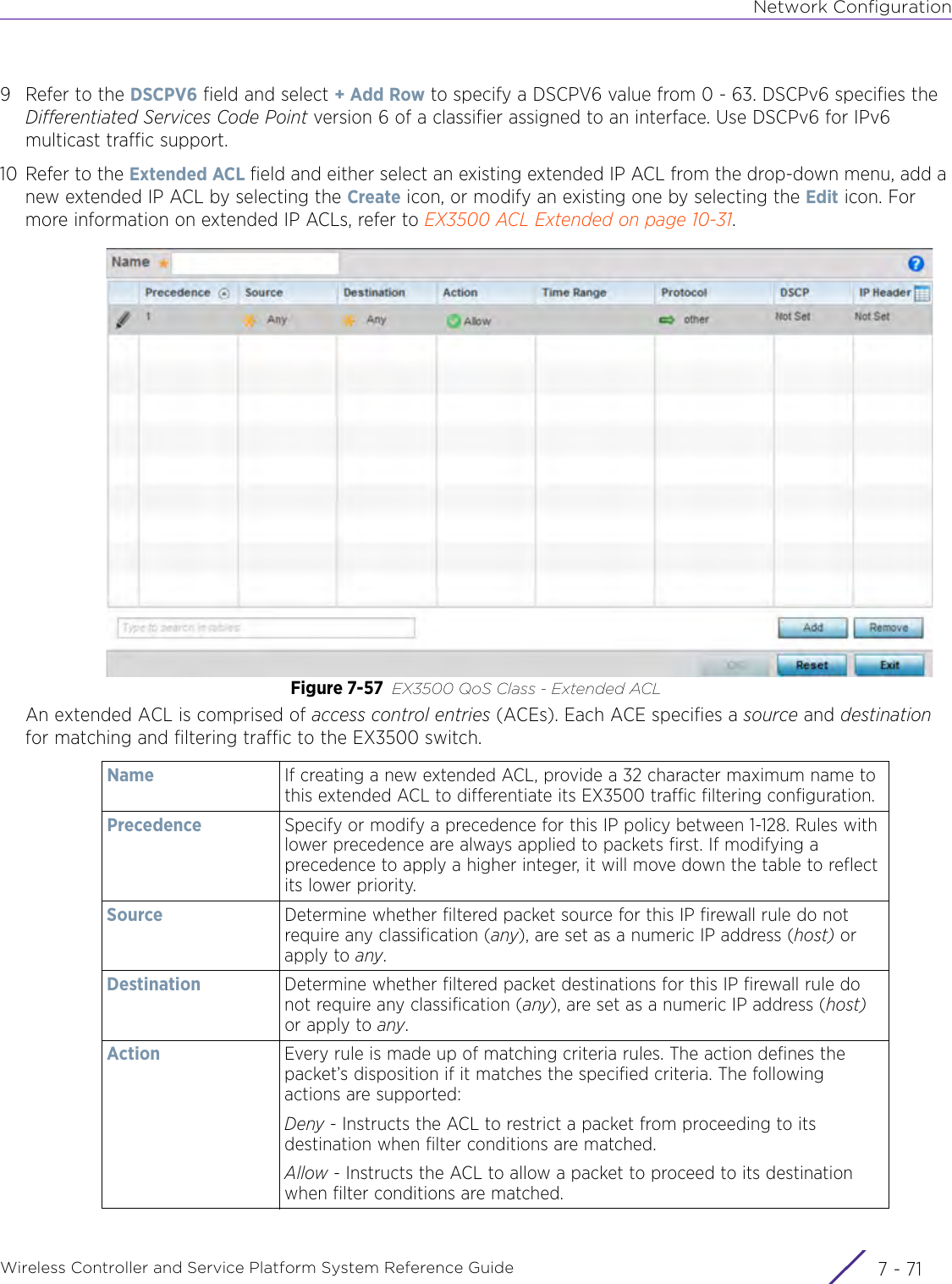
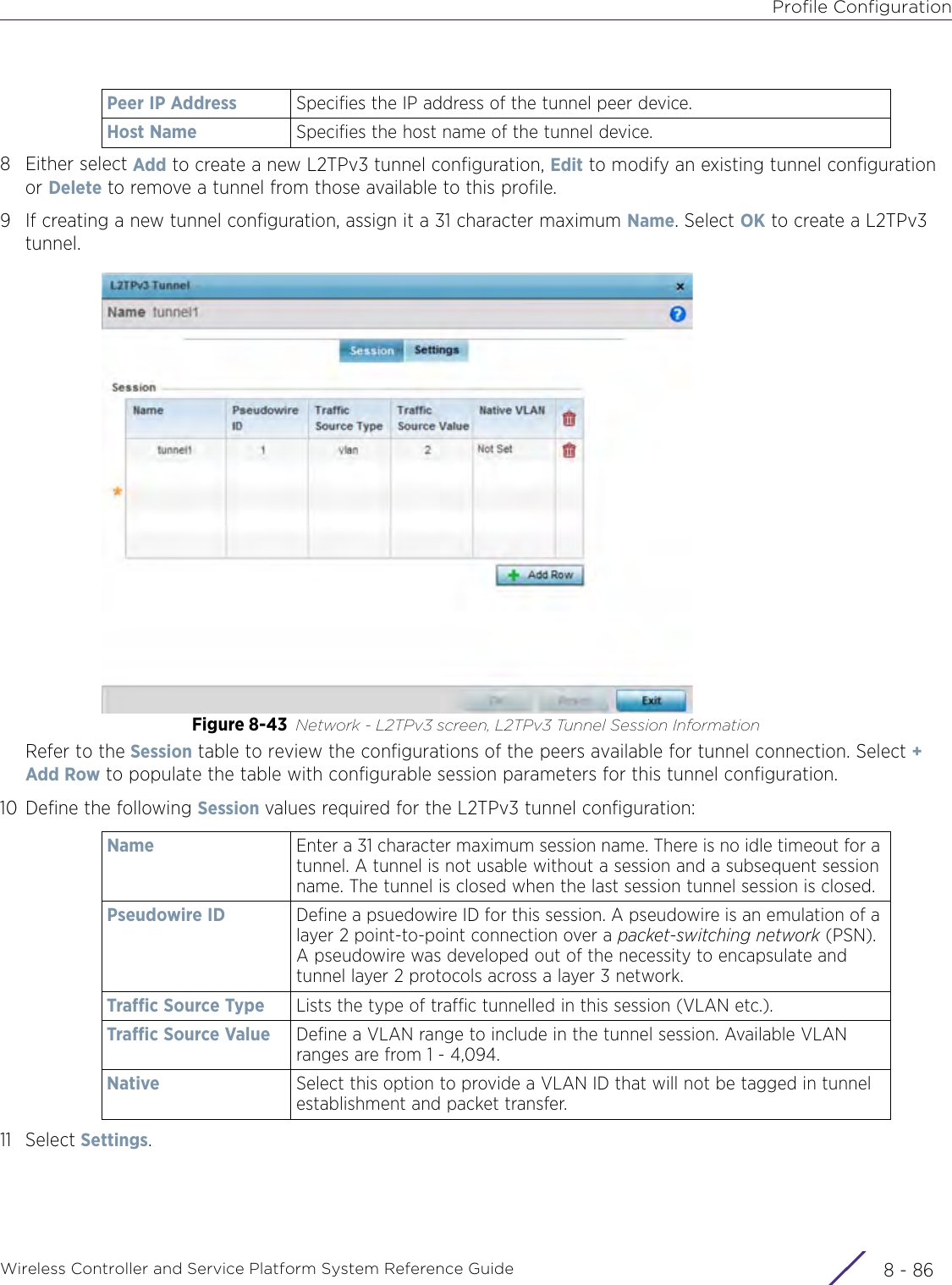
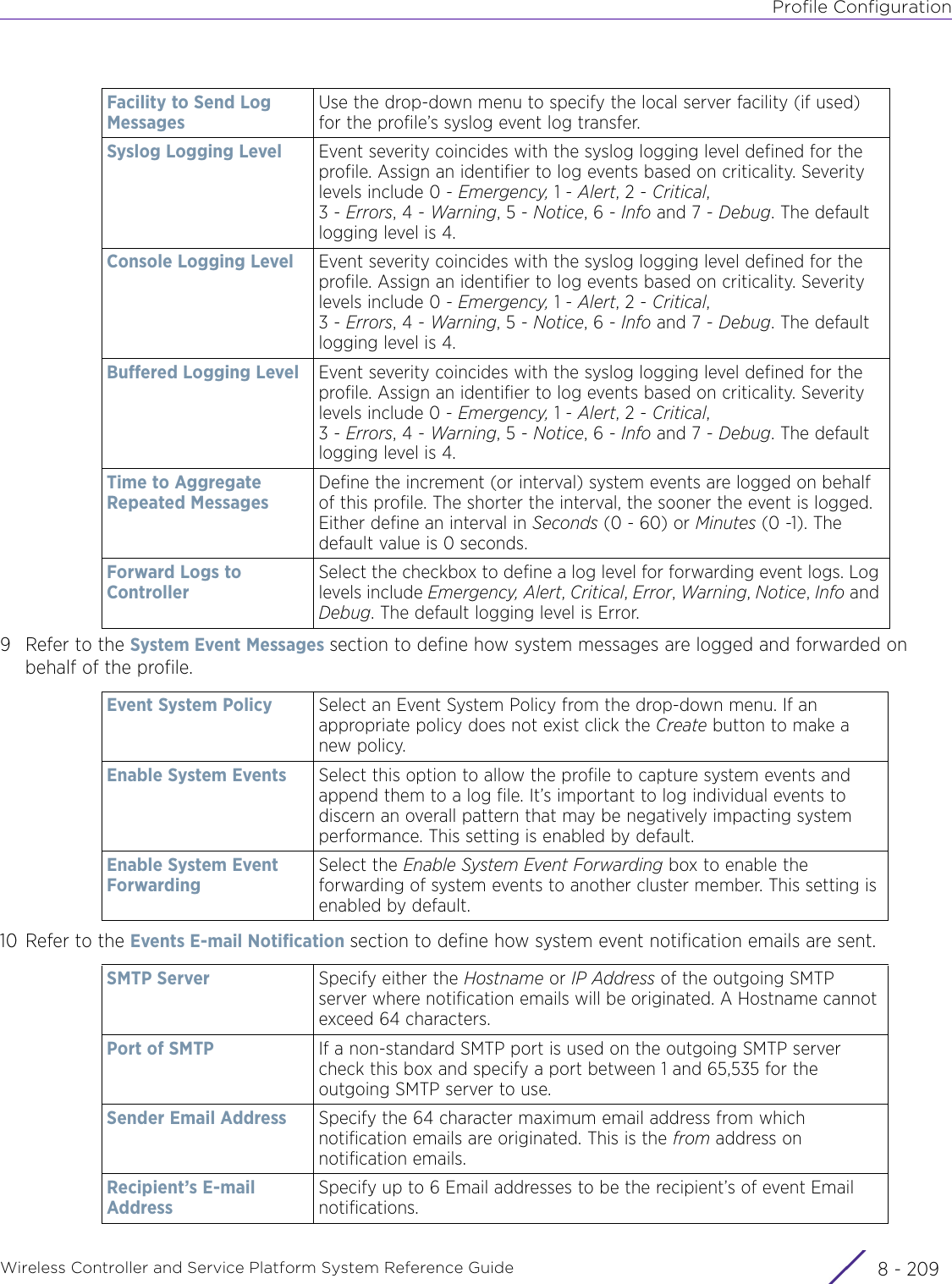
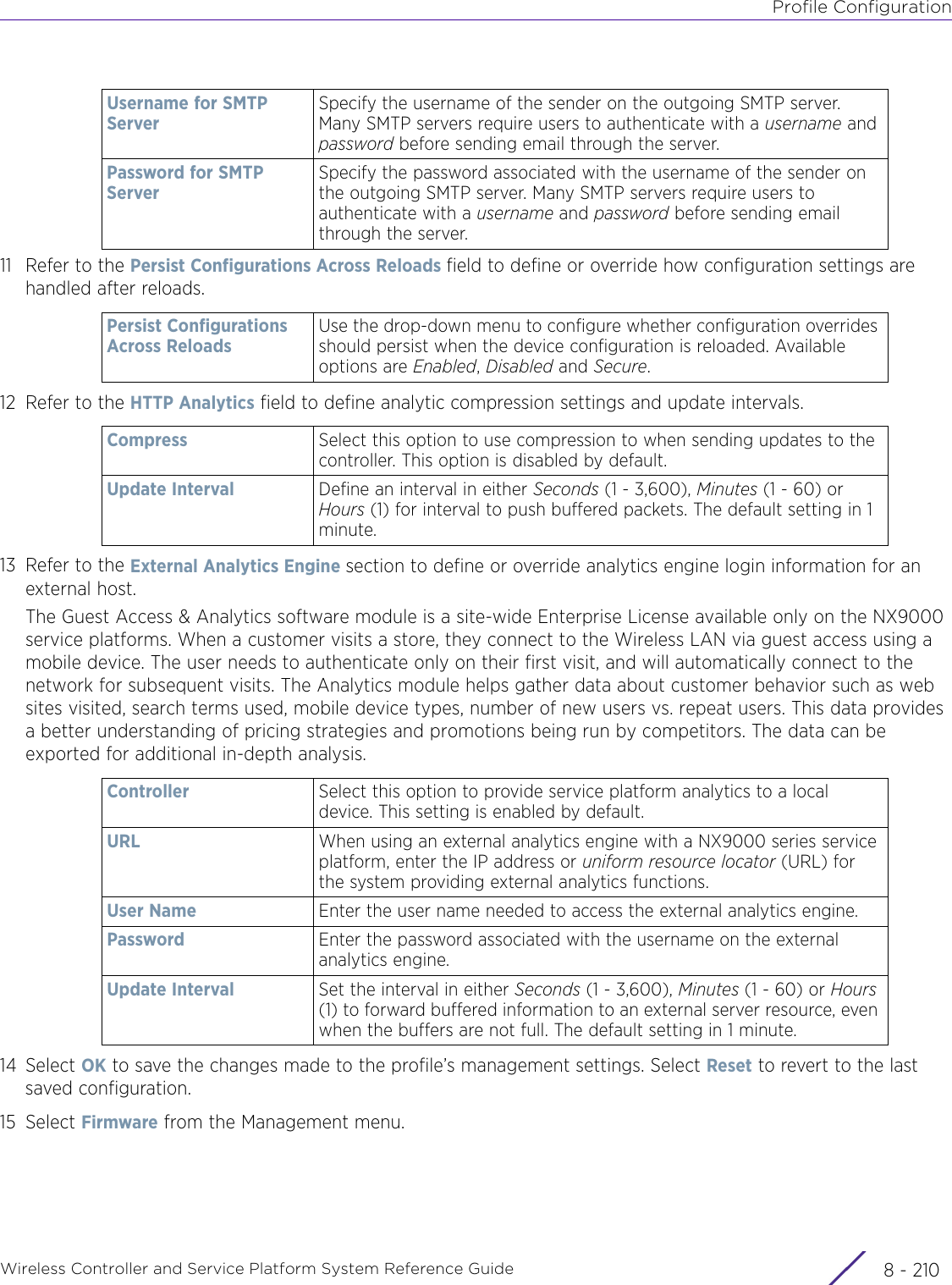
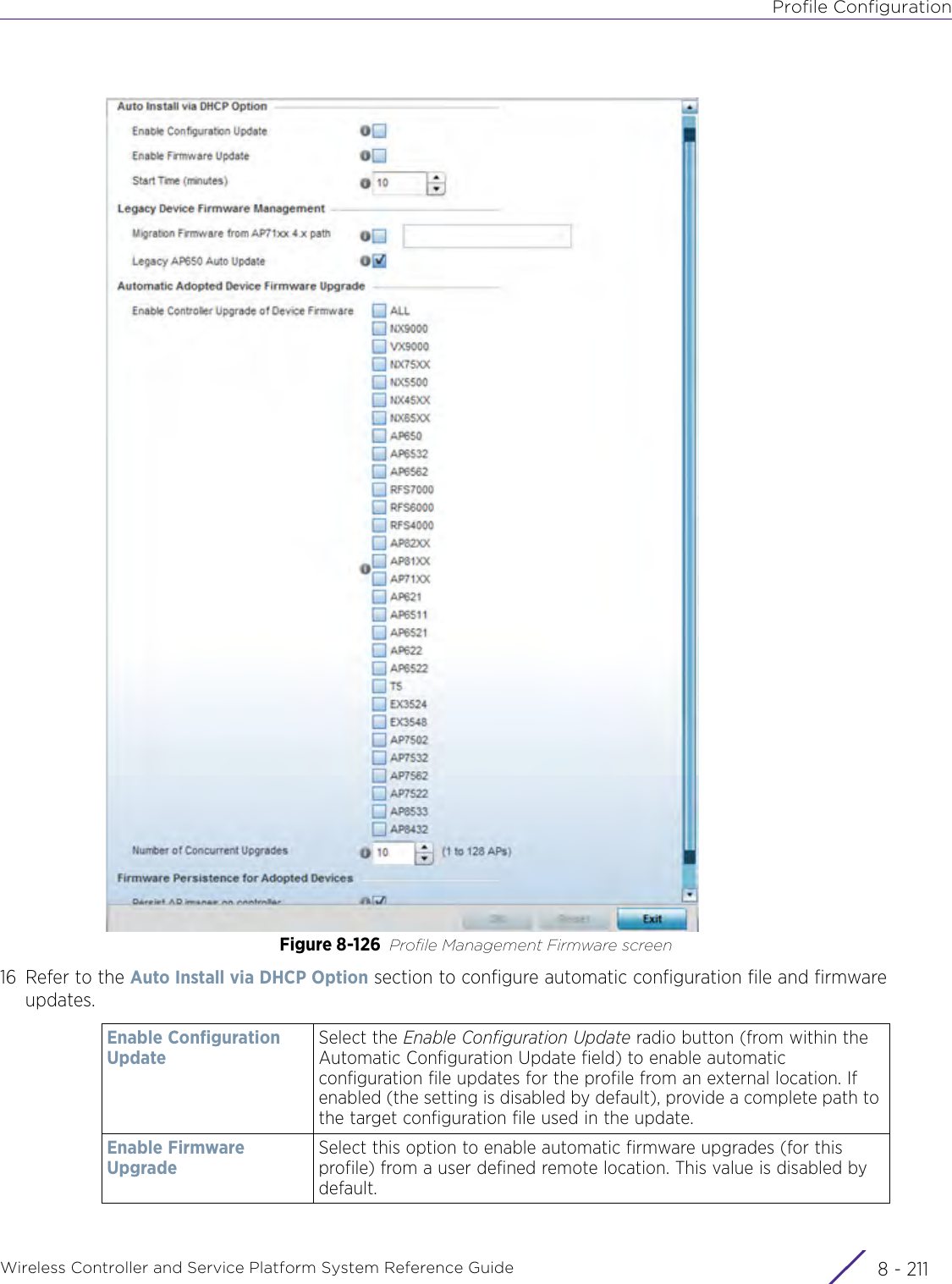
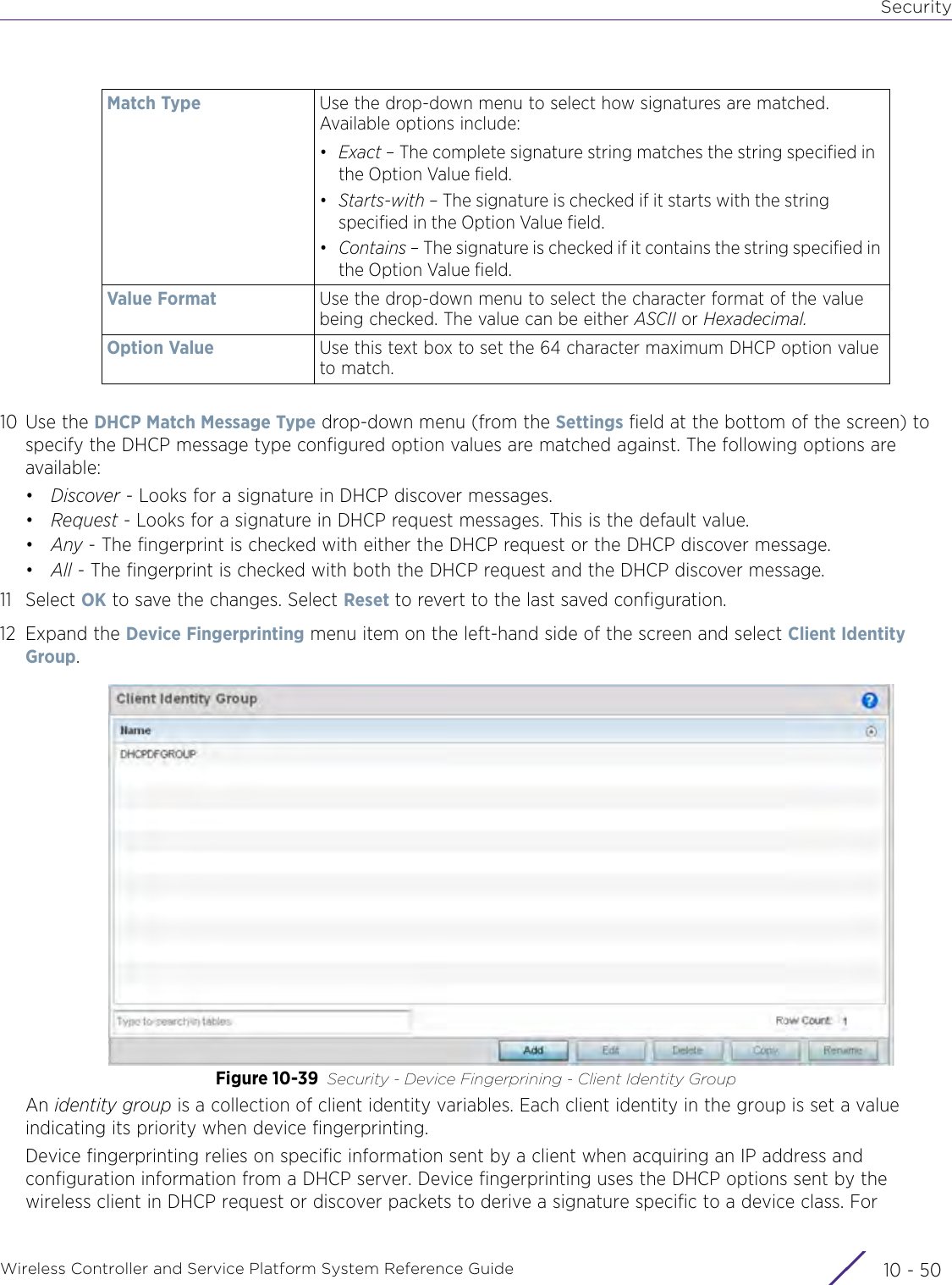
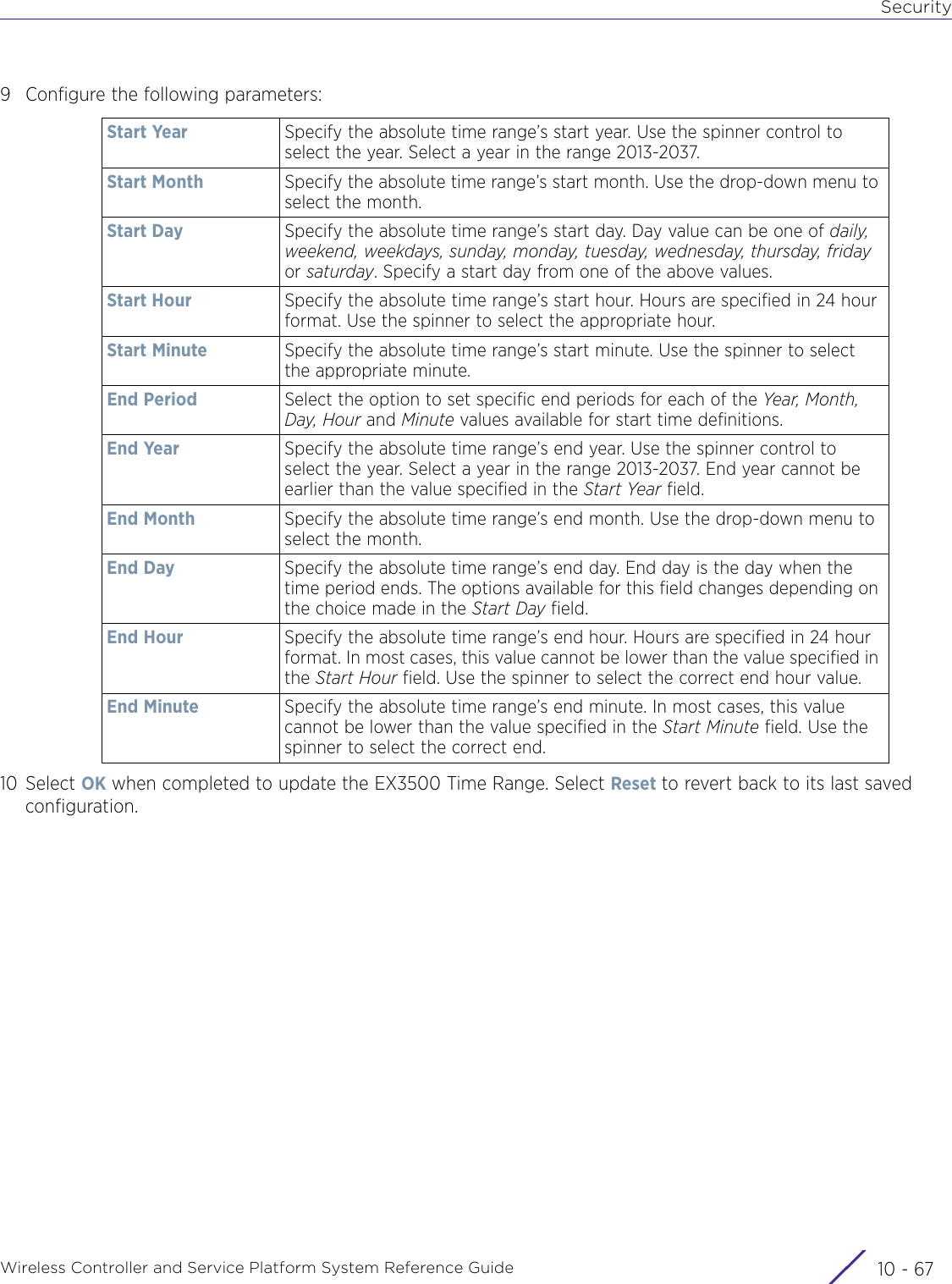
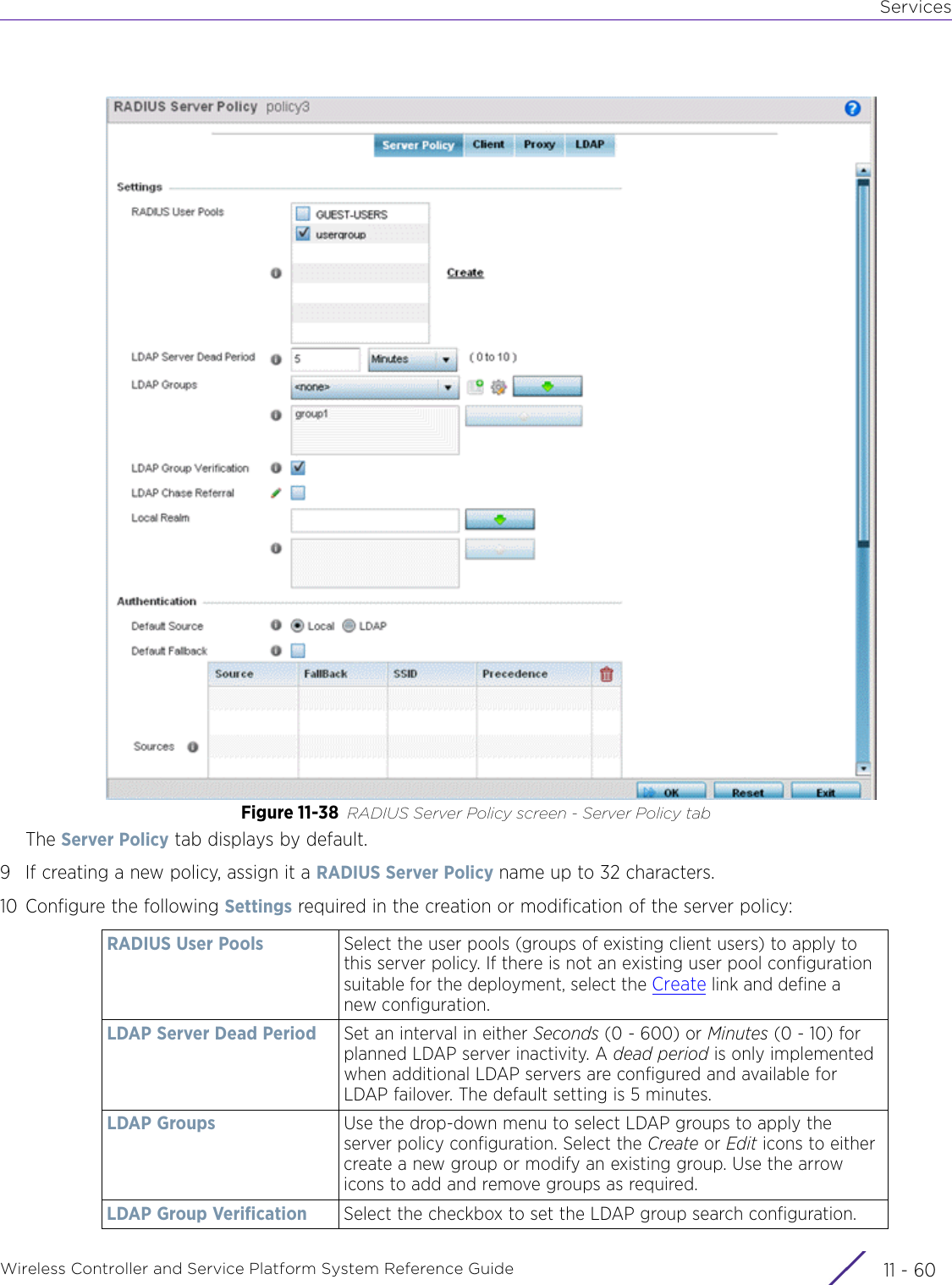
- 7. WiNG 5.9.1 System Reference Guide Part 3
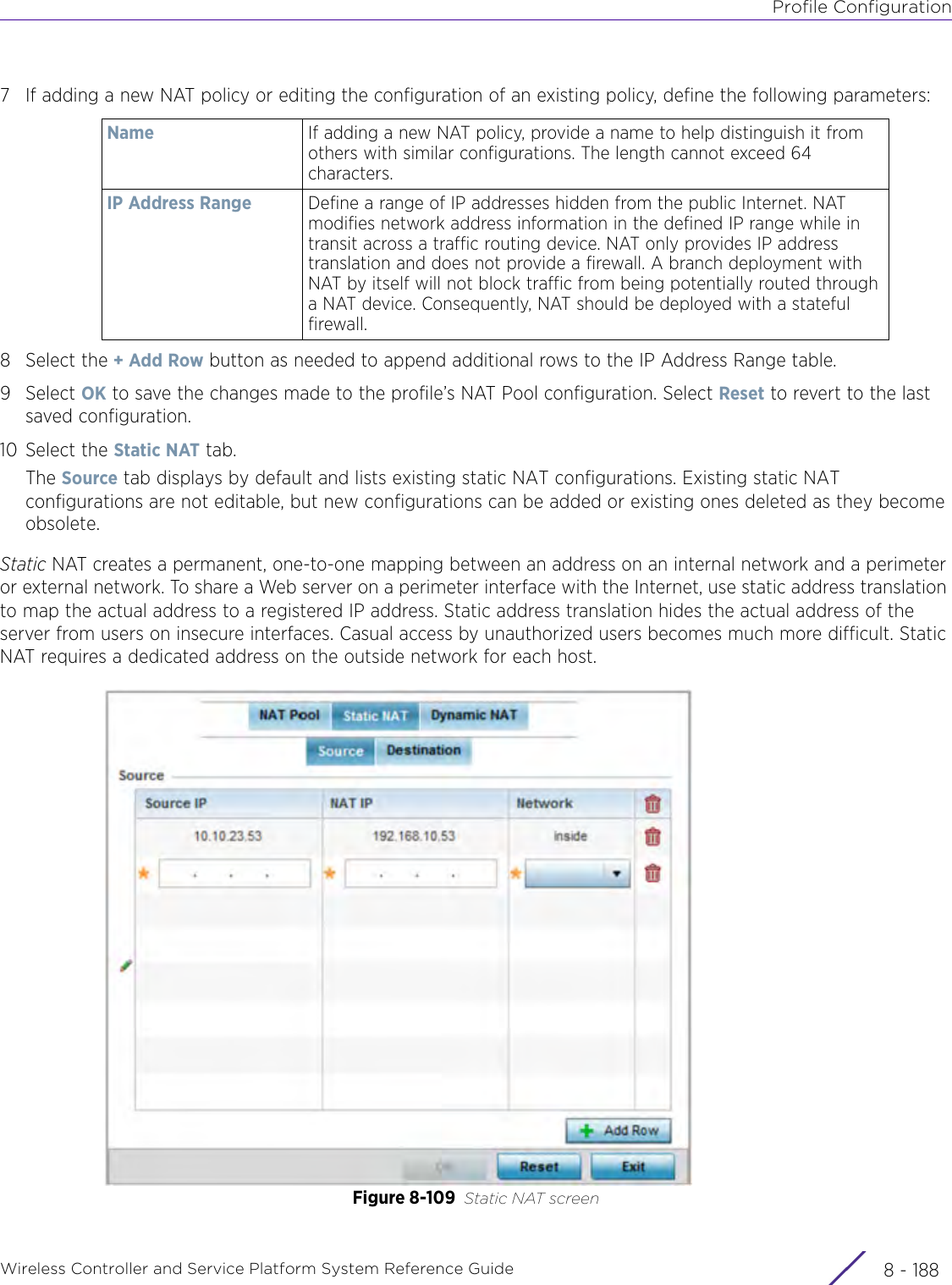
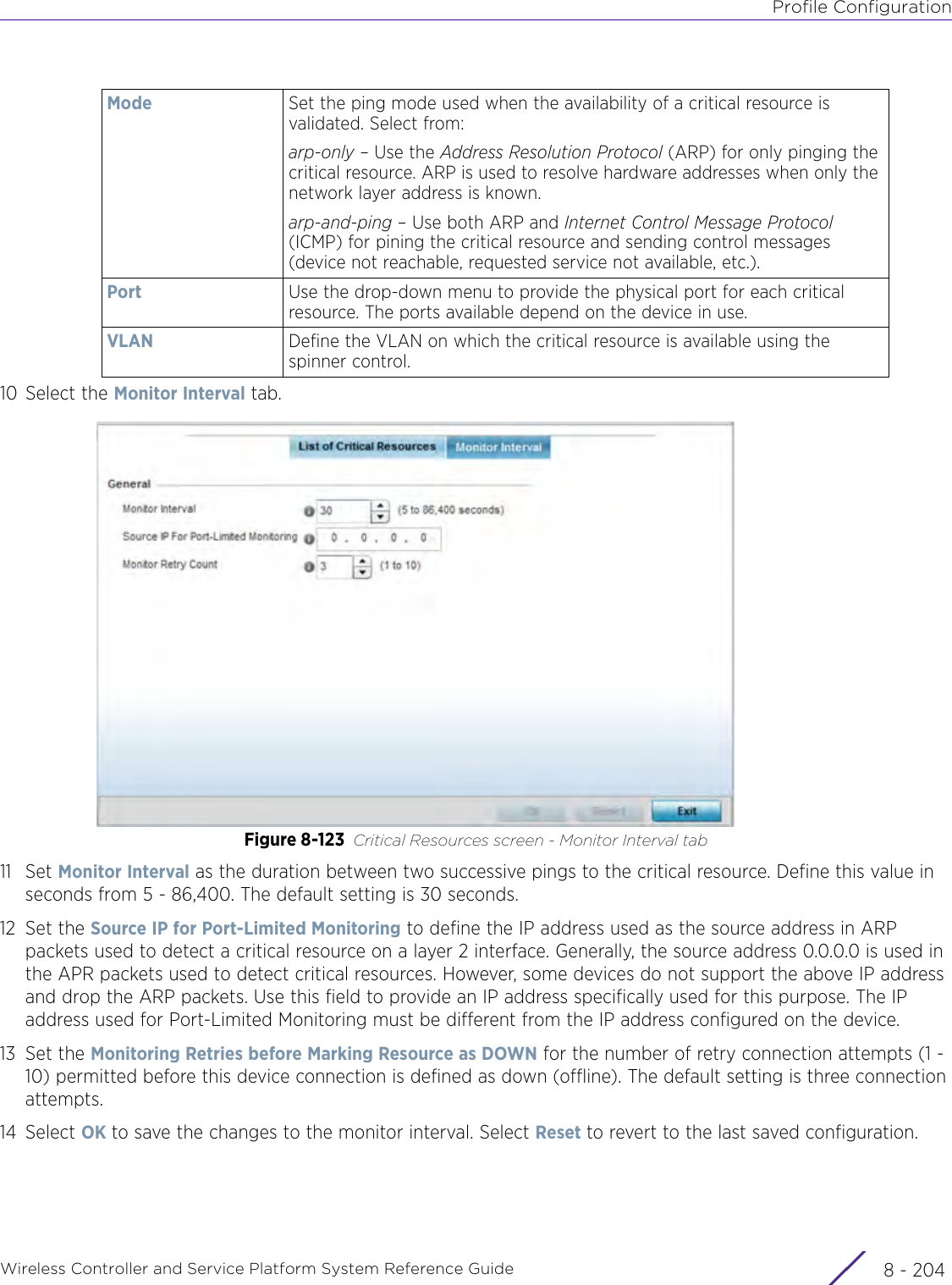
- 8. WiNG 5.9.1 System Reference Guide Part 4
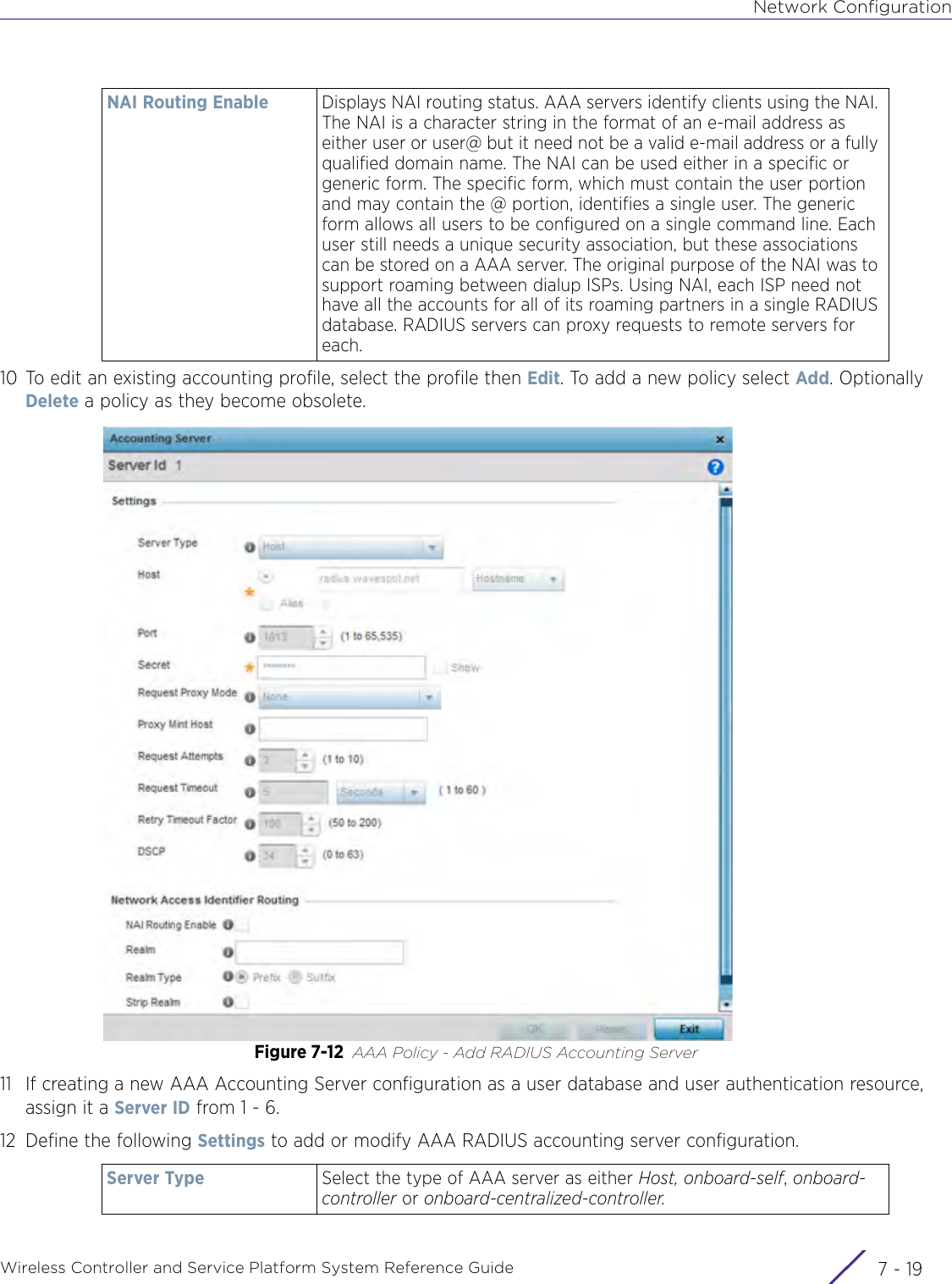
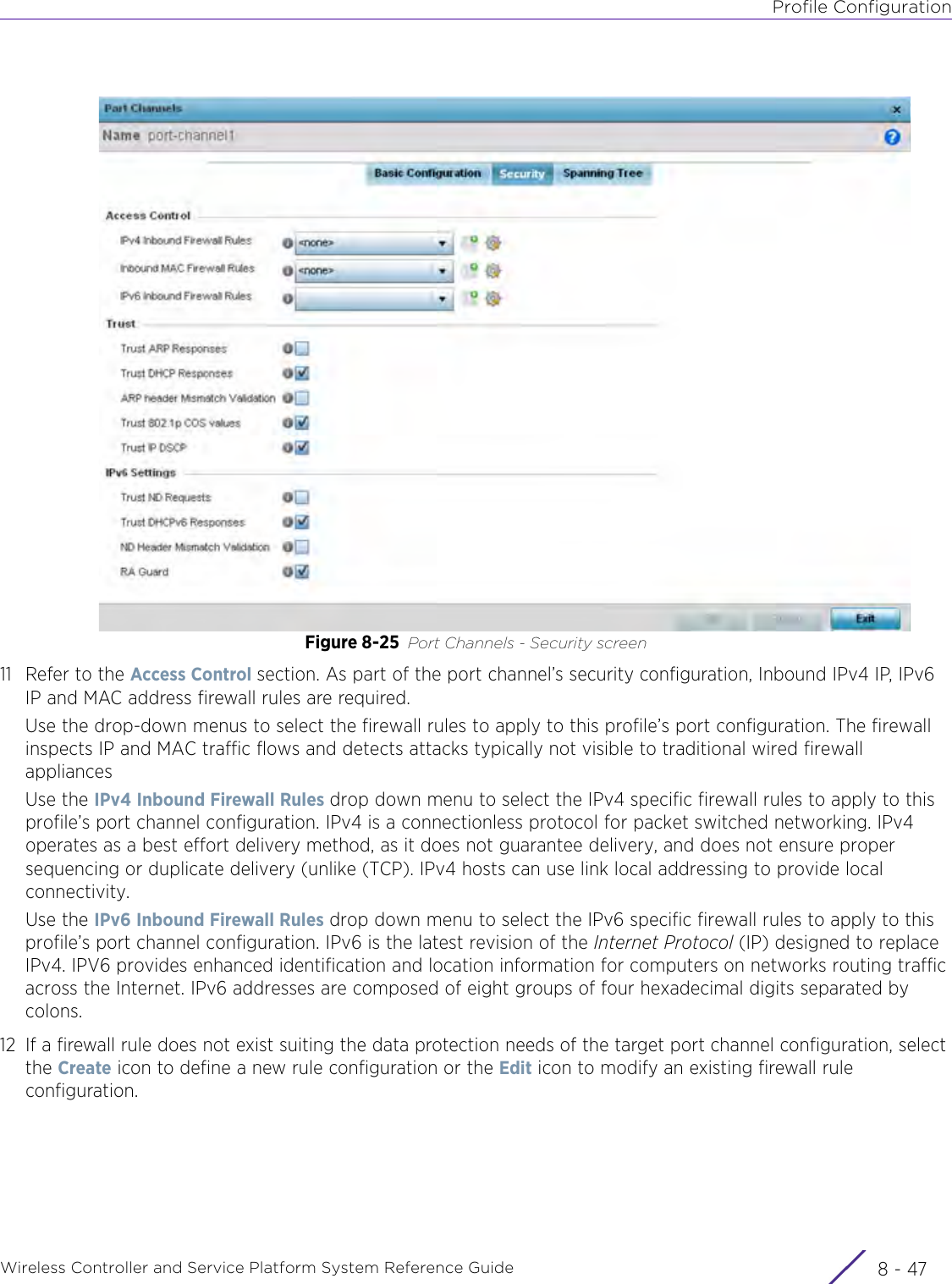
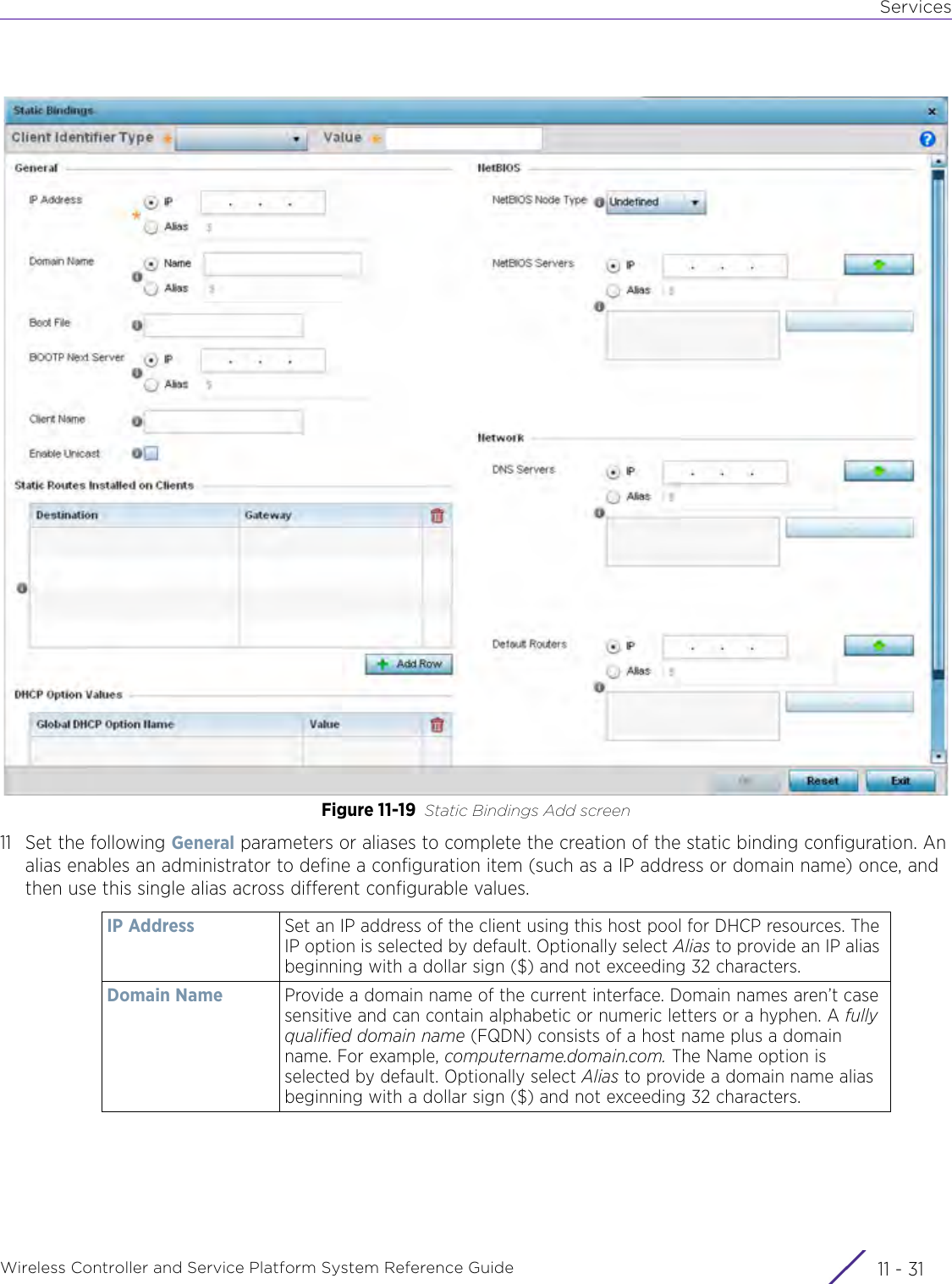
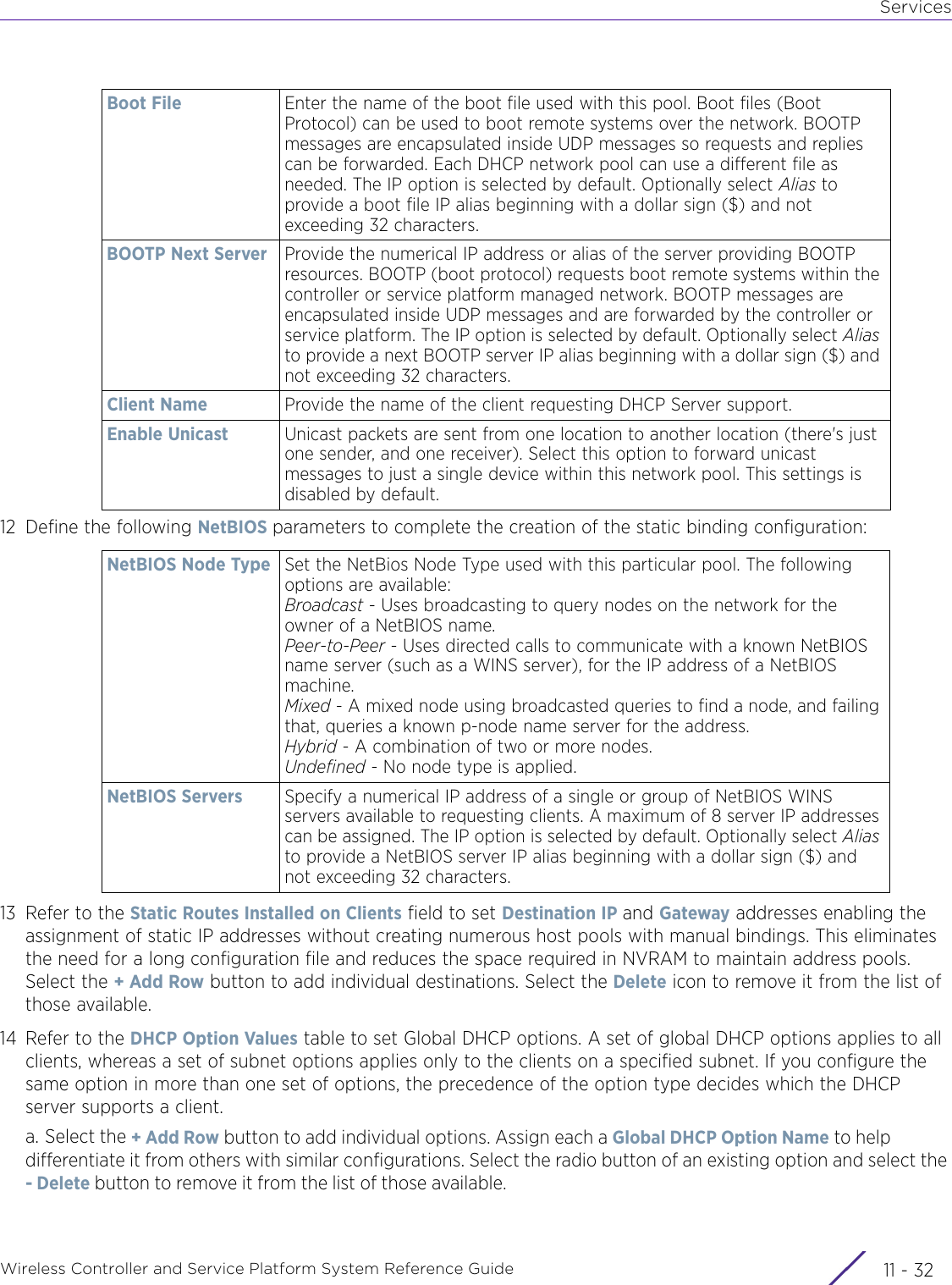
- 9. WiNG 5.9.1 CLI Reference Guide Part 1
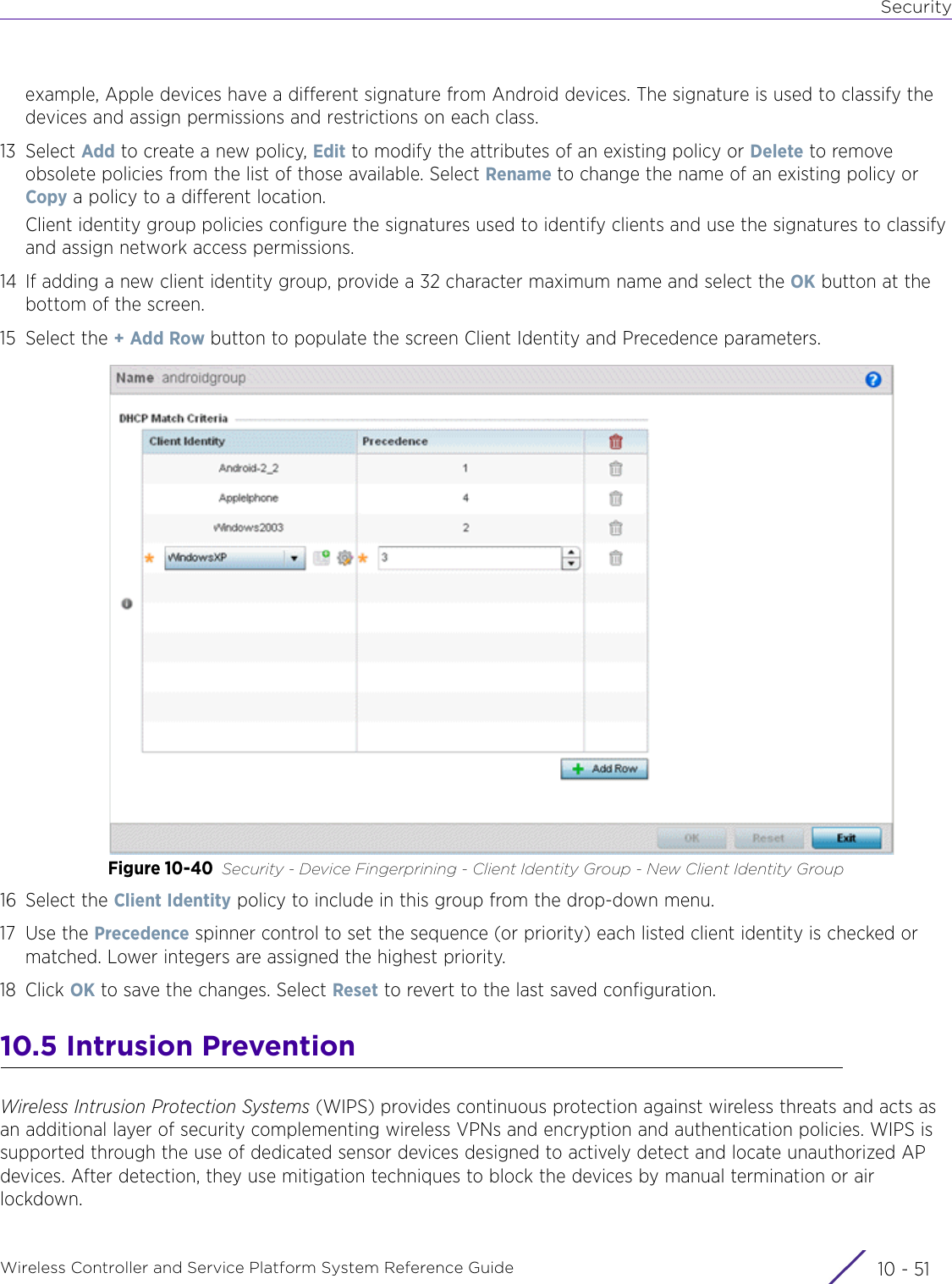
- 10. WiNG 5.9.1 CLI Reference Guide Part 2
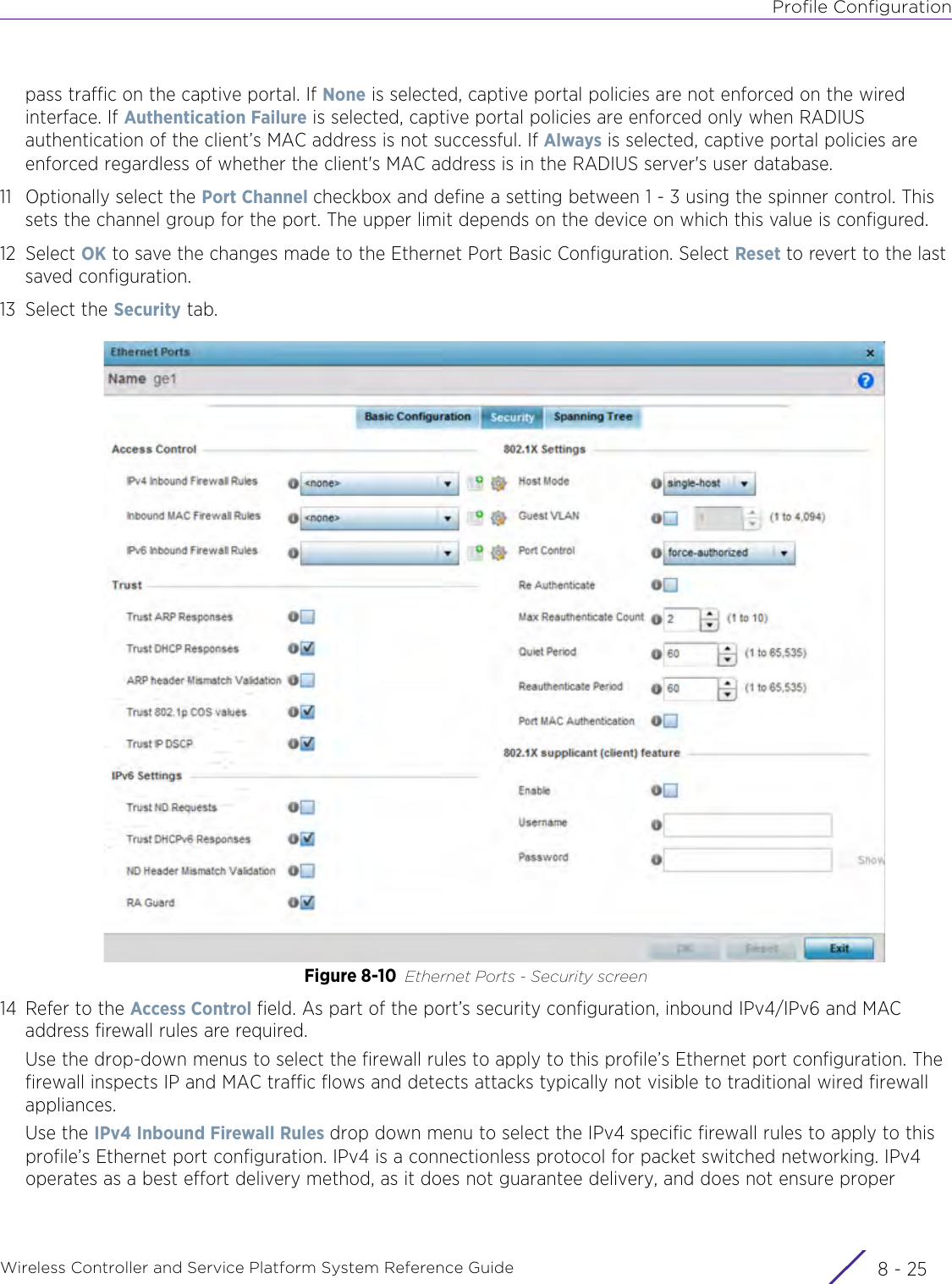
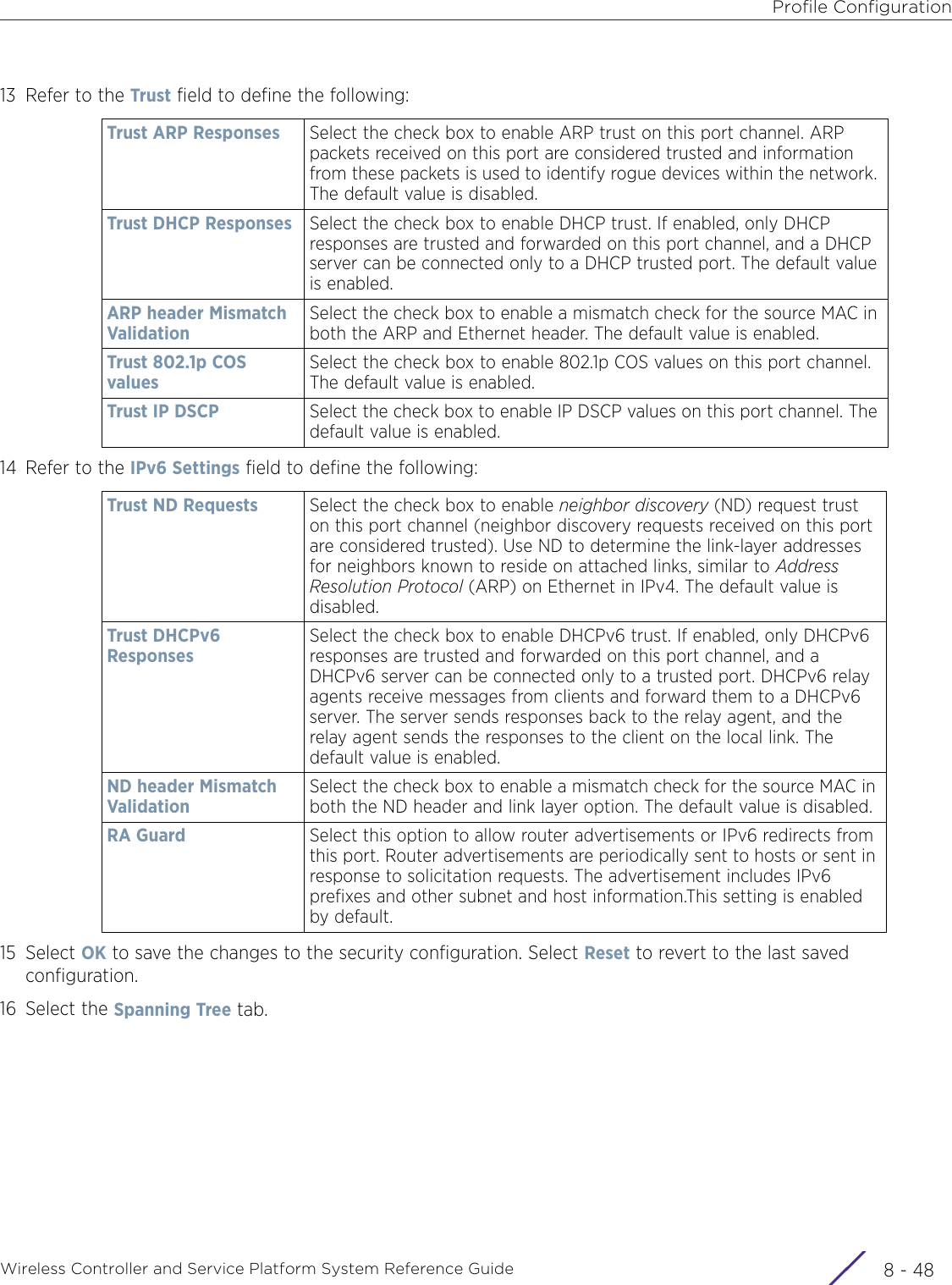
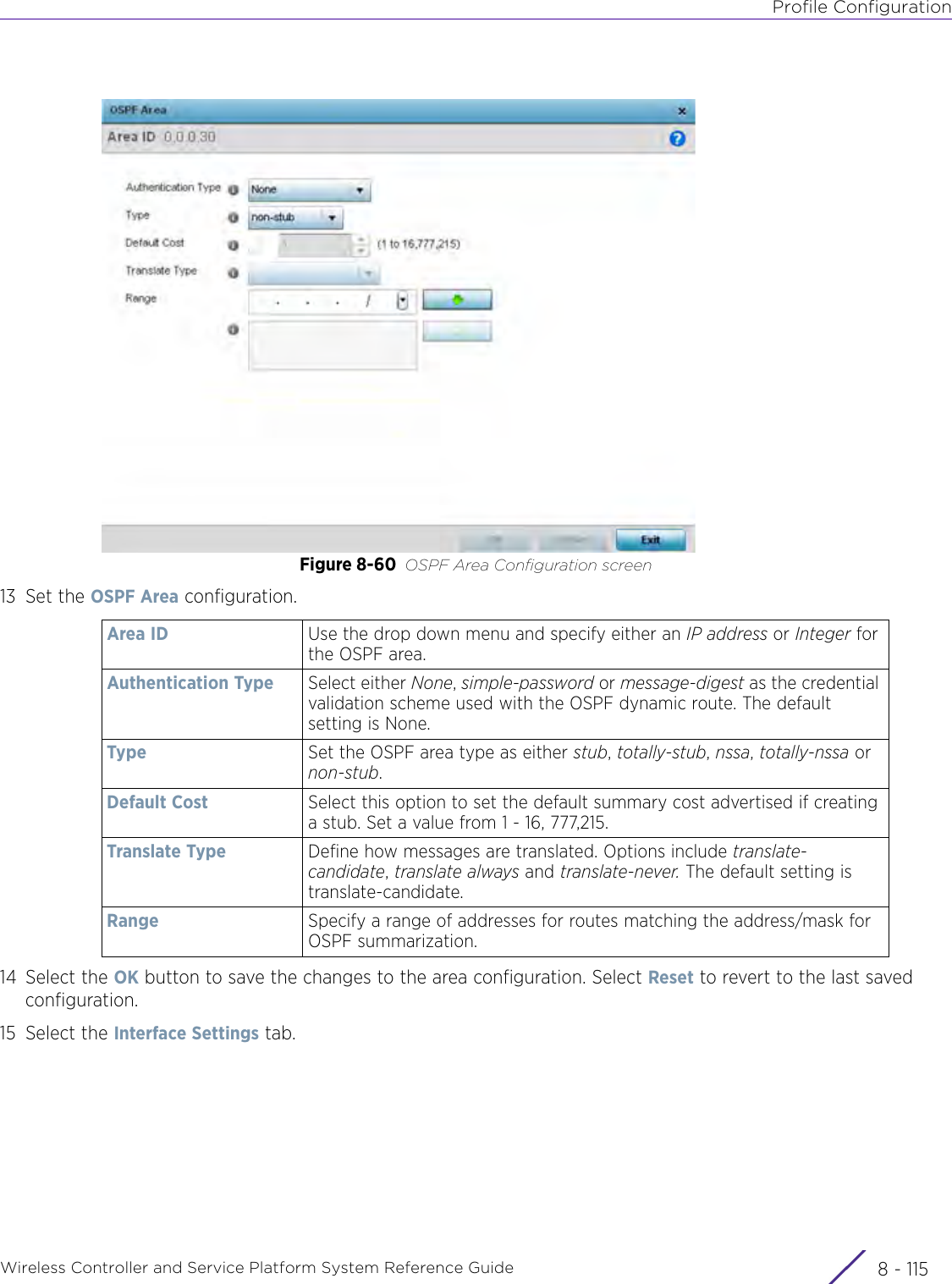
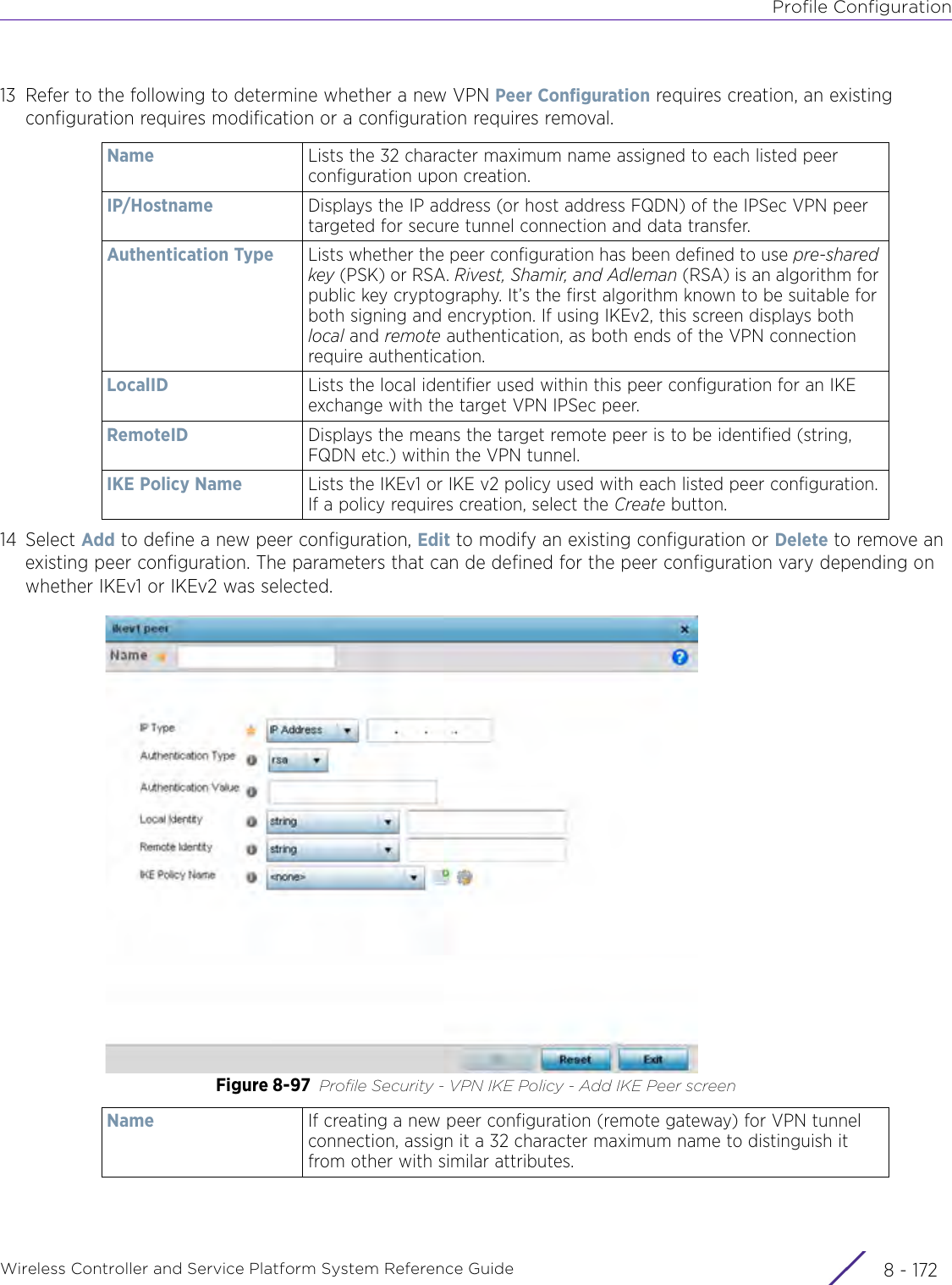
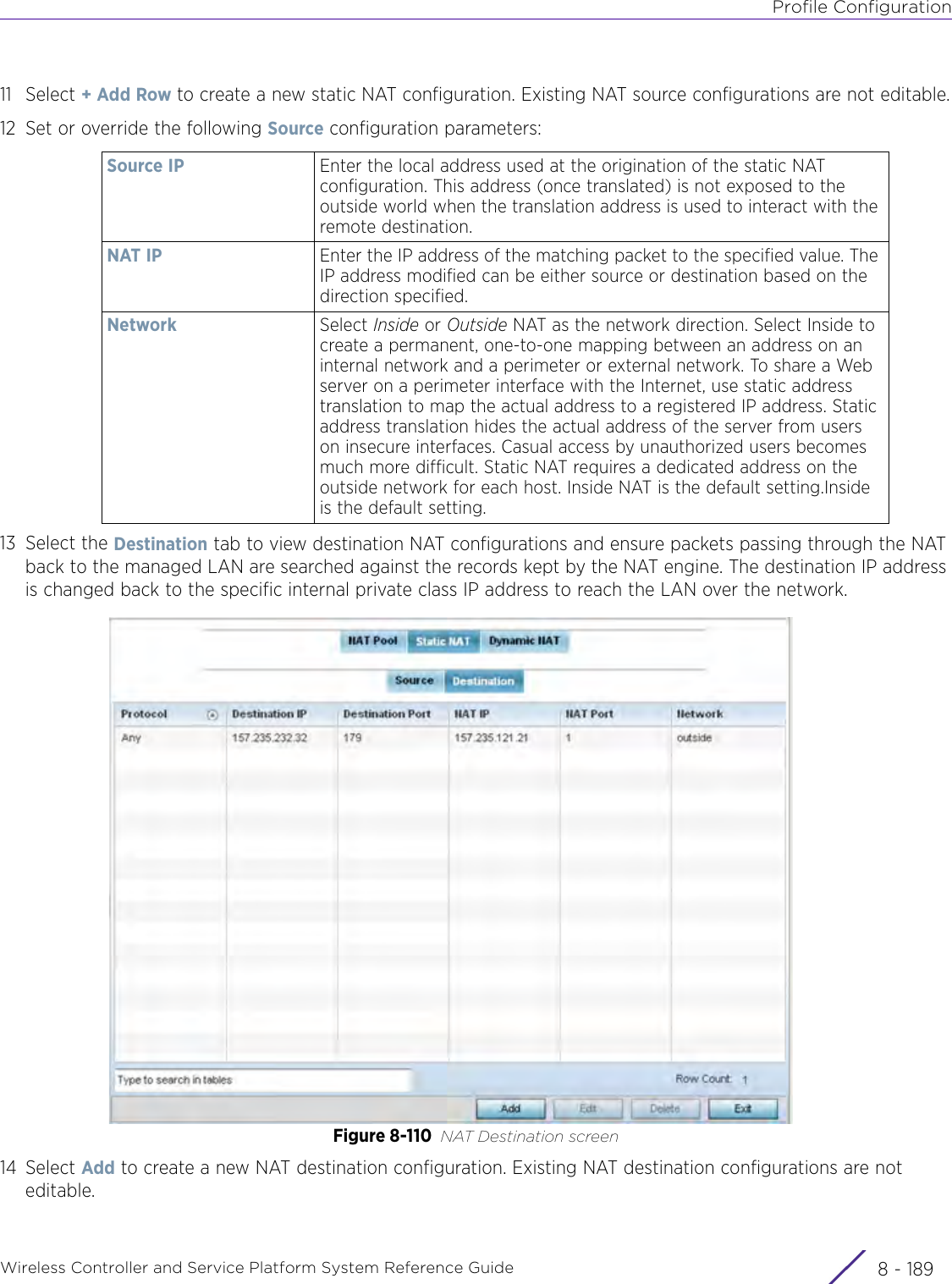
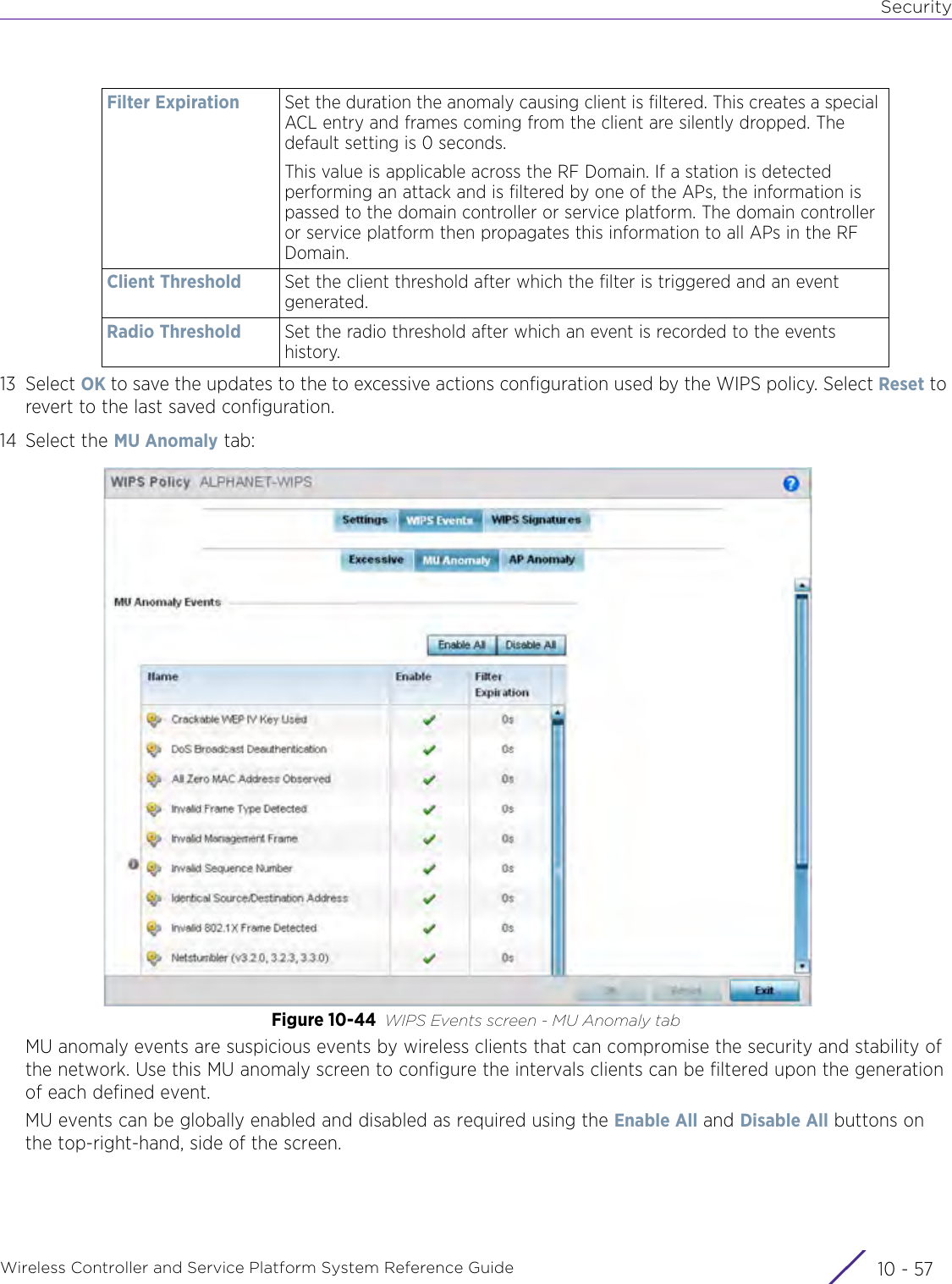
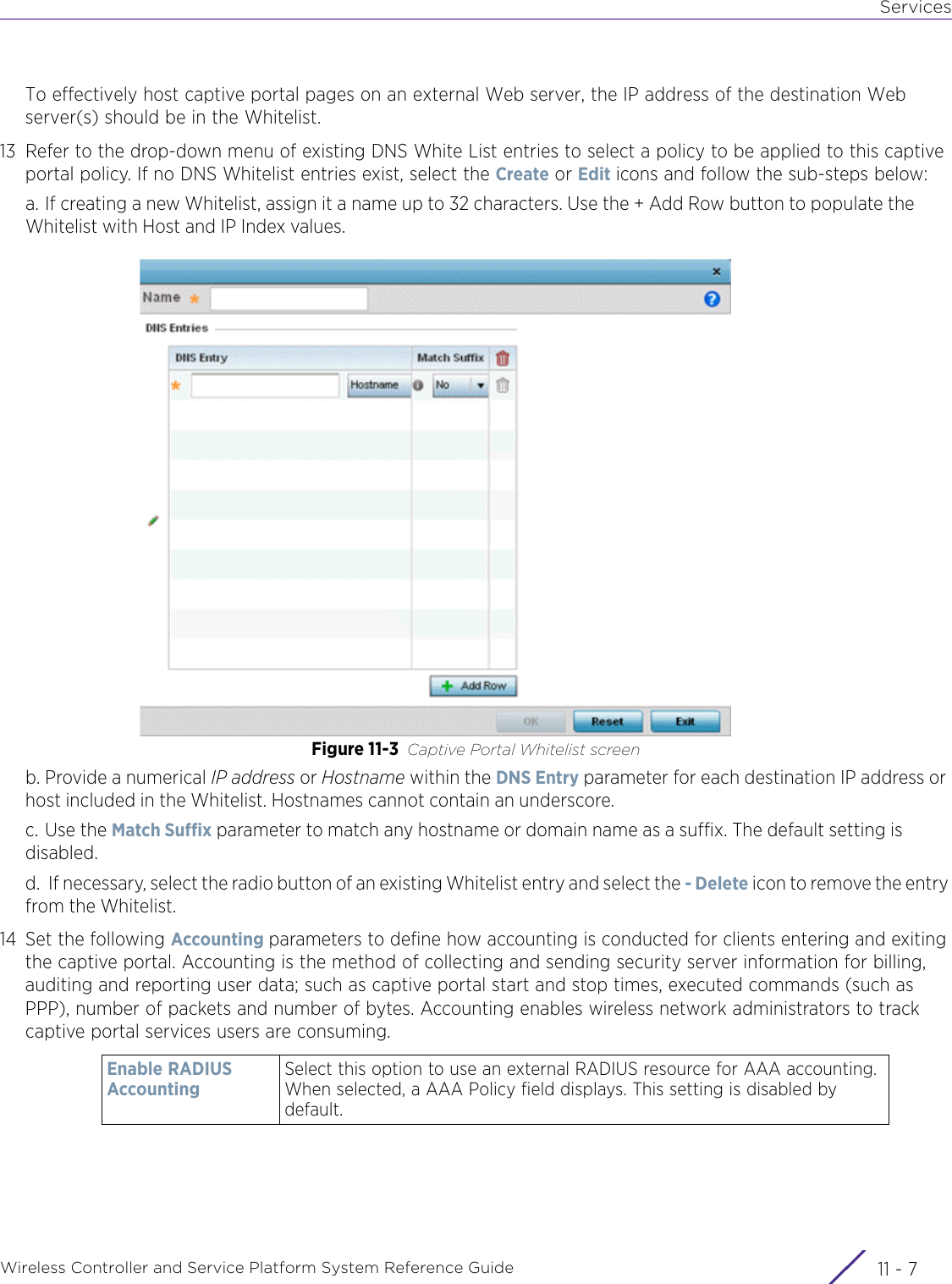
- 11. Extreme Wireless V10.41.06 User Guide Part 1
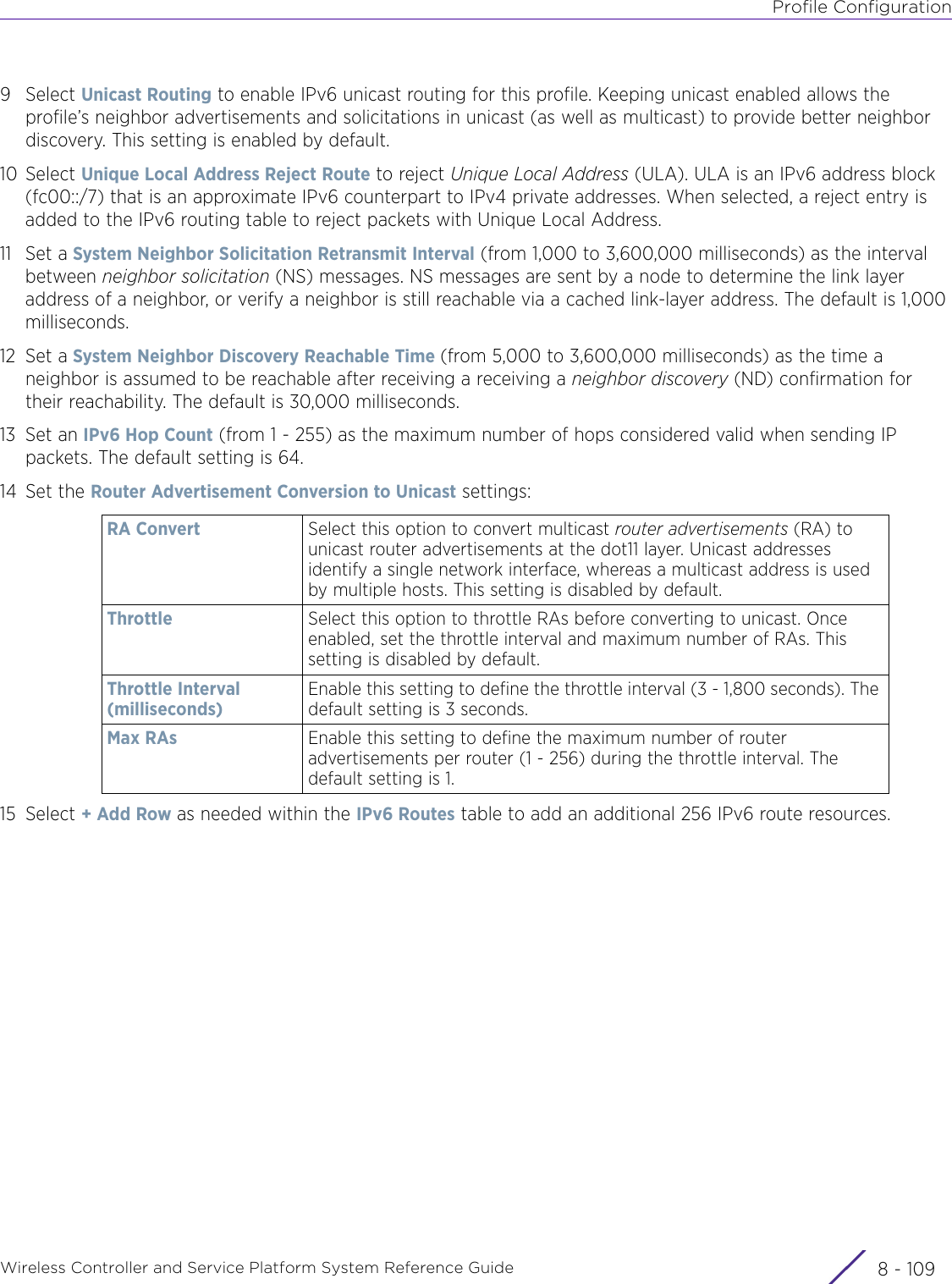
- 12. AP3917 User Manual
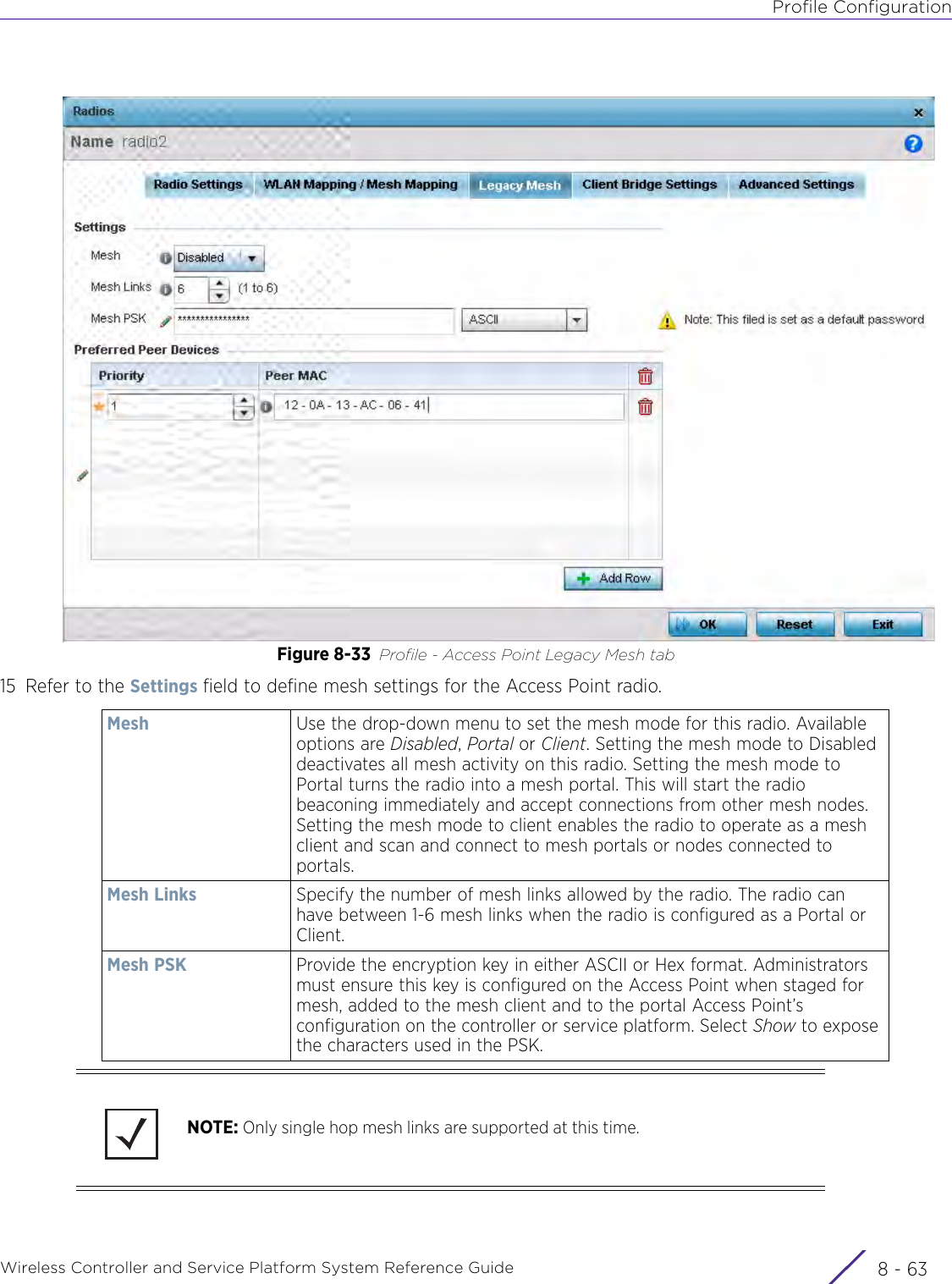
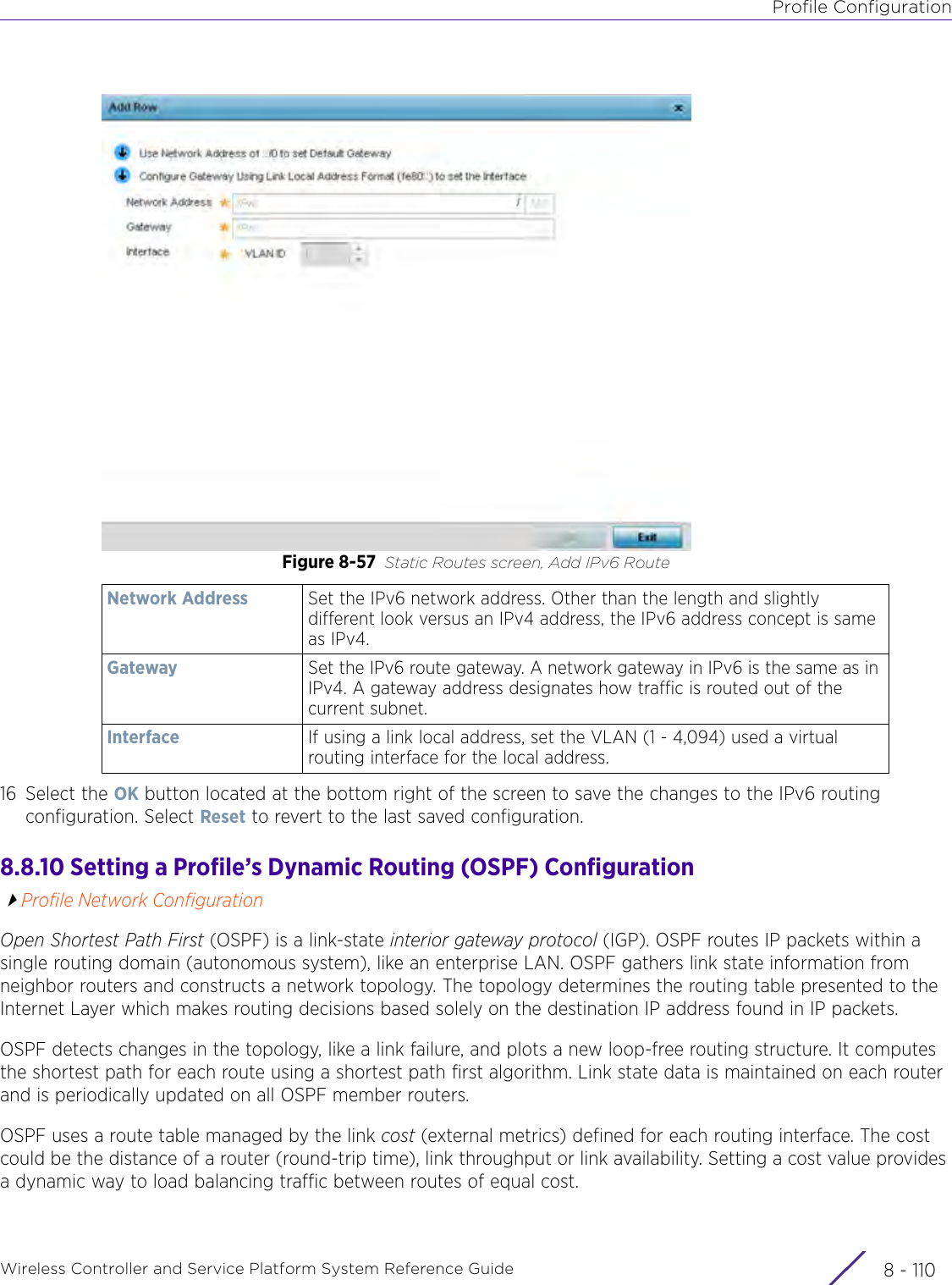
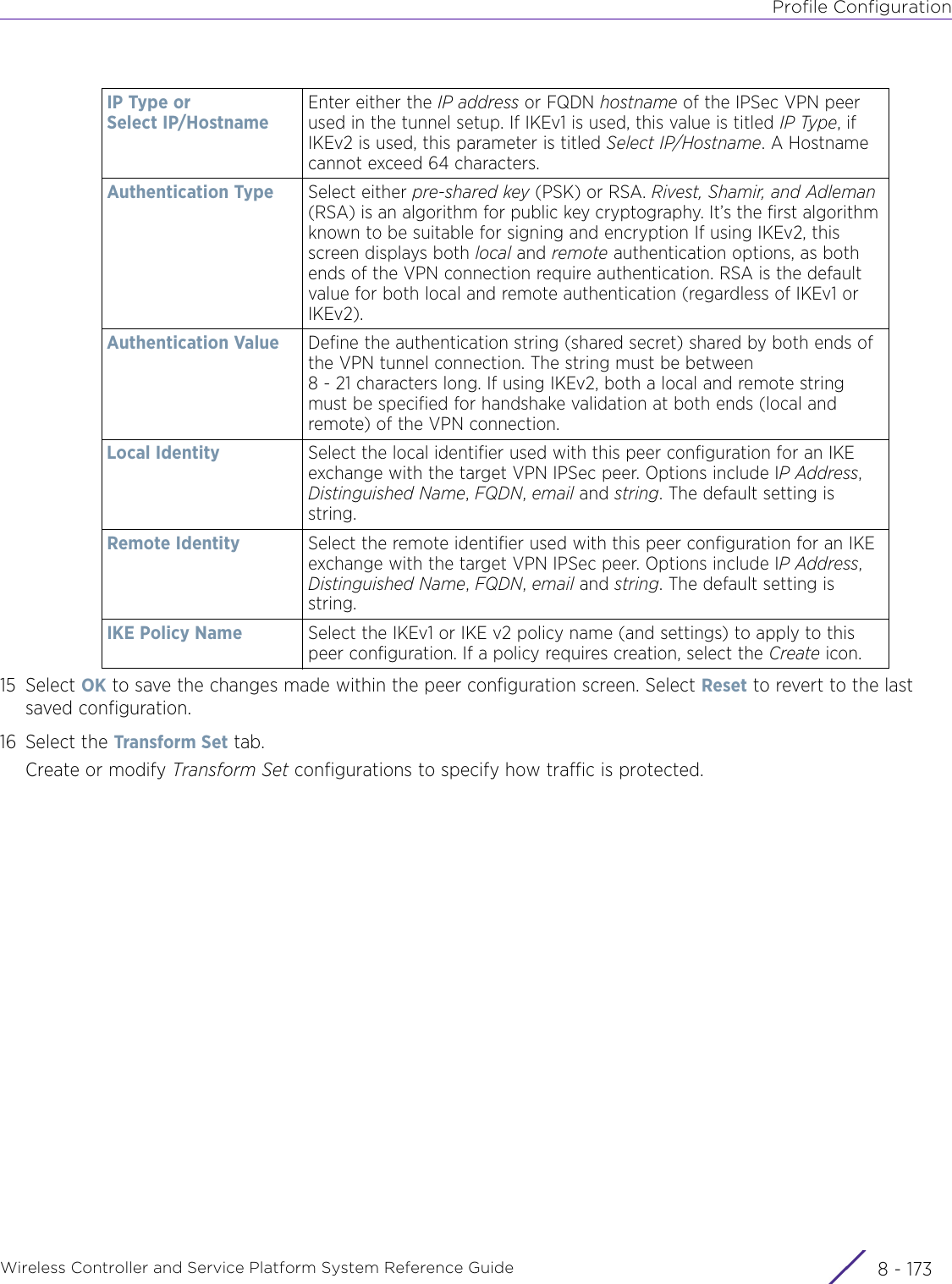
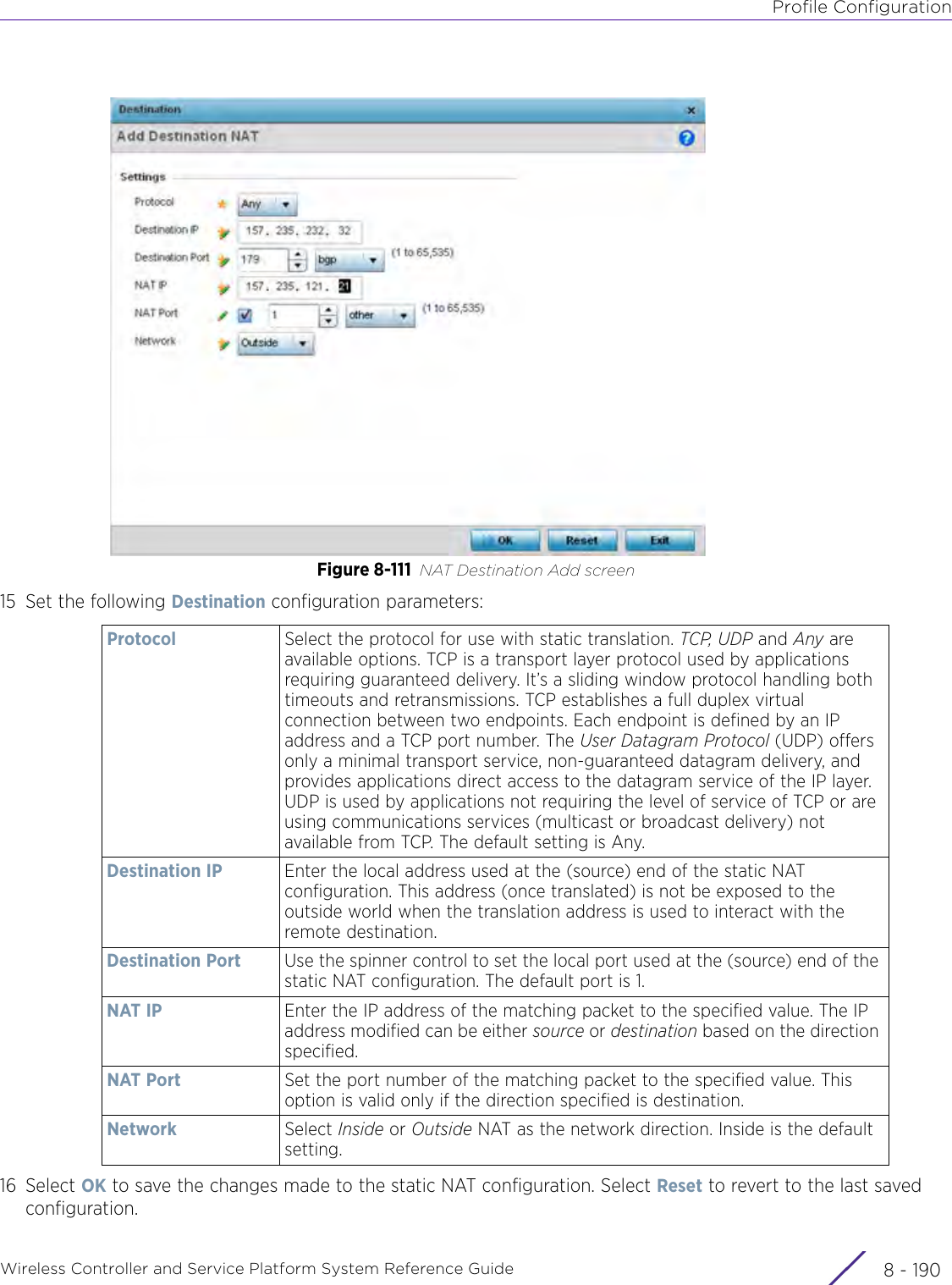
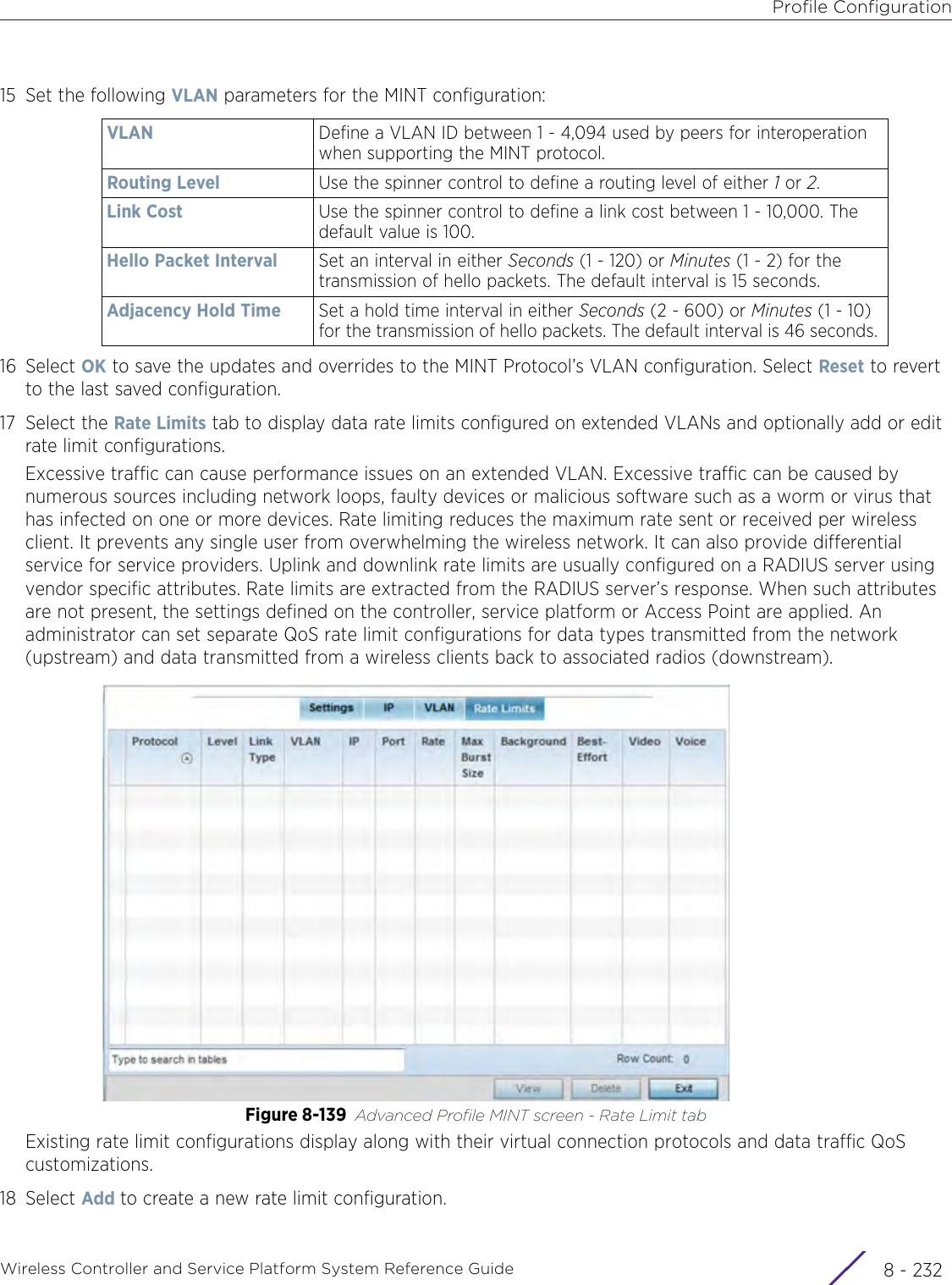
- 13. AP7662 User Manual
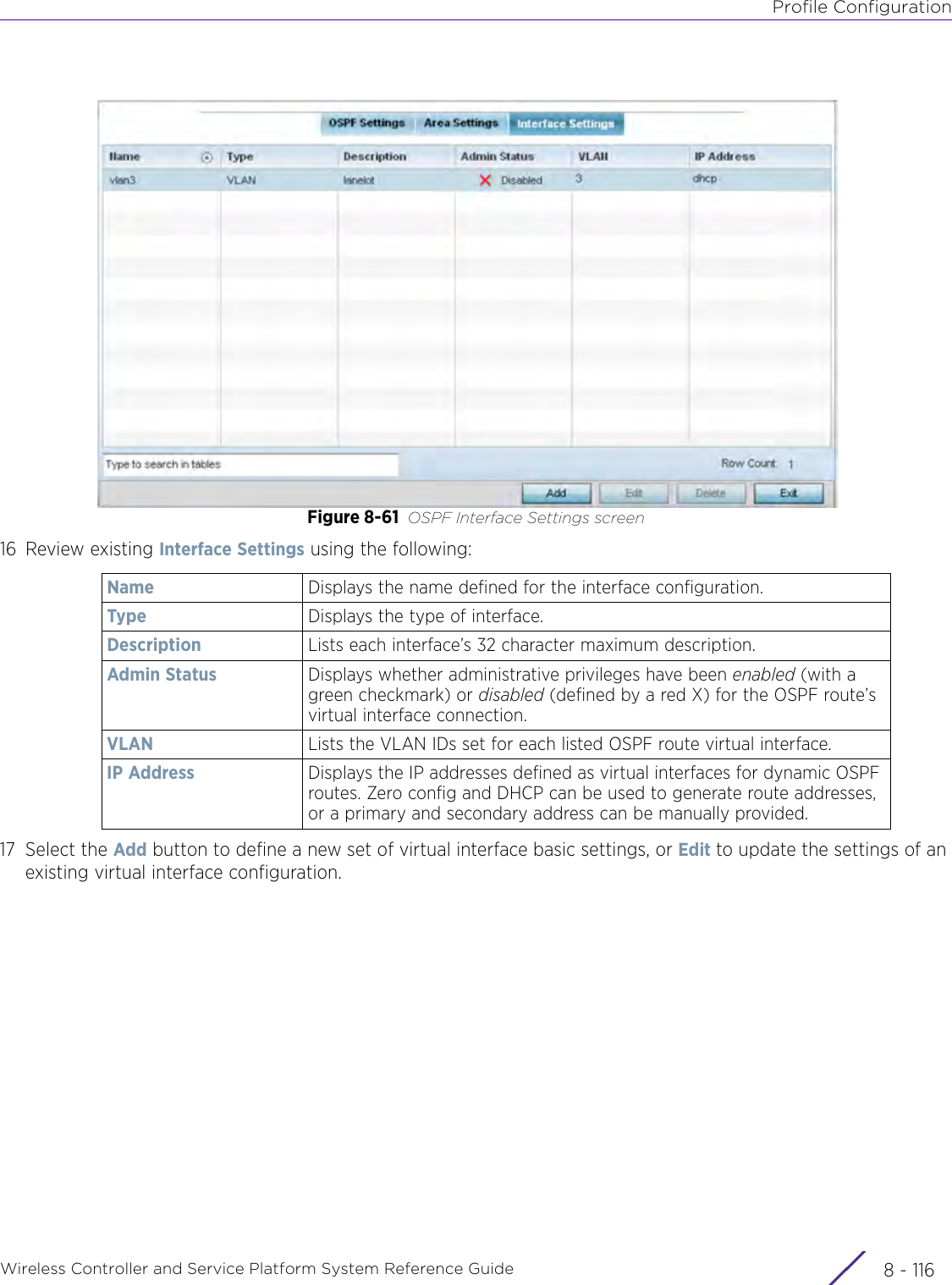
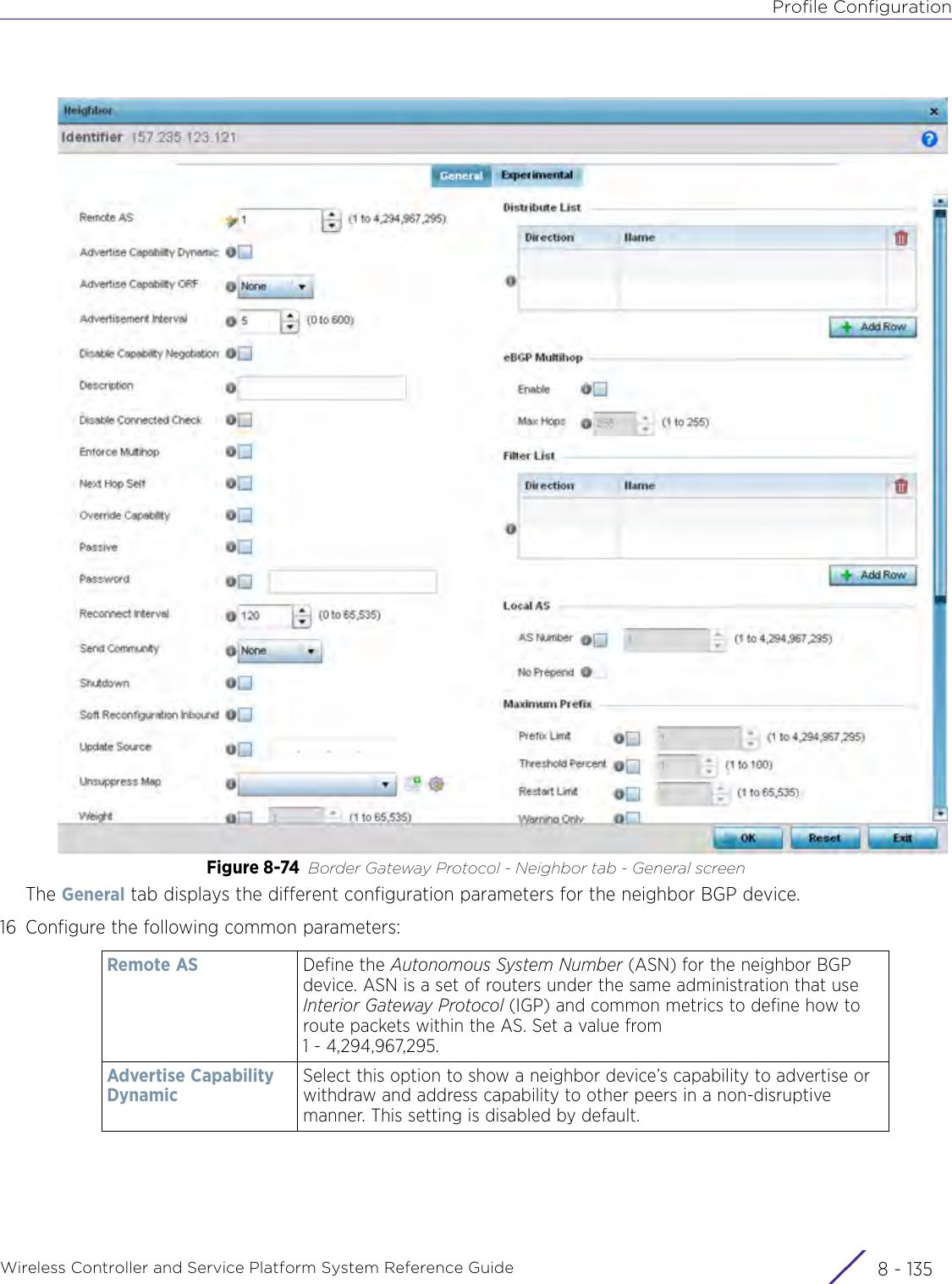
WiNG 5.9.1 System Reference Guide Part 2